Systems Programming
Article info.
- Operating System
- Linux File System
- Relational Database Management System
- Systems Modelling Language
- Systems Thinking
- Programming Paradigms

Article Versions
- 4 2022-05-30 18:30:08 3705,3694 4,3705 By arvindpdmn Completing the article and publishing.
- 3 2022-05-23 13:13:29 3694,3693 3,3694 By arvindpdmn See Also added.
- 2 2022-05-22 16:30:21 3693,946 2,3693 By arvindpdmn Questions added.
- 1 2018-09-10 05:29:06 1,946 By gurumoorthyP First version
- Submitting ... You are editing an existing chat message. All Versions 2022-05-30 18:30:08 by arvindpdmn 2022-05-23 13:13:29 by arvindpdmn 2022-05-22 16:30:21 by arvindpdmn 2018-09-10 05:29:06 by gurumoorthyP All Sections Summary Discussion Sample Code References Milestones Tags See Also Further Reading

Systems are built from hardware and software components. Systems programming is about implementing these components, their interfaces and the overall architecture. Individual components perform their prescribed functions and at the same time work together to form a stable and efficient system.
Systems programming is distinct from application programming. System programs provide services to other software. Via abstractions, they expose API to simplify the development of applications. They're often optimized to low-level machine architecture. Unlike application software, most system software are not directly used by end users.
Assembly and C language have been historically used for systems programming. Go, Rust, Swift and WebAssembly are newer languages suited for systems programming.

Operating systems, device drivers, BIOS and other firmware, compilers, debuggers, web servers, database management systems, communication protocols and networking utilities are examples of system software. As part of operating systems, memory management, scheduling, event handling and many more essential functions are done by system software. Examples of application software are Microsoft Office, web browsers, games, and graphics software.
Application software generally don't directly access hardware or manage low-level resources. They do so via calls to system software. We may thus view system software as aiding application software with low-level access and management. Application developers can therefore focus on the business logic of their applications.
While application developers may not build system software, they can become better developers by knowing more about the design and implementation of system software. Specifically, by knowing and using system API s correctly they can avoid implementing similar functions in their applications.
For example, a C application on UNIX/Linux calls the system API getpid() . The OS creates the process, allocates memory and assigns a process identifier.

An operating system such as Linux is a collection of system programs. These deal with files and directories, manage processes for executable programs, enable I/O for those programs and allocate/release memory as needed. The OS manages users, groups and associated permissions. The OS prevents normal user programs from executing privileged operations. The shell is a special system program that allows users to interact with the system. If processes need to communicate or respond to external events, signals (aka software interrupts) facilitate this.
There are systems programs that transform other programs into machine-level instructions for execution: compilers, assemblers, macro processors, loaders and linkers. Their aim is to generate instructions optimized for speed or memory. Use of registers, loops, data structures, and algorithms are considered in these system programs.
Programming languages, editors and debuggers are also system programs. These are tools to write good and reliable system programs. They have to be easy to learn and productive for a developer while also being efficient and safe from a system perspective.
A system programmer is one who write system software and this task is called system programming or systems programming. But there's an older definition that's been used in the context of mainframes since the 1960s.
On a mainframe, a system programmer installs, upgrades, configures and maintains the operating system. She does capacity planning and evaluates new products. She's also skilled in optimizing the system for performance, troubleshooting problems and analyzing memory dumps.
On the other hand, a system administrator handles day-to-day operations such as adding/removing users, configuring access, installing software, and monitoring performance. She deals with applications whereas a system programmer is more well-versed with the mainframe hardware.
In small IT organizations, both roles may be performed by a single individual.
Wikipedia lists more than a dozen languages: C/C++, Ada, D, Nim, Go, Rust, Swift, and more. Notably, the following popular languages are absent: JavaScript, Java, C#, Python, Visual Basic, PHP, Perl, and Ruby. Implemented in Haskell, COGENT is a functional programming language that's also suited for systems programming.
System programming languages are required to provide direct access to hardware including memory and I/O access. Performance, explicit memory management and fine-grained control at bit level are essential capabilities. Where they also offer high-level programming constructs, system programming languages (C, Rust, Swift, etc.) are also used for application programming.
Since such languages give access to low-level hardware functions, there's a risk of introducing bugs. Rust was created to balance aspects of both safety and control. C sacrifices safety for control while Java does the opposite.
Scripting languages such as Python, JavaScript and Lua are not for systems programming. However, the introduction of static typing (for safety) and Just-in-Time ( JIT ) compilation (for speed) has seen these languages being used for systems programming.
On the web, applications adopt the client-server architecture. Server-side logic may be implemented as many microservices distributed on a cloud platform. Applications make use of API s served by different endpoints. In this context, we have systems programs that help create distributed applications for the cloud. System programs must be designed to address network topology changes, security concerns, high latency, and poor network connections.
Rob Pike commented that developers thought that Go was for systems programming. In fact, it was for writing any server-side code. Later he saw anything running on the cloud as systems software. Ousterhout commented in 1998 that on the web Java was being used for systems programming.
Bunardzic commented that "the only way to program a system is to program a network". Systems should be designed for concurrency, fault encapsulation/detection/recovery, upgrade without downtime, observability, and asynchronous communication. Developers who use system services and API s must be free to choose their own technology stack. One service shouldn't depend on others.
A systems programmer needs to know the system API s well. In addition, she should know how the OS kernel, programs and users interact with one another.
Designing a good system is not a one-time task. The system should be designed for iteration and incremental improvements. System designers must be open to feedback. Historically, many Linux system programmers blamed application developers for program crashes instead of seeing these as opportunities to improve the Linux kernel or system tools.
All assumptions must be made explicit. Systems software should get the abstractions right, minimize if not avoid leaky abstractions. In other words, its users shouldn't need to know implementation details. For instance, ORM frameworks that interface between applications and databases are often leaky due to a conceptual mismatch between objects and relations.
Before implementation, it's beneficial to do system modelling, analysis and simulations. Unified Modelling Language ( UML ) can help. Small and simple systems are amenable to formal analysis. Anything else, we need to apply statistical analysis. More components there are, more complex becomes the system.
Till early and even mid-1960s, the first concern in designing computer systems is the hardware itself. Programming them becomes a secondary concern. Programming techniques are chaotic. Often they're not as intended by the hardware designers. Systems programming as a discipline is only starting to emerge.

Shaw considers assemblers, interpreters, compilers, and monitors as translators ; that is, they translate code in one form to another. Referring to the figure, translator T translates A to B. He defines the following,
Systems Programming is the science of designing and constructing translators.
At the NATO Conference on Software Engineering, the merits of high-level languages are discussed: cost, maintainability, correctness. System programmers however object to high-level languages. They don't like anything to get in between themselves and the machine. Reconciling these two concerns is the main challenge in design a suitable systems programming language.
Unix operating system is invented at Bell Laboratories, first in assembly on PDP-7 (1969) and subsequently migrated to C on PDP-11 (1971). A decade later one of its inventors, Dennis Ritchie, comments that only the assembler is still written in assembler. Most other system programs are written in C language.

