- Contact Sales
- Getting Started

Documentation
- AWS Marketplace
- Enterprises
- Public Sector
- Bahasa Indonesia
- AWS Management Console
- Account Settings
- Billing & Cost Management
- Security Credentials
- AWS Personal Health Dashboard
AWS & Cloud Computing
Training & resources, support & services, websites & web apps, backup, storage, & archive, big data & hpc, energy & utilities, financial services, game development, digital media, healthcare & life sciences, business apps, telecommunications, networking & content delivery, developer tools, aws cost management, management tools, media services, security, identity & compliance, ar & vr, machine learning, mobile services, application integration, customer engagement, business productivity, desktop & app streaming, internet of things, resource center, sdks & toolkits, additional software & services, aws general reference.
- Amazon EC2 Auto Scaling
- Amazon Elastic Container Service
- Amazon Elastic Container Service for Kubernetes
- Amazon Elastic Container Registry
- Amazon Lightsail
- AWS Elastic Beanstalk
- AWS Fargate
- AWS Serverless Application Repository
- Elastic Load Balancing
- VMware Cloud on AWS
- Amazon Simple Storage Service (S3)
- Amazon Elastic Block Store (EBS)
- Amazon Elastic File System (EFS)
- Amazon Glacier
- AWS Storage Gateway
- AWS Snowball
- AWS Snowball Edge
- AWS Snowmobile
- Amazon Aurora
- Amazon DynamoDB
- Amazon ElastiCache
- Amazon Redshift
- Amazon Neptune
- AWS Database Migration Service
- AWS Migration Hub
- AWS Application Discovery Service
- AWS Server Migration Service
- Amazon VPC PrivateLink
- Amazon CloudFront
- Amazon Route 53
- Amazon API Gateway
- AWS Direct Connect
- AWS CodeStar
- AWS CodeCommit
- AWS CodeBuild
- AWS CodeDeploy
- AWS CodePipeline
- AWS Tools & SDKs
- Amazon CloudWatch
- AWS Auto Scaling
- AWS CloudFormation
- AWS CloudTrail
- AWS OpsWorks
- AWS Service Catalog
- AWS Systems Manager
- AWS Trusted Advisor
- AWS Command Line Interface
- AWS Managed Services
- Amazon Elastic Transcoder
- Amazon Kinesis Video Streams
- AWS Elemental MediaConvert
- AWS Elemental MediaLive
- AWS Elemental MediaPackage
- AWS Elemental MediaStore
- AWS Elemental MediaTailor
- Amazon SageMaker
- Amazon Comprehend
- Amazon Polly
- Amazon Rekognition
- Amazon Machine Learning
- Amazon Translate
- Amazon Transcribe
- AWS DeepLens
- AWS Deep Learning AMIs
- Apache MXNet on AWS
- TensorFlow on AWS
- Amazon Athena
- Amazon CloudSearch
- Amazon Elasticsearch Service
- Amazon Kinesis
- Amazon QuickSight
- AWS Data Pipeline
- AWS Identity and Access Management (IAM)
- Amazon Cloud Directory
- Amazon Cognito
- Amazon GuardDuty
- Amazon Inspector
- Amazon Macie
- AWS Certificate Manager
- AWS CloudHSM
- AWS Directory Service
- AWS Firewall Manager
- AWS Key Management Service
- AWS Organizations
- AWS Secrets Manager
- AWS Single Sign-On
- AWS Artifact
- AWS Mobile Hub
- Amazon Pinpoint
- AWS AppSync
- AWS Device Farm
- AWS Mobile SDK
- Amazon Sumerian
- Amazon Simple Queue Service (SQS)
- Amazon Simple Notification Service (SNS)
- AWS Step Functions
- Amazon Connect
- Amazon Simple Email Service (SES)
- Alexa for Business
- Amazon Chime
- Amazon WorkDocs
- Amazon WorkMail
- Amazon WorkSpaces
- Amazon AppStream 2.0
- AWS IoT Core
- Amazon FreeRTOS
- AWS Greengrass
- AWS IoT 1-Click
- AWS IoT Analytics
- AWS IoT Button
- AWS IoT Device Defender
- AWS IoT Device Management
- Amazon GameLift
- Amazon Lumberyard
- AWS Cost Explorer
- AWS Budgets
- Reserved Instance Reporting
- AWS Cost and Usage Report
How to Enable Multi-Factor Authentication (MFA) for Your AWS User Account
AWS Multi-Factor Authentication (MFA) is a simple best practice that adds an extra layer of protection on top of your user name and password. With MFA enabled, when a user signs in to an AWS website, they will be prompted for their user name and password (the first factor—what they know), as well as for an authentication response from their AWS MFA device (the second factor—what they have). Taken together, these multiple factors provide increased security for your AWS account settings and resources.
Get Started with AWS IAM »
[getting started] aws security hub.
Get started with AWS Security Hub in just a few clicks in the Management Console .
Learn More »
[Blog] AWS Security Blog
Read about the latest launches and features at the AWS Security Blog.
Read More »
How do I use an MFA token to authenticate access to my AWS resources through the AWS CLI?
I want to use an MFA token to authenticate access to my AWS resources with the AWS Command Line Interface (AWS CLI).
It's a best practice to protect your account and its resources by using a multi-factor authentication (MFA) device . If you plan to interact with your resources using the AWS CLI when using an MFA device, then you must create a temporary session. If you're using an MFA hardware device, then the value is similar to GAHT12345678 . If you're using a virtual MFA, then the value can be found by viewing the Security credentials. It looks similar to arn:aws:iam::123456789012:mfa/user . For more information, see Checking MFA status .
- Support for security keys is available only with the AWS Management Console. For more information, see Activating a FIDO security key (console) . As a workaround, you can use a virtual MFA device. For more information, see Enabling and managing virtual MFA devices (AWS CLI or AWS API) .
- All AWS Identity and Access Management (IAM) users must have sufficient permissions to create, view, and deactivate MFA devices assigned to them as a user. They must also have an MDA device turned on and assigned to their user before beginning.
- If you receive errors when running AWS CLI commands, make sure that you’re using the most recent version of the AWS CLI .
Run the sts get-session-token AWS CLI command, replacing the variables with information from your account, resources, and MFA device:
You receive an output with temporary credentials and an expiration time (by default, 12 hours) similar to the following:
Note: You can specify an expiration duration (in seconds) using the --duration-seconds option in the sts get-session-token command. The value can range from 900 seconds (15 minutes) to 129600 seconds (36 hours). If you are using root user credentials, then the range is from 900 seconds (15 minutes) to 3600 seconds (1 hour).
Using temporary credentials with environment variables
You can use temporary credentials by exporting their values to environment variables using these commands.
If you set the environment variables, be sure to unset them before making the get-session-token call again using these commands.
Using temporary credentials with named profiles
You can also use named profiles to specify the commands that require MFA authentication. To do so, edit the credentials file in the .aws folder in the home directory of the user. In the credentials file, add a new profile configuration for issuing MFA-authenticated commands. Here's an example profile configuration:
After the credentials expire, run the get-session-token command again, and then export the returned values to the environment variables or to the profile configuration.
Tip: Try running a script or a cron job in the background that checks for "expiration" from the get-session-token command output, and then prompts for reauthentication.
If the AWS CLI is configured using the configure command, there's a default configuration with permanent AWS Identity and Access Management (IAM) user credentials. This IAM user can use commands that don't require MFA authentication.
Example configuration:
.aws/credentials
Note: You can't use the mfa_serial parameter with permanent IAM credentials.
If you use profiles to authenticate commands using the AWS CLI, specify the --profile option followed by the profile name. This is done to verify that the calls authenticate using MFA.
For example, this command uses the default profile credentials and isn't authenticated with MFA.
Important: Be sure that you understand the credential precedence so that you can verify that correct credentials are used when making API calls. This can be done by using the GetCallerIdentity command.
You can require a user to authenticate using an MFA to perform particular API actions. Use either the aws:MultiFactorAuthPresent or aws:MultiFactorAuthAge conditions in an IAM policy to accomplish this.
Related information
Enabling MFA devices for users in AWS
Lost or unusable multi-factor authentication (MFA) device
Related videos

To run "aws sts get-session-token" command, I need to provide the AWS profile. To provide the AWS profile I need to store the "aws_access_key_id" and "aws_secret_access_key" under the credential file on my local machine. Then what is the point of using temporary credential with MFA from the same machine where information for Access key is already stored!!. How does this makes it more secure?
I don't see an option to create Access Key with limited permission where only "sts get-session-token" is allowed, in which case I can use that Access Key on my machine to first get temporary credentials and then use those temporary creds to access other resources.
I found the answer to my confusion when looking at https://repost.aws/knowledge-center/mfa-iam-user-aws-cli
Thank you for your comment. We'll review and update the Knowledge Center article as needed.
Relevant content
- Using AWS CLI in automation without MFA token Accepted Answer AWS-User-2896749 lg ... asked 2 years ago lg ...
- Best practice is to use MFA, but neither Google Authenticator nor Twillio Authy works... CandaceSoVan lg ... asked a year ago lg ...
- Use an OIDC token from Azure AD or GCP to access AWS resources (workload Identity federation) Accepted Answer MrAnderson_ lg ... asked a year ago lg ...
- How to protect aws account. Monica lg ... asked 6 months ago lg ...
- How to update advanced settings of AWS Amplify resources through Amplify CLI? Vitor lg ... asked a year ago lg ...

