This browser is no longer supported.
Upgrade to Microsoft Edge to take advantage of the latest features, security updates, and technical support.

Roles and permissions (Reporting Services)
- 9 contributors
Reporting Services provides an authentication subsystem and role-based authorization model. Authentication and authorization models vary depending on whether the report server runs in native mode or SharePoint mode. If the report server is part of a SharePoint deployment, SharePoint permissions determine who has access to the report server.
Identity and access control for native mode
Default authentication is based on Windows Authentication and integrated security. You can change the authentication settings to allow the report server to respond to different authentication requests. Or, you can replace the default security features with a custom authentication extension that you provide.
Authorization is based on roles that you assign to a principal. Each role consists of a set of related tasks, which are in turn composed of related operations. For example, the Manage reports task grants access to the following report server operations: view reports, add report, update report, delete report, schedule report, and update report properties.
Identity and access control for SharePoint mode
In SharePoint integrated mode, authentication and authorization are handled on the SharePoint site, before requests reach the report server. Depending on how you configure authentication, requests from a SharePoint site include a security token or a trusted user name. Permissions that you set for SharePoint users and groups authorize access to report server items that are placed in SharePoint libraries.
In this section
Granting permissions on a native mode report server Describes the role-based authorization model that provides access to content and operations.
Grant permissions on report server items on a SharePoint site Explains how SharePoint groups, permission levels, and permissions are used to control access to a report server.
Related content
Authentication with the report server Grant permissions on a native mode report server
Was this page helpful?
Coming soon: Throughout 2024 we will be phasing out GitHub Issues as the feedback mechanism for content and replacing it with a new feedback system. For more information see: https://aka.ms/ContentUserFeedback .
Submit and view feedback for
Additional resources
- SQL Server training
- Write for us!

Managing SSRS security and using PowerShell automation scripts
So much has changed with Reporting Services 2016 but in terms of security it’s the same under the hood and that’s not necessarily a bad thing. SSRS has long had a robust folder & item level security model with the ability to inherit permissions from parent folders, much like SharePoint and windows in general.
Managing this security model, however, can become difficult as the use of SSRS expands over years & even versions. 5 folders & 40 reports quickly become 30 folders, 200 reports and many different business units or even clients in the same environment. Once you introduce processes to move databases down to non-production environments, it quickly becomes a difficult task to maintain security never mind implement any changes or improvements. I want to outline some tips that have helped me over the years and some PowerShell scripts that will save you hours of clicking!
Best Practices & tips
AD Groups reduce maintenance
It might be an obvious one, but it’s a basic rule in my opinion. Wherever possible, grant security in SSRS (& your database too) to AD groups and fill those groups with the relevant users. This gives you a single place to add/remove people, whether that’s a quarterly task or once every decade. Using AD groups may give you one more step to check “who has access to what” but it makes finding & maintaining those users significantly easier.
Keep permissions to a minimum
Reporting Services has several “out of the box” roles to choose from. If none of those fit the bill or a user needs wants slightly more than Browser access (i.e. View Data Sources) don’t just bump them up to full Content Manager.

By connecting to your Reporting Services instance via Management Studio (SSMS) you can View the built in security roles. From here you can Add permissions to an existing role or create a whole new role, if only a subset of users need the extra permissions.

Some further reading on SSRS roles: Role Definitions – Predefined Roles
Clean up default Permissions
You may have noticed that by Default, BUILTIN\Administrators is added as a Content Manager to the Home folder (and every inherited folder!). This is great for initial setup. It allows the server admin(s) to access Report Manager & get started without any security prerequisites.

Beyond “Day 1” setup this should be removed. In the vast majority of implementations, the server admin will not be the Reporting Services admin, or there will always be people in one group who shouldn’t be in the other.
If you leave this in place you are giving everyone who has administrator rights of the SSRS server full Content Manager access. This is best to remove at first implementation before your instance grows, folders get unique permissions and it’s no longer a single click to fix (though I’ll give you a fast way to fix it later!)
Plan your Security Model
When implementing Reporting Services from scratch, or any new technology/app, it can be too easy to just use a select few “service accounts” for multiple functions & tasks. Usually it’s a case of “whatever gets this fixed/online the fastest”. Using a single AD account for each function within SSRS is good practice & minimises security risk.
An example of accounts used in a production environment:
- Domain\DataAccess for stored credentials in datasources. This account doesn’t need any access in SSRS or any server permissions. It may be granted db_datareader or more on the datasources it needed to access to.
- Domain\Deploy would be used to deploy content to Reporting Services. This would only need the Publisher role in SSRS. It could also be a group of senior developers or a dev manager.
- Domain\Service is the account Reporting Services would run under. This would need the RSExecRole on the ReportServer DB (this is granted during configuration/install). This account would have no data access or Reporting services access.
- Domain\rsAdmins is an AD group with the admins who manage content & permissions. Generally, this group would not need data access

