

Cybersecurity Capstone: Breach Response Case Studies Quiz Answers
- In Information Technology
- In IBM Cybersecurity Analyst Professional Certificate
- On April 1, 2024
All Weeks Cybersecurity Capstone: Breach Response Case Studies Quiz Answers
Table of contents, cybersecurity capstone: breach response case studies week 01 quiz answers, incident management knowledge check ( practice quiz ).
Q1. In creating an incident response capability in your organization, NIST recommends taking 6 actions. Which three (3) actions are included on that list? (Select 3)
- ‘Create an incident response policy
- ‘Develop an incident response plan based on the incident response policy
- Establish a formal incident response capability
Q2. Which incident response team model would best fit the needs of a small company that runs its business out of a single office building or campus?
- Central incident response team
Q3. True or False. An incident response team needs a blend of members with strong technical and strong soft skills?
Q4. Assuring systems, networks, and applications are sufficiently secure to resist an attack is part of which phase of the incident response lifecycle?
- Preparation
Cyberattack Frameworks Knowledge Check ( Practice Quiz )
Q1. According to the IRIS Framework, during which stage of an attack would the attacker conduct external reconnaissance, alight tactics, techniques, and procedures to target and prepare his attack infrastructure?
- Attack beginnings
Q2. According to the IRIS Framework, during which stage of an attack would the attacker escalate evasion tactics to evade detection?
- Launch and execute the attack
Q3. According to the IRIS framework, during the third phase of an attack when the attackers are attempting to escalate privileges, what should the IR team be doing as a countermeasure?
- Enforce strong user password policies by enabling multi-factor authentication and restricting the ability to use the same password across systems
Q4. According to the IRIS framework, during the fifth phase of an attack, the attackers will attempt execute their final objective. What should the IR team be doing as a countermeasure?
- Thoroughly examine available forensics to understand attack details, establish mitigation priorities, provide data to law enforcement, and plan risk reduction strategies
Q5. True or False. A data breach only has to be reported to law enforcement if external customer data was compromised?
Quiz 02 – Incident Management Response and Cyberattack Frameworks Graded Assessment ( Main Quiz )
- Considering the relevant factors when selecting an incident response team model
- Establish policies and procedures regarding incident-related information sharing
- Develop incident response procedures
Q2. Which incident response team model would best fit the needs of a the field offices of a large distributed organizations ?
- Distributed incident response team
Q3. Which incident response team staffing model would be appropriate for a small retail store that has just launched an online selling platform and finds it is now under attack? The platform was put together by its very small IT department who has no experience in managing incident response.
- Completely outsource the incident response work to an onsite contractor with expertise in monitoring and responding to incidents
Q4. Which three (3) technical skills are important to have in an organization’s incident response team ? (Select 3)
- System administration
- Programming
- Network administration
Q5. Identifying incident precursors and indicators is part of which phase of the incident response lifecycle ?
- Detection & Analysis
Q6. Automatically isolating a system from the network when malware is detected on that system is part of which phase of the incident response lifecycle?
- Containment, Eradication & Recovery
Q7. According to the IRIS Framework, during which stage of an attack would the attacker send phishing emails, steal credentials and establish a foothold in the target network?
Q8. According to the IRIS Framework, during which stage of an attack would the attacker execute their final objectives ?
- Attack objective execution
Q9. According to the IRIS framework, during the first stage of an attack, when the bad actors are conducting external reconnaissance and aligning their tactics, techniques and procedures, what should the IR team be doing as a countermeasure ?
- Build a threat profile of adversarial actors who are likely to target the company
Q10. According to the IRIS framework, during the fourth phase of an attack, the attackers will attempt to evade detection. What should the IR team be doing as a countermeasure?
- Analyze all network traffic and endpoints, searching for anomalous behavior
Q11. True or False. A data breach always has to be reported to law enforcement agencies.
Cybersecurity Capstone: Breach Response Case Studies Week 02 Quiz Answers
Phishing scams graded assessment.
Q1. Which three (3) techniques are commonly used in a phishing attack? (Select 3)
- Breaking in to an office at night and installing a key logging device on the victim’s computer.Sending an email with a fake invoice that is overdue.Make an urgent request to cause the recipient to take quick action before thinking carefully.
- Send an email from an address that very closely resembles a legitimate address.
Q2. You are working as an engineer on the design of a new product your company hopes will be a big seller when you receive an email from someone you do not personally know. The email is addressed to you and was sent by someone who identifies herself as the VP of your Product division. She wants you to send her a zip file of your design documents so she can review them. While her name is that of the real VP, she explains that she is using her personal email system since her company account is having problems. You suspect fraud. What kind of attack are you likely under?
- A phishing attack.
- A whale attack.
- A man in the middle attack.
- A spear phishing attack.
Q3. Phishing attacks are often sent from spoofed domains that look just like popular real domains. Which brand has been spoofed the most in phishing attacks?
Q4. Which feature of this email is a red flag, indicating that it may be a phishing attack and not a legitimate account warning from PayPal?
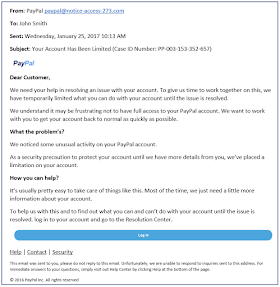
- Suspicious attachments
- There are spelling errors.
- Poor quality layout
- There is a hyperlink in the body of the email
Q5. Which three (3) of these statistics about phishing attacks are real? (Select 3)
- BEC (Business Email Compromise) scams accounted for over $12 billion in losses according the US FBI.
- 76% of businesses reported being a victim of phishing attacks in 2018.
- Phishing attempts grew 65% between 2017 and 2018.
- 94% of phishing messages are opened by their targeted users.
Q6. Which is the most common type of identity theft?
- Phone or utility fraud
- Loan or lease fraud
- Credit card fraud
- Government documents or benefits fraud
Quiz 02 – Point of Sale Breach Graded Assessment
Q1. Which group suffers from the most PoS attacks?
- Government agencies.
- Social media companies like Facebook and Instagram.
- Restaurants and small retail stores.
- Large online retailers like Amazon.com
Q2. Which three (3) of these control processes are included in the PCI-DSS standard? (Select 3)
- Maintain a vulnerability management program
- Protect cardholder data
- Require use of multi-factor authentication for new card holders
- Build and maintain a secure network and systems
Q3. Which three (3) of these are PCI-DSS requirements for any company handling, processing or transmitting credit card data? (Select 3)
- Encrypt transmission of cardholder data across open, public networks
- Use and regularly update antivirus software
- All employees with direct access to cardholder data must be bonded
- Develop and maintain secure systems and applications
Q4. Which three (3) additional requirements did the Ingenico Group recommend be used to enhance credit card transactions above and beyond the requirements found in PCI-DSS? (Select 3)
- Employee Education
- Mobile Device Management (MDM)
- Discontinue use of magnetic strip readers and cards
- Tokenization
Q5. When is credit card data most vulnerable to PoS malware ?
- After the card data has been received by the credit card processor
- While stored on the PoS device hard drive
- While in transit between the PoS device and the credit card processing center
- While in RAM
Q6. Which scenario best describes how a stolen credit card number is used to enrich the thief ?
- Credit card thieves sell stolen credit cards directly to carders using weekly dark web auctions. The carders then encode credit card blanks with the stolen numbers and resell the cards
- Credit card thieves resell stolen card numbers to dark web companies that use call-center style operations to purchase goods on behalf of customers who pay for them at discounted rates using real credit cards
- Credit card thieves use stolen credit cards to buy merchandise that is then returned to the store in exchange for store credit that is sold at a discount for profit
- Stolen credit card numbers are sold to brokers who resell them to carders who use them to buy prepaid credit cards that are then used to buy gift cards that will be used to buy merchandise for resale
Cybersecurity Capstone: Breach Response Case Studies Week 03 Quiz Answers
Third-party breach graded assessment.
Q1. True or False. According to a 2018 Ponemon study, organizations surveyed cited “A third-party misused or shared confidential information…” as their top cyber security concern for the coming year.
Q2. How effective were the processes for vetting third-parties as reported by the majority (64%) of the companies surveyed?
- Highly effective
- Somewhat or not effective
- Not effective at all
Q3. In the first few months of 2020 data breaches were reported from Instagram, Carson City, Amazon, GE, T-Mobile, radio.com, MSU, and Marriot. While different data were stolen from each organization, which two data elements were stolen from all of them ? (Select 2)
- Corporate financial data
- Confidential corporate strategy data
- Customer financial information
- Personal information
Q4. True or False. More than 63% of data breaches can be linked to a third-party.
Q5. According to a 2019 Ponemon study, which is the most common course of action for a consumer who has lost personal data in a breach ?
- Tell others of their experience
- Use social media to complain about their experience
- Comment directly on the company’s website
- File a complaint with the FTC or other regulatory body
Quiz 02 – Ransomware Graded Assessment
Q1. You get a pop-up message on your screen telling you have been locked out of your computer and that access will remain blocked until you pay a fee to have your access restored. What type of ransomware has attacked your system ?
- Leakware/Doxware
Q2. You get a pop-up message on your screen telling you that embarrassing photos taken of you at a college party many years ago have been downloaded and will be made public unless you pay a fee. What type of ransomware has attacked your system ?
Q3. You get an email from your Internet service provider addressed to “Dear Customer” asking you to log in and verify your credentials due to “suspicious activity” detected in your account. This email is most likely trying to exploit which attack vector ?
- Malicious Links
- Remote Desktop Protocol (RDP)
- Software Vulnerabilities
Q4. A person you meet at a party offers to help you optimize your computer so you arrange for her to log in remotely. The next time you reboot your system, you get a pop-up message telling you all your critical files have been encrypted and you must pay a ransome to get the encryption key. What attack vector was used to exploit your system?
Q5. You fear that the security patches sent out by the vendor of one of your products may introduce changes to what you are used to so you never allow the updates. What attack vector are you setting yourself up for ?
Q6. You log into your bank and see an offer for a 0% interest rate loan. You click on the link to check out the details and suddenly your computer is locked and there is a message demanding payment in order to unlock it. Your bank’s website was hacked! What attack vector was being used to install ransomware on your system ?
Q7. True or False. Being vigilant about email you receive, links your follow and websites you visit is an effective way to keep yourself safe from a ransomware attack.
Q8. Which ransomware used fake Adobe Flash download websites to distribute and install ransomware?
Q9. True or False. It is feared that in the future our cars, homes and factories may fall victim to ransomware attacks as more and more devices join the Internet of Things.
Next Course Quiz Answers >>
IBM Cybersecurity Analyst Assessment
<< Previous Course Quiz Answers
Cyber Threat Intelligence
All Course Quiz Answers of IBM Cybersecurity Analyst Professional Certificate
Course 01: Introduction to Cybersecurity Tools & Cyber Attacks
Course 02: Cybersecurity Roles, Processes & Operating System Security
Course 03: Cybersecurity Compliance Framework & System Administration
Course 04: Network Security & Database Vulnerabilities
Course 05: Penetration Testing, Incident Response, and Forensics
Team Networking Funda
We are Team Networking Funda, a group of passionate authors and networking enthusiasts committed to sharing our expertise and experiences in networking and team building. With backgrounds in Data Science, Information Technology, Health, and Business Marketing, we bring diverse perspectives and insights to help you navigate the challenges and opportunities of professional networking and teamwork.
Related Posts
Gmail coursera quiz answers – networking funda.
- September 29, 2022