AWS MFA: Keeping your Account Secure via Multi-Factor Authentication

Table of contents
What is multi-factor authentication, importance of mfa at aws, supported types, enabling a virtual mfa device for the root user, mfa for iam users, hardware totp tokens and fido security keys, logging into the aws management console, getting temporary credentials for the aws api, enabling mfa for root users and locking them away, enforcing mfa for users, monitoring usage of mfa, about password managers and their mfa capabilities, recovering your account after losing the mfa device.
An AWS account comes with unlimited possibilities. You can provision almost endless computing resources that exceed small data centers. This power comes with the risk of potential misuse. That's why protecting your account and each IAM user is important. Enabling multi-factor authentication is one crucial step (creating organizations a second 😉)
Introduction
Before we stumble into practice, let's go through the fundamentals of MFA. We'll go through the definition of MFA, why it's important to enable it, and which MFA types are currently supported by AWS
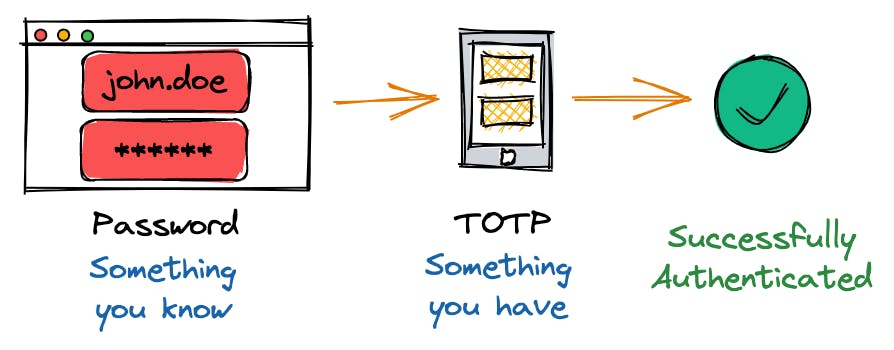
Multi-Factor Authentication (or short MFA) adds another layer of security to any authentication mechanism. With MFA you can combine:
something you know, e.g. your username and password, with
something you own, e.g. a device (virtual or hardware-based) that issues a one-time password
Even if one gets compromised, it won't be enough to access the corresponding service in your name.
As said in the introduction, with great power comes great responsibility. Your AWS is one of your most significant responsibilities as a compromised account can ruin your financial future in a short time frame.
MFA is one major security layer to prevent account compromise. And it comes for free and with low effort.
Different MFA types can be used with AWS. Among them are:
Virtual MFA devices - A virtual device, often a smartphone app, that's used to generate a time-based one-time password (TOTP). Popular are the Google or Microsoft Authenticator or Authy.
Hardware MFA devices - A physical device that also generates a TOTP that's just valid for a specific time frame. YubiKey or RSA security tokens are well-known and widely used MFA hardware devices.
SMS-delivered MFA codes - A one-time code that is sent to your mobile phone via SMS. This method is discouraged by AWS and many other services as it has potential security vulnerabilities, including a high risk for spoofing and fishing as well as SIM swapping.
The most commonly used type is the virtual MFA via an authentication app.
Setting up AWS MFA
Setting up an MFA method at AWS is simple and only takes a few minutes.
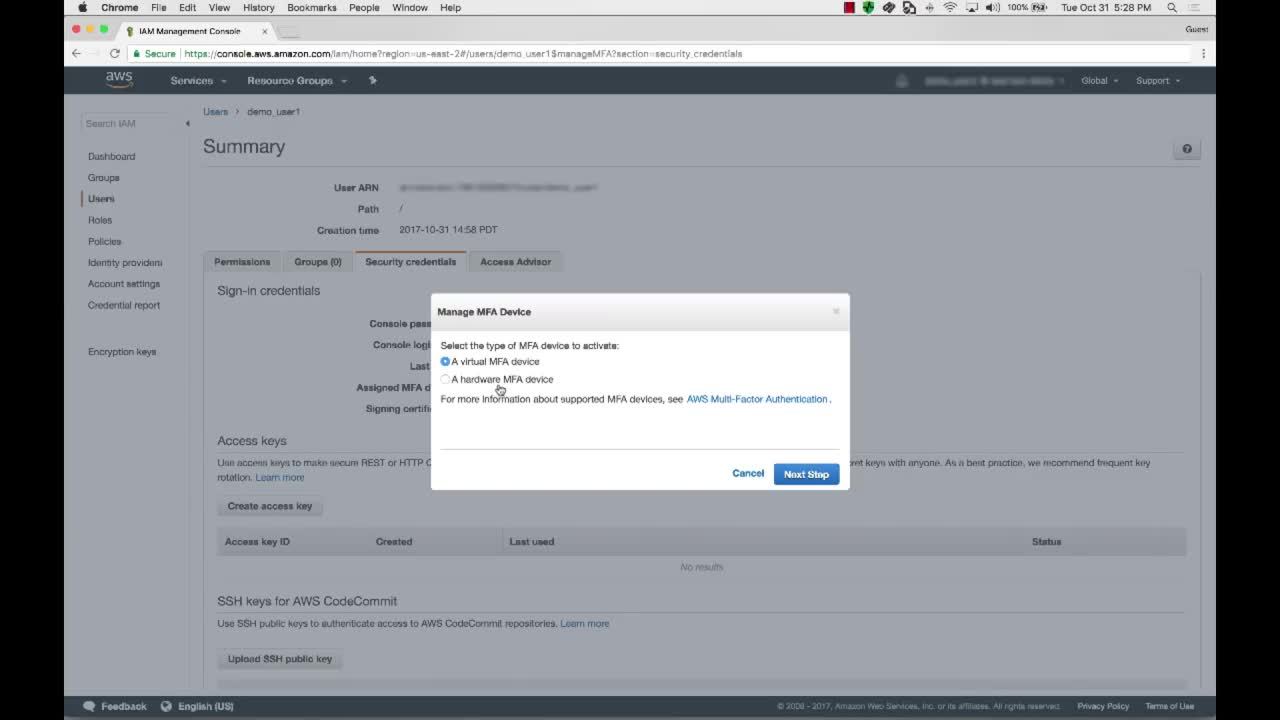
After logging in with your root user, click on the top right of your user and select Security Credentials for being redirected to the security dashboard of your account.
You'll see options to change your password, create access keys for command line access and assign an MFA device. By clicking on the latter one, you'll be prompted to choose your preferred method.
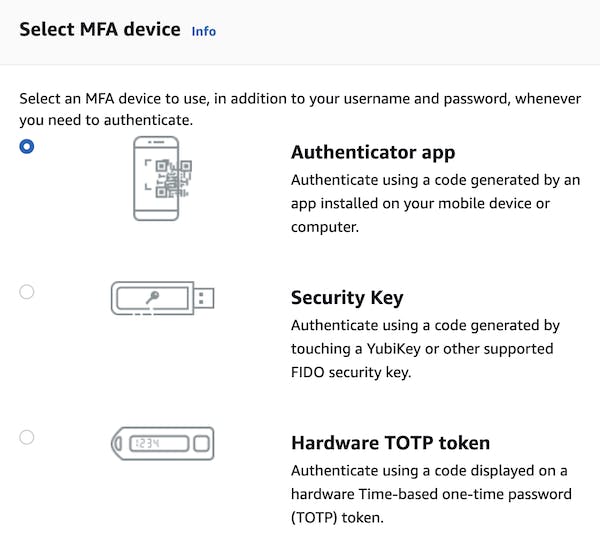
Let's select the authenticator app. You can use any authenticator you prefer, e.g. Google Authenticator, Microsoft Authenticator, or Authy. Each of them is available for both Android and iOS devices.
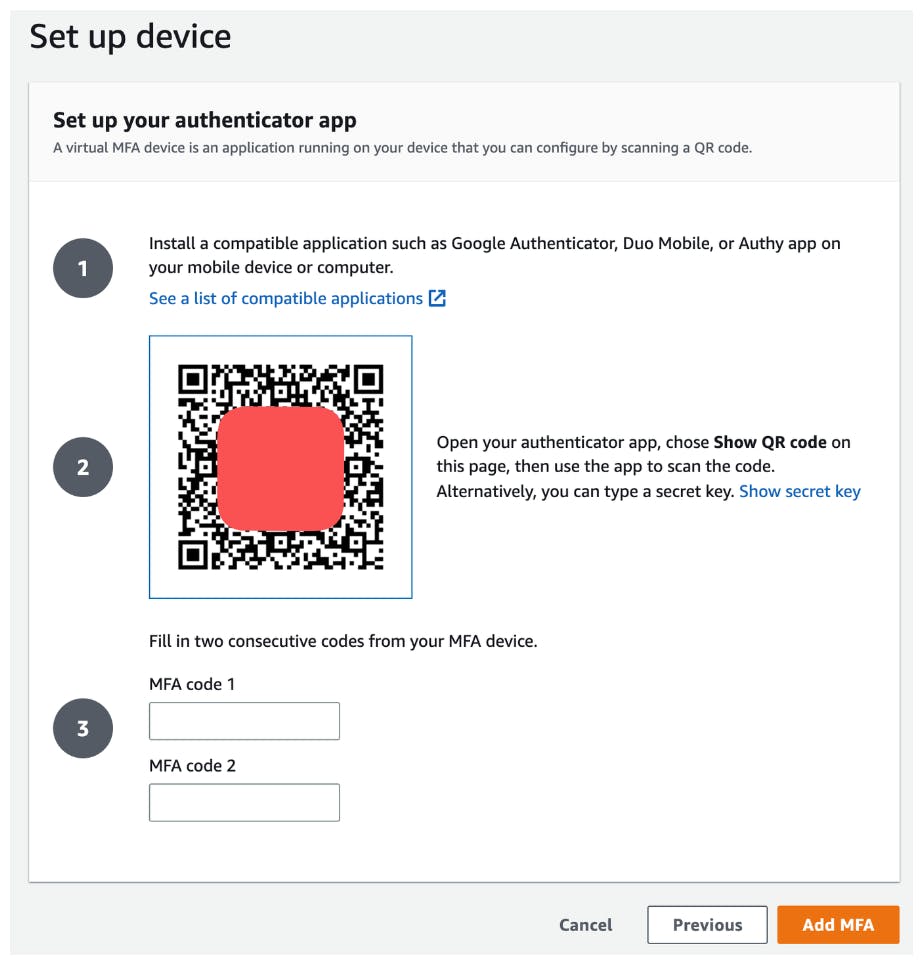
After scanning the QR code with your device, the app will start to generate one-time passwords (commonly with 6 digits). You'll have to enter two consecutive codes at the AWS console to activate the virtual device which will then require you to enter both your credentials and a one-time pass for every login to the console.
IAM users can be heavily restricted in their possible permissions. Nevertheless, it's best practice to configure an MFA device for those users.
The MFA configuration is completely decoupled from the root user. Each IAM user can and should have their MFA device.
Setting it up is exactly equal to the steps shown before for your root user. Everything happens in the security credentials tab after logging into the AWS console with the specific user.
TOTP token generators work by sharing a secret and the current time to generate a password that can be used one time to complete the authentication that has started with the login credentials.
The password will be generated via a mathematical algorithm and the internal clock which ensures that the password is both unique and cannot be guessed easily. Hardware TOTP tokens like SecurID by RSA are a convenient MFA method that doesn't require your phone or an internet connection. Additionally, it can be a good backup mechanism in the event of a failure or loss of the primary MFA devices.
Besides TOTP token hardware devices, there's support for FIDO U2F keys at AWS. YubiKeys are a prominent example of a FIDO-capable device. They work by requiring the user to interact with the device physically, typically by pressing a button, to complete the authentication flow.
This is another security enhancement as the authentication mechanism can't solely be completed via software, but always requires physical interaction.
Using AWS MFA
We've successfully set up MFA devices for our account's root and IAM users. Let's go through all the flows for which we'll now require the second factor.
After successfully setting up MFA for your user, each login will be prompted for an MFA code.