Researchers at the Carnegie-Mellon University invent a new systems programming language that they name BLISS . They describe it as a general purpose high-level language for writing large software systems for specific machines. They enumerate the requirements of any good systems programming language: space/time economy, access to hardware features, data structures, control structures, understandability, debugging, etc. The figure shows an example of how BLISS enables bit-level access. Such low-level access is typical of systems software.
Weicker proposes Dhrystone as a benchmark for systems programming. Currently we have the Whetstone benchmark that's tuned to measure floating-point arithmetic. Systems programs often use enumerations, records and pointer data types. Compared to numerical programs, systems programs have fewer loops, simpler compute statements, more conditional branching and more procedure calls. The Dhrystone benchmark accounts for these.
An IBM research report details the challenges and pitfalls in programming for a multi- CPU and multi-threaded environment. They refer to the System/370 architecture. Shared memory and data structures have to be handled carefully. Therefore, parallelism is a new concern for systems programming. However, multi-programming was considered in the design of Unix back in the early 1970s.
This decade sees the wide adoption of scripting languages such as Perl, Tcl, Ruby, PHP, Python and JavaScript. They're seen as languages that "glue together" various components whereas systems programming languages are used to create those components. In the 2010s, the boundaries blur as some scripting languages are used to build large systems software.
Wolfe proposes changes to how systems programming must be taught to students. The curriculum would include small challenges in various aspects of systems programming and not just focus on assemblers and compilers. Currently, students perceive systems programming as boring, the techniques themselves stale, and the courses disconnected from systems programming jobs out there.
Brewer et al. note that 35 years after the invention of C language, we still don't have a suitable alternative for systems programming. Shapiro voices a similar complaint in 2006. Advances in programming languages have not motivated systems programmers to adopt them.
Mozilla begins sponsoring the development of Rust . Rust is announced to the world in 2010. The first stable release of the language happens in May 2015. Today Rust is well-recognized as a systems programming language.
Crichton at Stanford University proposes that students of programming languages must be taught systems programming. Courses must not be about theory and formal methods alone. They should include practical programming while also providing effective mental models of computation and formal reasoning. He includes WebAssembly and Rust in the proposed curriculum.
- Beck, Leland L. 1997. "System Software: An Introduction to Systems Programming." Third Edition, Addison-Wesley. Accessed 2022-05-23.
- Bunardzic, Alex. 2022. "An open source developer's guide to systems programming." Opensource.com, April 29. Accessed 2022-05-23.
- Crichton, Will. 2018. "What is Systems Programming, Really?" September 9. Accessed 2022-05-23.
- Crichton, W. 2019. "From Theory to Systems: A Grounded Approach to Programming Language Education." arXiv, v1, April 14. Accessed 2022-05-23.
- Donovan, John J. 1972. "Systems Programming." Tata McGraw-Hill Edition (1991), The McGraw-Hill, Inc. Accessed 2022-05-23.
- Eberhardt, Colin. 2022. "WebAssembly & Modern Systems Programming Languages." QCon London, May 12. Accessed 2022-05-24.
- Encyclopaedia Britannica. 2021. "systems programming." Encyclopaedia Britannica, August 2. Accessed 2022-05-23.
- Farkas, T., C. Neumann, and A. Hinnerichs. 2009. "An Integrative Approach for Embedded Software Design with UML and Simulink/" 33rd Annual IEEE International Computer Software and Applications Conference, pp. 516-521. doi: 10.1109/COMPSAC.2009.185. Accessed 2022-05-30.
- GoLang Docs. 2020. "System programming in Go - 1." GoLang Docs, September 17. Accessed 2022-05-24.
- IBM. 2008. "Mainframe concepts." z/OS Basic Skills Information Center, IBM Corporation. Accessed 2022-05-23.
- Jung, Ralf, Jacques-Henri Jourdan, Robbert Krebbers, and Derek Dreyer. 2021. "Safe Systems Programming in Rust." Communications of the ACM, vol. 64, no. 4, pp. 144-152, April. Accessed 2022-05-24.
- Kerr, Luka. 2020. "Extending a Purely Functional Language to Enable Low-Level Systems Programming." B.E. Thesis, The University of New South Wales, December 11. Accessed 2022-05-23.
- Li, Peng. 2004. "Safe Systems Programming Languages." Department of Computer and Information Science, University of Pennsylvania, October 6. Accessed 2022-05-23.
- Lithmee. 2018. "Difference Between System Software and Application Software." Pediaa, June 22. Accessed 2022-05-24.
- Love, Robert. 2013. "Linux System Programming." Second Edition, O'Reilly. Accessed 2022-05-23.
- Madunuwan, Dumindu. 2021. "Why Rust?" Learning Rust, April 27. Accessed 2022-05-30.
- McDaniel, Patrick. 2015. "Module: Systems Programming." CMPSC 311- Introduction to Systems Programming, Penn State Univ. Accessed 2022-05-23.
- PCMag. 2022. "System software." Encyclopedia, PCMag. Accessed 2022-05-26.
- Perkins, C. 2012. "Evolution of Systems Programming." Lecture 11 in Advanced Operating Systems, School of CS, Accessed 2022-05-23.
- Ritchie, Dennis M. 1984. "The Evolution of the Unix Time-sharing System." Lucent Technologies Inc. Accessed 2022-05-23.
- Shapiro, Jonathan. 2006. "Programming language challenges in systems codes: why systems programmers still use C, and what to do about it." PLOS '06: Proceedings of the 3rd workshop on Programming languages and operating systems: linguistic support for modern operating systems, October. doi: 10.1145/1215995.1216004. Accessed 2022-05-30.
- Shaw, Alan C. 1966. "Lecture notes on a course in systems programming." Technical Report No. 52, CS Dept, Stanford University, December 9. Accessed 2022-05-23.
- Suda, Jon. 2015. "Stop Leak." Blog, Jon's Musings, July 25. Accessed 2022-05-30.
- Swift. 2022. "About Swift." Swift. Accessed 2022-05-26.
- TIOBE. 2022. "TIOBE Index for May 2022." TIOBE. Accessed 2022-05-30.
- Techopedia. 2015. "System Programming." Techopedia, September 28. Accessed 2022-05-23.
- Treiber, R. Kent. 1986. "Systems Programming: Coping with Parallelism." Research Report, RJ 5118, IBM Almaden Research Center, April 23. Accessed 2022-05-23.
- Watts, Stephen. 2020. "What is Systems Programming?" Blog, BMC, April 24. Accessed 2022-05-23.
- Weicker, Reinhold P. 1984. "Dhrystone: a synthetic systems programming benchmark." Communications of the ACM, vol. 27, no. 10, pp. 1013-1030, October. Accessed 2022-05-23.
- Weicker, R. P. 1990. "An Overview of Common Benchmarks." IEEE Computer, vol. 23, no. 12, pp. 65-75, 1990, doi: 10.1109/2.62094. Accessed 2022-05-23.
- Weiss, Stewart. 2020. "Chapter 1: Introduction to System Programming." Lecture notes, UNIX Application and System Programming, Department of Computer Science, Hunter College. Accessed 2022-05-23.
- Wikipedia. 2022. "Systems programming language." Wikipedia, April 22. Accessed 2022-05-23.
- Wolfe, James L. 1992. "Reviving systems programming." ACM SIGCSE Bulletin, vol. 24, no. 1, pp. 255–258, March. Accessed 2022-05-23.
- Wulf, W.A., D.B. Russell, and A.N. Habermann. 1971. "BLISS: A Language for Systems Programming." Communications of the ACM, vol. 14, no. 12, pp. 780-790, December. Accessed 2022-05-23.
Further Reading
- Robbins, Kay A., and Steven Robbins. 2003. Unix™ Systems Programming: Communication, Concurrency, and Threads." Pearson. Accessed 2022-05-23.
Article Stats
Author-wise stats for article edits.
Article Warnings
- Readability score of this article is below 50 (48). Use shorter sentences. Use simpler words.
- Browse Articles
- Community Outreach
- About Devopedia
- Author Guidelines
- FAQ & Help
- Forgot your password?
- Create an account
Free On-line Version
Print version, announcements, 2019-2020 early adopters, current adopters, mailing list, dive into systems.
Suzanne J. Matthews , West Point Tia Newhall , Swarthmore College Kevin C. Webb , Swarthmore College
Dive into Systems is a free, online textbook that serves as a gentle introduction to computer systems, computer organization, and parallel computing. The book is intended for an audience that has only a CS1 background. It guides readers through a vertical slice of a computer to develop an understanding of a variety of systems topics, including:
how a computer runs a program, from a program expressed in a high-level language to low-level binary representation and circuits
programming in C and Assembly (assuming a CS1 background)
introduction to operating systems and the systems costs that affect program performance (the memory hierarchy, caching, and code optimization)
introduction to parallel computing with shared memory and pthreads
Dive into Systems is designed to be present topics in as independent manner as possible so that it can be used as a primary textbook for a wide range of introductory-level computer systems courses, or as a supplemental background textbook for upper-level courses that cover Operating Systems, Computer Architecture, Compilers, Networks, Databases, and Parallel Computing.
Dive into Systems includes one or more chapters on the following topis: Introduction to Computer Systems ; C Programming (covers most of the C language, debugging with gdb and valgrind, and code optimization); Computer Organization and Architecture (includes binary representation, computer architecture, memory hierarchy, and caching); Assembly Programming (covers 64-bit x86, 32-bit x86, and 64-bit ARM); The Operating System ; and Parallel Computing (focus on shared memory and threads, and also looking ahead to others).
Read The Book
Our textbook is available free, on-line in two different formats (mult-page, and single page). Additionally, a low-cost print version of our textbook is available from No Starch Press (note that our textbook will always remain free on-line here ). Instructors, if you are using our textbook for your course, please let us know (please email us at [email protected] sharing this information with us).
|
|
This is release of Version 1.2 of the Dive into Systems textbook that was updated on August 25, 2023 . This version includes two new appendices and links to early versions of interactive exercises.
The two Appendices added since Version 1.0 of our book are:
Appendix 1: "Chapter 1 for Java Programers" . This is a version of Chapter 1 that uses Java code examples to compare to C code (Python examples are used in Chapter 1).
Appendix 2: "Using Unix" . This starts with the basics of Unix command line and Unix file system, and then covers a wide range of Unix commands and utilities (e.g., tar, make and Makefiles, editors, chmod, ssh, man, io redirection, …). It also introduces some more advanced features like pipes, getting system state, and writing shell scripts. With each topic we include links to resources for further information.
If you find any errors, typos, etc., please contact us. We appreciate your feedback!
Instructors: if you are using our textbook for your course, please let us know. Please email us at [email protected] sharing this information with us.

A low cost print version of our textbook is available by purchace directly from No Starch Press , and from numerous other sellers including Amazon .
Please keep in mind that the online version of our textbook will always remain free from our website.
Dive into Systems Print Version , No Starch Press, August 2022 (ISBN-13: 9781718501362).
Book Activities
We are delighted to announce our NSF sponsored project to add interactive content to our textbook . As part of this effort we are seeking community help to create and add dynamic visualizations, interactive exercises, and worked examples to augment our textbook with online resources that will include exercises for students and supplemental resources for instructors.
To learn about recruting and events associated with this project, and to hear about other information about and updates to our book, please subscribe to our low-volume Mailing List .
SIGCSE'24 Affiliated Event: Building interactivity into Dive into Systems . Wednesday, March 20, 2023 , 1-5:45 PM, See the link for more details, and to fill out the RSVP form to register for this event.
Past Events/Presentations
SIGCSE'23 Affiliated Event: Building interactivity into Dive into Systems . Wednesday, March 15, 2023, Toronto, CA. ( program link )
Presentation, CCSC Eastern'22 : " Adding Interactive Content to Dive into Systems, a free online textbook for introducing students to computer systems ". ( talk slides )
Panel: " How do you write an open-access textbook and why should you do it? ". Panelists: Carmelo Galanti, Temple University, Donald Wargo, Temple University, Tia Newhall, Swarthmore College. Moderated by Suzanne J. Matthews, West Point. Oct. 13, 2022, Friends Center, Philadelphia, PA. Sonsored by the Aydolotte Foundation and Swarthmore College Libraries.
Presentation, SIGCSE'21 : " Dive into Systems: A Free, Online, Textbook for Introducting Computer Systems ". ( open access paper , talk slides )
Panel, SIGCSE'21 : " TextbooksForAll: Free textbooks and their place in computer science education ". Suzanne Matthews, Chris Mayfield, Remzi Arpaci-Dusseau, Kevin Webb. ( abstract )
See our open-access paper from SIGCSE'21 for more information about our textbook, including an evaluation from student and faculty participants in our 2019-2020 Early Adopters Program:
"Dive into Systems: A Free, Online Textbook for Introducing Computer Systems" , Suzanne J. Matthews, Tia Newhall, Kevin C. Webb. In Proceedings of the 52nd ACM Technical Symposium on Computer Science Education (SIGCSE '21), March, 2021.
"A Free Online Textbook Introducting Computer Architecture Topics", Tia Newhall, Suzanne Matthews, Kevin Webb. In Proceedings of the Workshop on Computer Architecture Education ( WCAE'23 ) in conjunction with the 50th International Symposium on Computer Architecture ( ISCA ), June 2023.
Using Dive into Systems
Everyone is free to use Dive into Systems in their course! The book will remain free online. If you are using Dive into Systems at your institution, please reach out and let us know ( [email protected] )! This information will really help us continue to expand the book.
Dive into Systems was first piloted as a textbook in the Computer Organization course at West Point in Fall 2018 and in the ( Intro to Computer Systems ) at Swarthmore College in Spring 2019. In Fall 2019, Dive into Systems launched its Early Adopter Program, which enabled faculty around the United States to pilot the stable release of Dive into Systems at their institutions. The Early Adopter Program was a huge help to the authors, as it helped us get valuable insight into student and faculty experiences with the textbook. We used the feedback we receive to improve and strengthen the content of Dive into Systems , and are very thankful to everyone who completed our student and faculty surveys.
The following individuals piloted Dive into Systems as a textbook at their institutions during the 2019-2020 Academic Year:
John Barr (Ithaca College) - Computer Organization & Assembly Language (Comp 210)
Chris Branton (Drury University) - Computer Systems Concepts (CSCI 342)
Dick Brown (St. Olaf College) - Hardware Design (CSCI 241)
David Bunde (Knox College) - Introduction to Computing Systems (CS 214)
Bruce Char (Drexel University) - Systems Programming (CS 283)
Bryan Chin (U.C. San Diego) - Computer Organization and Systems Programming (CSE 30)
Stephen Carl (Sewanee: The University of the South) - Computer Systems and Organization (CSci 270)
John Dougherty (Haverford College) - Computer Organization (cs240)
John Foley (Smith College) - Operating Systems (CSC 262)
Elizabeth Johnson (Xavier University) - Programming in C
Bill Kerney (Clovis Community College) - Assembly Programming (CSCI 45)
Deborah Knox (The College of New Jersey) - Computer Architecture (CSC 325)
Doug MacGregor (Western Colorado University) - Operating Systems/Architecture (CS 330)
Jeff Matocha (Ouachita Baptist University) - Computer Organization (CSCI 3093)
Keith Muller (U.C. San Diego) - Computer Organization and Systems Programming (CSE 30)
Crystal Peng (Park University) - Computer Architecture (CS 319)
Leo Porter (U.C. San Diego) - Introduction to Computer Architecture (CSE 141)
Lauren Provost (Simmons University) - Computer Architecture and Organization (CS 226)
Kathleen Riley (Bryn Mawr College) - Principles of Computer Organization (CMSC B240)
Roger Shore (High Point University) - Computer Systems (CSC-2410)
Tony Tong (Wheaton College, Norton MA) - Advanced Topics in Computer Science: Parallel and Distributed Computing (COMP 398)
Brian Toone (Samford University) - Computer Organization and Architecture (COSC 305)
David Toth (Centre College) - Systems Programming (CSC 280)
Bryce Wiedenbeck (Davidson College) - Computer Organization (CSC 250)
Richard Weiss (The Evergreen State College) - Computer Science Foundations: Computer Architecture (CSF)
The following institutions are currently using Dive into Systems . If you don’t see your institution listed, please reach out to us ( [email protected] )!
U.S. Adopters
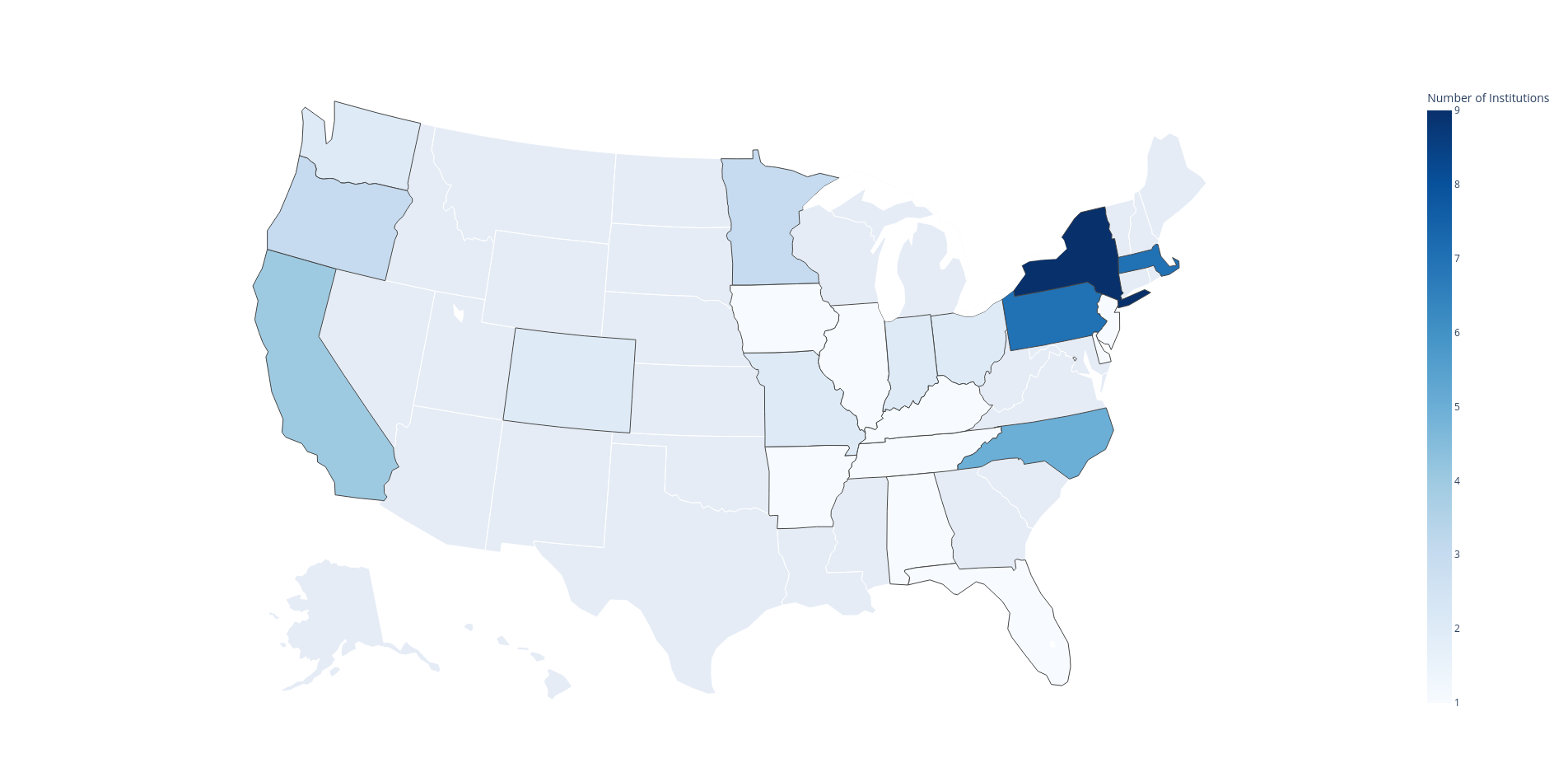
International Adopters
NYU Paris - Paris, FR
Polish-Japanese Academy of Computer Science - Warsaw, PO
To hear announcements and updates related to the textbook, please consider joining our low-volume mailing list .
If you have any questions, comments or want to see your institution listed, please e-mail us at [email protected]
You are using an outdated browser. Please upgrade your browser to improve your experience.
Your browser does not support the HTML5 canvas. Please upgrade your browser to improve your experience.
An open source developer's guide to systems programming