Google Drive Coursera Quiz Answers – Networking Funda
- September 18, 2022

Google Calendar Coursera Quiz Answers – Networking Funda
Leave a reply cancel reply.
Your email address will not be published. Required fields are marked *
Save my name, email, and website in this browser for the next time I comment.
I accept the Privacy Policy *
Post Comment
Trending now

The marketplace for case solutions.
Case Study Solutions
Hundreds of case solutions at your fingertips! Case study answers written by top business students.
We are the marketplace for case study solutions
Save time and get inspired by our case solutions. We help you be a top student at your university!
High-quality only
Immediate access.

What Students Say About Us

I finished my assignment thanks to your solution. Thank you very much for this! Much better than what I expected. It was a great idea to let me sample it before I buy – many companies don’t do this, and what a wasted sale in my opinion! Best of luck! 🙂
U.S. News & World Report Education takes an unbiased approach to our recommendations. When you use our links to buy products, we may earn a commission but that in no way affects our editorial independence.

Cybersecurity Capstone: Breach Response Case Studies
About this course.
This course gives you the background needed to gain Cybersecurity skills as part of the Cybersecurity Security Analyst Professional Certificate program. You will explore incident response methodologies and security models. You will learn to recognize and categorize key types of vulnerabilities and associated attacks against today's organizations. You will explore in depth several past and recent breaches to learn how they were detected and what was done or could have been done to reduce the threat risk to the organization. Finally, you will explore the costs of data breaches through research studies and well known breaches. This course requires you to select and research a cybersecurity breach in the news today and apply your knowledge and skills from this course and previous cybersecurity courses to analyze the type of attack, attack timeline, vulnerable systems, and any missed opportunities. This project will be graded by your peers in the course. This course is intended for anyone who wants to gain a basic understanding of Cybersecurity or as the seventh and final course in a series of courses to acquire the skills to work in the Cybersecurity field as a Cybersecurity Analyst. The completion of this course also makes you eligible to earn the Cybersecurity Capstone: Breach Response Case Studies IBM digital badge. More information about the badge can be found https://www.youracclaim.com/org/ibm/badge/cybersecurity-breach-case-studies . In this course, you will learn to: ● Apply incident response methodologies. ● Research and describe a watering hole attack. ● Research and describe ransomware threats and the consequences to organization. ● Research and describe 3rd party breaches and how they affect an organization. ● Research and describe the effects of a phishing attack. ● Research and describe a point of sale attack and approximate cost of data breaches. ● Perform a case study on a current cyber attack and breach.
Add a Verified Certificate for $49 USD
Other Courses in this Specialization
Introduction to cybersecurity tools & cyber attacks.