Go back to your authenticator app and type in the current code that appears. Note the limited time that the code is valid and can be used to complete your login.
After you've enabled MFA, you can't simply work with only your AWS Access Key ID and Secret Access anymore. You're always required to use temporary credentials that can be retrieved with your keys and a TOTP from your device.
If you're not a terminal fan, this is very tedious work. But there are a lot of tools that make this process way easier.
One of them is Leapp which also helps you to easily assume identities & roles. It even supports other providers like Azure.
For a more simplistic terminal-based experience you can use AWSume .
Best Practices for the Daily Work
Your root user has full control over your account, your billing, and every resource you’ll ever create. As a best practice, it’s recommended to lock it away immediately after enabling MFA and switch to Identity and Access Management (IAM) users.
Don’t ever use the root credentials for your daily work, neither in the AWS console nor with infrastructure as code or the AWS command line interface.
Also, citing the AWS documentation about root users:
We strongly recommend that you do not use the root user for your everyday tasks, even the administrative ones. Instead, adhere to the best practice of using the root user only to create your first IAM user.
As the root user of an account, it's possible to strictly enforce MFA for IAM users. This needs the configuration of a policy that denies all actions except for those to manage the user's own credentials and MFA devices.
Let's jump to IAM and select Policies on the navigation tab, then choose Create Policy .
Select the JSON tab and insert the policy that you can find in one of the AWS guides that cover how to allow MFA-authenticated IAM users to manage their own credentials .
The important part is the following statement:
It restricts users from all actions that are not necessary to set up their MFA devices.
After you've created the policy you can attach it to your desired IAM user's group so all users will be forced to use MFA from now on. Be sure to test this carefully before with a test group.
You can verify that IAM users are using MFA by checking CloudTrail logs for sign-in events.
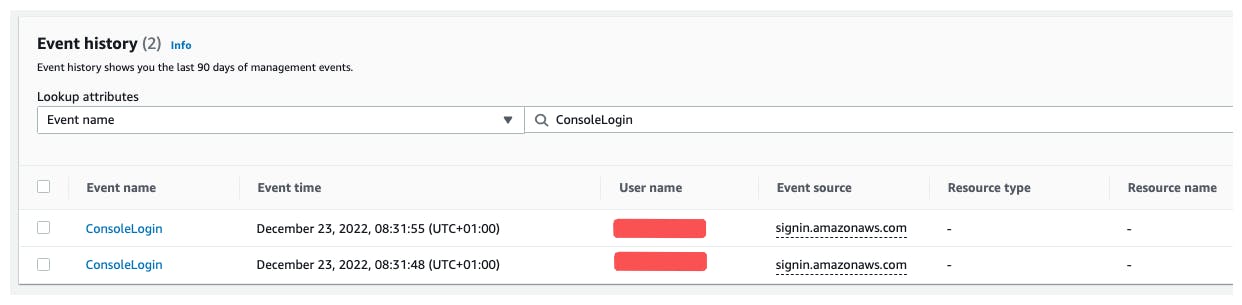
You only have to click on your event history and filter for the event name ConsoleLogin . By selecting an event you'll see the event itself which will look like this:
By checking the nested object additionalEventData you will find MFAUsed .
You can also automate this by creating a dedicated trail, sending the events to CloudWatch , and setting up an alarm that will notify you in case of a login event without MFA occurs.
Yes, this is very convenient. But it completely undercuts the purpose of having a second factor at all, as it's supposed to require another physical or virtual device. As the compromise of an AWS account can have an immense impact on your financial resources, we commend keeping your second factor a real second factor.
Troubleshooting
Things can go wrong and humans do make mistakes. That's especially true for the software development process. Let's go through the most common ones regarding MFA.
If you lose your MFA device, you're not completely lost. You can still contact AWS Support . Alternatively, check the guide by AWS on what to do if an MFA device is lost or stops working .
If your TOTP codes are rejected, it can be due to the fact that your MFA device is out of sync (this can't happen for FIDO security keys) and needs to be resynchronized .
Enabling multi-factor authentication for your account is a must. It will immensely enhance the security of your account.
If you haven't done this yet, the next best time is now .
Introducing Amplify Gen 2
Fullstack typescript.
Write your app's data model, auth, storage, and functions in TypeScript; Amplify will do the rest.
Built with the AWS CDK
Use any cloud resource your app needs. Never worry about scale.
Choose your framework/language
Was this page helpful?
Can you provide more details?
Page updated May 17, 2024
Multi-factor authentication
Amplify Auth supports Multi-factor Authentication (MFA) for user sign-in flows. MFA is an extra layer of security used to make sure that users trying to gain access to an account are who they say they are. It requires users to provide additional information to verify their identity. Amplify Auth supports the MFA methods with Time-based-One-Time Passwords (TOTP) as well as text messages (SMS). In this guide we will review how you can set up MFA using TOTP and SMS and the tradeoffs between these methods to help you choose the right set up for your application. We will also review how to set up MFA to remember a device and reduce sign-in friction for your users.
Configure multi-factor authentication
Use defineAuth to enable MFA for your app. The example below is setting up MFA with TOTP but not SMS as you can see that the phone number is not a required attribute. If you are using SMS, then the PhoneNumber attribute must be true .
When multi-factor authentication (MFA) is REQUIRED with SMS in your backend auth resource, you will need to pass the phone number during sign-up API call. If you are using the email or username as the primary sign-in mechanism, you will need to pass the phone_number attribute as a user attribute. This will change depending on if you enable SMS, TOTP, or both. Visit the multi-factor authentication documentation to learn more about enabling MFA on your backend auth resource.
Understand your MFA options
When enabling MFA you will have two key decisions to make:
- MFA enforcement: As part of this setup you will determine how MFA is enforced. If you require MFA by setting MFA login to "ON", all your users will need to complete MFA to sign in. If you keep it "Optional", your users will have the choice whether to enable MFA or not for their account.
- MFA methods: You will also specify which MFA method you are using - TOTP (Time-based One-time Password), SMS (text message), or both. We recommend that you use TOTP-based MFA as it is more secure and you can reserve SMS for account recovery.
| Time-based One-time Password (TOTP) | Short Message Service (SMS) | |
|---|---|---|
| Generates a short-lived numeric code for user authentication that includes a shared secret key and current time using an authenticator app. | Generates a one-time code shared via text message that is entered with other credentials for user authentication. | |
| More secure than SMS since the code is generated locally and not transmitted over a network. TOTP also works without cell service as long as the TOTP app is installed. | Easy to set up with a user-provided phone number and is familiar to users as a common authentication method. | |
| Requires an app to generate codes and adds to the initial setup of an account. Codes also expire quickly and must be used promptly after it is generated. | SMS requires cell service and can include an additional cost for the user. Although rare, SMS messages can also be intercepted. |
Multi-factor authentication with SMS
Once you have setup SMS as your second layer of authentication with MFA as shown above, your users will get an authentication code via a text message to complete sign-in after they sign in with their username and password.
Warning: In order to send SMS authentication codes, you must request an origination number . Learn more about configuring your auth resource for production workloads .
Enable SMS MFA during sign-up
You will need to pass phone_number as a user attribute to enable SMS MFA for your users during sign-up. However, if the primary sign-in mechanism for your Cognito resource is phone_number (without enabling username ), then you do not need to pass it as an attribute.
By default, you have to verify a user account after they sign up using the confirmSignUp API, which will send a one-time password to the user's phone number or email, depending on your Amazon Cognito configuration.
Manage SMS MFA during sign-in
After a user signs in, if they have MFA enabled for their account, a challenge will be returned that you would need to call the confirmSignIn API where the user provides their confirmation code sent to their phone number.
If MFA is ON or enabled for the user, you must call confirmSignIn with the OTP sent to their phone.
After a user has been signed in, call updateMFAPreference to record the MFA type as enabled for the user and optionally set it as preferred so that subsequent logins default to using this MFA type.
Multi-factor authentication with TOTP
You can use Time-based One-Time Password (TOTP) for multi-factor authentication (MFA) in your web or mobile applications. The Amplify Auth category includes support for TOTP setup and verification using authenticator apps, offering an integrated solution and enhanced security for your users. These apps, such as Google Authenticator, Microsoft Authenticator, have the TOTP algorithm built-in and work by using a shared secret key and the current time to generate short-lived, six digit passwords.
Set up TOTP for a user
After you initiate a user sign in with the signIn API where a user is required to set up TOTP as an MFA method, the API call will return CONTINUE_SIGN_IN_WITH_TOTP_SETUP as a challenge and next step to handle in your app. You will get that challenge if the following conditions are met:
- MFA is marked as Required in your user pool.
- TOTP is enabled in your user pool.
- User does not have TOTP MFA set up already.
The CONTINUE_SIGN_IN_WITH_TOTP_SETUP step signifies that the user must set up TOTP before they can sign in. The step returns an associated value of type TOTPSetupDetails which must be used to configure an authenticator app like Microsoft Authenticator or Google Authenticator. TOTPSetupDetails provides a helper method called getSetupURI which generates a URI that can be used, for example, in a button to open the user's installed authenticator app. For more advanced use cases, TOTPSetupDetails also contains a sharedSecret which can be used to either generate a QR code or be manually entered into an authenticator app.
Once the authenticator app is set up, the user can generate a TOTP code and provide it to the library to complete the sign in process.
The TOTP code can be obtained from the user via a text field or any other means. Once the user provides the TOTP code, call confirmSignIn with the TOTP code as the challengeResponse parameter.
Enable TOTP after a user is signed in
TOTP MFA can be set up after a user has signed in. This can be done when the following conditions are met:
- MFA is marked as Optional or Required in your user pool.
- TOTP is marked as an enabled MFA method in your user pool.
TOTP can be set up by calling the setUpTOTP and verifyTOTPSetup APIs in the Auth category.
Invoke the setUpTOTP API to generate a TOTPSetupDetails object which should be used to configure an Authenticator app like Microsoft Authenticator or Google Authenticator. TOTPSetupDetails provides a helper method called getSetupURI which generates a URI that can be used, for example, in a button to open the user's installed Authenticator app. For more advanced use cases, TOTPSetupDetails also contains a sharedSecret which can be used to either generate a QR code or be manually entered into an Authenticator app.
that contains the sharedSecret which will be used to either to generate a QR code or can be manually entered into an Authenticator app.
Once the Authenticator app is set up, the user must generate a TOTP code and provide it to the library. Pass the code to verifyTOTPSetup to complete the TOTP setup process.
After TOTP setup is complete, call updateMFAPreference to record the MFA type as enabled for the user and optionally set it as preferred so that subsequent logins default to using this MFA type.
Recover from a lost TOTP device
If a user loses access to their TOTP device, they will need to contact an administrator to get help accessing their account. Based on the Cognito user pool configuration, the administrator can use the AdminSetUserMFAPreference to either change the MFA preference to a different MFA method or to disable MFA for the user.
In a scenario where MFA is marked as "Required" in the Cognito User Pool and another MFA method is not set up, the administrator would need to first initiate an AdminUpdateUserAttributes call and update the user's phone number attribute. Once this is complete, the administrator can continue changing the MFA preference to SMS as suggested above.
Set up a user's preferred MFA method
Fetch the current user's mfa preferences.
Invoke the following API to get the current MFA preference and enabled MFA types, if any, for the current user.
Update the current user's MFA preferences
Invoke the following API to update the MFA preference for the current user.
Only one MFA method can be marked as preferred at a time. If the user has multiple MFA methods enabled and tries to mark more than one MFA method as preferred, the API will throw an error.
If multiple MFA methods are enabled for the user, the signIn API will return CONTINUE_SIGN_IN_WITH_MFA_SELECTION as the next step in the auth flow. During this scenario, the user should be prompted to select the MFA method they want to use to sign in and their preference should be passed to confirmSignIn .
Remember a device
Remembering a device is useful in conjunction with MFA because it allows the second factor requirement to be automatically met when your user signs in on that device and reduces friction in their sign-in experience. By default, this feature is turned off.
Note: The device tracking and remembering features are not available if any of the following conditions are met:
- the federated OAuth flow with Cognito User Pools or Hosted UI is used, or
- the User Pool uses email , phone_number , or alias attributes as sign-in methods
- when the signIn API uses the USER_PASSWORD_AUTH as the authFlowType .
Configure device tracking
You can configure device tracking with deviceTracking construct.
There are differences to keep in mind when working with remembered, forgotten, and tracked devices.
- Tracked: Every time the user signs in with a new device, the client is given the device key at the end of a successful authentication event. We use this device key to generate a salt and password verifier which is used to call the ConfirmDevice API. At this point, the device is considered to be "tracked". Once the device is in a tracked state, you can use the Amazon Cognito console to see the time it started to be tracked, last authentication time, and other information about that device.
- Remembered: Remembered devices are also tracked. During user authentication, the device key and secret pair assigned to a remembered device is used to authenticate the device to verify that it is the same device that the user previously used to sign in.
- Not Remembered: A not-remembered device is a tracked device where Cognito has been configured to require users to "Opt-in" to remember a device but the user has chosen not to remember the device. This use case is for users signing into their application from a device that they don't own.
- Forgotten: In the event that you no longer want to remember or track devices, you can use the forgetDevice() API to remove devices from being both remembered and tracked.
- Learn how to sign-up with MFA enabled
- Learn how to manage user devices
DailySysAdmin | For all things IT!
A resource for Sys Admins & IT Pros
Add Microsoft Authenticator MFA to AWS Accounts
The aim of this post is to configure policies in AWS to allow accounts that have been provisioned for users with specific permissions to register for MFA themselves. The authenticator we will be using is the Microsoft IOS app but it could also be Google or any other authenticator.
First, we need to create a policy that can be assigned to the user that will not only force them to login with MFA but also allow them the permissions they need in order to carry out the registration process.
Go to IAM and click Policies then click create policy. Click the JSON tab and copy the below JSON code into the policy.
Click Review Policy