Now, this level of separation isn’t always possible and in some smaller organizations a single person covers most of these functions so don’t take the above as a hard requirement. Using these separate domain accounts reduces a single point of failure caused by password lockouts & resets or compromised accounts.
PowerShell Automation
There’s a great deal of automation that can be achieved with PowerShell in Reporting Services., I’ve detailed a few scripts below specific to this security topic, but there’s an abundance of content out there for many tasks, such as deploying reports, folders, data sources etc. Although I’ve focused primarily on native mode Reporting Services, there are also scripts that work with SharePoint integrated mode too.
Development environment security
Unlike your production environment you may want to simplify your dev environment’s security to make it easier for developers to deploy & test without running into permissions issues. This is a good place to utilize Reporting Services’ inherit functionality. Setting all folders to “Revert to Parent Security” makes it easy to add/remove permissions to the whole environment from the top level folder.
If you ever need to copy down your production database this can be a mammoth task to update. This is where PowerShell comes in handy. The following simple script will revert all subfolders in an SSRS environment to Revert to Parent Security .
You may need to adjust the .asmx file for different versions of SSRS though this should work just fine in 2012 onwards.
Security auditing
If you’re inheriting an existing environment or even want to overhaul/audit your current security, the following PowerShell script will allow you to quickly output every folder’s security to csv allowing you to analyse erroneous permissions without searching through folders in Report Manager.
Targeted Changes
Following a security review, you may want to add or remove a single AD account/group across every folder in your environment. There may be many occasions that call for such a blanket change. Again, this would normally be a laboriously manual task without PowerShell. These little snippets show how it can be done & you can always edit these to target a specific folder (& all its sub-folders).
You can then use the following script to remove a user/group or reverse the change made in the last script.
NOTE: The above targeted scripts won’t add or remove users or groups from the top level folder. This process can be easily added, though I’ve omitted it to reduce the risk of removing an admin user/group from the entire site and in the case of adding users, I’ve worked with RS instances where multiple clients share a single instance and only admin accounts have access to the top level “home”.
Love PowerShell!
I hope I’ve provided a few examples of security practices in SSRS and some basic PowerShell scripts to automate administration of security in Reporting Services. You can build upon these scripts to do more advanced tasks such as setting instance wide security from an input file (good for refreshing other environments from production backups.
I know there is a lot of good work going into PowerShell for DBA tasks over at dbatools.io that shows PowerShell is something you want on your tool belt!
Microsoft also put together a bunch of PowerShell scripts for Reporting Services late last year. You can find the article: Community contributions to the PowerShell scripts for Reporting Services & the scripts are on GitHub here: ReportingServicesTools
For SSRS documentation, consider ApexSQL Doc , a tool that documents reports (*.rdl), shared datasets (*.rsd), shared data sources (*.rds) and projects (*.rptproj) from the file system and web services (native and SharePoint) in different output formats.
- SSRS Roles: Role Definitions – Predefined Roles
- DBATools page
- Microsoft SSRS PowerShell Tools: Community contributions to the PowerShell scripts for Reporting Services
- GitHub link: Reporting Services Powershell Tools

- Recent Posts
- How to secure Reporting Services with Group Managed Service Accounts (GMSA) - November 7, 2018
- Contribute, contribute, contribute! - June 20, 2018
- Top 10 things you must document in SQL Server Reporting Services (SSRS) - February 26, 2018
Related posts:
- Choosing and Setting a PowerShell Execution Policy
- Migrating SSRS content with PowerShell
- SQL Server Policy Based Management – best practices
- SQL Server Policy Based Management – applying policies to non-compliant targets
- PowerShell SQL Server Validation Utility – DBAChecks

SSRS 2016: You are not allowed to view this folder. Contact your administrator to obtain the necessary permissions.
In this article, I will solve the below issue in SQL Server Reporting Service 2016
Could not load folder contents You are not allowed to view this folder. Contact your administrator to obtain the necessary permissions.
SQL Server Reporting Service 2016.

Login to the SSRS Report Manager.
Add the ssrs report manager url to local intranet zone in internet explorer..
- Manage SQL Server Reporting Service 2016 Permissions.
By default, the Local Administrators have a System Administrator permission to manage SQL Server Reporting Service.
You must log in to the SSRS Report Manager via an account that already a member of the Local Administrator Group on the SSRS Server.
Add the SQL Server Reporting Service Account to the Local Administrator Group.
Make sure that the current account that will be used to manage SSRS permissions is a member of the Local Administrator Group on the SSRS Server
- Login to the SSRS (SQL Server Reporting Service ) Server.
- Open Server Manager > Tools > Computer Management.