Programming is an activity that helps implement a model. What is a model? Typically, programmers model real-world situations, such as online shopping.
When you go shopping in the real world, you enter a store and start browsing. When you find items you'd like to purchase, you place them into the shopping cart. Once your shopping is done, you go to the checkout, the cashier tallies up all the items, and presents you with the total. You then pay and leave the store with your newly purchased items.
Thanks to the advancements in technology, you can now accomplish the same shopping activities without traveling to a physical store. You achieve that convenience by having a team of software creators model actual shopping activities and then simulate those activities using software programs.
Such programs run on information technology systems composed of networks and other computing infrastructure. The challenge is to make a reliable system in the presence of failures.
Why failures?
The only way to offer virtual capabilities such as online shopping is to implement the model on a network (i.e., the internet). One problem with networks is that they are inherently unreliable. Whenever you plan to implement a network app, you must consider the following pervasive problems:
- The network is not reliable.
- The latency on the network is not zero.
- The bandwidth on the network is not infinite.
- The network is not secure.
- Network topology tends to change.
- The transport cost on the network is not zero.
- The network is not homogenous.
- "Works on my machine" is not a proof that the app is actually functional.
As can be seen from the above list, there are many reasons to expect failures when planning to launch an app or service.
What is a system?
You depend on a system to support the app. So, what is a system?
A system is something that stands together, meaning it's a composition of programs that offer services to other programs. Such a design is loosely coupled. It is distributed and decentralized (i.e., it does not have global supervision/management).
What is a reliable system?
Consider the attributes that make up a reliable system:
- A reliable system is a system that is always up and running. Such a system is capable of graceful degradation, meaning that when performance starts to degrade, the system will not suddenly stop working.
- A reliable system is not only always up and running, but it is also capable of progressive enhancement. As the demand for the system's capabilities increases, a reliable system scales to meet the needs.
- A reliable system is also easily maintainable without expensive changes.
- A reliable system is low-risk. It is safe and simple to deploy changes to such a system, either by rolling back or forward.
Everything built eventually exceeds the ability to understand it
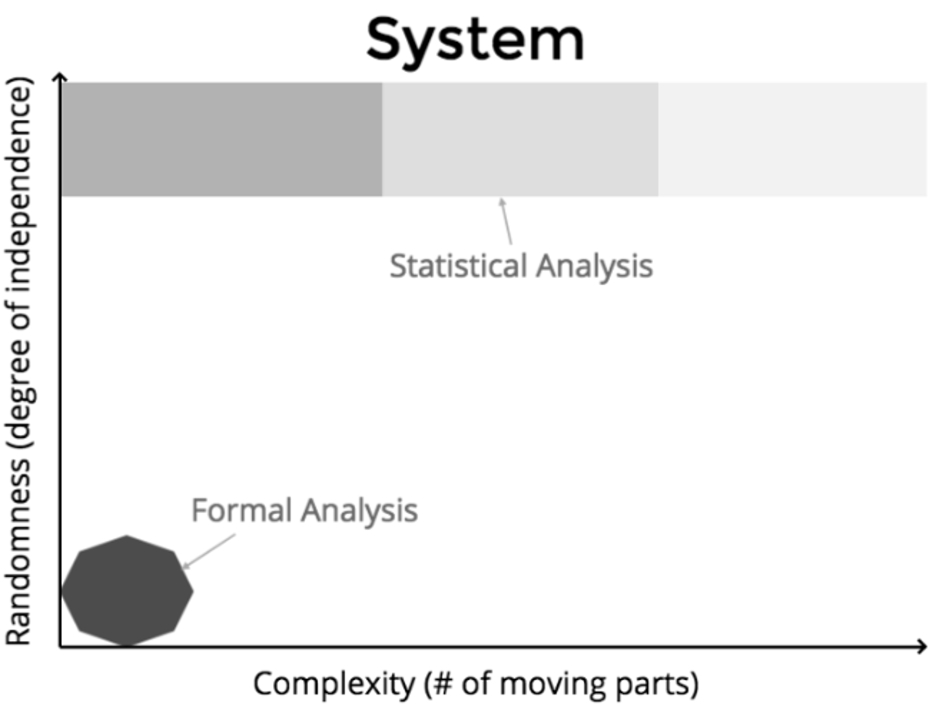
Every successful system was created from a much simpler design. As systems are enhanced and embellished, they eventually reach a point where their complexity cannot be easily understood.
Consider a system that consists of many moving parts. As the number of moving parts in the system increases, the degree of interdependence between those moving parts also increases (Figure 1).
(Alex Bunardzic, CC BY-SA 4.0)
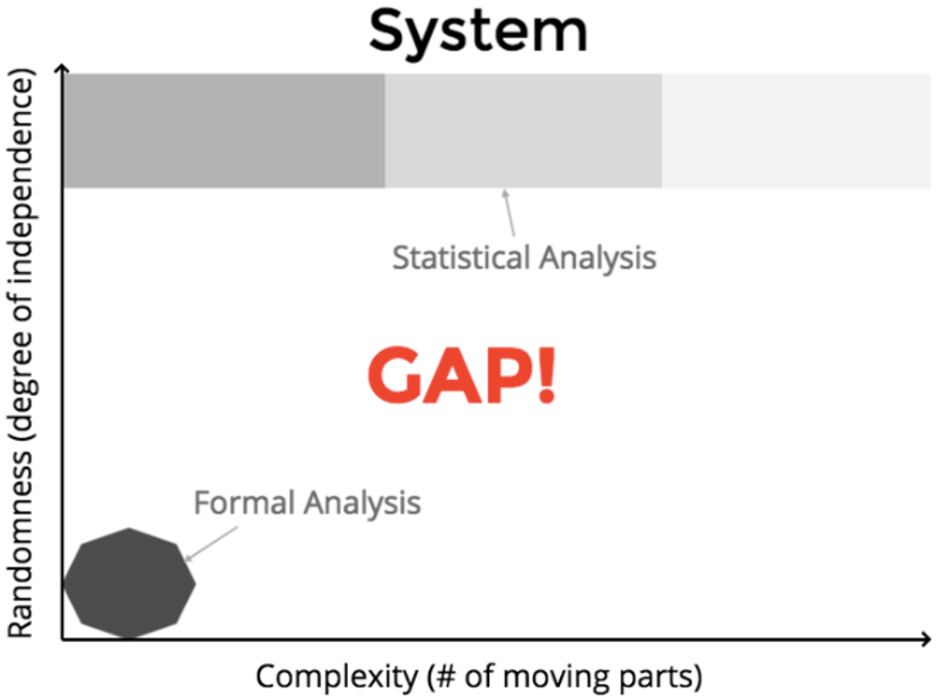
It is only during the early stages of the growth of that system that people can perform a formal analysis of the system. After a certain point of system complexity, humans can only reason about the system by applying statistical analysis.
There is a gap between formal analysis and statistical analysis (Figure 2).
How to program a system?
Developers know how to write useful apps, but they must also know how to program a system that enables the app to function on the network.
It turns out that there doesn't seem to be a system programming language available. While developers may know many programming languages (e.g., C, Java, C++, C#, Python, Ruby, JavaScript, etc.), all those languages specialize in modeling and emulating the functioning of an app. But how does one model system functionality?
Look at how the system is assembled. Basically, in a system, programs talk to each other. How do they do that?
They communicate over a network. Since there cannot be a system without two or more programs talking to each other, it is clear that the only way to program a system is to program a network.
Before looking more closely at how to program a network, I will examine the main problem with networks—failure.
Failures are at the system level
How do failures occur in a system? One way is when one or more programs suddenly becomes unavailable.
That failure has nothing to do with programming errors. Actually, programming errors are not really errors—they are bugs to be squashed!
A network is basically a chain, and as everyone knows, a chain is only as strong as its weakest link.
When a link breaks (i.e., when one of the programs becomes unavailable), it is critical to prevent that outage from bringing the entire system down.
How do administrators do that? They provide an abstraction boundary that stops the propagation of errors. I will now examine ways to provide such an abstraction boundary inside the system. Doing that amounts to programming a system.
Best practices in system programming
It is very important to design programs and services to meet the needs of the machines. It is a common mistake to create programs and services to serve human needs. But when doing systems programming, such an approach is incorrect.
There is a fundamental difference between designing services for machines versus humans. Machines do not need operational interfaces. However, humans cannot consume services without a functional interface.
What machines need is programming interfaces. Therefore, when doing systems programming, focus entirely on the application programming interfaces (APIs). It will be easy to bolt operational interfaces on top of the already implemented programming interfaces, so do not rush into creating operational interfaces first.
It is also important to build only simple services. This may seem unreasonable at first, but once you understand that simple services are easily composable into more complex ones, it makes more sense.
Why are simple services so essential when doing systems programming? By focusing on simple services, developers minimize the risk of slipping into premature abstraction. It becomes impossible to over-abstract such simple services. The result is a system component that is easy to make, reason about, deploy, fix, and replace.
Developers must avoid the temptation to turn the service into a monolith. Abstain from doing that by refusing to add functionalities and features. Furthermore, resist turning service into a stack. When other users (programs) decide to use the services the component offers, they should be free to choose commodities suitable for the consumption of the services.
Let the service users decide which datastore to use, which queue, etc. Programmers must never dictate a custom stack to clients.
Services must be fully isolated and independent. In other words, services must remain autonomous.
Value of values
What is a value in the context of programming? The following attributes characterize a value:
- No identity
- On the wire
Consider an example value of a service that returns the total monthly service charge. Suppose a customer receives $425.00 as a monthly service charge. What are the characteristics of the value $425.00?
- It has no identity.
- No name – it is just four hundred twenty-five dollars—no need for a separate name.
- It is ephemeral – as the time progresses, the monthly charge keeps changing.
- It is always sent on a wire and received by the client.
The ephemeral nature of values implies flow.
Systems are not place-oriented
A place-oriented product could be depicted as a ship being built in a shipyard.
Systems are flow-oriented
For example, cars are built on a moving assembly line.
How do values flow in the system?
Values undergo transformations and are moved, routed, and recorded.
- Keep the above activities segregated
How do values move in the system?
- Source => destination
- Mover (producer) depends on identity/availability
- Must decouple producers from consumers
- Must remove dependency on identity
- Must remove dependency on availability
- Use queues Pub/sub
It is essential to avoid dependencies for values to flow effectively through the system. Brittle designs include processes that count on a certain service being found by its identity or requiring a certain service to be available. The only robust design that allows values to flow through the system is using queues to decouple dependencies. It is recommended to use the publish/subscribe queuing model.
Design services primarily for machines
Avoid designing services to be consumed by humans. Machines should never be expected to access services via operational interfaces. Build human operational interfaces only after you've built a machine-centric service.
Strive to build only simple services. Simple services are easily composable. When designing simple services, there is no danger of premature abstraction.
It is not possible to over-abstract a simple service.
Avoid turning a service into a monolith
Abstain from adding functionality and features (keep it super simple). Avoid at all costs turning a service into a stack. Allow service users to choose which commodities to use when consuming them. Let them decide which datastore to use, which queue, etc. Don't dictate your custom stack to clients.
System failure model is the only failure model
Next, acknowledge that system failures are guaranteed to happen! It is not the question of if but when and how often.
When do exceptions occur? Any time a runtime system doesn't know what to do, the result is an exception and a system failure.
Those failures are different from programming errors. The errors occur when a team makes mistakes while implementing the processing logic (developers call those errors "bugs").
Whenever a system fails, notice that it is partial and uncoordinated. It is improbable that the entire system would fail at once (almost impossible for such an event to happen).
Minimum requirements for reliable systems
At a minimum, a reliable system must possess the following capabilities:
Concurrency
Fault encapsulation, fault detection, fault identification, hot code upgrade, stable storage, asynchronous message passing.
I'll examine those attributes one by one.
For the system to be capable of handling two or more processes concurrently, it must be non-imperative. The system must never block the processing or apply the "pause" button on the process. Furthermore, the system must never depend on a shared mutable state.
In a concurrent system, everything is a process. Therefore, it is paramount that a reliable system must have a lightweight mechanism for creating parallel processes. It also must be capable of efficient context switching between processes and message passing.
Any process in a concurrent system must rely on fault detection primitives to be able to observe another process.
Faults that occur in one process must not be able to damage/impair other processes in the system.
"The process achieves fault containment by sharing no state with other processes; its only contact with other processes is via messages carried by a kernel message system." - Jim Gray
Here is another useful quote from Jim Gray:
"As with hardware, the key to software fault-tolerance is to hierarchically decompose large systems into modules, each module being a unit of service and a unit of failure. A failure of a module does not propagate beyond the module."
To achieve fault tolerance, it is necessary to only write code that handles the normal case.
In case of a failure, the only recommended course of action is to let it crash! It is not a good practice to fix the failure and continue. A different process should handle any error (the escalation error handling model).
It is crucial to constantly ensure clean separation between error recovery code and normal case code. Doing so greatly simplifies the overall system design and system architecture.
A programming language must be able to detect exceptions both locally (in the process where the exception occurred) and remotely (seeing that an exception occurred in a non-local process).
A component is considered faulty once its behavior is no longer consistent with its specification. Error detection is an essential component of fault tolerance.
Try to keep tasks simple to increase the likelihood of success.
In the face of failure, administrators become more interested in protecting the system against damage than offering full service. The goal is to provide an acceptable level of service and become less ambitious when things start to fail.
Try to perform a task. If you cannot perform a task, try to perform a simpler task.
You should be able to identify why an exception occurred.
The ability to change code as it is executing and without stopping the system.
Developers need a stable error log that will survive a crash. Store data in a manner that survives a system crash.
Asynchronous message passing should be the default choice for inter-service communication.
Well-behaved programs
A system should be composed of well-behaved programs. Such programs should be isomorphic to the specification. If the specification says something silly, then the program must faithfully reproduce any errors in the specification. If the specification doesn't say what to do, raise an exception!
Avoid guesswork—this is not the time to be creative.
"It is essential for security to be able to isolate mistrusting programs from one another, and to protect the host platform from such programs. Isolation is difficult in object-oriented systems because objects can easily become aliased (i.e., at least two or more objects hold a reference to an object)" -Ciaran Bryce
Tasks cannot directly share objects. The only clean way for tasks to communicate is to use a standard copying communication mechanism.
Applications run on systems and understanding how to properly program systems is a critical skill for developers. Systems include reliability and complexity that are best managed using a series of best practices. Some of these include:
- Processes are units of fault encapsulation.
- Strong isolation leads to autonomy.
- Processes do what they are supposed to do or fail as soon as possible (fail fast).
- Allowing components to crash and then restart leads to a simpler fault model and more reliable code. Failure, and the reason for failure, must be detectable by remote processes.
- Processes share no state, but communicate by message passing.