Network Security & Database Vulnerabilities

Penetration Testing, Incident Response and Forensics

Cybersecurity Roles, Processes & Operating System Security

Cyber Threat Intelligence
IBM Cybersecurity Analyst Assessment

Cybersecurity Compliance Framework & System Administration

What Else Should I Know?
Computer Science
- JEE Main 2024
- MHT CET 2024
- JEE Advanced 2024
- BITSAT 2024
- View All Engineering Exams
- Colleges Accepting B.Tech Applications
- Top Engineering Colleges in India
- Engineering Colleges in India
- Engineering Colleges in Tamil Nadu
- Engineering Colleges Accepting JEE Main
- Top IITs in India
- Top NITs in India
- Top IIITs in India
- JEE Main College Predictor
- JEE Main Rank Predictor
- MHT CET College Predictor
- AP EAMCET College Predictor
- GATE College Predictor
- KCET College Predictor
- JEE Advanced College Predictor
- View All College Predictors
- JEE Main Question Paper
- JEE Main Cutoff
- JEE Main Advanced Admit Card
- JEE Advanced Admit Card 2024
- Download E-Books and Sample Papers
- Compare Colleges
- B.Tech College Applications
- KCET Result
Quick links
- Mechanical Engineering
- Civil Engineering
- Aeronautical Engineering
- Information Technology
- Electronic Engineering
B.Tech Companion Use Now Your one-stop Counselling package for JEE Main, JEE Advanced and BITSAT
- MAH MBA CET Exam
- View All Management Exams
Colleges & Courses
- MBA College Admissions
- MBA Colleges in India
- Top IIMs Colleges in India
- Top Online MBA Colleges in India
- MBA Colleges Accepting XAT Score
- BBA Colleges in India
- XAT College Predictor 2024
- SNAP College Predictor
- NMAT College Predictor
- MAT College Predictor 2024
- CMAT College Predictor 2024
- CAT Percentile Predictor 2023
- CAT 2023 College Predictor
- CMAT 2024 Admit Card
- TS ICET 2024 Hall Ticket
- CMAT Result 2024
- MAH MBA CET Cutoff 2024
- Download Helpful Ebooks
- List of Popular Branches
- QnA - Get answers to your doubts
- IIM Fees Structure
- Colleges Accepting Admissions
- Top Law Colleges in India
- Law College Accepting CLAT Score
- List of Law Colleges in India
- Top Law Colleges in Delhi
- Top NLUs Colleges in India
- Top Law Colleges in Chandigarh
- Top Law Collages in Lucknow
Predictors & E-Books
- CLAT College Predictor
- MHCET Law ( 5 Year L.L.B) College Predictor
- AILET College Predictor
- Sample Papers
- Compare Law Collages
- Careers360 Youtube Channel
- CLAT Syllabus 2025
- CLAT Previous Year Question Paper
Engineering Preparation
- Knockout JEE Main 2024
- Test Series JEE Main 2024
- JEE Main 2024 Rank Booster
Medical Preparation
- Knockout NEET 2024
- Test Series NEET 2024
- Rank Booster NEET 2024
Online Courses
- JEE Main One Month Course
- NEET One Month Course
- IBSAT Free Mock Tests
- IIT JEE Foundation Course
- Knockout BITSAT 2024
- Career Guidance Tool
- IPU CET BJMC
- JMI Mass Communication Entrance Exam
- IIMC Entrance Exam
- Media & Journalism colleges in Delhi
- Media & Journalism colleges in Bangalore
- Media & Journalism colleges in Mumbai
- List of Media & Journalism Colleges in India
- Free Ebooks
- Free Sample Papers
- NID DAT Exam
- Pearl Academy Exam
- Design Colleges in India
- Top NIFT Colleges in India
- Fashion Design Colleges in India
- Top Interior Design Colleges in India
- Top Graphic Designing Colleges in India
- Fashion Design Colleges in Delhi
- Fashion Design Colleges in Mumbai
- Top Interior Design Colleges in Bangalore
Predictors & Articles
- NIFT College Predictor
- UCEED College Predictor
- NID DAT College Predictor
- NID DAT Syllabus 2025
- NID DAT 2025
- NIFT Result 2024
- NIFT Fees Structure
- NIFT Syllabus 2025
- Free Design E-books
- List of Branches
- Careers360 Youtube channel
- AIIMS Nursing
- Top Medical Colleges in India
- Top Medical Colleges in India accepting NEET Score
- Medical Colleges accepting NEET
- List of Medical Colleges in India
- List of AIIMS Colleges In India
- Medical Colleges in Maharashtra
- Medical Colleges in India Accepting NEET PG
- NEET College Predictor
- NEET PG College Predictor
- NEET MDS College Predictor
- NEET Rank Predictor
- DNB PDCET College Predictor
- NEET Admit Card 2024
- NEET PG Application Form 2024
- NEET Cut off
- NEET Online Preparation
- Download Helpful E-books
NEET Companion Use Now Your one-stop Counselling package for NEET, AIIMS and JIPMER
- CUET PG 2024
- IGNOU B.Ed Admission 2024
- DU Admission 2024
- UP B.Ed JEE 2024
- LPU NEST 2024
- IIT JAM 2024
- IGNOU Online Admission 2024
- Universities in India
- Top Universities in India 2024
- Top Colleges in India
- Top Universities in Uttar Pradesh 2024
- Top Universities in Bihar
- Top Universities in Madhya Pradesh 2024
- Top Universities in Tamil Nadu 2024
- Central Universities in India
Upcoming Events
- CUET Exam City Intimation Slip 2024
- IGNOU Date Sheet
- CUET Mock Test 2024
- CUET Admit card 2024
- CUET PG Syllabus 2024
- CUET Participating Universities 2024
- CUET Previous Year Question Paper
- CUET Syllabus 2024 for Science Students
- E-Books and Sample Papers
- CUET Exam Pattern 2024
- CUET Exam Date 2024
- CUET Cut Off 2024
- CUET Exam Analysis 2024
- IGNOU Exam Form 2024
- CUET 2024 Exam Live
- CUET Answer Key 2024
- IT Colleges in Tamil Nadu
- IT Colleges in Uttar Pradesh
- MCA Colleges in India
- BCA Colleges in India
Quick Links
- Information Technology Courses
- Programming Courses
- Web Development Courses
- Data Analytics Courses
- Big Data Analytics Courses
Top Streams
- IT & Software Certification Courses
- Engineering and Architecture Certification Courses
- Programming And Development Certification Courses
- Business and Management Certification Courses
- Marketing Certification Courses
- Health and Fitness Certification Courses
- Design Certification Courses
Specializations
- Digital Marketing Certification Courses
- Cyber Security Certification Courses
- Artificial Intelligence Certification Courses
- Business Analytics Certification Courses
- Data Science Certification Courses
- Cloud Computing Certification Courses
- Machine Learning Certification Courses
- View All Certification Courses
- UG Degree Courses
- PG Degree Courses
- Short Term Courses
- Free Courses
- Online Degrees and Diplomas
- Compare Courses
Top Providers
- Coursera Courses
- Udemy Courses
- Edx Courses
- Swayam Courses
- upGrad Courses
- Simplilearn Courses
- Great Learning Courses
- NCHMCT JEE 2024
- Mah BHMCT CET
- Top Hotel Management Colleges in Delhi
- Top Hotel Management Colleges in Hyderabad
- Top Hotel Management Colleges in Mumbai
- Top Hotel Management Colleges in Tamil Nadu
- Top Hotel Management Colleges in Maharashtra
- B.Sc Hotel Management
- Hotel Management
- Diploma in Hotel Management and Catering Technology
Diploma Colleges
- Top Diploma Colleges in Maharashtra
- RUHS Pharmacy Admission Test
- Top Pharmacy Colleges in India
- Pharmacy Colleges in Pune
- Pharmacy Colleges in Mumbai
- Colleges Accepting GPAT Score
- Pharmacy Colleges in Lucknow
- List of Pharmacy Colleges in Nagpur
- GPAT Result
- GPAT 2024 Admit Card
- GPAT Question Papers
- CA Intermediate
- CA Foundation
- CS Executive
- CS Professional
- Difference between CA and CS
- Difference between CA and CMA
- CA Full form
- CMA Full form
- CS Full form
- CA Salary In India
Top Courses & Careers
- Bachelor of Commerce (B.Com)
- Master of Commerce (M.Com)
- Company Secretary
- Cost Accountant
- Charted Accountant
- Credit Manager
- Financial Advisor
- Top Commerce Colleges in India
- Top Government Commerce Colleges in India
- Top Private Commerce Colleges in India
- Top M.Com Colleges in Mumbai
- Top B.Com Colleges in India
- UPSC IAS 2024
- SSC CGL 2024
- IBPS RRB 2024
- NDA Application Form 2024
- UPSC IAS Application Form 2024
- CDS Application Form 2024
- CTET Admit card 2024
- HP TET Result 2023
- SSC GD Constable Admit Card 2024
- UPTET Notification 2024
- SBI Clerk Result 2024
- Previous Year Sample Papers
- Free Competition E-books
- Sarkari Result
- QnA- Get your doubts answered
- UPSC Previous Year Sample Papers
- CTET Previous Year Sample Papers
- SBI Clerk Previous Year Sample Papers
- NDA Previous Year Sample Papers
Other Exams
- SSC CHSL 2024
- UP PCS 2024
- UGC NET 2024
- RRB NTPC 2024
- IBPS PO 2024
- IBPS Clerk 2024
- IBPS SO 2024
- Top University in USA
- Top University in Canada
- Top University in Ireland
- Top Universities in UK
- Top Universities in Australia
- Best MBA Colleges in Abroad
- Business Management Studies Colleges
Top Countries
- Study in USA
- Study in UK
- Study in Canada
- Study in Australia
- Study in Ireland
- Study in Germany
- Study in China
- Study in Europe
Student Visas
- Student Visa Canada
- Student Visa UK
- Student Visa USA
- Student Visa Australia
- Student Visa Germany
- Student Visa New Zealand
- Student Visa Ireland
- CBSE Class 10th
- CBSE Class 12th
- UP Board 10th
- UP Board 12th
- Bihar Board 10th
- Bihar Board 12th
- Top Schools in India
- Top Schools in Delhi
- Top Schools in Mumbai
- Top Schools in Chennai
- Top Schools in Hyderabad
- Top Schools in Kolkata
- Top Schools in Pune
- Top Schools in Bangalore
Products & Resources
- JEE Main Knockout April
- NCERT Notes
- NCERT Syllabus
- NCERT Books
- RD Sharma Solutions
- Navodaya Vidyalaya Admission 2024-25
- NCERT Solutions
- NCERT Solutions for Class 12
- NCERT Solutions for Class 11
- NCERT solutions for Class 10
- NCERT solutions for Class 9
- NCERT solutions for Class 8
- NCERT Solutions for Class 7
Popular Searches
- CAT Percentile Predictor
- CAT Score Vs Percentile