- Local Users and Groups > Groups > Double click on Administrators group.
- Make sure that the SSRS account that will manage the SSRS is a member of this Local Administrator Group.
- If it does not exist, add it.

Although the current SSRS login account is a member of the local administrator group, you may get the below error
An error has occurred. You do not have permission for this operation. Contact your administrator to obtain the necessary permissions.

So it’s an important prerequisite step to add the SSRS Report Manager URL to Local Intranet Zone by doing the following:
- Open Internet Explorer.
- Browse the Report Manager URL.
- Open Tools > Internet Options > Security tab > Local Intranet > Sites.

Manage SQL Server Reporting Service 2016 Permissions
Now, you are ready to manage the Users Permissions in SSRS 2016 as the following:
- Click on the Manage Folder button in the SSRS 2016 homepage.

- The Security page should be opened.
- Click on Add group or user .
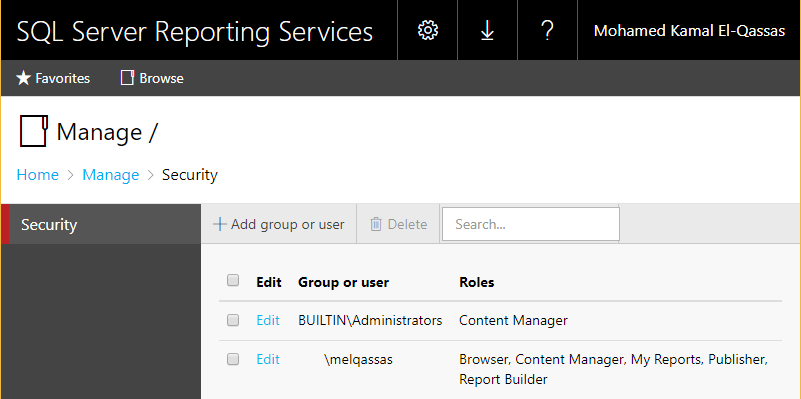
- Provide the username (no need for the domain).
- Select the role as you prefer.

- Try to access the Report Manager using the newly added user, that should be now able to access without any issue.

In this article, I have explained How to manage access permission in Reporting Service 2016?
- SSRS: Manage Permissions in Reporting Service.
- Reporting Service permission issue: user does not have required permissions.
- Install and Configure SQL Server Reporting Service (SSRS).
- Install and Configure Power BI Report Server Step by Step
Share this:
- Click to share on Facebook (Opens in new window)
- Click to share on Twitter (Opens in new window)
- Click to share on LinkedIn (Opens in new window)
3 thoughts on “SSRS 2016: You are not allowed to view this folder. Contact your administrator to obtain the necessary permissions.”
Thanks a lot. An important point is that in the security/New Role, when you want to add a new group or user, you have to insert the user that has been added in SQL Report server. You cannot add your favorable name. The name must be as same as the name which has been added before in SQL Server report.
Regards, Alireza Azad
Leave a Reply Cancel reply
Subscribe to our newsletter.
Aenean massa feugiat imperdiet a scelerisque et morbi tempus massa tincidunt vitae libero aenean tincidunt molestie.

- Our Services
- Free products
Subscription
Create SCCM Report Administrator Role
Founder of System Center Dudes. Based in Montreal, Canada, Senior Microsoft SCCM Consultant, 8 times Enterprise Mobility MVP. Working in the industry since 1999. His specialization is designing, deploying and configuring SCCM, mass deployment of Windows operating systems, Office 365 and Intune deployments.
Benoit Lecours
Table of Content
How to create sccm report administrator role, assign the security role to an administrative user, sql server reporting services permission.