Name the policy Force_MFA

While still in IAM click groups and create a new group called EC2MFA.

Attach the Force_MFA policy we just created to the group

Next select the user that we want to force to register for MFA and add them to the group

Now using a different browser or a completely new session login as the user you just applied the MFA policy too. (This is just for demo purposes – the user will do this part themselves)

Check the user’s permissions and they should not be able to do anything at this point as MFA is required.

Click the username and select My Security Credentials

Click Assign MFA device

There seems to be a bug whereby sometimes it appears as though the user has already registered for MFA as the below error suggests:

To overcome this we can use the AWS PowerShell module. Login with an appropriate account and run the below command to see which accounts have an MFA device attached:

Copy the user’s details and put into a remove command as below:

Now the user can try again to register and MFA device as before:

You then need to ensure that the user has downloaded the Microsoft Authenticator app to their mobile device. Then click Show QR code.

On the mobile device tap the +

Select Work or school account

Hold your camera over the QR code on screen

AWS is automatically associated

We then just have to put in the next two codes that appear on the app and click Assign MFA

The Setup should be successful

The user can then login again as normal:

But will then be prompted for their MFA code from the authenticator app

Related Posts:

Share this:
- Click to share on Twitter (Opens in new window)
- Click to share on Facebook (Opens in new window)
Leave a Reply Cancel reply
Your email address will not be published. Required fields are marked *
Save my name, email, and website in this browser for the next time I comment.
Notify me of follow-up comments by email.
Notify me of new posts by email.
- Stack Overflow Public questions & answers
- Stack Overflow for Teams Where developers & technologists share private knowledge with coworkers
- Talent Build your employer brand
- Advertising Reach developers & technologists worldwide
- Labs The future of collective knowledge sharing
- About the company
Collectives™ on Stack Overflow
Find centralized, trusted content and collaborate around the technologies you use most.
Q&A for work
Connect and share knowledge within a single location that is structured and easy to search.
Get early access and see previews of new features.
How to use MFA with AWS CLI?
How do I type in the MFA code when using the AWS CLI? I have checked the documentation page of IAM http://docs.aws.amazon.com/cli/latest/reference/iam/index.html .
I have the MFA-Devices already enabled under my username.
- amazon-web-services
19 Answers 19
The CLI can manage a lot of this for you if you're using roles. Described here: http://docs.aws.amazon.com/cli/latest/userguide/cli-roles.html
In my credentials file I have:
Note the mfa_serial entry. You can get this value from your user details in the AWS IAM console. This entry tells the CLI that MFA is required for that role.
When I call aws s3 ls --profile my_admin_role it says Enter MFA code: , after I paste in the code it returns the listing.
Note: I haven't found a way to get the CLI to ask for MFA when calling a user profile ( --profile my_iam_user ) only calling a role profile triggers the MFA request.
The MFA token is then carried forward and the user profile can be used as well:
- 11 This technique blew my mind. It was so much simpler than dealing with temporary keys and tokens directly! I'm surprised this isn't mentioned more often. – killthrush Mar 21, 2018 at 22:48
- 1 When I try to create a role for myself, there aren't any good options. How did you create the role? – Ryan Shillington Mar 15, 2019 at 18:45
- This technique is fine but one draw back for me is that after one hour my role profile credentials time out and I have to reenter the mfa code even though my main account only needs mfa reauth every 12 hours or so. Is there some way to refresh the token without retyping the mfa key (for 12h)? – user2636840 Apr 7, 2020 at 10:37
- 2 This method, combined with aws-shell , is absolutely perfect. Thank you for sharing. aws-shell --profile roleProfileName will launch an aws shell with that role, meaning you don't have to pass --profile to every command. MFA will be prompted for automatically when needed AND you get code-completion and documentation from aws-shell. Awesome! – CB-Dan May 22, 2020 at 17:11
- 3 Issue for having this work without roles: github.com/aws/aws-cli/issues/1985 – Johan Walles Jan 26, 2022 at 6:56
Call aws sts get-session-token --serial-number <serial> --token-code <code> documented here . This will give you a temporary security token. Documentation on using the temporary security token can be found here .
- 1 It seems to also need --serial-number – Gert van den Berg Jan 10, 2020 at 7:52
- Thanks @GertvandenBerg. Corrected the post with the updated CLI command (it was correct at the time of publishing, 4 years ago). – rmharrison Apr 28, 2020 at 22:27
- Sample code is here - github.com/venkat-vs-id/kat-aws-utils/blob/master/README.md – Venkat.V.S May 26, 2020 at 12:48
- 2 @Phifo this question is about using 2FA tokens. The code is the 2FA token. – Mark B Feb 18, 2021 at 18:44
Step-by-step manual solution:
- Request a session token with MFA
arn-of-the-mfa-device : visible from your user IAM
- Option: Use CLI to retrieve: aws iam list-mfa-devices --user-name ryan
- Option: View in IAM console: IAM --> Users --> <YOU> --> Security Credentials
code-from-token : 6 digit code from your configured MFA device
- Create a profile with the returned credentials
aws_session_token is not included in aws configure
- Test command
- 3 God bless you for this answer! Thanks for telling me how to add aws_sesison_token to the profile – pnv Mar 5, 2021 at 18:54
- 2 @pnv Indeed, it's great to know what's going on "behind the scenes", but for everyday I highly recommend using a tool. There are 3-4 popular ones. I use github.com/broamski/aws-mfa – rmharrison Mar 6, 2021 at 2:06
- 1 @pnv You can also update ~/.aws/credentials from a text editor, and not bother with the aws configure at all. – rmharrison Mar 6, 2021 at 2:07
I have published a PR for aws-cli, which will allow to use mfa_serial in the credentials, that will force you to enter the token before making request to AWS (and it will be cached while token is valid)
- Issue: https://github.com/aws/aws-cli/issues/3172
- botocore PR: https://github.com/boto/botocore/pull/1399
- aws-cli PR: https://github.com/aws/aws-cli/pull/3174
Feel free to vote, if you want to get it in.
aws-mfa acts as a wrapper around sts and works really well: https://github.com/broamski/aws-mfa
Wrote a tool to add MFA support for standard IAM user profiles until @outcoldman PR gets merged: https://github.com/tongueroo/aws-mfa-secure
Setup for those in a hurry
- Install gem
- Setup your ~/.aws/credentials with mfa_serial
~/.aws/credentials:
- Add the alias to your ~/.bash_profile
Restart your terminal.
Example with Output
Assume role profiles.
Assume role profiles work already for the AWS CLI, here's an example:
I'm on windows and I created a batch file to pass in my MFA code and have it automatically set up my credentials. First, you need to set up your production credentials in AWS:
Answer the questions appropriately with your key and secret. Then, I run my script like this:
Here are the contents of my mfa-getCreds.bat :
For this to run, you'll need the excellent jq package in your path.
- 1 Thanks mate.. saved me creating it :) – Paul Dunlop Jul 15, 2019 at 10:20
My use-case is I have a root account where all IAM users are created and assigned to IAM groups which in turn have the capability to assume roles on a different account with varying degree of access depending on the group they are on. I have a few house rules in place;
- No one is allowed to do anything on the root account except to manage their own IAM Users account.
- Required password reset.
- Required MFA.
- You cannot switch accounts without logging in with MFA.
This has been set up using AWS Shared Organizations.
Previously, I've been using a python script I wrote to let my users to login via cli with MFA and switch accounts. This is done by manipulating the ~/.aws/credentials.
I've since migrated to using this project https://gitlab.com/severity1/aws-auth , which is written in Go and allows me to do the same without much setup and it works on windows, macosx and linux.
This effectively gives all my users the ability to do local testing while developing Apps for AWS without having to hardcode AWS Credentials into their code.
Run the sts get-session-token AWS CLI command, replacing the variables with information from your account, resources, and MFA device:
$ aws sts get-session-token --serial-number arn-of-the-mfa-device --token-code code-from-token
https://aws.amazon.com/premiumsupport/knowledge-center/authenticate-mfa-cli/
I wrote a small bash script to get over this annoying problem. You can find it here: https://gist.github.com/geekgunda/db4c9c8d850c08a48d1d60f119628032
Assumptions:
- Your original AWS Creds should be stored at ~/.aws/credentials
- You've corrected ARN for MFA device (search for FIXME)
- You've given correct MFA Code as cli argument
- You have jq installed. Ref: https://stedolan.github.io/jq/
We documented a few considerations for AWS API multifactor in general (where to add the conditions, what are the implications etc.) in the documentation for some custom tooling ( https://github.com/kreuzwerker/awsu ) we developed for using Yubikeys as source for the TOTP tokens. This makes working with roles and long-term credentials + session tokens pretty easy.
I have forked Chinmay's gist and updated it to pull the device serial from aws instead of hardcoding it. I have also updated the exits to return a status of 1 instead of just exiting.
Available here: https://gist.github.com/jpribyl/e44021ae5cbf7fd1b4549598e85b5341
I am using it in deploy scripts like this (I renamed the script to awsMfaCli.sh):
AWS MFA use on the command line can be rather unpleasant and cumbersome, especially if you have multiple profiles and roles.
I have released awscli-mfa.sh script that makes MFA/role session management on the command line a lot easier. A companion script enable-disable-vmfa-device.sh similarly makes it easy to enable or disable a virtual MFA device on an IAM user account.
awscli-mfa.sh persists a started session in ~/.aws/credentials (with some info in ~/.aws/config ), or allows you to start an in-env session only so that its details don't get persisted. When executed in Windows Subsystem for Linux, the script also provides session activation strings for PowerShell and Windows command line. However, the script itself only runs in bash (written for macOS, Linux, and WSL bash with Ubuntu).
You can find the scripts and the example MFA policies in my GitHub repo at https://github.com/vwal/awscli-mfa
- I wish there was something like this for Windows. – Ryan Shillington Mar 15, 2019 at 19:02
- @RyanShillington If you install Windows Subsystem for Linux (WSL) , the script runs well in it. In fact, when you run it in WSL, it also provides the MFA and role session activation strings for Windows CMD and PowerShell. – Ville Mar 15, 2019 at 21:18
A one-liner to authorize and append an MFA user to your credentials file using jq:
Authenticating with MFA is done with the aws sts command. The basic process is:
- Set up a "permanent" profile in ~/.aws/credentials .
- Call the aws sts command with the "permanent" profile.
- Create a "temporary" profile in ~/.aws/credentials with the result from #2
- Use the "temporary" profile with your aws commands.
You'll notice that this is kind of an excessive process for logging in. I recommend using a utility/script for this purpose. Several exist, including some mentioned in other answers.
I have also written such a utility, as well as an in-depth article on how to authenticate with MFA using the AWS CLI (includes a couple of other details, like how to require MFA).
My utility is just a short script, and doesn't use a pip installer, which makes it easy to inspect.
Overview of process
Utility for automation
- 1 Please explain the details here, as just links are not following the code of conduct and are not sustainable over time! – lony Sep 3, 2022 at 20:30
- Your answer could be improved with additional supporting information. Please edit to add further details, such as citations or documentation, so that others can confirm that your answer is correct. You can find more information on how to write good answers in the help center . – Community Bot Sep 10, 2022 at 8:32
I think my answer will be useful for people trying to follow the official docs , which sadly leave out a lot of details. I discovered a few nuances when trying to figure out how to do this according to the official docs so I wrote this up to help.
I originally had a non-MFA CLI user configured in my ~/.aws/credentials file (this will be important later)
I then created a 2nd user "mfa-test" to which I attached a custom policy named Force_MFA. I sourced the policy from this aws doc
Nuances I learned about this command: aws sts get-session-token --serial-number arn:aws:iam::853680132675:mfa/mfa-test --token-code 630011
You should update to the latest version of the AWS CLI before running the command. The docs mention it might fail if your aws cli isn't updated, but it's easy to miss that suggestion.
The TOTP(time-based one-time password) token code 630011 comes from your virtual MFA device