- Cybersecurity Capstone Breach Response Case Studies
Cybersecurity Capstone: Breach Response Case Studies
Cybersecurity Capstone programme helps applicants in gaining required cyber security skills, to work as an expert Cyber security analyst.
The highlights
What you will learn.
- Admission Details
The syllabus
- Scholarship
How it helps
Similar courses, courses of your interest.
- More courses by provider
Quick facts
Course overview.
The use of computer systems to store and share data has led to the threat of cyber-attack and unauthorized access to sensitive data. This has given birth to a new branch in information technology which is named as Cybersecurity . Cybersecurity deals with the practices and processes that are made to protect data, devices, networks, and applications from damage and unofficial access.
The Cybersecurity Capstone: Breach Response Case Studies programme will provide a platform to the candidate, to attain necessary skills to work as a professional research analyst in Cybersecurity. By taking up the course, the participant will be exploring the methodologies related to incident response and the models of the security.
They will be getting insights, to categorise and recognise various important types of attacks and vulnerabilities at their workplace. Also, they will be exploring the breaches that happened in the recent past, to understand the process of identification of the threat and measures taken by the organisation to combat the threat and reduce its risks in future.
The participants will be provided with a project wherein they will be selecting a breach in cyber security, carry out analysis of the timeline of the attack, the effect of an attack on systems, by applying their knowledge and skills. The Cybersecurity Capstone: Breach Response Case Studies training course is for anyone who wants to learn the basics of cybersecurity and gradually attain expertise.
- Offered by IBM
- 100% online
- Flexible deadline
- Subtitles in English
- Shareable certificate
- Experiential learning by peer learning projects
Program offerings
- Practice exercise
- Pre-recorded videos
- Reading material
Course and certificate fees
One can start the course by getting a subscription to Coursera. A free trial of 7 days will be provided, after which the candidate will be charged Rs. 4,023 on monthly basis.
Fee details of Cybersecurity Capstone: Breach Response Case Studies
certificate availability
Certificate providing authority.
The participants will master the following skills:
- Describing ransomware threats and its repercussion on the organisation.
- Describing water hole attack after research.
- Applying methodologies of incident response.
- Explaining breaches by the third party along with its consequences.
- Report the point of sale attack and approximate the cost in case of data breaches.
- Understand the consequences of the phishing effect.
- Making a case study report on recent breach and cyber-attack.
Who it is for
Admission details.
Step 1: Visit the website of Coursera and choose the course- Cybersecurity Capstone: Breach Response Case Studies
https://www.coursera.org/learn/ibm-cybersecurity-breach-case-studies#
Step 2: To have complete access to the course material for 7 days, click on the hyperlink ‘Enroll for free’
Step 3: A pop up window will appear, read the details and click on ‘Start free trial’.
Step 4: Enter the details including card number, name on the card, expiry date, CVV, and name of the country will be asked to the candidate.
Step 5: Get started with 7 days of free trial after entering the required details.
Week 1: Incident Management Response and Cyber Attack Frameworks
- NIST Incident Response Lifecycle - Teams
- NIST Incident Response Lifecycle
- What is a Breach?
- Target Attack Timeline
- IBM X-Force IRIS Cyberattack Framework
- Target Attack Vulnerabilities
- Watering Hole Attack
- Course introduction
- Earn an IBM digital badge
- Apply Incident Response
- X-Force Command Center
- X-Force Threat Intelligence Index 2023
Practice exercises
- Incident Management Knowledge Check
- Cyberattack Frameworks Knowledge Check
- Case Studies Knowledge Check
- Incident Management Response and Cyberattack Frameworks Graded Assessment
Week 2: Point of Sale Breach
- Point of Sale Breach Overview
- PoS Case Study - Home Depot
- PoS Malware
- PoS Skimming
- The Cyber Kill Chain in PoS Breaches
- Introduction to Point of Sale Attacks Knowledge Check
- PoS Case Study: Home Depot Knowledge Check
- Point of Sale Breach Graded Assessment
Week 2: Phishing Scams
- Phishing Scams Overview
- Impact of Phishing
- Phishing Email Study
- Phishing Case Study: Google & Facebook
- Exploring Steps to Recovery
- Can You Spot the Difference?
- Introduction to Phishing Scams Knowledge Check
- Phishing Case Study Knowledge Check
- Phishing Scams Graded Assessment
Week 3: Ransomware
- Ransomware Overview
- Examples of Ransomware
- Ransomware Case Study - City of Atlanta
- Emerging Trends in Ransomware
- Ransomware of Things
- Ransomware Knowledge Check
- Ransomware Case Study Knowledge Check
- Ransomware Graded Assessment
Week 3: 3rd Party Breach
- 3rd Party Breach Overview
- 3rd Party Breach - Quest Diagnostics
- 3rd Party Breach Impacts
- List of 3rd Party Breaches
- Breach Plan
- Third-Party Breach Knowledge Check
- Third-Party Breach Graded Assessment
Week 4: Apply Your Skill - Data Breaches
- Introduction to the Peer-to-Peer Applied Project - Data Breaches

Scholarship Details
Financial aid is provided in which the participant will get access to all the learning material and certification. One can apply for financial aid by following the steps given below:
- Visit the official site of Coursera https://www.coursera.org/learn/ibm-cybersecurity-breach-case-studies#
- Click on the tab containing hyperlink which states ‘Financial help available.
- A pop-up window will appear, wherein the participants will be provided with options like Enroll and start learning today or continue the application (for getting financial aid).
- If the participant chooses to get any financial aid, then they need to choose the option-Continue the application.
- There will be terms and conditions with check box bullets. The participant needs to tick the bullets to accept the terms and conditions.
- Further, an application form will appear where the candidate will be asked for the background information and some of the descriptive questions.
- After answering all the questions, the candidate need to click on Submit application
- It may take around 15 days for the review of the application, after which the candidate will be informed further.
Cybersecurity has emerged as a key area for job and career growth. Cybersecurity certification seems the most brilliant and viable career option in information technology. With the emergence of concepts like big data , IoT , and cloud computing the magnitude of the importance of cybersecurity has increased immensely. Apart from this, Cybersecurity Capstone: Breach Response Case Studies classes course offers a global exposure to applicants where the expert can travel overseas to serve their skills.
As cyber-crimes are increasing day by day, cybersecurity withholds due importance in order to maintain availability, confidentiality, and integrity of the data. By helping police forces and national crime agencies one can do a greater good to the country too. This makes the cybersecurity job as most rewarding and satisfying.
In the Cybersecurity Capstone: Breach Response Case Studies programme the participants will be exploring the framework of cyber-attack and response during incident management. They will get an opportunity to conduct a case study on two corporations who have suffered phishing attacks. They will also learn the impact of point of sale breaches on the organisation through case studies. They will be choosing a particular company, to identify data breaches, susceptibility, and its cost to the company by applying their knowledge and skills.
The access to assignments and lectures depends on the type of enrolment chosen by the entrant. If s/he chooses to audit the course, then s/he can only view the free course material. To get access to graded assignments, the participants have to purchase the certificate during or after the audit.
The participants are provided with videos, practice exercise, reading material along with assignments and quizzes as a part of the assessment.
As the course is a subset of various other courses, it is being applied to various professional certificate and Specialisation programmes. Successful completion of the course will be considered while applying for other courses like IBM Cybersecurity Analyst Professional Certificate and Security Analyst Fundamentals Specialization.
On subscribing to Coursera, there is a deduction of fees every month. After the free trial of seven days ends, the candidate will be charged monthly fees by auto-deduction, if s/he forgets to cancel the subscription. Although, the participant can cancel the subscription at any time to avoid deductions from the following month.
Yes, the participant is free to enrol for more than one course at a time.
There is an availability of financial aid. To apply, the participant needs to fill up an application form and they will be intimated about the status after about 15 days.
No, there is no provision of language options other than English.
The course is being instructed by IBM Global Subject Matter Experts working in IBM Security Learning Services. The teaching is rated 4.5/5 by the previous candidates of the course.
After subscribing to Coursera, the candidate will receive the certificate after successful completion of the course. As the certificate is in electronic form, it provides an ease to share it online, and link it to CV and LinkedIn profile. In case the candidate opts for the audit the course then there will be no provision of the certificate.
Popular Articles
Latest Articles

Threat Intelligence Lifecycle Fundamentals
IBM via Edx

Information Technology Fundamentals for Business P...
Polytechnic University of Valencia, Valencia
Polytechnic University of Valencia, Valencia via Edx

Introduction to the Threat Intelligence Lifecycle
IBM via Coursera

Introduction to Cybersecurity Essentials

Check Point Jump Start Cloud Security
Check Point Software Technologies Limited
Check Point Software Technologies Limited via Coursera

Cybersecurity and Privacy in The Internet of Thing...
Curtin University, Perth
Curtin University, Perth via Edx

Cyber Security Certification
Board Infinity

Security Operations Center - SOC with Splunk and F...