Get the latest insights and exclusive content delivered to your inbox
Role based administration is used to secure the access that is needed to administer SCCM. You also secure access to the objects that you manage, like collections, deployments, and sites but lacks a couple of roles to be complete. For example, there’s no built-in role for report administration or report viewer.
We already covered the report viewer role in a previous post . This role give access to your users to consult and run SCCM Reports on the SSRS website. But what if you want to give access to an administrator to create, modify and upload reports without giving them access to the SCCM console ? This post will describe how to create SCCM Report Administrator Role which will fulfill this need.
- The first step is to create a Report Users role
- Once created, go to Administration \ Security \ Security Roles
- Right-click Report Users and select Copy
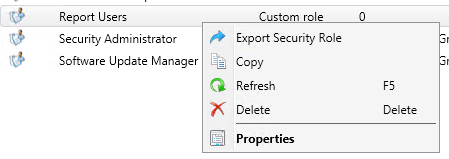
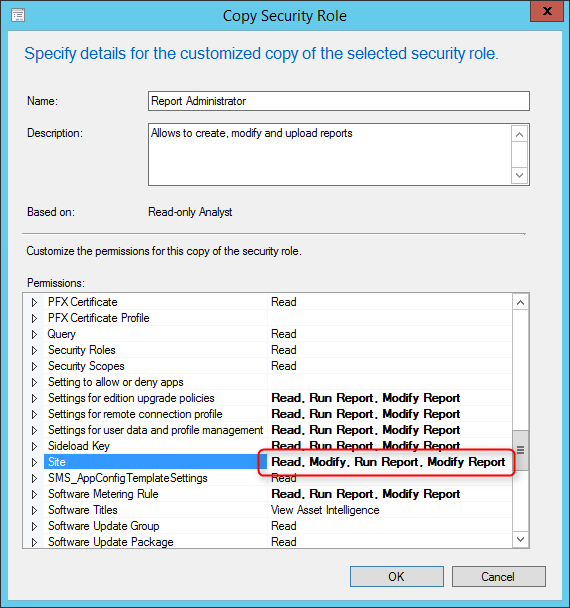
- In Name , type Report Administrator and add a brief description
- On the lower pane, browse to each class where you have Run Report right and add Modify Report
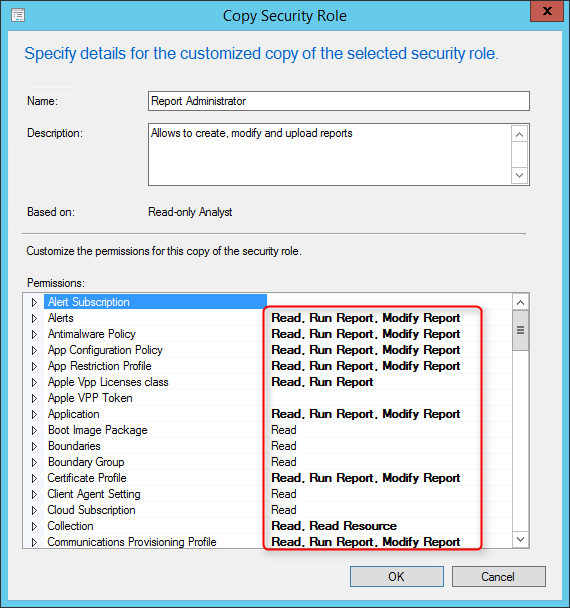
- Ensure that the Site class has Read, Modify Report and Modify permissions and click OK
We now need to assign the Report Administrator security role to a user.
- Go to Administration \ Security \ Administrative Users
- Right-click Administrative User and select Add User or Group
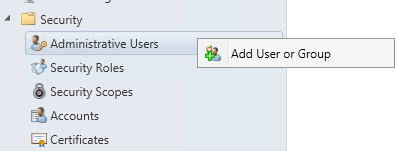
- In the Add User or Group window, click Browse and select your user
- Click Add, select the Report Administrator Role that you just created
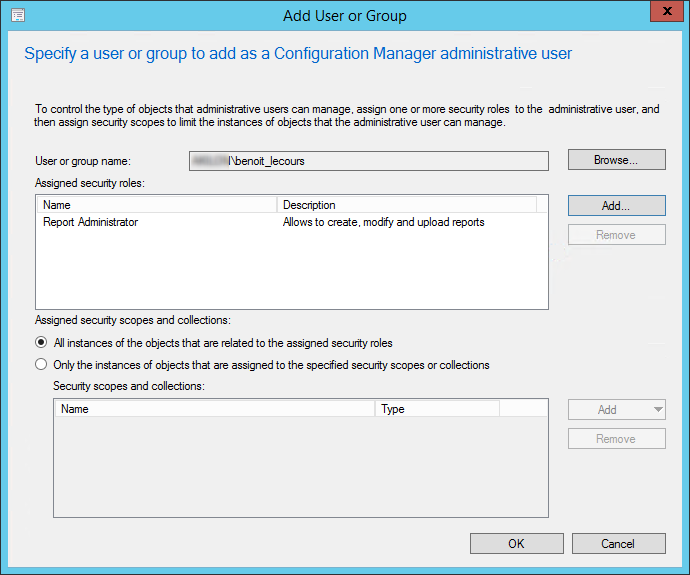
- In the lower pane select All instances of the objects that are related to the assigned security roles
You have now assign your user or group to your report administrator role in SCCM.
There’s one last step to complete. We need to give access to this user on the SSRS Website. SCCM overwrites permission modification by using the role-based assignments stored in the site database.
As per Technet :