The command will fail (without a useful error message) if ~/.aws/credentials corresponds to another account (like non-MFA CLI user).
In other words, there's a hard requirement that the credentials used when running the aws sts get-session-token --serial-number arn:aws:iam::853680132675:mfa/mfa-test --token-code 630011 command, map to the user referenced in that command (username = mfa-test ). (The only exception is if you have additional profiles defined in ~/.aws/credentials & ~/.aws/config and reference them using --profile additional_profile )
So I'd recommend running aws sts get-caller-identity and making sure you see the user (mfa-test) in the results (.../user/mfa-test) matches the user mentioned in the ARN of the mfa device (.../mfa/mfa-test)
Also if you install jq (json query) cli tool then unix users can use the following trick to streamline the trade-off of non-MFA CLI creds to MFA CLI creds that expire after 12 hours by default (note the | tr -d '"' in the command is read as translate delete " , it strips out the double quotes)
export MFA_CLI_SESSION=$(aws sts get-session-token --serial-number arn:aws:iam::853680132675:mfa/mfa-test --token-code 630011)
You can run these commands as a smoke test to verify the variables aren't empty.
From this point on your AWS CLI commands will work for the next 12 hours within that terminal session (since they're implemented as env vars). Also they'll work without having to add --profile additional_profile flag to your commands.
Snippet easy to copy and paste.
- error: read: -p: no coprocess – gangadhars Apr 25, 2023 at 4:17
- It worked here. It is a bash script. – Fabrício Ceolin Apr 25, 2023 at 16:56
Using 1Password CLI with AWS plugin
Note: this solution requires 1Password, which requires a paid subscription.
1Password can securely store credentials, and automatically create short-term credentials even in cases where you are working in a basic setup with AWS_ACCESS_KEY_ID and AWS_SECRET_ACCESS_KEY configuration.
MFA can be enabled using biometrics (e.g. faceid, touchid, apple watch in the Apple world, others as well) -- 1Password will supply the required MFA token automatically.
Set up the 1Password CLI ( op ) using these instructions: https://developer.1password.com/docs/cli
Set up the AWS plugin, including steps to enable MFA using these instructions: https://developer.1password.com/docs/cli/shell-plugins/aws
Here's a PowerShell module that lets you set up AWS profiles that authenticate using MFA. It will manage the MFA session token, which will last up to 36 hours without needing to re-enter MFA credentials:
https://github.com/CurtisLusmore/AwsCredentialsManager/tree/161783a4c89a3f694b8010778dd34029bc153921
- I'm a macOS user, but why do you link to a specific commit? Does it not make more sense to be more generic? – lony Oct 2, 2023 at 8:58
Your Answer
Reminder: Answers generated by artificial intelligence tools are not allowed on Stack Overflow. Learn more
Sign up or log in
Post as a guest.
Required, but never shown
By clicking “Post Your Answer”, you agree to our terms of service and acknowledge you have read our privacy policy .
Not the answer you're looking for? Browse other questions tagged amazon-web-services or ask your own question .
- The Overflow Blog
- Introducing Staging Ground: The private space to get feedback on questions...
- Featured on Meta
- The 2024 Developer Survey Is Live
- The return of Staging Ground to Stack Overflow
- The [tax] tag is being burninated
- Policy: Generative AI (e.g., ChatGPT) is banned
Hot Network Questions
- Complexity of definable global choice functions
- What is the frequentist's Bayesian prior for a coin with unknown bias
- How to create an enumerate environment with Case 1, Case 2,
- Could a 200m diameter asteroid be put into a graveyard orbit and not be noticed by people on the ground?
- Can I expect to find taxis at Kunming Changshui Airport at 2 am?
- What should I get paid for if I can't work due to circumstances outside of my control?
- I can't search in Messages on iOS anymore. How to fix it?
- Are your memories part of you?
- Build the first 6 letters of an Italian codice fiscale (tax identification number)
- What is the difference in meaning between the two sentences?
- Which program is used in this shot of the movie "The Wrong Woman"
- How to Adjust Comparator Output Voltage for Circuit to Work at 3.3V Instead of 5V?
- Do features with high variance contribute more to top principal components that explain much of the variance in dataset and vice versa?
- Are there any jobs that are forbidden by law to convicted felons?
- TeX capacity exceeded, sorry [grouping levels=255] while using enumerate
- How to remind myself of important matters in the heat of running the game?
- Print all correct parenthesis sequences of () and [] of length n in lexicographical order
- ConnectFourFX.java - A Java FX GUI app for playing Connect Four against AI
- Energy stored in a saturating inductor
- Transformer with same size symbol meaning
- Under physicalism, should I still be sad if my murdered wife is replaced with a perfect clone?
- My players think they found a loophole that gives them infinite poison and XP. How can I add the proper challenges to slow them down?
- How do I snap the edges of hex tiles together?
- On a planet with 6 moons, how often would all 6 be full at the same time?

AWS MFA: Enable Multi-Factor Authentication In 6 Simple Steps
- The Philomath
- October 25, 2021
Multi-Factor Authentication – AWS MFA is a security measure that adds a layer of protection to your AWS account. You can use it in conjunction with or instead of the standard username and password login process for accessing certain services, such as Amazon S3 buckets . Once you enable AWS MFA, you will be prompted for both your username and password AND either a one-time code sent to your phone via SMS text message OR a sequence of numbers generated by the Google Authenticator app on your phone before being able to access these resources.
This two-factor authentication scheme is very good because it means that even if someone knows your username and password, they still cannot access any protected information from the website unless they have one more factor. That can be something like a code or a picture.
Enhancing AWS Security with MFA Codes
Enabling Multi-Factor Authentication (MFA) in AWS is a pivotal step to enhance account security. To get an MFA code for AWS, you first activate MFA in your account settings. This involves associating your account with a virtual or hardware MFA device. Once activated, during login, you’ll be prompted to provide an additional authentication factor beyond just your password. This second factor can be generated by the MFA device. It’s a time-sensitive code that adds a layer of defense against unauthorized access. By setting up MFA and obtaining the MFA code, you substantially bolster your AWS account’s protection against potential security breaches.
To enhance the security of your AWS account, enabling Multi-Factor Authentication (MFA) is essential. By setting up MFA with AWS, often referred to as “aws-mfa,” you add an extra layer of protection to your account, requiring not only your password but also a secondary authentication method, such as a mobile app or hardware token. This six-step process to set up multi-factor authentication in AWS ensures that your account remains highly secure, safeguarding your valuable resources and data from unauthorized access.
What is AWS MFA?
“Amazon Web Services Multi-Factor Authentication (AWS MFA) is a security feature that provides an additional level of security for your AWS account.”
So, what does this mean?
In layman’s terms, it means that when you log in to your AWS console, be it via the web or mobile apps, you have to enter a code in addition to your username and password. That code is generated on a device that you have registered with AWS MFA before, such as a smartphone or license generator token.
Build Your Career as a AWS Solution Architect
- Live Projects
- Resume / Interview Preparation

Why should I use it?
AWS MFA provides a way for you to add a layer of security to your account so that even if someone has your username and password, they can’t access your account without the MFA code. We all know that typing in our password incorrectly or not logging out of our account properly are very easy mistakes to make. If someone has access to your account for just a few minutes, they could wreak havoc on your AWS resources while you’re blissfully unaware until it’s too late.
Another reason you should use it is that it makes your AWS account more secure from phishing attacks. In a phishing attack, someone sends you an email that looks like it’s from Amazon, asking for your username and password. If you give them this information, they have access to your account just as if they had your username and password. With AWS MFA, you can rest assured that they won’t be able to get into your account even if they have the correct credentials.
Boost your earning potential with AWS expertise. Explore our certified AWS Courses for a high-paying career
- Explore AWS Architect Professional Certification
What do I need to use it?
- You must have an AWS account to use AWS MFA. If you don’t already have one, sign up here.
- An IAM user with permission to access your account’s MFA settings. More on this in the next section.
- A smartphone or other device where you can generate the AWS MFA code, such as an RSA SecurID token or a DUO Security license generator token (in beta at the time of writing).
- A way to generate the code you need on that device, such as a QR scanner or an SMS. This article assumes that we will be using one of the devices in the list and the AWS MFA apps for generating codes (which seems like a popular option).
Let’s Start!!
- Login to your AWS Management Console account.

