- Privacy Policy

Home » Case Study – Methods, Examples and Guide

Case Study – Methods, Examples and Guide
Table of Contents

A case study is a research method that involves an in-depth examination and analysis of a particular phenomenon or case, such as an individual, organization, community, event, or situation.
It is a qualitative research approach that aims to provide a detailed and comprehensive understanding of the case being studied. Case studies typically involve multiple sources of data, including interviews, observations, documents, and artifacts, which are analyzed using various techniques, such as content analysis, thematic analysis, and grounded theory. The findings of a case study are often used to develop theories, inform policy or practice, or generate new research questions.
Types of Case Study
Types and Methods of Case Study are as follows:
Single-Case Study
A single-case study is an in-depth analysis of a single case. This type of case study is useful when the researcher wants to understand a specific phenomenon in detail.
For Example , A researcher might conduct a single-case study on a particular individual to understand their experiences with a particular health condition or a specific organization to explore their management practices. The researcher collects data from multiple sources, such as interviews, observations, and documents, and uses various techniques to analyze the data, such as content analysis or thematic analysis. The findings of a single-case study are often used to generate new research questions, develop theories, or inform policy or practice.
Multiple-Case Study
A multiple-case study involves the analysis of several cases that are similar in nature. This type of case study is useful when the researcher wants to identify similarities and differences between the cases.
For Example, a researcher might conduct a multiple-case study on several companies to explore the factors that contribute to their success or failure. The researcher collects data from each case, compares and contrasts the findings, and uses various techniques to analyze the data, such as comparative analysis or pattern-matching. The findings of a multiple-case study can be used to develop theories, inform policy or practice, or generate new research questions.
Exploratory Case Study
An exploratory case study is used to explore a new or understudied phenomenon. This type of case study is useful when the researcher wants to generate hypotheses or theories about the phenomenon.
For Example, a researcher might conduct an exploratory case study on a new technology to understand its potential impact on society. The researcher collects data from multiple sources, such as interviews, observations, and documents, and uses various techniques to analyze the data, such as grounded theory or content analysis. The findings of an exploratory case study can be used to generate new research questions, develop theories, or inform policy or practice.
Descriptive Case Study
A descriptive case study is used to describe a particular phenomenon in detail. This type of case study is useful when the researcher wants to provide a comprehensive account of the phenomenon.
For Example, a researcher might conduct a descriptive case study on a particular community to understand its social and economic characteristics. The researcher collects data from multiple sources, such as interviews, observations, and documents, and uses various techniques to analyze the data, such as content analysis or thematic analysis. The findings of a descriptive case study can be used to inform policy or practice or generate new research questions.
Instrumental Case Study
An instrumental case study is used to understand a particular phenomenon that is instrumental in achieving a particular goal. This type of case study is useful when the researcher wants to understand the role of the phenomenon in achieving the goal.
For Example, a researcher might conduct an instrumental case study on a particular policy to understand its impact on achieving a particular goal, such as reducing poverty. The researcher collects data from multiple sources, such as interviews, observations, and documents, and uses various techniques to analyze the data, such as content analysis or thematic analysis. The findings of an instrumental case study can be used to inform policy or practice or generate new research questions.
Case Study Data Collection Methods
Here are some common data collection methods for case studies:
Interviews involve asking questions to individuals who have knowledge or experience relevant to the case study. Interviews can be structured (where the same questions are asked to all participants) or unstructured (where the interviewer follows up on the responses with further questions). Interviews can be conducted in person, over the phone, or through video conferencing.
Observations
Observations involve watching and recording the behavior and activities of individuals or groups relevant to the case study. Observations can be participant (where the researcher actively participates in the activities) or non-participant (where the researcher observes from a distance). Observations can be recorded using notes, audio or video recordings, or photographs.
Documents can be used as a source of information for case studies. Documents can include reports, memos, emails, letters, and other written materials related to the case study. Documents can be collected from the case study participants or from public sources.
Surveys involve asking a set of questions to a sample of individuals relevant to the case study. Surveys can be administered in person, over the phone, through mail or email, or online. Surveys can be used to gather information on attitudes, opinions, or behaviors related to the case study.
Artifacts are physical objects relevant to the case study. Artifacts can include tools, equipment, products, or other objects that provide insights into the case study phenomenon.
How to conduct Case Study Research
Conducting a case study research involves several steps that need to be followed to ensure the quality and rigor of the study. Here are the steps to conduct case study research:
- Define the research questions: The first step in conducting a case study research is to define the research questions. The research questions should be specific, measurable, and relevant to the case study phenomenon under investigation.
- Select the case: The next step is to select the case or cases to be studied. The case should be relevant to the research questions and should provide rich and diverse data that can be used to answer the research questions.
- Collect data: Data can be collected using various methods, such as interviews, observations, documents, surveys, and artifacts. The data collection method should be selected based on the research questions and the nature of the case study phenomenon.
- Analyze the data: The data collected from the case study should be analyzed using various techniques, such as content analysis, thematic analysis, or grounded theory. The analysis should be guided by the research questions and should aim to provide insights and conclusions relevant to the research questions.
- Draw conclusions: The conclusions drawn from the case study should be based on the data analysis and should be relevant to the research questions. The conclusions should be supported by evidence and should be clearly stated.
- Validate the findings: The findings of the case study should be validated by reviewing the data and the analysis with participants or other experts in the field. This helps to ensure the validity and reliability of the findings.