Configuration Manager connects to Reporting Services and sets the permissions for users on the Configuration Manager and Reporting Services root folders and specific report folders. After the initial installation of the reporting services point, Configuration Manager connects to Reporting Services in a 10-minute interval to verify that the user rights configured on the report folders are the associated rights that are set for Configuration Manager users. When users are added or user rights are modified on the report folder by using Reporting Services Report Manager, Configuration Manager overwrites those changes by using the role-based assignments stored in the site database. Configuration Manager also removes users that do not have Reporting rights in Configuration Manager.
It’s not possible just to add your user with the Config Report Administrators role because it will be reset in 10 minutes.
- To fix this, you must click Site Settings in the upper right corner
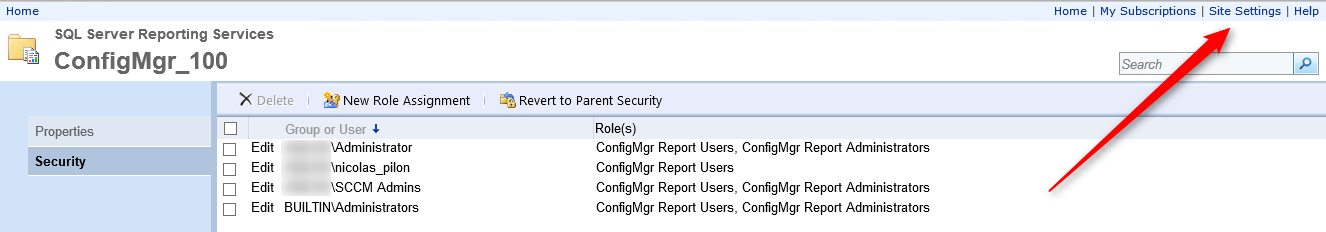
- Click Security and New Role Assignment
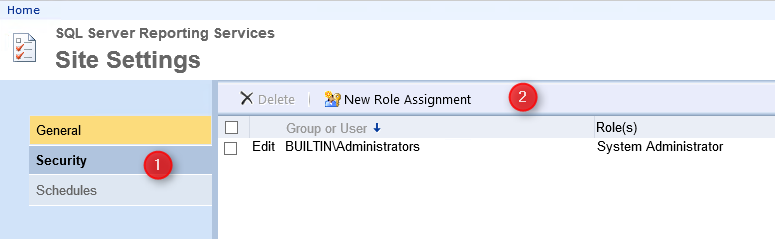
- Enter your user or group name without your domain
- This role give access to view system properties, shared schedules, and allow use of Report Builder or other clients that execute report definitions
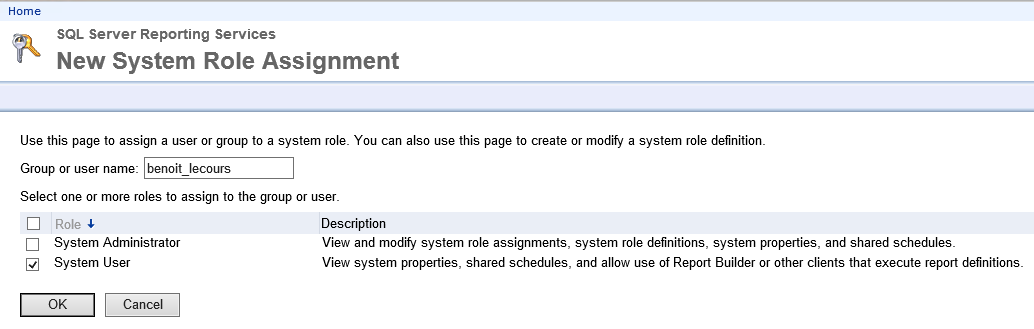
Once set, you can validate that your user has been given the rights.
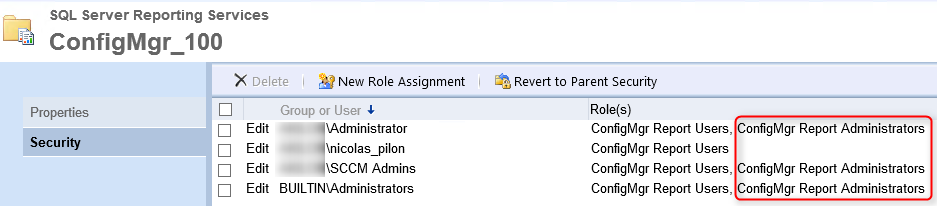
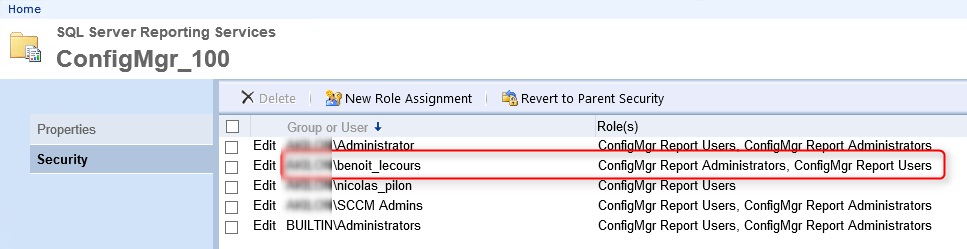
- Go to the root of your SQL Reporting Service Website, click you ConfigMgr site and select Security
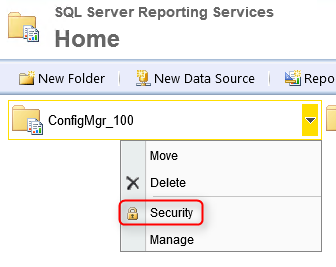
- Validate that your user has been added. Those permission won’t be overwrite. All set !
Only authorized users can leave comments
Peter Bajurny
Two days ago, Microsoft had an outage affecting Intune AutoPilot Pre-Provisionning. Users...
SCCM can be used to deploy packages and applications on multiple computers. But as with any other...
Microsoft has released the first SCCM version for 2024 as the release cadence is now reduced to 2...
Please fill out the form, and one of our representatives will contact you in Less Than 24 Hours . We are open from Monday to Friday .
Consulting Services
Reports and Guides
I'm interested in working with you
Consulting services and time banks are used for generic requests. All others are fixed-price plans.
Thank you for your request. You will receive an email with more details. Take note that we normally work from Monday to Friday. We will get in touch with you as soon as possible.
Thank for your reply!
Something went wrong!
SQL Server Reporting Services Report Manager Site Permissions Error After Installation
By: Dallas Snider | Comments (12) | Related: > Reporting Services Security