Note: Before creating MFA you need to delete all Security Access keys for your account.

In Microsoft Authenticator, you need to Add An Account and then click on another account (Google, Facebook, etc.). Now scan the given QR Code on the screen to generate MFA Codes.
- Add 2 consecutive MFA Codes and click on Assign MFA.

Congratulations! You have successfully assigned Virtual MFA to your account.
Conclusion:
Security is always a hot topic, and with more of your business lives being stored in the cloud than ever before, it’s important to be proactive about protecting your company from potential breaches. Here are two simple steps you can take right now to secure your AWS account against common threats: Enable Multi-Factor Authentication on all accounts that require it; Make sure any admin passwords are strong enough (even if they aren’t required by default). These easy steps will help protect the data you store on Amazon’s highly reliable servers. You can learn more about these topics by checking out our Blogs or Courses page!
Happy Computing!!
Quick Take Away
No comment yet, add your voice below!
Add a Comment Cancel reply
Your email address will not be published. Required fields are marked *
Save my name, email, and website in this browser for the next time I comment.
Interview Preparation Questions
Category : quiz.
- Cyber Security Quiz
Need a Free Career Counselling ?
Book your personalized session today.

Popular Courses
- CBAP Certification
- Azure DevOps Certification
- DevOps Online Training
- SQL Certification Training
- Safe Agilist Certification
- RPA Certification
- SOC Analyst Training
- Uipath Training
- Terraform Certification
- Python Certification Course
Popular Blogs
- DevOps training and placement
- AWS Certification vs Azure Certification
- Best Certification for SOC Analyst
- What does a Cloud Practitioner do
- Solutions Architect Projects
- Cloud Computing Opportunities
Recent Posts
How to create an extremely useful elastic file system (efs), amazon sns: send quick notifications of various events, top 30 azure dba interview questions & answers, follow us on.
Expert Guidenace?

Job Support
Ready to go download our app.
Download Thinkcloudly App today for enhanced experience on the go!

Scan QR Code to Download

Upskill for your Dream Job
- Batch Of 5 Students
- Brainstorming Sessions
- Career Oriented Training
Trusted By Employees Of

- Call For Support : +1 725 710 9949

Boost your It career preparation
Download free ebooks.

Login with confidence. Protect your passwords and accounts with LogMeOnce rich features.
- Top Features
- Free Mobile Security
- PasswordLess QR Login
- PasswordLess Photo Login
- Two-Factor Authentication
- Scheduled Login ©

Scan Dark Web for stolen passwords. Stop hackers from attacking your online activity. Collect hacker’s metadata!
- Anti-Hacker Protecter
- Mugshot (patented)
- Password SHOCK ©

Encrypt files, images, and documents stored on your favorite cloud storage sites with your own password!

Our award-winning software helps to effectively protect and manage passwords for teams of 50 or less.
- Cloud Encrypter
- Identity Theft Protection
- Pricing & Comparison

Secure employees, contractors, and partners’ access with Single Sign-On, MFA and more rich security features.
- Passwordless MFA
Protecting your government agency requires threats awareness of external and internal elements.

As an MSP, you need to manage your company’s internal passwords and your customers' passwords too.
- Become a Partner
- MSP Password Manager
- How LogmeOnce Works
- How Secure is Logmeonce ?
- Dangers of Weak Password
- Teams / Business / Enterprise
- Personal / Family
- Students – 50% off on total bundle
- Student – 50% off everything
Nicole’s, journey in the tech industry is marked by a passion for learning and an unwavering commitment to excellence. Whether it’s delving into the latest software developments or exploring innovative computing solutions, Nicole’s expertise is evident in her insightful and informative writing style. Her ability to connect with readers through her words makes her a valuable asset in any technical communication endeavor.
Related Posts
- VCA IT Support
- Accessing Snapchat Without Email or Password: Alternative Login Methods
- How To Unlock LG Phone Forgot Password Without Losing Data
- IT Business Solution
- Password Viewer Outlook
- How To Update Autofill Address On iPhone
- Applications
- Cloud Security
- Password Manager
- Single Sign On
- Social Media
- Two Factor Authentication
Protect your passwords, for FREE
How convenient can passwords be? Download LogMeOnce Password Manager for FREE now and be more secure than ever.

Global Data Breach Statistics

- LogMeOnce, HQ, USA, Washington DC
- 1 (800) 935-4619
- Corporate: [email protected]
- Sales: [email protected] Media Contact: [email protected] Careers: [email protected]
- Pricing and Comparison
More Security
- Anti-Hacker
- Cloud Storage Encryption
- Password Shock ©
- Schedule Login ©
- Dark Web Monitoring
- How LogMeOnce Works
- Why Use LogMeOnce
- How Secure is LogMeOnce ?
- NIST 800 Information Security Policies
- Your LogMeOnce Password Management Benefits
- Support Center
- Password Generator
- Partner Login
- Company Overview
- Executive Team
- Patents & Licensing
- Media Coverage
- Online Media Kit
LogMeOnce is a US based company, operating globally with offices in Washington DC, USA,. All other company, product , service names and trademarks used in this website are for identification purposes only, and are property of their respective owners . Use of these names, trademarks and brands does not imply endorsement.
This content is intended to provide general information. While we strive for accuracy and reliability, it may contain errors or outdated information. It should not be considered professional or personalized advice. Please use this content as a starting point for further research and consult relevant experts when needed. We do not assume any responsibility or liability for the use or interpretation of this content.
| You might be using an unsupported or outdated browser. To get the best possible experience please use the latest version of Chrome, Firefox, Safari, or Microsoft Edge to view this website. |
Best AWS Certifications Of 2024

Published: May 31, 2024, 12:00pm

Key Takeaways
- Amazon Web Services (AWS) creates the only official AWS certifications. However, several online educational providers offer courses to help you prepare for specific AWS certifications.
- AWS itself offers some of the most comprehensive and affordable courses for AWS certification prep.
- AWS certification courses range from free for introductory programs to thousands of dollars for bootcamp-style programs designed to take you from beginner to expert.
Amazon Web Services (AWS) has quickly become one of the most popular cloud services for handling tasks like database storage, mobile app development and networking. Because many businesses now rely on AWS cloud services to handle their data, companies often seek out IT professionals who are well-versed in AWS.
Earning an AWS certification can boost your credibility and showcase your expertise in the fast-growing cloud computing industry. AWS offers several certifications for data engineers, developers and solutions architects, any of which you can prepare to earn with the right certification course.
We’ve rounded up some of the best AWS certification courses based on writer research, including a mix of programs to fit different experience levels, budgets, and learning styles.
Why You Can Trust Forbes Advisor Education
Forbes Advisor’s education editors are committed to producing unbiased rankings and informative articles covering online colleges, tech bootcamps and career paths. Our ranking methodologies use data from the National Center for Education Statistics , education providers, and reputable educational and professional organizations. An advisory board of educators and other subject matter experts reviews and verifies our content to bring you trustworthy, up-to-date information. Advertisers do not influence our rankings or editorial content.
- 6,290 accredited, nonprofit colleges and universities analyzed nationwide
- 52 reputable tech bootcamp providers evaluated for our rankings
- All content is fact-checked and updated on an annual basis
- Rankings undergo five rounds of fact-checking
- Only 7.12% of all colleges, universities and bootcamp providers we consider are awarded
Should You Pursue an Online AWS Certification?
Before we dive into certification options, let’s answer the fundamental questions for those new to cloud computing: What is AWS, and how can getting an AWS certification benefit you?
AWS is a cloud computing platform that provides the building blocks necessary for app and software creation. AWS certification can help developers, machine learning specialists, cloud architects and other professionals stand out when applying for jobs or being considered for advancements.
AWS also provides certified professionals with digital badges to display on their websites or LinkedIn profiles, opportunities to collaborate with developers to improve AWS exams and access to networking events.
Still, learning online isn’t a viable option for everyone. Before starting an online AWS certification program, consider the following points:
- What is your schedule like? AWS certification courses are available in different online formats to suit varying schedule needs. Synchronous courses feature live lessons with an instructor, while asynchronous options follow a set timeline but allow you to access lessons at any time of day or night as long as you keep up with the class schedule. Self-paced courses have no deadlines. If you need flexibility, asynchronous lessons or a self-paced format might work best for you.
- Will you learn well online? Learning AWS online can be challenging, especially if you typically understand concepts better with the more individualized and structured education face-to-face learning can provide. In contrast, online learning might be right for you if you’re a self-starter and have good time management skills.
- Do you have reliable equipment? You’ll need a reliable computer and internet connection to take part in AWS certification courses. Look for equipment specifications on the course information page before starting.
- Are there hidden costs? Some online AWS courses say they’re free, but they may only be free for a portion of the program and require a fee or subscription to unlock the rest. These fees are only sometimes fully transparent on websites, so you may need to contact support to get more details.
Degree Finder
Online aws certification options.
The only way to get an AWS certification is to take an official AWS exam through Amazon Web Services.
Keep this in mind when comparing AWS courses, as you may come across some that promise to lead to certification after completion. While the best AWS certification courses, like those listed below, can help you prepare for various AWS certifications, you’ll still need to take an AWS exam to become officially certified.
7 Online AWS Certification Course Options
Freecodecamp.
Program Title: AWS Skill Builder Cost: Free; paid version for $29/month or $449/year Program Length: Self-paced Program Overview: AWS provides some of the most comprehensive AWS certification training for beginners to advanced users through its Skill Builder platform. Students can access more than 600 on-demand courses with a free account, but a monthly or annual subscription adds access to hands-on labs, assessments, game-based simulations and advanced exam prep tools.
AWS Skill Builder also occasionally provides free live streams on Twitch with AWS experts, digging into specific topics for cloud computing professionals and learners, like generative AI, AWS architecture and certification exam tips.
Program Title: AWS Associate and Professional Bundle Cost: $200 Program Length: Self-paced with lifetime access Program Overview: Cantrill is a cloud and technical training platform built by solutions architect Adrian Cantrill. The AWS Associate and Professional course bundle includes the following Cantrill courses, ideal for learners interested in multiple AWS certifications:
- AWS Certified Solutions Architect – Associate
- AWS Certified Developer – Associate
- AWS Certified SysOps Administrator – Associate
- AWS Certified Solutions Architect – Professional
- AWS Certified DevOps Engineer – Professional
The self-paced course includes recorded video lessons, each 20 minutes or less, covering topics like data analytics, advanced AWS deployment and management, advanced storage configuration and AWS disaster recovery. Quizzes are available after each lesson for students to test their knowledge.
Cantrill’s bundle includes lifetime access, so learners can work through and revisit the content indefinitely.
Program Title: AWS and DevOps Course Cost: $13,800 Program Length: 37 weeks Program Overview: Clarusway ‘s AWS and DevOps course is formatted bootcamp-style, making it ideal for learners who want structure and guidance to learn the AWS skills needed to pass the AWS Certified DevOps Engineer – Professional certification.
Students learn on a part-time schedule with a mix of live classes, recorded videos and lab sessions. Live classes occur five times per week for three hours each.
Students don’t need a tech background to enroll, and the cost includes access to mentorship, career development services, upskilling resources and hands-on projects throughout the program. Covered topics and skills include computer networking basics, AWS security, Amazon ElastiCache, Kubernetes and Jenkins.
This course offers a few payment options, including a $5,850 discount when paying upfront and an installment plan through Clarusway with zero interest.
Program Title: Exam Prep: AWS Certified Solutions Architect – Associate Cost: $49/month Program Length: Self-paced with an estimated four-week timeframe Program Overview: The Exam Prep: AWS Certified Solutions Architect – Associate course hosted on Coursera includes video lessons from AWS instructors. The program is broken into six modules covering cloud technical essentials, architecting solutions and exam preparation.
Although no background knowledge is required to enroll, Coursera suggests students have some solutions architect experience to get the most out of the program. The course content features about eight hours of video instruction and readings and is available for as long as the student’s Coursera membership remains active.
Program Title: AWS Certified Cloud Practitioner Foundational Course Cost: $60 Program Length: Self-paced with one year of access Program Overview: Learners pursuing the AWS Certified Cloud Practitioner credential may feel more prepared for the exam after completing this course from ExamPro . It includes nearly 14 hours of videos with 293 lectures exploring cloud architecture, networking, databases, EC2 pricing models, governance and more.
Students also access learning tools like flashcards, video quizlets and practice exams to supplement their learning. Although designed to be completed in one or two weeks, the course content is available for users to work through for up to one year after purchase.
After finishing the course, learners get a certificate of completion to share with their employer or display online.
Program Title: AWS Cloud Complete Bootcamp Cost: Free Program Length: Self-paced with 107 hours of video content Program Overview: freeCodeCamp offers a 107-hour AWS Cloud Complete Bootcamp course on its YouTube channel for free. The program was originally a live class taught over 12 weeks, but learners can now access the recording and work through the content at their own pace.
Students should have at least a beginner’s understanding of cloud computing, as the content builds upon basic skills in AWS architecture, container deployment, CI/CD tools and API development. By the end of the course, learners should feel prepared to design a complete cloud computing project using AWS.
Program Title: Ultimate AWS Certified Cloud Practitioner CLF-C02 Cost: $150 Program Length: Self-paced with 15 hours of video content Program Overview: Udemy is an online educational marketplace that sells digital courses. AWS-certified professional Stephane Maarek created the Ultimate AWS Certified Cloud Practitioner CLF-C02 course to prepare learners for the AWS Certified Cloud Practitioner credential. The program includes videos, quizzes, hands-on projects, downloadable PDFs and practice exams.
As one of the most popular AWS certification courses on Udemy, this course is regularly updated to align with the most recent certification exams. Students don’t need previous AWS cloud experience and can move through the content at their own pace with lifetime access to the program.
Frequently Asked Questions (FAQs) About Online AWS Certification
Can aws certification be done online.
Yes—many AWS certification courses are available online with no time limits for completion, so you can spend as much time as you need on each concept. Some programs also offer live instruction, allowing you to learn online while getting real-time feedback from an instructor.
How much does AWS certification cost online?
Some AWS certification courses are free, but some providers, like AWS and Coursera, charge a monthly subscription for access to their courses. Subscription-based courses typically cost between $20 and $50 per month. Other AWS preparation programs charge a flat fee ranging from a couple of hundred dollars to thousands.
Can I learn AWS in two weeks?
Although you may be able to pass an AWS exam after studying for two weeks, you may still need more time to develop a thorough grasp of AWS skills, especially if you don’t have prior technical experience. If you have lifetime access to your AWS course, consider repeating lectures and assignments until you feel comfortable with the material.
Featured Online Schools
Learn about start dates, transferring credits, availability of financial credit and much more by clicking 'Visit Site'
- 5 Agile Certifications For Project Management Professionals
- 10 Best Cybersecurity Certifications: A Complete Guide
- The Best Data Analytics Certifications For Your Next Career Move
- Free Cybersecurity Training For Certification Prep
- Free PMP Certification Courses
- Free Scrum Master Certification Training And Prep Courses
- Ready To Earn A Business Certificate Online?
- Certificate vs. Degree vs. Bootcamp
- How To Get A TEFL Certification
- How To Earn Medical Billing And Coding Certification Online For Cheap
- Earning An Online Teacher Certification
- PMP Certification And Training
- Choosing Counseling Specializations