Comments are closed.
Related content.

Hands-On System Programming with Go by Alex Guerrieri
Get full access to Hands-On System Programming with Go and 60K+ other titles, with a free 10-day trial of O'Reilly.
There are also live events, courses curated by job role, and more.
An Introduction to System Programming
This chapter is an introduction to system programming, exploring a range of topics from its original definition to how it has shifted in time with system evolution . This chapter provides some basic concepts and an overview of Unix and its resources, including the kernel and the application programming interfaces ( API ). Many of these concepts are defined here and are used in the rest of the book.
The following topics will be covered in this chapter:
- What is system programming?
- Application programming interfaces
- Understanding how the protection ring works
- An overview of system calls
- The POSIX standard
Get Hands-On System Programming with Go now with the O’Reilly learning platform.
O’Reilly members experience books, live events, courses curated by job role, and more from O’Reilly and nearly 200 top publishers.
Don’t leave empty-handed
Get Mark Richards’s Software Architecture Patterns ebook to better understand how to design components—and how they should interact.
It’s yours, free.

Administrative Information
MW 10:00AM-10:50AM, Friend Center 101
To make the lectures more interactive, we will be using iClickers . Any hardware version is suitable.
The best way to get a spot in the precept of your choice is to regularly check the registrar's Course Offerings page and/or the listings on TigerHub. In our experience, more than a quarter of the total class enrollment changes precepts during shopping period. Please direct further questions concerning your precept assignment to Colleen Kenny , the CS Department's Undergraduate Coordinator. Colleen's contact information is provided later on this page. The course's teaching staff cannot manage precept assignments.
| 1 | MW 1:30PM-2:20PM | Friend Center 009 | Xiaoyan Li |
| 2 | MW 3:30PM-4:20PM | Friend Center 009 | Xiaoyan Li |
| 3 | MW 7:30PM-8:20PM | Friend Center 009 | Alberto Mizrahi Benmaman |
| 4 | TTh 12:30PM-1:20PM | Friend Center 009 | Donna Gabai |
| 5 | TTh 1:30PM-2:20PM | Friend Center 009 | Donna Gabai |
| 6 | TTh 3:30PM-4:20PM | Friend Center 009 | Josh Zhang |
Office hours have changed for Reading Period. Check Piazza!
Lead instructor.
Christopher Moretti, Ph.D. : 036 Corwin Hall : [email protected]
Office Hours: T 2:00PM-4:00PM and Th 10:00AM-12:00PM in 036 Corwin Hall
Lead Preceptor
Xiaoyan Li, Ph.D. : 221 Nassau Street, Room 104 : [email protected]
Office Hours: W 4:30PM-6:30PM and Th 2:00PM-4:00PM in 221 Nassau Street, Room 104
Faculty Preceptor
Donna Gabai : 039 Corwin Hall : [email protected]
Office Hours: F 11:00AM-1:00PM and Su 1:00PM-3:00PM in 039 Corwin Hall
Graduate Student Preceptors
Alberto Mizrahi Benmaman : [email protected]
Office Hours: M 5:00PM-7:00PM in Friend Center 010
Josh Zhang : [email protected]
Office Hours: T 4:30PM-6:30PM in Friend Center 010
Undergraduate Graders
Christine Cho, Katie Dykstra, Cristina Hain, Jacqueline He, Hannah Huh, Nabhonil Kar, James Lee, Austin Li, Ethan Li, Drew Limpasuvan, Nicole Meister, Vikash Modi, Tommy Nguyen, Claudia Popescu, Grace Wei, Daniel Wey, Mona Ye
Undergraduate Coordinator
Colleen Kenny : CS Building 210 : [email protected]
Lab Teaching Assistants
Available in rooms Lewis Library 121 and Lewis Library 122. A lab teaching assistant schedule provides details.
Prerequisites
COS 126. More specifically, you should have substantial programming experience using some high-level programming language such as Java. Prior experience with the C programming language is helpful but not essential.
Textbooks and Other Reading
The course uses these textbooks and manuals:
Required Textbooks
C Programming: A Modern Approach (Second Edition) , K. N. King, Norton & Co. 2008. The book covers the C programming language and advanced C programming.
ARM 64-bit Assembly Language , Larry Pyeatt with William Ughetta. The book covers the ARMv8 assembly language.
Those books are available in the University bookstore and is on reserve in the Engineering Library.
Highly Recommended Textbooks
The Practice of Programming , Brian W. Kernighan and Rob Pike, Addison-Wesley 1999. The book covers program and programming style. Many of the lectures in the first half of the course are derived, in part, from this book.
Computer Systems: A Programmer's Perspective (Third Edition) , Randal E. Bryant and David R. O'Hallaron, Prentice-Hall 2015. The book covers computer systems from the point of view of a C programmer. In particular, it covers x86-64 architecture and assembly language and the Linux operating system. The most important chapters of the book are available through Blackboard in the Course Materials section.
Those books are available in the University bookstore and are on reserve in the Engineering Library.
Recommended Textbook
Linux Pocket Guide , Daniel J. Barrett, O'Reilly 2012 (or 2004). The book covers the most fundamental aspects of the Linux operating system and the Bash shell from the user's point of view. One important section of the book is available through Blackboard in the Course Materials section.
Reference Manuals
The course uses these manuals, for reference only:
ARMv8 Instruction Set Overview
ARM Architecture Reference Manual
Academic Regulations
Please study the course Policies , especially those regarding collaboration on assignments.