After a successful installation of SQL Server Reporting Services 2012 on a personal computer such as a laptop, a permissions error is received when accessing the Report Manager site for the first time. The message typically states the following: "User DOMAIN_NAME\userID does not have required permissions. Verify that sufficient permissions have been granted and Windows User Account Control (UAC) restrictions have been addressed." This error can occur even though you the user, installer and database administrator have full administrative rights on your device.
Depending on your situation there are two methods that will typically resolve this problem. We will start with the easier solution first before moving to the more complicated solution. The goal of both solutions is to get the Site Settings to display in the top right corner as shown below. Site Settings is not displayed in the image above containing the error message.
1. The first method involves starting Internet Explorer by using the Run as administrator option as shown below.
2. If Site Settings is not displayed, please skip to step 8. If Site Settings is displayed in the top right corner, click on Site Settings. Click on the Security tab on the left. Next, click on New Role Assignment.
3. On the New System Role Assignment page, enter your group or user name and then select the System Administrator checkbox. Click on OK.
4. After clicking on OK, the system role assignments will be shown.
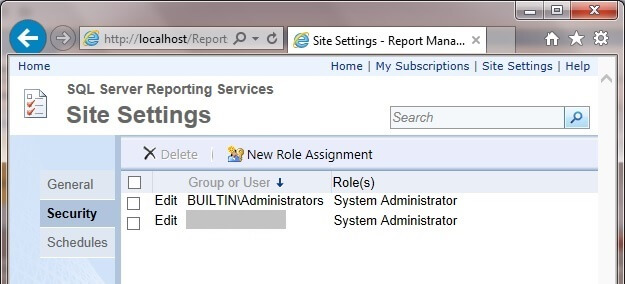
5. Next, click on Home in the top right and then click on Folder Settings.
6. Click on New Role Assignment. Add your group or user name and then choose the desired roles to be assigned. Click on OK when finished.
7. If you have made it this far, then the problem should be resolved. Exit from Internet Explorer and reopen Internet Explorer normally without running as administrator and navigate to your local Report Manager site.
8. The second method involves temporarily changing the User Access Control settings.
9. Change the settings from the default level as shown above to "Never notify" shown below. After clicking OK and rebooting your computer, attempt steps 1 through 7 above. When successfully making these changes, make sure to set the User Access Control settings back to the default level and reboot.
- Read through our Reporting Services Tutorial.
- Read through our Report Builder Tutorial.