Best Online Digital Marketing Certificates Of 2024
Best Online Pharmacy Technician Certification Programs Of 2024
Best GIS Certificates Online Of 2024
Best Online Graphic Design Certificates Of 2024
Shortest Online PMHNP Certificate Programs: Best Of 2024

Best Online Leadership Certificate Programs Of 2024
As a self-proclaimed lifelong learner and former educator, Amy Boyington is passionate about researching and advocating for learners of all ages. For over a decade, Amy has specialized in writing parenting and higher education content that simplifies the process of comparing schools, programs and tuition rates for prospective students and their families. Her work has been featured on several online publications, including Online MBA, Reader’s Digest and BestColleges.
TechRepublic

8 Best Data Science Tools and Software
Apache Spark and Hadoop, Microsoft Power BI, Jupyter Notebook and Alteryx are among the top data science tools for finding business insights. Compare their features, pros and cons.

EU’s AI Act: Europe’s New Rules for Artificial Intelligence
Europe's AI legislation, adopted March 13, attempts to strike a tricky balance between promoting innovation and protecting citizens' rights.

10 Best Predictive Analytics Tools and Software for 2024
Tableau, TIBCO Data Science, IBM and Sisense are among the best software for predictive analytics. Explore their features, pricing, pros and cons to find the best option for your organization.

Tableau Review: Features, Pricing, Pros and Cons
Tableau has three pricing tiers that cater to all kinds of data teams, with capabilities like accelerators and real-time analytics. And if Tableau doesn’t meet your needs, it has a few alternatives worth noting.

Top 6 Enterprise Data Storage Solutions for 2024
Amazon, IDrive, IBM, Google, NetApp and Wasabi offer some of the top enterprise data storage solutions. Explore their features and benefits, and find the right solution for your organization's needs.
Latest Articles

OpenAI, Anthropic Research Reveals More About How LLMs Affect Security and Bias
Anthropic opened a window into the ‘black box’ where ‘features’ steer a large language model’s output. OpenAI dug into the same concept two weeks later with a deep dive into sparse autoencoders.

Some Generative AI Company Employees Pen Letter Wanting ‘Right to Warn’ About Risks
Both the promise and the risk of "human-level" AI has always been part of OpenAI’s makeup. What should business leaders take away from this letter?

Cisco Talos: LilacSquid Threat Actor Targets Multiple Sectors Worldwide With PurpleInk Malware
Find out how the cyberespionage threat actor LilacSquid operates, and then learn how to protect your business from this security risk.

IBM’s Think 2024 News That Should Help Skills & Productivity Issues in Australia
TechRepublic interviewed IBM’s managing director for Australia about how announcements from the recent Think event could impact the tech industry in particular.

Cisco Live 2024: New Unified Observability Experience Packages Cisco & Splunk Insight Tools
The observability suite is the first major overhaul for Splunk products since the Cisco acquisition. Plus, Mistral AI makes a deal with Cisco’s incubator.

Top Tech Conferences & Events to Add to Your Calendar in 2024
A great way to stay current with the latest technology trends and innovations is by attending conferences. Read and bookmark our 2024 tech events guide.

Intel Lunar Lake NPU Brings 48 TOPS of AI Acceleration
Competition for AI speed heats up. Plus, the first of the two new Xeon 6 processors is now available, and Gaudi 3 deals have been cinched with manufacturers.

Cisco Live 2024: Cisco Unveils AI Deployment Solution With NVIDIA
A $1 billion commitment will send Cisco money to Cohere, Mistral AI and Scale AI.

The 5 Best Udemy Courses That Are Worth Taking in 2024
Udemy is an online platform for learning at your own pace. Boost your career with our picks for the best Udemy courses for learning tech skills online in 2024.

What Is Data Quality? Definition and Best Practices
Data quality refers to the degree to which data is accurate, complete, reliable and relevant for its intended use.

TechRepublic Premium Editorial Calendar: Policies, Checklists, Hiring Kits and Glossaries for Download
TechRepublic Premium content helps you solve your toughest IT issues and jump-start your career or next project.

What is the EU’s AI Office? New Body Formed to Oversee the Rollout of General Purpose Models and AI Act
The AI Office will be responsible for enforcing the rules of the AI Act, ensuring its implementation across Member States, funding AI and robotics innovation and more.

What is Data Science? Benefits, Techniques and Use Cases
Data science involves extracting valuable insights from complex datasets. While this process can be technically challenging and time-consuming, it can lead to better business decision-making.

Gartner’s 7 Predictions for the Future of Australian & Global Cloud Computing
An explosion in AI computing, a big shift in workloads to the cloud, and difficulties in gaining value from hybrid cloud strategies are among the trends Australian cloud professionals will see to 2028.