- Get started with computers
- Learn Microsoft Office
- Apply for a job
- Improve my work skills
- Design nice-looking docs
- Getting Started
- Smartphones & Tablets
- Typing Tutorial
- Online Learning
- Basic Internet Skills
- Online Safety
- Social Media
- Zoom Basics
- Google Docs
- Google Sheets
- Career Planning
- Resume Writing
- Cover Letters
- Job Search and Networking
- Business Communication
- Entrepreneurship 101
- Careers without College
- Job Hunt for Today
- 3D Printing
- Freelancing 101
- Personal Finance
- Sharing Economy
- Decision-Making
- Graphic Design
- Photography
- Image Editing
- Learning WordPress
- Language Learning
- Critical Thinking
- For Educators
- Translations
- Staff Picks
- English expand_more expand_less
Computer Programming Basics - Introduction to Computer Programming
Computer programming basics -, introduction to computer programming, computer programming basics introduction to computer programming.

Computer Programming Basics: Introduction to Computer Programming
Lesson 1: introduction to computer programming, introduction to programming.
Computer programming is the process of designing and writing computer programs . As a skill set, it includes a wide variety of different tasks and techniques, but our tutorials are not intended to teach you everything. Instead, they are meant to provide basic, practical skills to help you understand and write computer code that reflects things you see and use in the real world.
What you need to know
Our computer programming tutorials assume that you have no programming experience whatsoever. They do, however, require basic familiarity with the use of computers and web browsers. For example, you should be comfortable downloading and opening files, and using text editing software. If you don't feel confident in those skills, consider spending some time with these tutorials first:
- Computer Basics
- Internet Basics
As long as you are comfortable with those basics, you should be prepared to begin learning programming.
What these tutorials will cover
These tutorials focus on one particular type of programming: web development . When you visit websites , whether you use a laptop, a smartphone, or anything else, you're actually looking at computer code , which a web developer likely wrote, and which your web browser is interpreting to show you what you see on the screen.
These tutorials will show you how to begin writing three common types of code used in web development, which combined make up the average website that you see every day: HTML , CSS , and JavaScript .
Parts of a website
Imagine that every website you visit is a person. Every person is different in how they look, act, and speak, but they're generally made up of the same basic pieces.
If you imagine a website as a person, you can think of HTML as being the skeleton.
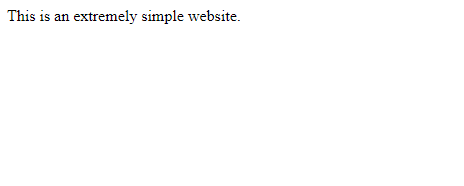
HTML is at the center of almost everything you see on the Internet. While it doesn't look like much on its own, it forms the building blocks on top of which all the other pieces rest. The HTML for an extremely simple website might look something like this:
And if you loaded that in your browser, you'd see this:
Try it yourself!
You can test some HTML yourself. Use this as a starting example:
Try entering that HTML in the input box below, then press the "View HTML" button. Make sure to type it in exactly as you see it.
You should see a button with the text you entered appear in the box above. It looks fairly plain, and it doesn't do anything yet, but you will learn about that later!
Congratulations, you just wrote HTML!
If HTML is the skeleton, you can think of CSS as making up all the muscle, skin, and so on that make a person actually look like a person.

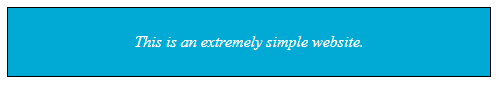
CSS doesn't do anything on its own. Instead, it takes plain HTML and styles it to look different . It can make what you see in the browser bigger or smaller, reorganize the pieces on the page, add colors, and more. Some CSS for an extremely simple website might look something like this:
If you were to apply the above CSS to the same extremely simple website you saw before, it would look like this:
You can test that CSS yourself. Use this as a starting example:
Try entering that snippet of CSS in the input box below, then press the "Update CSS" button. Make sure to type it in exactly as you see it.
You should see words in the box to the right become italicized. If you do, then congratulations! You just wrote CSS!
If HTML and CSS have combined to make a person that looks like a person, you can think of JavaScript as being the brain. Without it, a person just sits there, but with it, they are active and alive.
JavaScript can change the HTML and CSS of a website in real time after it has loaded. It can hide things, add new things, change what things look like, and more. Any time something on a website changes while you are looking at it, there is a good chance that JavaScript is being used to do it.
For example, imagine that you wanted the browser to create a pop-up greeting whenever somebody loaded the extremely simple website from before. One way would be to write some code that looks like this:
And when you loaded the website, you would see something like this:
You can test that JavaScript yourself. Use this code as an example:
Try entering that snippet of code in the input box below, then press the "Run Code" button. Make sure to type it in exactly as you see it.
You should see a pop-up just like in the example above, only with a different message. Congratulations, y ou just wrote JavaScript!
/en/computer-programming-basics/tools-to-start-programming/content/

- Onsite training
3,000,000+ delegates
15,000+ clients
1,000+ locations
- KnowledgePass
- Log a ticket
01344203999 Available 24/7

What is Programming? An Ultimate Guide
Programming is the act of creating and implementing instructions, known as code, that computers can execute to perform tasks or achieve specific objectives. Discover What is Programming and get a concise overview of this fascinating field. Programming involves giving instructions to computers to solve problems and perform tasks.

Exclusive 40% OFF
Training Outcomes Within Your Budget!
We ensure quality, budget-alignment, and timely delivery by our expert instructors.
Share this Resource
- D Programming Language Training
- Java Programming and Software Engineering Fundamentals Training
- Software Development Lifecycle Training
- Ruby Programming Course
- Visual Basic for Applications VBA Training

Programming is the composition of sequences of instructions. These sequences are called programs. Computers follow these patterns to perform tasks. It includes designing and implementing algorithms. If further condensed, the process can be described as teaching a computer how to think or act. This blog provides an easy-to-understand introduction to What is Programming. Read through to learn more!
Table of Contents
1) What is Programming?
2) How does Programming function?
3) Utilisations of Programming
4) Significance of Programming for organisations
5) Understanding Programming languages
6) The diversity of Programming languages
7) Logical structures within Programming
8) Tools and technologies in Programming
9) Getting started in computer Programming
10) Difference between coding and Programming
11) Conclusion
What is Programming?
Programming is teaching the computer what to do. More specifically, it refers to a procedure of writing codes in several Programming languages, such as Python, Java, and C++, among others, to create software applications, systems, and tools. It is a creative process—from the conception of an idea to a feasible working system.

Why Programming is needed?
Programming is essential because it powers the technology we use every day — from smartphones to cars to the internet. Without Programming, we wouldn’t have:
1) Websites
2) Mobile applications
3) Video games
4) Online banking
5) Automated manufacturing
It also enables us to solve complex problems and automate repetitive tasks, enhancing efficiency and enabling innovation and technological advancements.
How does Programming function?
Programming works by following these general steps:
1) Problem identification: Recognising and defining the problem or the task to be completed.
2) Planning: Outlining a solution, usually through algorithms or pseudocode.
3) Coding: Writing code in a Programming language.
4) Testing: Running the program to find and fix bugs or errors.
5) Deployment and maintenance: Implement the program in a live environment and update it as needed.
Through these steps, Programming translates logical solutions into a language that computers can understand.
Utilisations of Programming
Programming has a myriad of applications across different fields and industries. Here are some key utilisations:

1) Web Development: Creating and maintaining websites.
2) Software Engineering: Designing and developing software.
3) Data Analysis: Processing and analysing large data sets to find patterns or make predictions.
4) Artificial Intelligence: Building systems that can mimic human intelligence and perform tasks such as recognising speech images or making decisions.
5) Robotics: Developing algorithms that control the behaviour of robots.
Significance of Programming for organisations
For businesses, Programming is invaluable. It helps in:
1) Automation of operations: Streamlining business processes through software, reducing cost and increasing efficiency.
2) Data management: Efficient handling, storage, and analysis of data to enhance decision-making.
3) Customer engagement: Programming enables better customer service and interaction through apps and websites.
4) Innovation: Staying competitive by adopting the latest technologies and trends like IoT, blockchain, and more.
Understanding Programming Languages
Programming languages are tools that allow developers to communicate instructions to a computer efficiently. They are categorised based on their level of abstraction and the control they offer over hardware.

1) Machine Language (ML)
Machine Language is the lowest level of Programming language. It is made up of 0s and 1s; binary code, hence running directly through the Central Processing Unit (CPU) of a computer. In a sense, machine language Programming is thus very hardware-specific because every type of CPU has its own machine language.
2) Assembly Language (ASM)
Assembly language is a level above Machine Language and contains mnemonics that are symbolic representations of various machine code instructions; these instructions are far easier for humans to understand and write. Each statement in a program written in assembly language corresponds exactly to one in machine language. An assembler is a program that converts an assembly code program into executable machine code.
3) Mid-level language
Mid-level languages serve as a bridge between the low-level control of assembly languages and the high-level abstraction of advanced Programming languages. C is the most prominent example of a mid-level language, offering both the high-level functionalities necessary for developing complex programs and low-level features that allow detailed manipulation of hardware.
4) High-level language
High-level languages abstract the details of the computer hardware from the process of Programming, therefore allowing the developer to focus more on the logic of the application and less on the mechanics of the hardware. For instance, Python, Java, and C++. They are easy to use, flexible, and easily applied in all kinds of Programming, from software engineering to web development.
The diversity of Programming languages
The diversity in Programming languages allows developers to choose the most appropriate language based on the specific needs of their project, considering factors like application type, system resources, and performance requirements. From specialised languages designed for statistical analysis, such as R, to languages geared towards systems Programming, like Rust, the variety ensures that there is a tool for every job.
Unlock the power of OOP and elevate your coding skills with our comprehensive Object-Oriented Programming Course – Join now and transform your Programming prowess!
Logical structures within Programming
Logical structures are the fundamental elements of Programming that enable the control of flow within programs. These include:
1) Sequences: The default mode of operation where instructions are executed in order, one after another.
2) Decisions: Structures that involve choosing between different paths based on conditions, typically implemented using if-else or switch-case statements.
3) Loops: Used to iterate a block of code multiple times until a particular condition changes, common constructs include for, while, and do-while loops.
Understanding these structures is crucial for Programming because they enable developers to dictate not just what a computer should do but how it should handle different situations dynamically.
Tools and technologies in Programming
The field of Programming is diverse, with various tools and technologies that cater to different Programming needs. Understanding these tools is a step towards mastering Programming:
1) Programming languages: These are the core tools for any programmer. Popular languages include Python, Java, JavaScript, C#, and Ruby. Each language has specific uses, such as web development, software engineering, data analysis, and more.
2) Integrated Development Environments (IDEs): IDEs like Visual Studio, Eclipse, and PyCharm provide programmers with tools to write, test, and fix their code in a single application.
3) Version Control Systems (VCS): Tools like Git help manage changes to source code, facilitating collaboration among Programming teams.
4) Databases: Knowledge of databases is crucial. SQL databases like MySQL and PostgreSQL and NoSQL databases like MongoDB are widely used.
5) Frameworks and libraries: These are sets of pre-written code that programmers can apply to solve common problems or perform common tasks in a more standardised way. For example, React is used for front-end development, and Django is used for Python-based web applications.
Elevate your coding game with our D Programming Language Training – master a modern, efficient language and unleash your Software Development potential today!
Getting started in computer Programming
Beginning your journey in computer Programming involves a structured approach. Here’s how you can start:
1) Define your Programming objectives
Understanding what you want to achieve with Programming can guide your learning process. Whether it’s developing web applications, analysing data, or creating games, your objectives will determine the path you take.
2) Register in an introductory Programming course
Look for courses that suit your learning style. Options include online platforms or more structured settings like university courses or coding boot camps.
3) Develop fundamental Programming competencies
Start with the basics of your desired Programming language. Understand variables, control structures, data structures, syntax, and semantics. Building a strong foundation is crucial.
Embark on a journey to Ruby mastery – join our comprehensive Ruby Programming Course and unleash your potential as a dynamic Software Developer!
4) Engage with fellow programmers
Join Programming communities online (such as Stack Overflow, GitHub, or Reddit) or offline. Networking with other programmers can provide support, insights, and opportunities to collaborate on projects.
5) Accomplish coding projects
Use what you’ve learned by working on projects. Start with small tasks and gradually take on complex projects. This will build your confidence and enrich your problem-solving skills.
6) Explore potential career paths in Programming
As you gain skills, consider what career paths align with your interests. Programming opens doors to roles like software developer, web developer, systems analyst, and many others.
Difference between coding and Programming
While often used interchangeably, coding and Programming are distinct concepts:
1) Coding is the process of translating logic and algorithms into a language that a machine can understand. It is essentially writing the code that tells the computer what to do.
2) Programming involves a more holistic approach. It includes not only coding but also planning, designing, testing, and maintaining applications. A programmer thinks about the algorithm, writes the code, and solves problems that arise during development.
Conclusion
The capability to understand What is Programming is now the most fundamental skill to drive the new world, where the highest possibility of creation and innovation of new things occurs on several platforms and industries. Understanding its core principles, tools, and applications opens doors for everyone to realise the huge potential that Programming holds.
Level up your coding skills with our comprehensive Programming Training – unlock the secrets of Software Development and become a coding maestro!
Frequently Asked Questions
The first Programming language is generally considered to be Fortran, developed in the 1950s by IBM for scientific and engineering applications.
Programming is often considered the best because it offers a powerful way to solve problems, innovate, and create virtually anything imaginable. It provides flexibility in job markets and the satisfaction of building something from scratch. Additionally, Programming skills are versatile and applicable across various industries.
The Knowledge Academy takes global learning to new heights, offering over 30,000 online courses across 490+ locations in 220 countries. This expansive reach ensures accessibility and convenience for learners worldwide.
Alongside our diverse Online Course Catalogue, encompassing 17 major categories, we go the extra mile by providing a plethora of free educational Online Resources like News updates, Blogs , videos, webinars, and interview questions. Tailoring learning experiences further, professionals can maximise value with customisable Course Bundles of TKA .
The Knowledge Academy’s Knowledge Pass , a prepaid voucher, adds another layer of flexibility, allowing course bookings over a 12-month period. Join us on a journey where education knows no bounds.
The Knowledge Academy offers various Programming Trainings , including the M Python Programming Course, Visual Basic Course, and Object-Oriented Programming (OOPs) Course. These courses cater to different skill levels, providing comprehensive insights into Advantages of Object-Oriented Programming (OOP) .
Our Programming Training Blogs cover a range of topics related to Programming Fundamentals, offering valuable resources, best practices, and industry insights. Whether you are a beginner or looking to advance your Programming skills, The Knowledge Academy's diverse courses and informative blogs have got you covered.
Upcoming Programming & DevOps Resources Batches & Dates
Fri 2nd Aug 2024
Fri 1st Nov 2024
Get A Quote
WHO WILL BE FUNDING THE COURSE?
My employer
By submitting your details you agree to be contacted in order to respond to your enquiry
- Business Analysis
- Lean Six Sigma Certification
Share this course
Our biggest spring sale.