About the author

Comments For This Article

Related Content
SQL Server Reporting Services Custom Security with Single Sign-on
SQL Server Reporting Services 2012 Permissions
SQL Server Reporting Services Encryption Key
Determining who is viewing reports in SQL Server 2012 Reporting Services
SQL Server Reporting Services Security Options
SQL Server Reporting Services Column Level Security
Centralize and Control Data Access in SSRS 2008 R2
Related Categories
SQL Reference Guide
Reporting Services Administration
Reporting Services Best Practices
Reporting Services Configuration
Reporting Services Installation
Reporting Services Migration
Reporting Services Monitoring
Reporting Services Network Load Balancing
Reporting Services Performance
Reporting Services Security
Development
Date Functions
System Functions
JOIN Tables
SQL Server Management Studio
Database Administration
Performance
Performance Tuning
Locking and Blocking
Data Analytics \ ETL
Microsoft Fabric
Azure Data Factory
Integration Services
Popular Articles
Date and Time Conversions Using SQL Server
Format SQL Server Dates with FORMAT Function
SQL Server CROSS APPLY and OUTER APPLY
SQL Server Cursor Example
SQL CASE Statement in Where Clause to Filter Based on a Condition or Expression
DROP TABLE IF EXISTS Examples for SQL Server
SQL Convert Date to YYYYMMDD
Rolling up multiple rows into a single row and column for SQL Server data
SQL NOT IN Operator
Resolving could not open a connection to SQL Server errors
Format numbers in SQL Server
SQL Server PIVOT and UNPIVOT Examples
Script to retrieve SQL Server database backup history and no backups
How to install SQL Server 2022 step by step
An Introduction to SQL Triggers
Using MERGE in SQL Server to insert, update and delete at the same time
How to monitor backup and restore progress in SQL Server
List SQL Server Login and User Permissions with fn_my_permissions
SQL Server Loop through Table Rows without Cursor
SQL Server Database Stuck in Restoring State
Company Filings | More Search Options
Company Filings More Search Options -->

- Commissioners
- Reports and Publications
- Securities Laws
- Commission Votes
- Corporation Finance
- Enforcement
- Investment Management
- Economic and Risk Analysis
- Trading and Markets
- Office of Administrative Law Judges
- Examinations
- Litigation Releases
- Administrative Proceedings
- Opinions and Adjudicatory Orders
- Accounting and Auditing
- Trading Suspensions
- How Investigations Work
- Receiverships
- Information for Harmed Investors
- Rulemaking Activity
- Proposed Rules
- Final Rules
- Interim Final Temporary Rules
- Other Orders and Notices
- Self-Regulatory Organizations
- Staff Interpretations
- Investor Education
- Small Business Capital Raising
- EDGAR – Search & Access
- EDGAR – Information for Filers
- Company Filing Search
- How to Search EDGAR
- About EDGAR
- Press Releases
- Speeches and Statements
- Securities Topics
- Upcoming Events
- Media Gallery
- Divisions & Offices
- Public Statements
Press Release
Sec, fincen propose customer identification program requirements for registered investment advisers and exempt reporting advisers.
FOR IMMEDIATE RELEASE 2024-54
Washington D.C., May 13, 2024 —
Today the Securities and Exchange Commission and the U.S. Department of the Treasury’s Financial Crimes Enforcement Network (FinCEN) jointly proposed a new rule that would require SEC-registered investment advisers (RIAs) and exempt reporting advisers (ERAs) to establish, document, and maintain written customer identification programs (CIPs). The proposal is designed to prevent illicit finance activity involving the customers of investment advisers by strengthening the anti-money laundering and countering the financing of terrorism (AML/CFT) framework for the investment adviser sector.
Under this proposal, RIAs and ERAs would be required to implement reasonable procedures to identify and verify the identity of their customers, among other requirements, in order to form a reasonable belief that RIAs and ERAs know the true identity of their customers. The proposed rule would make it more difficult for criminal, corrupt, or illicit actors to establish customer relationships — including by using false identities — with investment advisers for the purposes of laundering money, financing terrorism, or engaging in other illicit finance activity.
This proposed rulemaking complements a separate FinCEN proposal in February 2024 to designate RIAs and ERAs as “financial institutions” under the Bank Secrecy Act (BSA) and subject them to AML/CFT program requirements and suspicious activity report (SAR) filing obligations, among other requirements. That proposal cites a Treasury risk assessment that identified that the investment adviser industry has served as an entry point into the U.S. market for illicit proceeds associated with foreign corruption, fraud, tax evasion, and other criminal activities. Together, these proposals aim to prevent illicit finance activity in the investment adviser sector and further safeguard the U.S. financial system.
“The proposed rule is designed to make it more difficult to use false identities to establish customer relationships with investment advisers,” said SEC Chair Gary Gensler. “I support this proposal because it could reduce the risk of terrorists and other criminals accessing U.S. financial markets to launder money, finance terrorism, or move funds for other illicit purposes.”
“Criminal, corrupt, and illicit actors have exploited the investment adviser sector to access the U.S. financial system and launder funds,” said FinCEN Director Andrea Gacki. “This proposal would help investment advisers better identify and prevent illicit actors from misusing their services, while advancing a harmonized set of CIP obligations.”
The rule, if adopted, would require RIAs and ERAs to, among other things, implement a CIP that includes procedures for verifying the identity of each customer to the extent reasonable and practicable and maintaining records of the information used to verify a customer’s identity, among other requirements. The proposal is generally consistent with the CIP requirements for other financial institutions, such as brokers or dealers in securities and mutual funds.
The proposal is published on SEC.gov and will be published in the Federal Register. The public comment period will remain open for 60 days after publication of the proposing release in the Federal Register. A fact sheet on the Notice of Proposed Rulemaking is available.
Related Materials
- Rule Details