Healthcare Data Security Privacy and Compliance
Johns Hopkins
Johns Hopkins via Coursera

Digital Security Training Cyber Threats and Risk M...
Coventry University, Coventry
Coventry University, Coventry via Futurelearn

An Introduction To Coding Theory
IIT Kanpur --> via Swayam
C++ Foundation
PW Skills -->
Data Science Foundations to Core Bootcamp
Springboard -->

NDG Linux Unhatched Essentials Linux I and II
Sona College of Technology, Salem -->

Full Stack Developer Course With Placement
AttainU -->

User Experience Design And Research
UM–Ann Arbor --> via Futurelearn

Data Analysis with Excel for Complete Beginners
CloudSwyft Global Systems, Inc --> via Futurelearn

Artificial intelligence Design and Engineering wit...

Data Science Fundamentals on Microsoft Azure
Artificial intelligence projects.
Great Learning -->
More Courses by IBM
Artificial intelligence chatbots without programmi..., r programming basics for data science, introduction to data engineering, relational database administration, introduction to web development with html css java..., introduction to devops, data scientist career guide and interview preparat..., data analyst career guide and interview preparatio..., introduction to software programming and databases, introduction to networking and storage, trending courses, popular courses, popular platforms, learn more about the courses.
The Brochure has been downloaded and sent to your registered email ID successfully.
Brochure has been downloaded.
Sign In/Sign Up
We endeavor to keep you informed and help you choose the right Career path. Sign in and access our resources on Exams, Study Material, Counseling, Colleges etc.
Help us to help you.
Download the Careers360 App on your Android phone
Regular exam updates, QnA, Predictors, College Applications & E-books now on your Mobile

- 150M + Students
- 30,000 + Colleges
- 500 + Exams
- 1500 + E-books

You’re using an older browser version. Update to the latest version of Google Chrome , Safari , Mozilla Firefox , or Microsoft Edge for the best site experience.
- eLearning Blog
- eLearning Basics
- Instructional Design
- Corporate Training
- Course Selling
- Manufacturing
- Products iSpring Suite iSpring Learn
- Use Cases Onboarding Compliance Training Induction Training Product Training Channel Partner Training Sales Training Microlearning Mobile Learning
- Company About Us Case Studies Customers Partnership Course Development Contact Us
- Knowledge Hub Knowledge Hub Academy Webinars Articles Guides Experts on iSpring
- Language EN English Français Deutsch Español Italiano Nederlands Português Polski 中文 日本語 العربية Indonesia
- Shopping Cart
Knowledge Checks in eLearning: Assess to Success

Table of Contents

Basic comprehension questions
Objective example 2: Applied knowledge
Your learner can demonstrate their ability to apply what they know by answering a question that measures more than just basic comprehension. These question types are a great way to confirm knowledge application.

Knowledge application questions
Objective example 3: Processes and procedures
There are some cases when you need to show step-by-step processes and procedures. Use these question types to confirm that your learner is able to comprehend and follow processes and procedural steps.

Process and procedure questions
Objective example 4: Feedback
You may wish to solicit feedback from learners on the quality and helpfulness of the learning materials you create. Feedback surveys can provide a structured format to receive and review input directly from the learning audience. Use Likert Scale questions to customize an array of response options. You can also use Numeric, Multiple Choice, and Short Answer questions for these purposes. For in-depth personal feedback, include an Essay question.

Feedback questions
Knowledge check question examples
Now, when you have an overall picture of how various question types can achieve different learning goals, let’s take a closer look at specific questions and how you can apply them for different training needs.
Prove or apply knowledge: Finding the Hotspot
Hotspot questions are a great way for learners to prove that they can interpret an image and identify or locate a specific element of, or item within, that image. Here are some ways that a Hotspot question can be used to prove knowledge application.
Check out how to create a hotspot question for an online quiz →
Meet a performance standard: Drag the Words
Some tasks need to be completed with uniform precision. Drag the Words questions are a good way for learners to prove that they can select the correct standard when faced with an array of choices. Add some extra distractors so your learners can’t randomly guess the answers.
Follow a process or procedure: A Sequence of Events
Sequence questions are an excellent way for a learner to prove that they can identify the steps of a process or procedure, then execute the steps in the correct order. This is a good question type to use for medical or first aid, cooking, legal or criminal justice, and project management training modules .
How to Build Knowledge Check Questions
Start with a question bank! A question bank is a great way to develop a stockpile of questions for use in quizzes and knowledge checks. You can copy, paste, edit, or re-purpose any item in your question bank for future projects, which can be a great time saver.
iSpring QuizMaker will save your quiz questions as a question group by default. These groups can become the question banks you draw from for knowledge check questions and assessments.
Let’s look at how to create and save a quiz question.
Creating a Multiple Response question
Step 1: Open iSpring QuizMaker
To get started, open iSpring QuizMaker and select Graded Quiz .

Step 2: Select Question Type
The graded quiz view will open. Click on the Question tab in the top left corner of the screen and choose Multiple Response .

Step 3: Enter your Questions and Answers
The page will open in Form View . Enter your question text and answers. Be sure to indicate which choices are correct.

Step 4: Design your slide
You can give your slide additional visual appeal by adding an image or changing font size or color. Click on Slide View to see how your slide will appear to learners.

This slide is rather plain. You can import an image to add visual appeal. Click the Insert tab, then select Picture to add a saved image from your hard drive.

The default slide size is 720 pixels wide by 540 pixels high. Be sure to size your image correctly so that it fits within the slide.
After you insert and size the image, click the Format tab, then Send to Back . This will ensure that all of your text is visible on the screen. Place the image on the slide and re-color text for visibility, if needed.

Step 5: Set your slide options
You can set parameters to deliver customized feedback and scoring options for each question on your quiz using the choices from the drop-down menus in the Slide Options panel on the right side of your screen.
- All feedback will be disabled for your question if you choose None as the feedback option. (Most course designers will rarely choose this option.)
- Select By Result to give feedback based on whether the learner’s answer choices were correct, incorrect, or partially correct.

- Enter Feedback and Branching information to redirect the learner based on whether their answer is correct, incorrect, or partially correct.
- Add information or hints in the Feedback field to help your learners correct mistakes.
Add branching options to take learners back to specific pages in the module to review information specific to this knowledge check question.
- Select By Result to compute the learner’s score based on whether the answer was completely correct.
- Select By Choice to give the learner partial credit for selecting some, but not all, of the correct answers.
Limit the number of attempts each learner can make to answer the question. For most question types, it’s best to allow no more than two attempts. For True/False questions, allow only one attempt to answer correctly.

HINT: Putting a limit on the number of times each learner may try to answer a question increases the likelihood that correct answers are the result of actual knowledge, not guesswork or elimination of any known wrong answers.
Step 6: Save and update your question bank
Click the drop-down arrow next to the File icon at the top left of the screen. Select Save , then choose a location and enter a name for your quiz.

You can continue to add questions to this group (or bank) of questions anytime.
Creating a Drag and Drop question
A Drag and Drop question is an effective and, at the same time, engaging way for learners to show their ability to apply what they know. In this question, they must drag text boxes, pictures, and/or shapes to the specified places on the slide.
For our Waste Sorting quiz, let’s create a knowledge check question that requires learners to put the waste into the right recycling bin.
Step 1: Add a question
Click the Questions tab on the top left of the ribbon to display the question types available. Select Drag and Drop (NOTE: If you mouse over the image, a thumbnail will pop up with information about the question type. )

Step 2: Switch from Form View to Slide View
The question opens in Form View by default. Click the Proceed button to switch views.

Step 3: Add images to the Slide View
For this task, let’s upload a picture of the frying pan and the images of the ingredients you want a learner to drop in the pan. Edit the headline text box to provide instructions for your learners.

Step 4: Identify correct matches in Form View
After placing all the content on your screen, click to return to Form View . Click the down arrow next to the first item in the Drop Target column under Correct Matches . Select the image that the first item in the Drag Item column should be dropped to. In this example, the picture of eggs should be dropped in the frying pan. Continue matching each correct Drag Item to its Drop Target until you’re finished.