We cannot process your enquiry without contacting you, please tick to confirm your consent to us for contacting you about your enquiry.
By submitting your details you agree to be contacted in order to respond to your enquiry.
We may not have the course you’re looking for. If you enquire or give us a call on 01344203999 and speak to our training experts, we may still be able to help with your training requirements.
Or select from our popular topics
- ITIL® Certification
- Scrum Certification
- Change Management Certification
- Business Analysis Courses
- Microsoft Azure Certification
- Microsoft Excel Courses
- Microsoft Project
- Explore more courses
Press esc to close
Fill out your contact details below and our training experts will be in touch.
Fill out your contact details below
Thank you for your enquiry!
One of our training experts will be in touch shortly to go over your training requirements.
Back to Course Information
Fill out your contact details below so we can get in touch with you regarding your training requirements.
* WHO WILL BE FUNDING THE COURSE?
Preferred Contact Method
No preference
Back to course information
Fill out your training details below
Fill out your training details below so we have a better idea of what your training requirements are.
HOW MANY DELEGATES NEED TRAINING?
HOW DO YOU WANT THE COURSE DELIVERED?
Online Instructor-led
Online Self-paced
WHEN WOULD YOU LIKE TO TAKE THIS COURSE?
Next 2 - 4 months
WHAT IS YOUR REASON FOR ENQUIRING?
Looking for some information
Looking for a discount
I want to book but have questions
One of our training experts will be in touch shortly to go overy your training requirements.
Your privacy & cookies!
Like many websites we use cookies. We care about your data and experience, so to give you the best possible experience using our site, we store a very limited amount of your data. Continuing to use this site or clicking “Accept & close” means that you agree to our use of cookies. Learn more about our privacy policy and cookie policy cookie policy .
We use cookies that are essential for our site to work. Please visit our cookie policy for more information. To accept all cookies click 'Accept & close'.
- Data Structures
- Linked List
- Binary Tree
- Binary Search Tree
- Segment Tree
- Disjoint Set Union
- Fenwick Tree
- Red-Black Tree
- Advanced Data Structures
- Hashing in Data Structure
- Introduction to Hashing - Data Structure and Algorithm Tutorials
What is Hashing?
- Index Mapping (or Trivial Hashing) with negatives allowed
- Separate Chaining Collision Handling Technique in Hashing
- Open Addressing Collision Handling technique in Hashing
- Double Hashing
- Load Factor and Rehashing
Easy problems on Hashing
- Find whether an array is subset of another array
- Union and Intersection of two Linked List using Hashing
- Pair with given Sum (Two Sum)
- Maximum distance between two occurrences of same element in array
- Most frequent element in an array
- Find the only repetitive element between 1 to N-1
- How to check if two given sets are disjoint?
- Non-overlapping sum of two sets
- Check if two arrays are equal or not
- Find missing elements of a range
- Minimum number of subsets with distinct elements
- Remove minimum number of elements such that no common element exist in both array
- Count pairs with given sum
- Count quadruples from four sorted arrays whose sum is equal to a given value x
- Sort elements by frequency | Set 4 (Efficient approach using hash)
- Find all pairs (a, b) in an array such that a % b = k
- Group words with same set of characters
- k-th distinct (or non-repeating) element among unique elements in an array.
Intermediate problems on Hashing
- Find Itinerary from a given list of tickets
- Find number of Employees Under every Manager
- Longest subarray with sum divisible by K
- Find the length of largest subarray with 0 sum
- Longest Increasing consecutive subsequence
- Count distinct elements in every window of size k
- Design a data structure that supports insert, delete, search and getRandom in constant time
- Find subarray with given sum | Set 2 (Handles Negative Numbers)
- Implementing our Own Hash Table with Separate Chaining in Java
- Implementing own Hash Table with Open Addressing Linear Probing
- Maximum possible difference of two subsets of an array
- Sorting using trivial hash function
- Smallest subarray with k distinct numbers
Hard problems on Hashing
- Clone a Binary Tree with Random Pointers
- Largest subarray with equal number of 0s and 1s
- All unique triplets that sum up to a given value
- Range Queries for Frequencies of array elements
- Elements to be added so that all elements of a range are present in array
- Cuckoo Hashing - Worst case O(1) Lookup!
- Count subarrays having total distinct elements same as original array
- Maximum array from two given arrays keeping order same
- Find Sum of all unique sub-array sum for a given array.
- Length of longest strict bitonic subsequence
- Find All Duplicate Subtrees
- Find if there is a rectangle in binary matrix with corners as 1
- Top 20 Hashing Technique based Interview Questions
Introduction to Hashing – Data Structure and Algorithm Tutorials
Hashing refers to the process of generating a fixed-size output from an input of variable size using the mathematical formulas known as hash functions. This technique determines an index or location for the storage of an item in a data structure.
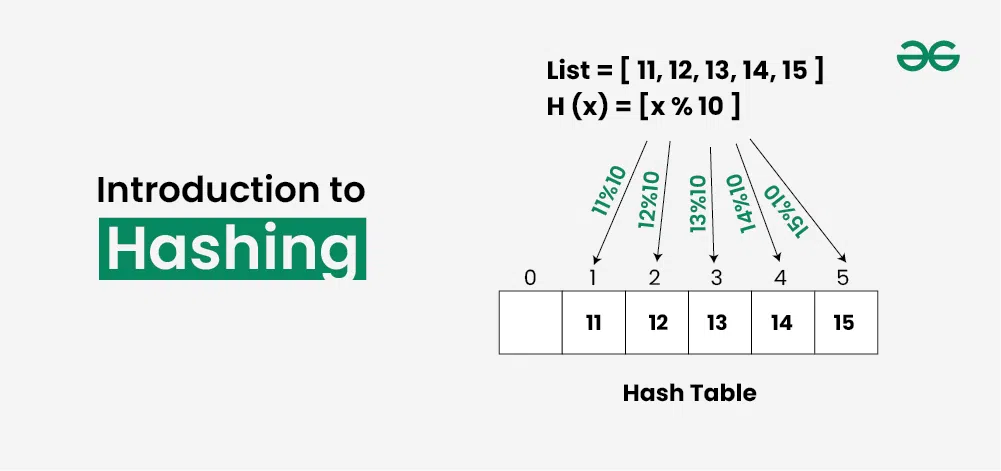
Table of Content
Need for Hash data structure
Components of hashing, how does hashing work, what is a hash function.
- Types of Hash functions
Properties of a Good hash function
Complexity of calculating hash value using the hash function, problem with hashing, what is collision, how to handle collisions.
- Separate Chaining
- Linear Probing
- Quadratic Probing
What is meant by Load Factor in Hashing?
What is rehashing, applications of hash data structure, real-time applications of hash data structure, advantages of hash data structure, disadvantages of hash data structure.
- Frequently Asked Questions(FAQs) on Hashing
Hashing in Data Structures refers to the process of transforming a given key to another value. It involves mapping data to a specific index in a hash table using a hash function that enables fast retrieval of information based on its key. The transformation of a key to the corresponding value is done using a Hash Function and the value obtained from the hash function is called Hash Code .
Every day, the data on the internet is increasing multifold and it is always a struggle to store this data efficiently. In day-to-day programming, this amount of data might not be that big, but still, it needs to be stored, accessed, and processed easily and efficiently. A very common data structure that is used for such a purpose is the Array data structure.
Now the question arises if Array was already there, what was the need for a new data structure! The answer to this is in the word ” efficiency “. Though storing in Array takes O(1) time, searching in it takes at least O(log n) time. This time appears to be small, but for a large data set, it can cause a lot of problems and this, in turn, makes the Array data structure inefficient.
So now we are looking for a data structure that can store the data and search in it in constant time, i.e. in O(1) time. This is how Hashing data structure came into play. With the introduction of the Hash data structure, it is now possible to easily store data in constant time and retrieve them in constant time as well.
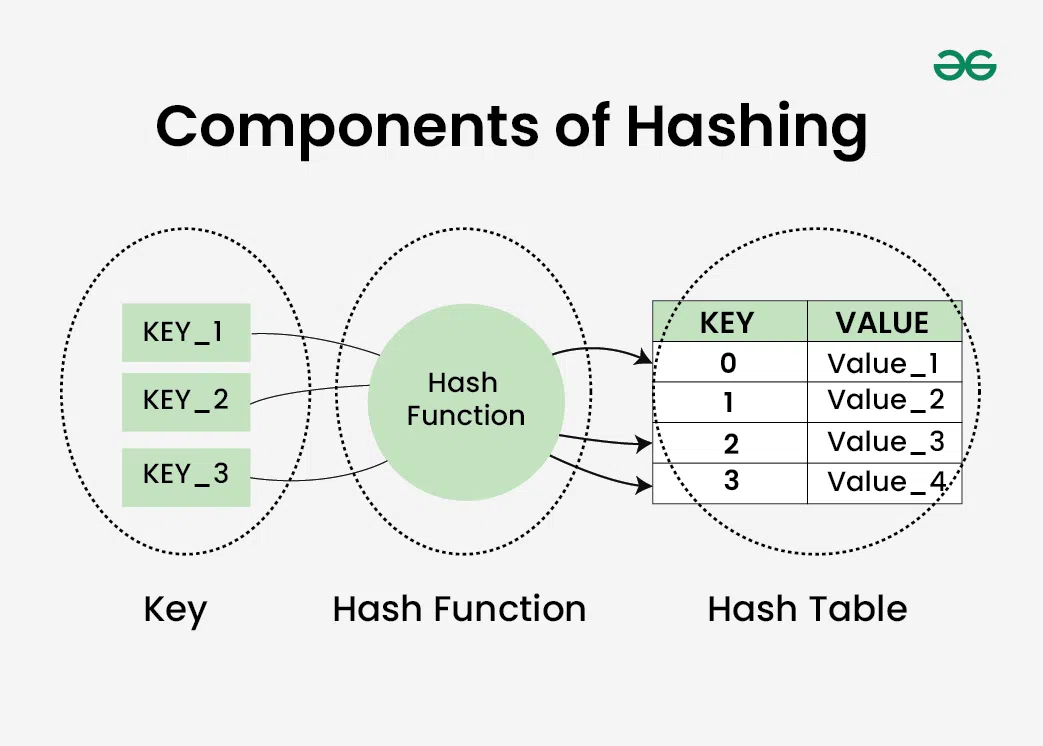
There are majorly three components of hashing:
- Key: A Key can be anything string or integer which is fed as input in the hash function the technique that determines an index or location for storage of an item in a data structure.
- Hash Function: The hash function receives the input key and returns the index of an element in an array called a hash table. The index is known as the hash index .
- Hash Table: Hash table is a data structure that maps keys to values using a special function called a hash function. Hash stores the data in an associative manner in an array where each data value has its own unique index.
Suppose we have a set of strings {“ab”, “cd”, “efg”} and we would like to store it in a table.
Our main objective here is to search or update the values stored in the table quickly in O(1) time and we are not concerned about the ordering of strings in the table. So the given set of strings can act as a key and the string itself will act as the value of the string but how to store the value corresponding to the key?
- Step 1: We know that hash functions (which is some mathematical formula) are used to calculate the hash value which acts as the index of the data structure where the value will be stored.
- “b”=2, .. etc, to all alphabetical characters.
- Step 3: Therefore, the numerical value by summation of all characters of the string:
“ab” = 1 + 2 = 3, “cd” = 3 + 4 = 7 , “efg” = 5 + 6 + 7 = 18
- Step 4: Now, assume that we have a table of size 7 to store these strings. The hash function that is used here is the sum of the characters in key mod Table size . We can compute the location of the string in the array by taking the sum(string) mod 7 .
- “ab” in 3 mod 7 = 3,
- “cd” in 7 mod 7 = 0, and
- “efg” in 18 mod 7 = 4.
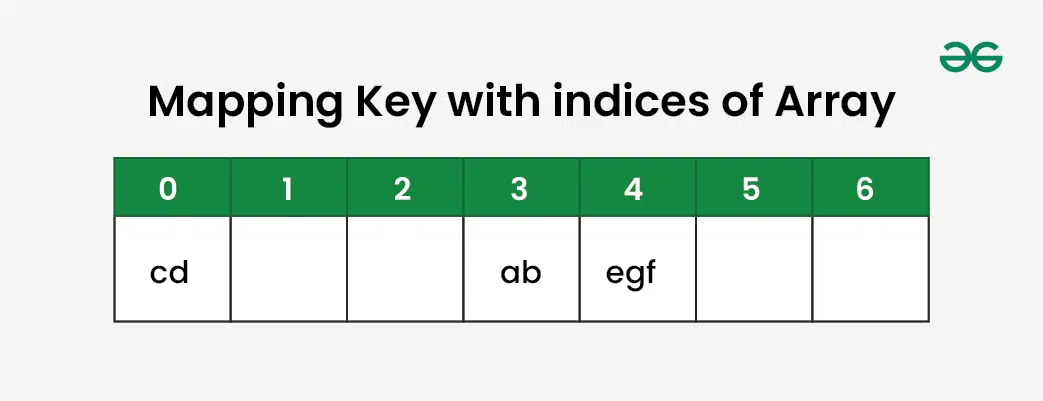
The above technique enables us to calculate the location of a given string by using a simple hash function and rapidly find the value that is stored in that location. Therefore the idea of hashing seems like a great way to store (key, value) pairs of the data in a table.
The hash function creates a mapping between key and value, this is done through the use of mathematical formulas known as hash functions. The result of the hash function is referred to as a hash value or hash. The hash value is a representation of the original string of characters but usually smaller than the original.
For example: Consider an array as a Map where the key is the index and the value is the value at that index. So for an array A if we have index i which will be treated as the key then we can find the value by simply looking at the value at A[i].