IMAGES
VIDEO
COMMENTS
In this article. Reporting Services provides an authentication subsystem and role-based authorization model. Authentication and authorization models vary depending on whether the report server runs in native mode or SharePoint mode. If the report server is part of a SharePoint deployment, SharePoint permissions determine who has access to the ...
Conclusion-SSRS 2012 Security. Implementing SSRS Security requires a two step approach. Object permissions must be granted at the database level while SSRS folder and report level permissions requires that a user be assigned to one or more SSRS roles. Several predefined roles exist and will suffice for much of your permission needs.
Failed at step #2. I got this message: User does not have required permissions. Verify that sufficient permissions have been granted and Windows User Account Control (UAC) restrictions have been addressed. - NoName. ... Open Reporting Services Configuration Manager -> then connect to the report server instance -> then click on Report Manager URL.
Domain\Service is the account Reporting Services would run under. This would need the RSExecRole on the ReportServer DB (this is granted during configuration/install). This account would have no data access or Reporting services access. Domain\rsAdmins is an AD group with the admins who manage content & permissions. Generally, this group would ...
Setting up permissions for a report is completed in the exact same way, except you are managing the report security and not the folder security. To begin the process, first select ellipse button ( 3 dots ) to the right of the folder and then pick Manage. Next select the security option.
The Management Studio SSRS Object Explorer allows for the following tasks: Maintenance and deletion of jobs. Creation, deletion, and maintenance of job schedules. Setup, deletion, and maintenance of regular roles. Setup, deletion, and maintenance of system roles. One big caveat with the SSMS interface stems from the fact that the SSRS ...
Not a direct answer to this question, but as an alternative and certainly very useful, I have followed the advise and link provided by Peter Vandivier in the comments above and doing some changes in the original script, like how to convert to VARBINARY(MAX) and even considered master.dbo.fn_varbintohexstr but it was too slow.. Here is the modified script, it gives all of the RDL files - it is ...
Provide the credential of the Windows Administrator Account. (Or a user that already member in the local administrator group). In Homepage > Click on Folder Settings. Click on Security > New Role Assignment. Type User / Group Name > Select the appropriate permission > OK. Try to login with the assigned user that should now have the required ...
Make sure that the current account that will be used to manage SSRS permissions is a member of the Local Administrator Group on the SSRS Server. Login to the SSRS (SQL Server Reporting Service ) Server. Open Server Manager > Tools > Computer Management.
you can use below script to set user permissions in Reporting services. I use this for set permission to a user on 250 reports and I found it easy to use. source: Using Powershell to set user permissions in Reporting Services
SCCM overwrites permission modification by using the role-based assignments stored in the site database. As per Technet : Configuration Manager connects to Reporting Services and sets the permissions for users on the Configuration Manager and Reporting Services root folders and specific report folders.
We currently assign permissions to Active Directory groups which are then used by SQL Server and SSRS to determine permissions. I want to know if there is a table within SSRS's metadata which tracks how permissions are assigned to reports. sql-server ... SQL Server 2008 Reporting Services permissions. 50. Reporting Services permissions on SQL ...
3. On the New System Role Assignment page, enter your group or user name and then select the System Administrator checkbox. Click on OK. 4. After clicking on OK, the system role assignments will be shown. 5. Next, click on Home in the top right and then click on Folder Settings. 6. Click on New Role Assignment.
Today the Securities and Exchange Commission and the U.S. Department of the Treasury's Financial Crimes Enforcement Network (FinCEN) jointly proposed a new rule that would require SEC-registered investment advisers (RIAs) and exempt reporting advisers (ERAs) to establish, document, and maintain written customer identification programs (CIPs).
You need to grant access rights to user you're accessing the reports server. There are MSDN tutorials for that: 1, 2, but short steps are: Open reports portal. Go to Settings page -> Security tab, and add your domain\user to the list of users as administrator. Go to reports page again. Click Manage folder, on opened page open Security tab.
I am new to SSRS and deployed my first report with it. When deploying the report, I added access to the site for the user group DOMAIN\\user-group with the "System User' role under Site Settin...