Step 5: Select your Slide Options
Specify the Feedback Type, Score, and number of Attempts for this question.
HINT: If you allow more than two attempts, you may want to limit the time allowed to answer the question. A time limit will reduce the possibility that a learner may get full credit through the process of trial-and-error with each ingredient.

Step 6: Select your Drag and Drop Options
You can set a default to specify how drag items will snap to a target and stack onto the target.

Want to learn more about this question type? Watch a video tutorial on how to create a Drag and Drop question.
As you can see, the process for creating a question type is fairly intuitive, once you’re familiar with the iSpring Suite interface.
How to Enhance Knowledge Checks
Knowledge checks are a way for learners to review their learning progress and see where any gaps exist. When questions are too easy, learners can feel overly confident. Extremely difficult knowledge check questions can scare learners away from a topic. Pay attention to these details so that you strike the right balance with each knowledge check question:
- Random Distribution of Questions: Setting your knowledge check to randomly select questions from a question bank means that the learning experience will be slightly different for each learner. Unique experiences decrease learners’ ability to cheat or collude on an assessment.
- Time Limits: Time limits to answer a question can decrease learners’ ability to cheat on an assessment by requiring fast action to answer a question.
- Number of Attempts: Allowing your learners more than one chance to answer a question correctly can also increase learner motivation and engagement with the content.
- Branching: Branching subtly steers learners back to content for review, rather than simply passing everyone forward. You can use branching to send a learner back to the content to review a problematic issue. You can set your knowledge check questions to branch based on the response chosen.
- Feedback: You can choose not to provide any feedback to your audience, but providing feedback by result allows you to customize a response based on their actual performance.
Incorporating several knowledge checks throughout an eLearning course is a great way to prepare your learners for success. An authoring tool such as iSpring Suite allows you to create and customize an array of knowledge check question types.
Ready to take your eLearning to the next level? Get a free iSpring QuizMaker trial right now.
Easy Quiz Maker
Create interactive quizzes for learning, knowledge checks, and skill practice

Content creator:
Helen Colman
She enjoys combining in-depth research with expert knowledge of the industry. If you have eLearning insights that you’d like to share, please get in touch .
You might also like this

Subscribe to our blog
Stay tuned to get our latest eLearning tips and tricks!
By clicking “Subscribe”, you agree to our Privacy Policy . All emails include an unsubscribe link, so that you can opt-out at any time.
We use cookies to give you the best possible experience on our website and also for analytics and marketing purposes. You can enable or disable optional cookies as desired. See our Cookie Policy for more details.
Manage your cookies
Essential cookies are always on. You can turn off other cookies if you wish.
Essential cookies
Analytics cookies
Social media cookies
Online Case Study Answer Generator for Students
Here Is Your Case Study Analysis
If you want to quickly and effectively carry out case study analyses, you’ve come to the right place. Just for you, we’ve created a free AI-powered tool that can analyze case studies on any subject!
Our app will be the perfect solution for those who don’t want to spend a ton of time structuring their texts and looking for examples. Use it to save time and nerves!
- ️🎉 Benefits of Our Generator
- ️🤖 How to Use
- ️✨ Case Study Definition
- ️🔎 Structure of a Case Study
- ️✍️ Writing Steps
- ️🔝 Top 12 Topics & Examples
- ️🔗 References
🎉 Benefits of Our Case Study Analysis Generator
Our generator is one of the best, and there are many reasons for us to say so:
🤖 How to Use Our Case Study Answer Generator
Getting a case study analysis has never been easier—see for yourself!
- Paste your case study into the field.
- Add questions or issues you need to address in your analysis.
- Press “Analyze now.”
- Get the results!
Keep in mind that the results provided by the tool are to be used for reference purposes only.
✨ Case Study Analysis Definition
A case study analysis is used to examine a problem and find a solution to it. This type of analysis is typically used in business as well as in other spheres, such as education, healthcare, and social sciences. The main feature of such a study is that it’s rooted in a real-life context.

Researchers use direct observations, interviews, tests, and samples to gather data for their case studies. This information is then used to develop solutions and recommendations backed with evidence.
🔎 Structure of a Case Study Analysis
Usually, a case study analysis consists of 6 parts. Each one is dedicated to a particular aspect and serves its own purpose. Let’s take a closer look at them and see how they differ.
Introduction
An introduction describes the context of the examined topic and provides substantial background on the case study’s subject. When you write it, keep in mind the following questions:
- What is your case study about?
- What is the primary goal of your research?
- Why is it important?
Problem Statement
The next part introduces the main problem or issue the study will be focusing on. Typically, it’s concerned with a challenge faced by an individual or organization in question. The problem statement provides a clear focus for the whole research.
Now, it’s time for the most interesting part—the analysis itself. When it comes to business problems, students can use various approaches, such as:
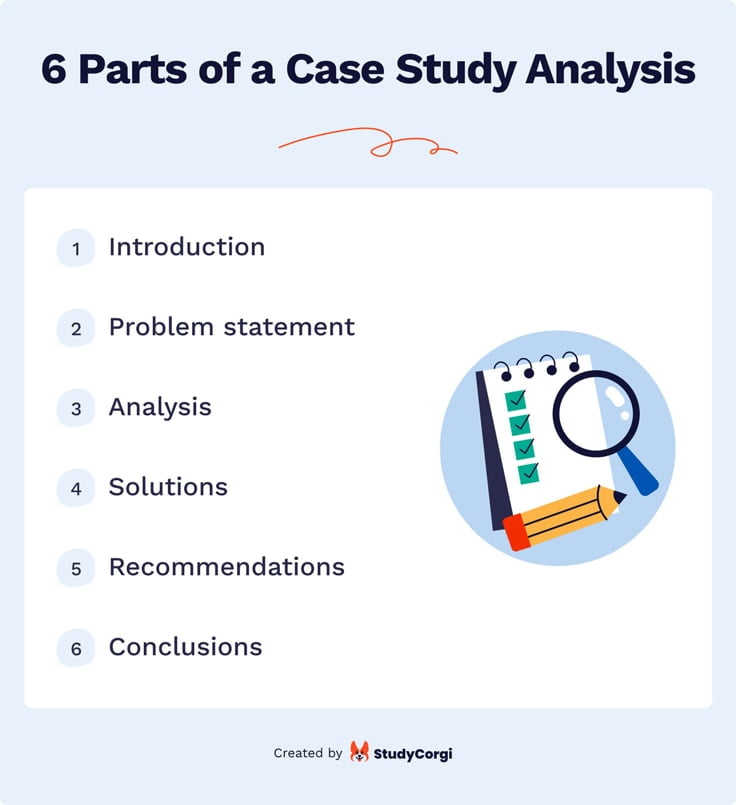
This part presents several ways to resolve the issue in question. The solutions must be realistic and achievable. It’s also worth to mention their pros and cons and thus identify the most potent ones.
Recommendations
This part focuses on the best possible solutions to the problem identified in the previous section. It explains how to implement it in practice and how it will help eliminate the issue. It may also suggest ways to deal with other, minor problems involved in the case.
Conclusions
Now, it’s time for the final part of the analysis: your conclusions . Here is what you need to do:
- Summarize the results of your case study analysis and explain how they relate to the research’s main problem.
- Be sure to emphasize how vital your study is and how it helps to make the issue more manageable.
- Make further suggestions based on your findings.
✍️ How to Write a Case Study
Now you know what to include in your case study. But how do you write one that is truly outstanding? Just follow our step-by-step guide:
1. Pick a Case to Explore
Choosing the right topic is essential. You need to do it early on to ensure that the research subject is sufficiently explored.
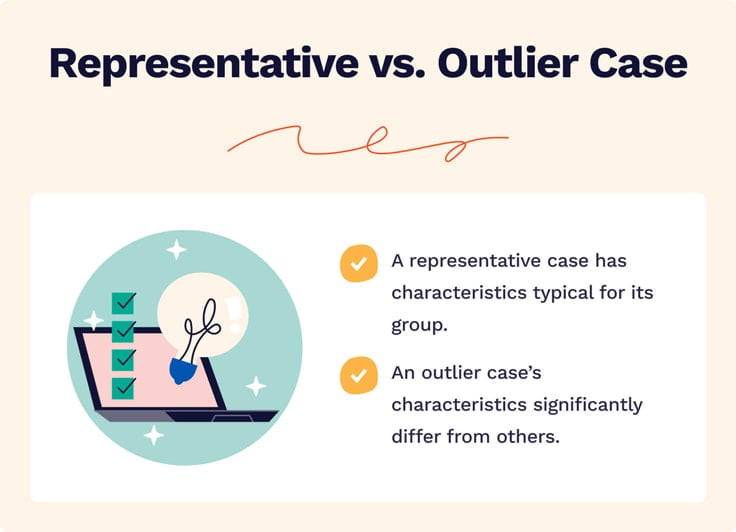
For example, suppose you want to examine how COVID-19 has affected the hospitality sector. In that case, you can choose either a representative case, such as a large hotel chain, or an outlier case, such as a small Bed and Breakfast that has managed to survive the pandemic. The latter case may sound more interesting, but if there's not enough information available on it, it's best to choose the former.
2. Formulate a Problem Statement
Now, you should clearly and concisely formulate the central problem you will be focusing on. To do it, answer the 5 Ws:
- What is the problem you’re researching?
- Who is affected by it?
- Where does it occur?
- When did the problem arise?
- Why is this issue significant?
If you need help with this part of your analysis, you can always use our research problem generator .
3. Gather Evidence & Collect Data
Data gathering can be done through both primary and secondary sources of information . You can use a range of research techniques, such as observations, surveys, and interviews. It is crucial to make sure the data you’ve collected is pertinent to the case study.
4. Describe Your Findings & Analyze Them
Next, you analyze trends and themes in your data. This analysis must be supported by facts and evidence. Use various analysis methods to make your study more in-depth.
5. Provide Solutions & Recommendations
Develop several possible solutions using the information you’ve gathered. Once you’ve done it, answer the following questions:
- What are the pros and cons of these solutions?
- Which one can be the most beneficial?
- How can the entity you’re analyzing implement it in practice?
The more detailed your recommendations are, the better. If possible, try to include aspects such as timeline, resource allocation, and KPIs for monitoring.
🔝 Top 12 Case Study Topics & Examples
Want inspiration for your analysis? Or maybe you need help picking a case to explore? Check out this list of topics with examples!
- Operations and Information Management: A Case Study of CC Music
- Netflix and Blockbuster: Case Study
- Strategic Planning Case Study: Process Management
- HRM Incident: Case Study Analysis
- Case Study Summary: Hiring a Sustainable Development Specialist
- Organizational Change: Qatargas Case Study
- Childhood Development Case Study
- Case Study of Engstrom Auto Mirror Plant and Workplace
- Strategic Marketing: Amazon Go Case Study
- Cognitive Behavioral Therapy: Case Study
- Social Determinants of Health: Case Study
- Recovering Supply Chain Operations: A Case Study of Nissan
Now you know how to complete a case study! Remember that the tiring process of analyzing can be effectively streamlined if you use our free case study answer generator. Try it out—you won’t regret it!
We also recommend using our transition words maker and personal statement generator to enhance your writing.
❓ Case Study Analysis Generator: FAQ
❓ what questions to answer in a case study.
A case study must either prove or disprove an existing theory. It also aims to find a solution to the research's central question. This question can vary depending on your topic and subject. You present the answer in your research findings and conclusions.
❓ How Do You Write a Case Study Analysis?
First, you introduce your case and provide its background. Then, you gather information and analyze it to develop several solutions. Finally, you propose the best solution and give recommendations on how to implement it. Also, remember to explain how your case study will deepen the existing knowledge.
❓ What Are the 4 Most Important Parts of Case Study?
Every case study begins with the introduction of a topic and its background. Then, you present an analysis of sources that can provide knowledge on the case. The third part is the analysis of collected data. Your case study ends with conclusions based on your findings.
❓ What Are Some Examples of Case Studies?
Case studies are frequently used in psychology to shed light on peculiar circumstances. Famous case study examples include Sigmund Freud's Little Hans as well as John Martin Marlow's study of Phineas Gage, the man who had a railroad spike driven through his brain.
🔗 References
- Case Study: Definition, Examples, Types, and How to Write: Verywell Mind
- What Is a Case Study?: Evidence Based Nursing
- What the Case Study Method Really Teaches: Harvard Business Review
- Using Case Studies to Teach: Boston University
- What Is a Case Study? Definition, Elements and 15 Examples: Indeed
- Writing a Case Study: University of Southern California
- Writing a Case Study – Student Academic Success: Monash University