Types of Hash functions:
There are many hash functions that use numeric or alphanumeric keys. This article focuses on discussing different hash functions :
- Division Method.
- Mid Square Method
- Folding Method.
- Multiplication Method
A hash function that maps every item into its own unique slot is known as a perfect hash function. We can construct a perfect hash function if we know the items and the collection will never change but the problem is that there is no systematic way to construct a perfect hash function given an arbitrary collection of items. Fortunately, we will still gain performance efficiency even if the hash function isn’t perfect. We can achieve a perfect hash function by increasing the size of the hash table so that every possible value can be accommodated. As a result, each item will have a unique slot. Although this approach is feasible for a small number of items, it is not practical when the number of possibilities is large.
So, We can construct our hash function to do the same but the things that we must be careful about while constructing our own hash function.
A good hash function should have the following properties:
- Efficiently computable.
- Should uniformly distribute the keys (Each table position is equally likely for each.
- Should minimize collisions.
- Should have a low load factor(number of items in the table divided by the size of the table).
- Time complexity: O(n)
- Space complexity: O(1)
If we consider the above example, the hash function we used is the sum of the letters, but if we examined the hash function closely then the problem can be easily visualized that for different strings same hash value is begin generated by the hash function.
For example: {“ab”, “ba”} both have the same hash value, and string {“cd”,”be”} also generate the same hash value, etc. This is known as collision and it creates problem in searching, insertion, deletion, and updating of value.
Collision in Hashing occurs when two different keys map to the same hash value. Hash collisions can be intentionally created for many hash algorithms. The probability of a hash collision depends on the size of the algorithm, the distribution of hash values and the efficiency of Hash function.
The hashing process generates a small number for a big key, so there is a possibility that two keys could produce the same value. The situation where the newly inserted key maps to an already occupied, and it must be handled using some collision handling technology.
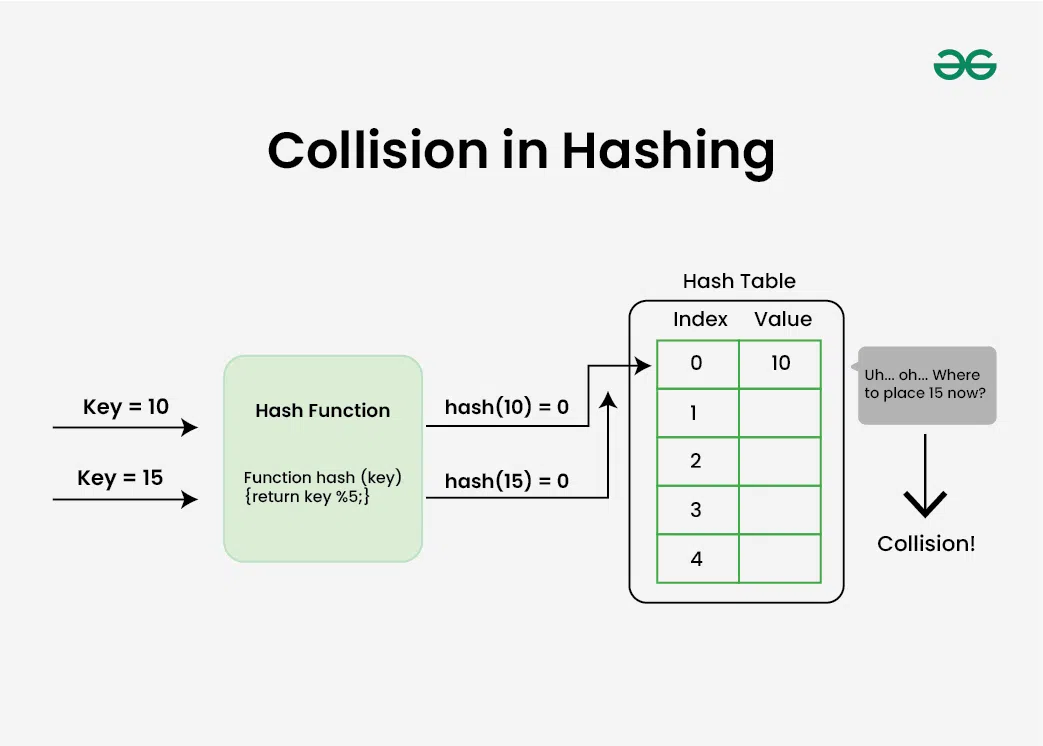
There are mainly two methods to handle collision:
- Open Addressing
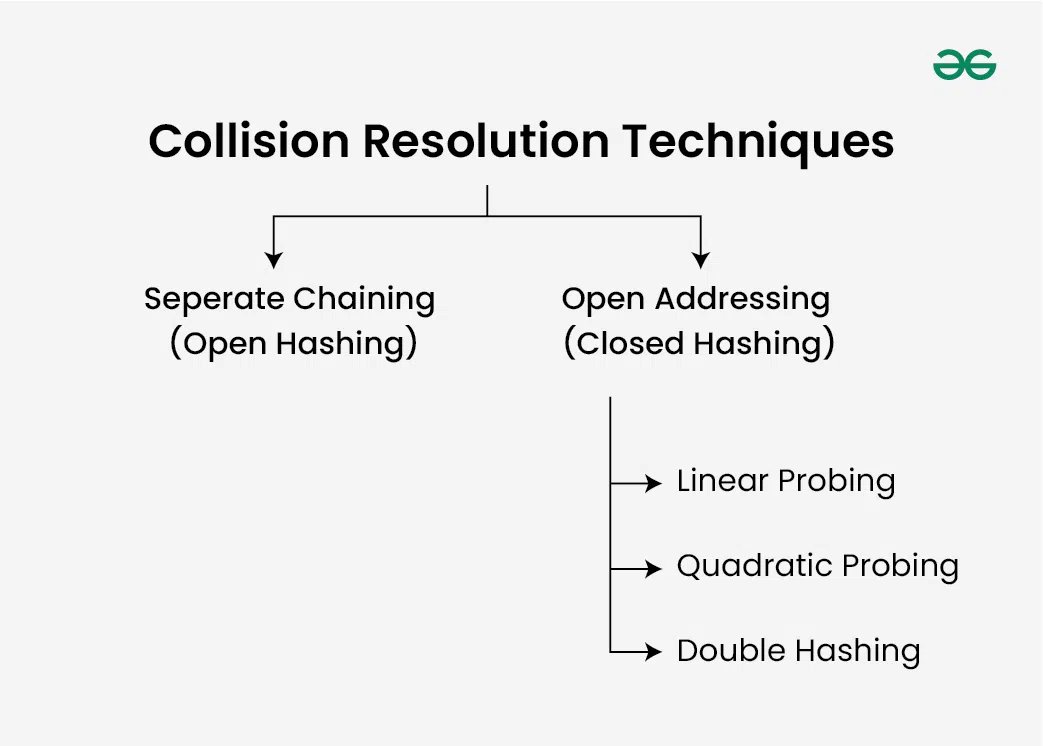
1) Separate Chaining
The idea is to make each cell of the hash table point to a linked list of records that have the same hash function value. Chaining is simple but requires additional memory outside the table.
Example: We have given a hash function and we have to insert some elements in the hash table using a separate chaining method for collision resolution technique.
Let’s see step by step approach to how to solve the above problem:
Hence In this way, the separate chaining method is used as the collision resolution technique.
2) Open Addressing
In open addressing, all elements are stored in the hash table itself. Each table entry contains either a record or NIL. When searching for an element, we examine the table slots one by one until the desired element is found or it is clear that the element is not in the table.
2.a) Linear Probing
In linear probing, the hash table is searched sequentially that starts from the original location of the hash. If in case the location that we get is already occupied, then we check for the next location.
Calculate the hash key. i.e. key = data % size Check, if hashTable[key] is empty store the value directly by hashTable[key] = data If the hash index already has some value then check for next index using key = (key+1) % size Check, if the next index is available hashTable[key] then store the value. Otherwise try for next index. Do the above process till we find the space.
Example: Let us consider a simple hash function as “key mod 5” and a sequence of keys that are to be inserted are 50, 70, 76, 85, 93.
2.b) Quadratic Probing
Quadratic probing is an open addressing scheme in computer programming for resolving hash collisions in hash tables. Quadratic probing operates by taking the original hash index and adding successive values of an arbitrary quadratic polynomial until an open slot is found.
An example sequence using quadratic probing is:
H + 1 2 , H + 2 2 , H + 3 2 , H + 4 2 …………………. H + k 2
This method is also known as the mid-square method because in this method we look for i 2 ‘th probe (slot) in i’th iteration and the value of i = 0, 1, . . . n – 1. We always start from the original hash location. If only the location is occupied then we check the other slots.
Let hash(x) be the slot index computed using the hash function and n be the size of the hash table.
If the slot hash(x) % n is full, then we try (hash(x) + 1 2 ) % n. If (hash(x) + 1 2 ) % n is also full, then we try (hash(x) + 2 2 ) % n. If (hash(x) + 2 2 ) % n is also full, then we try (hash(x) + 3 2 ) % n. This process will be repeated for all the values of i until an empty slot is found
Example: Let us consider table Size = 7, hash function as Hash(x) = x % 7 and collision resolution strategy to be f(i) = i 2 . Insert = 22, 30, and 50
2.c) Double Hashing
Double hashing is a collision resolving technique in Open Addressed Hash tables. Double hashing make use of two hash function,
- The first hash function is h1(k) which takes the key and gives out a location on the hash table. But if the new location is not occupied or empty then we can easily place our key.
- But in case the location is occupied (collision) we will use secondary hash-function h2(k) in combination with the first hash-function h1(k) to find the new location on the hash table.
This combination of hash functions is of the form
- i is a non-negative integer that indicates a collision number,
- k = element/key which is being hashed
- n = hash table size.
Complexity of the Double hashing algorithm:
Example: Insert the keys 27, 43, 692, 72 into the Hash Table of size 7. where first hash-function is h1(k) = k mod 7 and second hash-function is h2(k) = 1 + (k mod 5)
The load factor of the hash table can be defined as the number of items the hash table contains divided by the size of the hash table. Load factor is the decisive parameter that is used when we want to rehash the previous hash function or want to add more elements to the existing hash table.
It helps us in determining the efficiency of the hash function i.e. it tells whether the hash function which we are using is distributing the keys uniformly or not in the hash table.
As the name suggests, rehashing means hashing again. Basically, when the load factor increases to more than its predefined value (the default value of the load factor is 0.75), the complexity increases. So to overcome this, the size of the array is increased (doubled) and all the values are hashed again and stored in the new double-sized array to maintain a low load factor and low complexity.
- Hash is used in databases for indexing.
- Hash is used in disk-based data structures.
- In some programming languages like Python, JavaScript hash is used to implement objects.
- Hash is used for cache mapping for fast access to the data.
- Hash can be used for password verification.
- Hash is used in cryptography as a message digest.
- Rabin-Karp algorithm for pattern matching in a string.
- Calculating the number of different substrings of a string.
- Hash provides better synchronization than other data structures.
- Hash tables are more efficient than search trees or other data structures
- Hash provides constant time for searching, insertion, and deletion operations on average.
- Hash is inefficient when there are many collisions.
- Hash collisions are practically not avoided for a large set of possible keys.
- Hash does not allow null values.
Frequently Asked Questions(FAQs) on Hashing:
1. what is a hash function.
Hashing refers to the process of transforming a given key to another value. It involves mapping data to a specific index in a hash table using a hash function that enables fast retrieval of information based on its key.
2. What is a Hash function?
Hash function is a function that takes an input and return a fixed-size string of bytes. The hash function receives the input key and returns the index of an element in an array called a hash table. The index is known as the hash index.
3. What are Hash collisions?
Hash collisions occur when two different inputs passed to the hash function produce the same hash value. The lesser the number of hash collisions, the better the hash function is.
4. What are hash tables?
Hash tables are data structures that use hash functions to map keys to values, allowing for efficient retrieval of data when needed. Hash table maps keys to values using a special function called a hash function. Hash stores the data in an associative manner in an array where each data value has its own unique index.
5. What are some applications of Hashing?
Hashing is used in databases for indexing, disk-based data structures and data compression algorithms. Hashing is also used to store passwords securely by applying a hash function to the password and storing the hashed result, rather than the plain text password.
From the above discussion, we conclude that the goal of hashing is to resolve the challenge of finding an item quickly in a collection. For example, if we have a list of millions of English words and we wish to find a particular term then we would use hashing to locate and find it more efficiently. It would be inefficient to check each item on the millions of lists until we find a match. Hashing reduces search time by restricting the search to a smaller set of words at the beginning.
Please Login to comment...
Similar reads.
- DSA Tutorials
Improve your Coding Skills with Practice
What kind of Experience do you want to share?