OpenAI Adds PwC as Its First Resale Partner for the ChatGPT Enterprise Tier
PwC employees have 100,000 ChatGPT Enterprise seats. Plus, OpenAI forms a new safety and security committee in their quest for more powerful AI, and seals media deals.
Create a TechRepublic Account
Get the web's best business technology news, tutorials, reviews, trends, and analysis—in your inbox. Let's start with the basics.
* - indicates required fields
Sign in to TechRepublic
Lost your password? Request a new password
Reset Password
Please enter your email adress. You will receive an email message with instructions on how to reset your password.
Check your email for a password reset link. If you didn't receive an email don't forgot to check your spam folder, otherwise contact support .
Welcome. Tell us a little bit about you.
This will help us provide you with customized content.
Want to receive more TechRepublic news?
You're all set.
Thanks for signing up! Keep an eye out for a confirmation email from our team. To ensure any newsletters you subscribed to hit your inbox, make sure to add [email protected] to your contacts list.
Use an IAM role in the AWS CLI
An AWS Identity and Access Management (IAM) role is an authorization tool that lets a user gain additional (or different) permissions, or get permissions to perform actions in a different AWS account.
Prerequisites
Overview of using iam roles, configuring and using a role, using multi-factor authentication, cross-account roles and external id, specifying a role session name for easier auditing, assume role with web identity, clearing cached credentials.
To run the iam commands, you need to install and configure the AWS CLI. For more information, see Install or update to the latest version of the AWS CLI .
You can configure the AWS Command Line Interface (AWS CLI) to use an IAM role by defining a profile for the role in the ~/.aws/config file.
The following example shows a role profile named marketingadmin . If you run commands with --profile marketingadmin (or specify it with the AWS_PROFILE environment variable ), the AWS CLI uses the credentials defined in a separate profile user1 to assume the role with the Amazon Resource Name (ARN) arn:aws:iam:: 123456789012 :role/ marketingadminrole . You can run any operations that are allowed by the permissions assigned to that role.
You can then specify a source_profile that points to a separate named profile that contains user credentials with permission to use the role. In the previous example, the marketingadmin profile uses the credentials in the user1 profile. When you specify that an AWS CLI command is to use the profile marketingadmin , the AWS CLI automatically looks up the credentials for the linked user1 profile and uses them to request temporary credentials for the specified IAM role. The CLI uses the sts:AssumeRole operation in the background to accomplish this. Those temporary credentials are then used to run the requested AWS CLI command. The specified role must have attached IAM permission policies that allow the requested AWS CLI command to run.
To run a AWS CLI command from within an Amazon Elastic Compute Cloud (Amazon EC2) instance or an Amazon Elastic Container Service (Amazon ECS) container, you can use an IAM role attached to the instance profile or the container. If you specify no profile or set no environment variables, that role is used directly. This enables you to avoid storing long-lived access keys on your instances. You can also use those instance or container roles only to get credentials for another role. To do this, you use credential_source (instead of source_profile ) to specify how to find the credentials. The credential_source attribute supports the following values:
Environment – Retrieves the source credentials from environment variables.
Ec2InstanceMetadata – Uses the IAM role attached to the Amazon EC2 instance profile.
EcsContainer – Uses the IAM role attached to the Amazon ECS container.
The following example shows the same marketingadminrole role used by referencing an Amazon EC2 instance profile.
When you invoke a role, you have additional options that you can require, such as the use of multi-factor authentication and an External ID (used by third-party companies to access their clients' resources). You can also specify unique role session names that can be more easily audited in AWS CloudTrail logs.
When you run commands using a profile that specifies an IAM role, the AWS CLI uses the source profile's credentials to call AWS Security Token Service (AWS STS) and request temporary credentials for the specified role. The user in the source profile must have permission to call sts:assume-role for the role in the specified profile. The role must have a trust relationship that allows the user in the source profile to use the role. The process of retrieving and then using temporary credentials for a role is often referred to as assuming the role .
You can create a role in IAM with the permissions that you want users to assume by following the procedure under Creating a Role to Delegate Permissions to an IAM user in the AWS Identity and Access Management User Guide . If the role and the source profile's user are in the same account, you can enter your own account ID when configuring the role's trust relationship.
After creating the role, modify the trust relationship to allow the user to assume it.
The following example shows a trust policy that you could attach to a role. This policy allows the role to be assumed by any user in the account 123456789012, if the administrator of that account explicitly grants the sts:AssumeRole permission to the user.
The trust policy doesn't actually grant permissions. The administrator of the account must delegate the permission to assume the role to individual users by attaching a policy with the appropriate permissions. The following example shows a policy that you can attach to a user that allows the user to assume only the marketingadminrole role. For more information about granting a user access to assume a role, see Granting a User Permission to Switch Roles in the IAM User Guide .
The user doesn't need to have additional permissions to run the AWS CLI commands using the role profile. Instead, the permissions to run the command come from those attached to the role . You attach permission policies to the role to specify which actions can be performed against which AWS resources. For more information about attaching permissions to a role (which works identically to a user), see Changing Permissions for an IAM user in the IAM User Guide .
Now that you have the role profile, role permissions, role trust relationship, and user permissions correctly configured, you can use the role at the command line by invoking the --profile option. For example, the following calls the Amazon S3 ls command using the permissions attached to the marketingadmin role as defined by the example at the beginning of this topic.
To use the role for several calls, you can set the AWS_PROFILE environment variable for the current session from the command line. While that environment variable is defined, you don't have to specify the --profile option on each command.
Linux or macOS
For more information about configuring users and roles, see Users and Groups and Roles in the IAM User Guide .
For additional security, you can require that users provide a one-time key generated from a multi-factor authentication (MFA) device, a U2F device, or mobile app when they attempt to make a call using the role profile.
First, you can choose to modify the trust relationship on the IAM role to require MFA. This prevents anyone from using the role without first authenticating by using MFA. For an example, see the Condition line in the following example. This policy allows the user named anika to assume the role the policy is attached to, but only if they authenticate by using MFA.
Next, add a line to the role profile that specifies the ARN of the user's MFA device. The following sample config file entries show two role profiles that both use the access keys for the user anika to request temporary credentials for the role cli-role . The user anika has permissions to assume the role, granted by the role's trust policy.
The mfa_serial setting can take an ARN, as shown, or the serial number of a hardware MFA token.
The first profile, role-without-mfa , doesn't require MFA. However, because the previous example trust policy attached to the role requires MFA, any attempt to run a command with this profile fails.
The second profile entry, role-with-mfa , identifies an MFA device to use. When the user attempts to run a AWS CLI command with this profile, the AWS CLI prompts the user to enter the one-time password (OTP) that the MFA device provides. If the MFA authentication succeeds, the command performs the requested operation. The OTP is not displayed on the screen.
You can enable users to use roles that belong to different accounts by configuring the role as a cross-account role. During role creation, set the role type to Another AWS account , as described in Creating a Role to Delegate Permissions to an IAM user . Optionally, select Require MFA . Require MFA configures the appropriate condition in the trust relationship, as described in Using multi-factor authentication .
If you use an external ID to provide additional control over who can use a role across accounts, you must also add the external_id parameter to the role profile. You typically use this only when the other account is controlled by someone outside your company or organization.
When many individuals share a role, auditing becomes more of a challenge. You want to associate each operation invoked with the individual who invoked the action. However, when the individual uses a role, the assumption of the role by the individual is a separate action from the invoking of an operation, and you must manually correlate the two.
You can simplify this by specifying unique role session names when users assume a role. You do this by adding a role_session_name parameter to each named profile in the config file that specifies a role. The role_session_name value is passed to the AssumeRole operation and becomes part of the ARN for the role session. It is also included in the AWS CloudTrail logs for all logged operations.
For example, you could create a role-based profile as follows.
This results in the role session having the following ARN.
Also, all AWS CloudTrail logs include the role session name in the information captured for each operation.
You can configure a profile to indicate that the AWS CLI should assume a role using web identity federation and Open ID Connect (OIDC) . When you specify this in a profile, the AWS CLI automatically makes the corresponding AWS STS AssumeRoleWithWebIdentity call for you.
When you specify a profile that uses an IAM role, the AWS CLI makes the appropriate calls to retrieve temporary credentials. These credentials are stored in ~/.aws/cli/cache . Subsequent AWS CLI commands that specify the same profile use the cached temporary credentials until they expire. At that point, the AWS CLI automatically refreshes the credentials.
To retrieve and use temporary credentials using web identity federation, you can specify the following configuration values in a shared profile.
Specifies the ARN of the role to assume.
Specifies the path to a file which contains an OAuth 2.0 access token or OpenID Connect ID token that is provided by the identity provider. The AWS CLI loads this file and passes its content as the WebIdentityToken argument of the AssumeRoleWithWebIdentity operation.
Specifies an optional name applied to this assume-role session.
The following is an example of the minimal amount of configuration needed to configure an assume role with web identity profile.
You can also provide this configuration by using environment variables .
The ARN of the role to assume.
The path to the web identity token file.
The name applied to this assume-role session.
These environment variables currently apply only to the assume role with web identity provider. They don't apply to the general assume role provider configuration.
When you use a role, the AWS CLI caches the temporary credentials locally until they expire. The next time you try to use them, the AWS CLI attempts to renew them on your behalf.
If your role's temporary credentials are revoked , they are not renewed automatically, and attempts to use them fail. However, you can delete the cache to force the AWS CLI to retrieve new credentials.

To use the Amazon Web Services Documentation, Javascript must be enabled. Please refer to your browser's Help pages for instructions.
Thanks for letting us know we're doing a good job!
If you've got a moment, please tell us what we did right so we can do more of it.
Thanks for letting us know this page needs work. We're sorry we let you down.
If you've got a moment, please tell us how we can make the documentation better.

IMAGES
VIDEO
COMMENTS
For a list of a few supported apps that you can use as virtual MFA devices, see Multi-Factor Authentication. For instructions on setting up a virtual MFA device with AWS, see Enabling a virtual multi-factor authentication (MFA) device (console). Hardware TOTP token
AWS Multi-Factor Authentication (MFA) is a simple best practice that adds an extra layer of protection on top of your user name and password. With MFA enabled, when a user signs in to an AWS website, they will be prompted for their user name and password (the first factor—what they know), as well as for an authentication response from their AWS MFA device (the second factor—what they have).
To do so, edit the credentials file in the .aws folder in the home directory of the user. In the credentials file, add a new profile configuration for issuing MFA-authenticated commands. Here's an example profile configuration: [mfa] aws_access_key_id = example-access-key-as-in-returned-output.
Logging into the AWS Management Console. After successfully setting up MFA for your user, each login will be prompted for an MFA code. Go back to your authenticator app and type in the current code that appears. Note the limited time that the code is valid and can be used to complete your login.
Multi-factor authentication with TOTP. You can use Time-based One-Time Password (TOTP) for multi-factor authentication (MFA) in your web or mobile applications. The Amplify Auth category includes support for TOTP setup and verification using authenticator apps, offering an integrated solution and enhanced security for your users.
In the AWS Management Console, search for "IAM" in the "Search Services" bar and select "IAM.". On the IAM Dashboard, click on "Add MFA" which is on the right of "Add MFA for yourself" under "Security Recommendations". Security Credentials Tab. This will bring you to "Security credentials" with two steps to complete ...
Select Work or school account. Hold your camera over the QR code on screen. AWS is automatically associated. We then just have to put in the next two codes that appear on the app and click Assign MFA. The Setup should be successful. The user can then login again as normal: But will then be prompted for their MFA code from the authenticator app ...
alias aws="aws-mfa-secure session" Restart your terminal. Example with Output $ export AWS_PROFILE=mfa $ aws s3 ls Please provide your MFA code: 751888 2019-09-21 15:53:34 my-example-test-bucket $ aws s3 ls 2019-09-21 15:53:34 my-example-test-bucket $ Assume Role Profiles. Assume role profiles work already for the AWS CLI, here's an example:
Login to your AWS Management Console account. Open My Security Credentials under the dropdown menu. Note: Before creating MFA you need to delete all Security Access keys for your account. Click on Assign MFA Device. Now, select the Virtual MFA device and click on Continue.
The Amazon Web Services (AWS) Multi-Factor Authentication (MFA) App is the perfect tool for keeping your data safe and secure. With the help of the MFA App, you can easily add an extra layer of security to your online accounts, ensuring that only authorised users are granted access. As well as providing password security, the ...
Program Title: AWS Certified Cloud Practitioner Foundational Course. Cost: $60. Program Length: Self-paced with one year of access. Program Overview: Learners pursuing the AWS Certified Cloud ...
8 Best Data Science Tools and Software. Apache Spark and Hadoop, Microsoft Power BI, Jupyter Notebook and Alteryx are among the top data science tools for finding business insights. Compare their ...
Using multi-factor authentication. For additional security, you can require that users provide a one-time key generated from a multi-factor authentication (MFA) device, a U2F device, or mobile app when they attempt to make a call using the role profile. First, you can choose to modify the trust relationship on the IAM role to require MFA.