Niyander Tech
Learn with fun
- Coursera Answers
IBM IT Support Professional Certificate Coursera Quiz Answers
In this article i am gone to share IBM IT Support Professional Certificate All Courses Quiz Answers with you..
IBM IT Support Professional Certificate
Prepare for a career as an IT support specialist. Gain the in-demand skills and hands-on experience to get job-ready in as little as 3 months. No prior experience required.
Professional Certificate – 9 course series
Prepare for an in-demand career in Information Technology (IT). In this program, you’ll develop a strong foundation in IT fundamentals, networking, cybersecurity, and cloud computing to get job-ready in as little as 3 months, with no prior experience or degree needed to get started.
Almost every organization, business, or individual relies on technology. A career in IT Support is about providing technological assistance to better optimize organizational efficiency. This can include troubleshooting, setting up computers, setting up network & wifi, along with providing excellent customer service.
You’ll learn the latest skills and tools used by IT support professionals including hardware and software setup, technical support, customer service, ticketing systems, service level agreements, and troubleshooting. You’ll demonstrate your knowledge of networking, security, and cloud computing, and practice analyzing user help requests and troubleshooting various issues.
When you successfully complete the program, you’ll have a portfolio of projects to demonstrate your proficiency, a Professional Certificate from IBM to showcase your job readiness to potential employers, and you’ll receive exclusive access to career support resources to help you in your job search.
You’ll also be prepared to take the CompTIA ITF+ certification exams and receive a 30% discount voucher for the certification exams like A+. | Enrol Now |
Applied Learning Project
The IBM Technical Support Professional Certificate provides more than 70 hours of instructional videos and engaging hands-on interactive exercises, labs, projects and practice tests.
The skills you’ll gain through labs and projects include hardware & mobile device setup, software configuration, Windows/Linux usage, GUI & command line, troubleshooting procedures, IT helpdesk & ticketing systems, customer service & tech support best practices, network & wifi setup, cloud computing & cybersecurity fundamentals, and much more.
In the final capstone course, you will apply your knowledge and skills to real-world case studies, and upon completion, will be able to confidently demonstrate your IT support skills to prospective employers.
Course staff and teaching assistants are available throughout the program to support your success.
Select your Course and open in the new tab to get Answers
Course 1: Introduction to Technical Support
Course 2: Introduction to Hardware and Operating Systems
Course 3: Introduction to Software, Programming, and Databases
Course 4: Introduction to Networking and Storage
Course 5: Introduction to Cybersecurity Essentials
Course 6: Introduction to Cloud Computing
Course 7: Practice Exam for CompTIA ITF+ Certification
Course 8: Technical Support (IT) Case Studies and Capstone
Graded Case Study: Computer Hardware and Software Specifications Quiz Answers
Graded Case Study: System Software, Versions, and Application Software Compatibility Quiz Answers
Graded Case Study: Configure, Test, and Troubleshoot a SOHO Network Quiz Answers
Graded Case Study: Public Browsing Safety Quiz Answers
Graded Case Study: Cloud Service and Deployment Models Quiz Answers
Exam – Cloud Computing Basics Quiz Answers
Graded Quiz: Final Exam Quiz Answers
Course 9: Tech Support Career Guide and Interview Preparation
2 thoughts on “ IBM IT Support Professional Certificate Coursera Quiz Answers ”
Course 6: Introduction to Cloud Computing https://niyander.com/introduction-to-networking-and-cloud-computing-coursera-quiz-answers/
Link is wrong
I apologize for the inconvenience caused. Now link is updated.
Leave a Reply Cancel reply
Your email address will not be published. Required fields are marked *
Save my name, email, and website in this browser for the next time I comment.
- GDPR Privacy Policy
- Privacy Policy
- Terms and Conditions
Greetings, Hey i am Niyander, and I hail from India, we strive to impart knowledge and offer assistance to those in need.
CASLI Resources
Sample case studies answers.