IMAGES
VIDEO
COMMENTS
A system programmer is one who write system software and this task is called system programming or systems programming. But there's an older definition that's been used in the context of mainframes since the 1960s. On a mainframe, a system programmer installs, upgrades, configures and maintains the operating system.
1.1 Introduction. A modern software application typically needs to manage both private and system resources. Private resources are its own data, such as the aluesv of its internal data structures. System resources are things such as les, screen displays, and network connections.
System programming defined. System programming is used to develop applications that make life easier. For example, you can walk into a fast-food restaurant, walk to the counter, and place your order with a restaurant employee. Still, with an app developed by a software developer and system programmer, you can place your order on an app inside ...
Systems programming, or system programming, is the activity of programming computer system software. The primary distinguishing characteristic of systems programming when compared to application programming is that application programming aims to produce software which provides services to the user directly (e.g. word processor), whereas ...
Dive into Systems includes one or more chapters on the following topis: Introduction to Computer Systems; C Programming (covers most of the C language, debugging with gdb and valgrind, and code optimization); Computer Organization and Architecture (includes binary representation, computer architecture, memory hierarchy, and caching); Assembly Programming (covers 64-bit x86, 32-bit x86, and 64 ...
An introduction to system programming and C. By Lawrence Angrave at the University of Illinois at Urbana-Champaign 2014
Doing that amounts to programming a system. Best practices in system programming. It is very important to design programs and services to meet the needs of the machines. It is a common mistake to create programs and services to serve human needs. But when doing systems programming, such an approach is incorrect.
Chapter 1 - Program Structure. Chapter 2 - Review of Pointers and Memory Allocation. Chapter 3 - Introduction to Shells and Scripting. Chapter 4 - Introduction to UNIX System Programming. Chapter 5 - Writing Your Own Shell. Chapter 9 - Introduction to SQL. Chapter 10 - Introduction to Software Engineering and Design Patterns. Feedback or ...
Introduction 1. Program Structure 2. Review of Pointers and Memory Allocation 3. Introduction to Shells and Scripting 4. Introduction to Unix Systems Programming 5.Writing Your Own Shell 6.Programming with Threads 7.The Internet and Socket Programming 8.Writing Your Own Web Server 9. Introduction to SQL
System programming. "low-level" programming (e.g., a device driver) "high-level" programming (e.g., the Firefox web browser) Mostly C, and a bit of C++. lot of software is written in C (or C++) the vast majority of the programs running on your computer. including the operating system.
• Covers "programming in the large" (required for COS 333)! • Computer Systems: A Programmer's Perspective (Second Edition), Bryant and O'Hallaron, 2010.! • Covers "under the hood," key sections are on e-reserve! • First edition is sufficient! • Programming with GNU Software, Loukides and Oram, 1997.!
Understand how to use system calls to accomplish: file manipulation, process control, threads, and syncronization. Know how to implement existing functions, such as gcc, by using system calls. Review the Unix operating system structure. Be able to manipulate files using system calls. Understand how processes work between the child and parent.
System Programming Fundamentals ©2020, Michael Kerrisk Course Introduction 1-5 §1.1 Lab sessions Lots of lab sessions... For programming exercises, you can use any suitable programming language in which you are proficient C/C++ (easiest...) Go, D, Rust, & other languages that compile to native machine code
An Introduction to System Programming. This chapter is an introduction to system programming, exploring a range of topics from its original definition to how it has shifted in time with system evolution.. This chapter provides some basic concepts and an overview of Unix and its resources, including the kernel and the application programming interfaces (API).
The foundational knowledge for the position of an IBM z/OS System Programmer and System Administrator begins with this third and final course in the three course professional certificate track. This course provides hands-on labs to everyday z/OS tasks with JCL, JES, ISHELL and HFS, and z/OSMF. Topics covered include VSAM, z/OS System Libraries ...
System programming. "low-level" programming (e.g., a device driver) "high-level" programming (e.g., the Firefox web browser) Mostly C, and a bit of C++. A lot of software is written in C or C++. the vast majority of the programs running on your computer (now!) including the operating system.
Includes an introduction to object-oriented programming and design, and illustrates these concepts of object-oriented languages, compilers, and operating systems. Brings the book up-to-speed with industry by including current operating systems topics, such as multiprocessor, distributed, and client/server systems.
Books. System Software: An Introduction to Systems Programming, 3e. In this third edition of his classic title, Leland Beck provides a complete introduction to the design and implementation of various types of system software. A core text for undergraduate/graduate software students, it stresses on the relationship between system software and ...
System Programming can be defined as the act of building Systems Software using System Programming Languages. According to Computer Hierarchy, Hardware comes first then is Operating System, System Programs, and finally Application Programs. ... Introduction: System protection in an operating system refers to the mechanisms implemented by the ...
This comprehensive guide of Programming Tutorialor Coding Tutorial provides an introduction to programming, covering basic concepts, setting up your development environment, and common beginner problems. Learn about variables, data types, control flow statements, functions, and how to write your first code in various languages.
This course provides hands-on labs to everyday z/OS tasks with JCL, JES, ISHELL and HFS, and z/OSMF. Topics covered include VSAM, z/OS System Libraries, the Language Environment, Generation Data Groups, RAIM, DB2, UNIX System Services, and USS File System.
The Practice of Programming, Brian W. Kernighan and Rob Pike, Addison-Wesley 1999. The book covers program and programming style. Many of the lectures in the first half of the course are derived, in part, from this book. Computer Systems: A Programmer's Perspective (Third Edition), Randal E. Bryant and David R. O'Hallaron, Prentice-Hall 2015 ...
Introduction to programming. Computer programming is the process of designing and writing computer programs. As a skill set, it includes a wide variety of different tasks and techniques, but our tutorials are not intended to teach you everything. Instead, they are meant to provide basic, practical skills to help you understand and write ...
An Introduction to Interactive Programming in Python (Part 2) Course. Imperial College London. Getting started with TensorFlow 2. Course. Northwestern University. Modern Robotics, Course 2: Robot Kinematics. ... operating systems, object-oriented programming, full-stack development, and learning about new tools that can make a software ...
Programming is teaching the computer what to do. More specifically, it refers to a procedure of writing codes in several Programming languages, such as Python, Java, and C++, among others, to create software applications, systems, and tools. It is a creative process—from the conception of an idea to a feasible working system.
With the introduction of the Hash data structure, it is now possible to easily store data in constant time and retrieve them in constant time as well. Components of Hashing . There are majorly three components of hashing: ... This method is commonly used in databases, caching systems, and various programming. 5 min read.
Intel® Xeon® Processors Built for data centers and workstations to handle the heavy processing demands of cloud, big data, modeling, AI, and more. Intel® Core™ Ultra Processors Featuring new AI experiences, immersive graphics, and an optimal balance of battery life and performance. Intel® Core™ Processors Family Intel's CPUs for ...