Case Study #1
What should the interpreter do?
- Ask the agency for materials regarding the meeting in order to prepare sufficiently.
- Research the organization to be fully prepared for the job.
- Inform agency that a team interpreter is not needed.
- Ask for a team with Deaf interpreters.
- Set up ground rules for turn-taking during the meeting.
- Ask for more interpreters to be included on the team.
- Ask the participant with low-vision to move to a seat preferred by the interpreters.
- Confer with key meeting members about communication logistics.
- Contact the agency and ask for a team of Deaf interpreters.
- Tell the Deaf supervisor that the interpreters cannot provide interpreting service for low-vision participants.
- Confer with the team interpreter and decide on how to provide the interpretation most effectively.
What should the interpreters do?
- Alert the participants as it is getting close to the end of the meeting that the interpreters may need to leave.
- Contact the agency to see if arrangements can be made to cover the continuation of the assignment.
- Wait until the time they were scheduled to end and leave the meeting.
- Continuing interpreting until the end of the meeting.
- The first interpreter should ask the second interpreter to stay longer, so the first interpreter can leave.
Case Study #2
What should the interpreter do?
- Say that there is no confidentiality because the interpreter is like a staff member in that program .
- Continue interpreting so the two residents can continue to bond.
- Report the situation to the interpreter’s supervisor at the agency .
- Encourage the two residents to continue chatting on their own using paper and pen to maintain the confidentiality of their conversations.
- Make up an excuse to be able to stop interpreting the conversation.
- Excuse them self and tell the conversation to the group counselor .
- Continue the interpretation without any further action.
- Leave to complete the other assignments on the interpreter’s calendar without taking any action.
- Post on a social media site that the interpreter is having a bad day.
- Call another certified interpreter friend to confide in but leave out any identifying information and ask for advice upon next actions to be taken .
- Cancel the next two appointments of the day saying they are sick.
- Call the child protective services to report the situation .
- Research state laws regarding mandatory reporting .
- De-stress by going home and confiding in their partner the incident including the identifying information for an advice upon next action to be taken.
- Decide not to interpret there any more due to the conflict of interest.
- Report the alleged incident to the interpreter’s agency director.
- Not to do anything about reporting the incident because of the Deaf resident’s history.
- Offer to sit outside the isolation room with the Deaf resident if the interpreter can manage their emotions.
- Attend group support meetings to relieve the emotional stress from the interpreting assignment at the group home.
- Tell the houseparents to get the Deaf resident out of isolation.
- Skip to main content
- Keyboard shortcuts for audio player
Wait Wait...Don't Tell Me!
- Latest Show
- Subscribe to NPR's Up First Email

'Wait Wait' for May 18, 2024: With Not My Job guest Maya Hawke
Recorded at the Studebaker Theater in Chicago, with guest host Alzo Slade, Not My Job guest Maya Hawke and panelists Faith Salie, Negin Farsad and Adam Burke.

Wait Wait...Don't Tell Me!
- See Wait Wait... Don't Tell Me! sponsors and promo codes

IMAGES
VIDEO
COMMENTS
Cybersecurity Capstone: Breach Response Case Studies Week 01 Quiz Answers. Incident Management Knowledge Check ( Practice Quiz ) Q1. In creating an incident response capability in your organization, NIST recommends taking 6 actions. Which three (3) actions are included on that list?
Cybersecurity Capstone Breach Response Case Studies | All Quiz Answers | Coursera | IBMCybersecurity Capstone Breach Response Case Studies ll Part of IBM Cyb...
Cybersecurity Capstone: Breach Response Case Studies, Week (1-4) All Quiz Answers With Assignment You audit this course free on coursera but i...
This course requires you to select and research a cybersecurity breach in the news today and apply your knowledge and skills from this course and previous cybersecurity courses to analyze the type of attack, attack timeline, vulnerable systems, and any missed opportunities. This project will be graded by your peers in the course.
Cybersecurity Capstone: Breach Response Case Studies Week 2 Quiz Answer | Phishing Scams Graded AssessmentKeywords-----Cybersecurity Capstone: B...
Case Studies Final Exam Quiz Answers. The Public Relations Society of America (PRCA) has a statement of professional values. What values does the statement, "We provide objective counsel to those we represent. We are accountable for our actions" fall underneath? Click the card to flip 👆. Independence. (other options: advocacy, loyalty ...
Richard Chamberlain, MD. When is the patient due for a follow-up visit? In 2 weeks. Study with Quizlet and memorize flashcards containing terms like What is the patient's first and last name?, What is the patient's social security number (SSN)?, At which service location did this patient receive care? and more.
There are several ways to conduct a knowledge check, including online, paper-based, and in-person assessments. Choose the most appropriate method for your training program and the learners. Step six: Analyze your results. After conducting your knowledge check, your next step is analyzing the results to determine your employees' understanding ...
3. Analytical questions: These questions test your ability to analyze data and draw insights. You may be given a set of data or a business problem and asked to provide a solution or recommendation. For example, you may be asked to analyze sales data to identify trends and suggest strategies for increasing revenue. 4.
There are 6 modules in this course. This course gives you the background needed to gain Cybersecurity skills as part of the IBM Cybersecurity Professional Certificate programs. You will explore incident response methodologies and security models. You will learn to recognize and categorize key types of vulnerabilities and associated attacks ...
Incident Management Knowledge Check ( Practice Quiz ) Q1) In creating an incident response capability in your organization, NIST recommends taking 6 actions. Which three (3) actions are included on that list? (Select 3) 'Create an incident response policy 'Develop an incident response plan based on the incident response policy
Case study answers written by top business students. We are the marketplace for case study solutions. Save time and get inspired by our case solutions. We help you be a top student at your university! High-quality only. We manually review all case study submissions being sent to us.
This project will be graded by your peers in the course. This course is intended for anyone who wants to gain a basic understanding of Cybersecurity or as the seventh and final course in a series ...
A case study is a detailed study of a specific subject, such as a person, group, place, event, organization, or phenomenon. Case studies are commonly used in social, educational, clinical, and business research. ... contextual, in-depth knowledge about a specific real-world subject. It allows you to explore the key characteristics, meanings ...
The Knowledge Check answer key is on the following page. a. It's important to minimize the transactions that pass from the database to the data grid. b. Web site efficiency is influenced by integrations with external systems. c. Scalability is a result of platform stability and optimal performance. d.
The Cybersecurity Capstone: Breach Response Case Studies programme will provide a platform to the candidate, to attain necessary skills to work as a professional research analyst in Cybersecurity. By taking up the course, the participant will be exploring the methodologies related to incident response and the models of the security.
Cybersecurity Capstone: Breach Response Case Studies Week 1 Quiz Answer | Incident Management Response and Cyberattack Frameworks Graded AssessmentKeywords--...
1700 Coursera Courses That Are Still Completely Free. In this IBM course, you will apply the knowledge gained from the IT Support Professional Certificate to realistic situations. This capstone course leads you through a series of technical support case studies that require hands-on work to resolve. Upon completing this course, you'll gain an ...
Click the Questions tab on the top left of the ribbon to display the question types available. Select Drag and Drop (NOTE: If you mouse over the image, a thumbnail will pop up with information about the question type.) Step 2: Switch from Form View to Slide View. The question opens in Form View by default.
It can efficiently analyze case studies of any subject. 🤩 User-friendly. Our app is intuitive and easy to operate. ⏳ Time-saving. Use it and save more time for conducting your research and polishing the results. 🌐 No download. You give our tool any case study task, and it will do the rest just like that.
Knowledge Check Week 9 6541 Knowledge Check Week 9 6541. Other 100% (8) 20. Final 2 pediatrics 1. ... Answers. Primary Care of Adolescents & Children (NURS 6541) 11 months ago. I'm having trouble finding the key questions on the following Ihuman case study. Olivia Grant. 1 y/o. 2' 7" (80 cm)
Course 8: Technical Support (IT) Case Studies and Capstone. Graded Case Study: Computer Hardware and Software Specifications Quiz Answers. Graded Case Study: System Software, Versions, and Application Software Compatibility Quiz Answers. Graded Case Study: Configure, Test, and Troubleshoot a SOHO Network Quiz Answers. Graded Case Study: Public ...
Step 1. What should the interpreter do? Ask the agency for materials regarding the meeting in order to prepare sufficiently. Research the organization to be fully prepared for the job. Inform agency that a team interpreter is not needed. Ask for a team with Deaf interpreters. Set up ground rules for turn-taking during the meeting.
Recorded at the Studebaker Theater in Chicago, with guest host Alzo Slade, Not My Job guest Maya Hawke and panelists Faith Salie, Negin Farsad and Adam Burke.