- Write the report: The final step is to write the report of the case study research. The report should provide a clear description of the case study phenomenon, the research questions, the data collection methods, the data analysis, the findings, and the conclusions. The report should be written in a clear and concise manner and should follow the guidelines for academic writing.
Examples of Case Study
Here are some examples of case study research:
- The Hawthorne Studies : Conducted between 1924 and 1932, the Hawthorne Studies were a series of case studies conducted by Elton Mayo and his colleagues to examine the impact of work environment on employee productivity. The studies were conducted at the Hawthorne Works plant of the Western Electric Company in Chicago and included interviews, observations, and experiments.
- The Stanford Prison Experiment: Conducted in 1971, the Stanford Prison Experiment was a case study conducted by Philip Zimbardo to examine the psychological effects of power and authority. The study involved simulating a prison environment and assigning participants to the role of guards or prisoners. The study was controversial due to the ethical issues it raised.
- The Challenger Disaster: The Challenger Disaster was a case study conducted to examine the causes of the Space Shuttle Challenger explosion in 1986. The study included interviews, observations, and analysis of data to identify the technical, organizational, and cultural factors that contributed to the disaster.
- The Enron Scandal: The Enron Scandal was a case study conducted to examine the causes of the Enron Corporation’s bankruptcy in 2001. The study included interviews, analysis of financial data, and review of documents to identify the accounting practices, corporate culture, and ethical issues that led to the company’s downfall.
- The Fukushima Nuclear Disaster : The Fukushima Nuclear Disaster was a case study conducted to examine the causes of the nuclear accident that occurred at the Fukushima Daiichi Nuclear Power Plant in Japan in 2011. The study included interviews, analysis of data, and review of documents to identify the technical, organizational, and cultural factors that contributed to the disaster.
Application of Case Study
Case studies have a wide range of applications across various fields and industries. Here are some examples:
Business and Management
Case studies are widely used in business and management to examine real-life situations and develop problem-solving skills. Case studies can help students and professionals to develop a deep understanding of business concepts, theories, and best practices.
Case studies are used in healthcare to examine patient care, treatment options, and outcomes. Case studies can help healthcare professionals to develop critical thinking skills, diagnose complex medical conditions, and develop effective treatment plans.
Case studies are used in education to examine teaching and learning practices. Case studies can help educators to develop effective teaching strategies, evaluate student progress, and identify areas for improvement.
Social Sciences
Case studies are widely used in social sciences to examine human behavior, social phenomena, and cultural practices. Case studies can help researchers to develop theories, test hypotheses, and gain insights into complex social issues.
Law and Ethics
Case studies are used in law and ethics to examine legal and ethical dilemmas. Case studies can help lawyers, policymakers, and ethical professionals to develop critical thinking skills, analyze complex cases, and make informed decisions.
Purpose of Case Study
The purpose of a case study is to provide a detailed analysis of a specific phenomenon, issue, or problem in its real-life context. A case study is a qualitative research method that involves the in-depth exploration and analysis of a particular case, which can be an individual, group, organization, event, or community.
The primary purpose of a case study is to generate a comprehensive and nuanced understanding of the case, including its history, context, and dynamics. Case studies can help researchers to identify and examine the underlying factors, processes, and mechanisms that contribute to the case and its outcomes. This can help to develop a more accurate and detailed understanding of the case, which can inform future research, practice, or policy.
Case studies can also serve other purposes, including:
- Illustrating a theory or concept: Case studies can be used to illustrate and explain theoretical concepts and frameworks, providing concrete examples of how they can be applied in real-life situations.
- Developing hypotheses: Case studies can help to generate hypotheses about the causal relationships between different factors and outcomes, which can be tested through further research.
- Providing insight into complex issues: Case studies can provide insights into complex and multifaceted issues, which may be difficult to understand through other research methods.
- Informing practice or policy: Case studies can be used to inform practice or policy by identifying best practices, lessons learned, or areas for improvement.
Advantages of Case Study Research
There are several advantages of case study research, including:
- In-depth exploration: Case study research allows for a detailed exploration and analysis of a specific phenomenon, issue, or problem in its real-life context. This can provide a comprehensive understanding of the case and its dynamics, which may not be possible through other research methods.
- Rich data: Case study research can generate rich and detailed data, including qualitative data such as interviews, observations, and documents. This can provide a nuanced understanding of the case and its complexity.
- Holistic perspective: Case study research allows for a holistic perspective of the case, taking into account the various factors, processes, and mechanisms that contribute to the case and its outcomes. This can help to develop a more accurate and comprehensive understanding of the case.
- Theory development: Case study research can help to develop and refine theories and concepts by providing empirical evidence and concrete examples of how they can be applied in real-life situations.
- Practical application: Case study research can inform practice or policy by identifying best practices, lessons learned, or areas for improvement.
- Contextualization: Case study research takes into account the specific context in which the case is situated, which can help to understand how the case is influenced by the social, cultural, and historical factors of its environment.
Limitations of Case Study Research
There are several limitations of case study research, including:
- Limited generalizability : Case studies are typically focused on a single case or a small number of cases, which limits the generalizability of the findings. The unique characteristics of the case may not be applicable to other contexts or populations, which may limit the external validity of the research.
- Biased sampling: Case studies may rely on purposive or convenience sampling, which can introduce bias into the sample selection process. This may limit the representativeness of the sample and the generalizability of the findings.
- Subjectivity: Case studies rely on the interpretation of the researcher, which can introduce subjectivity into the analysis. The researcher’s own biases, assumptions, and perspectives may influence the findings, which may limit the objectivity of the research.
- Limited control: Case studies are typically conducted in naturalistic settings, which limits the control that the researcher has over the environment and the variables being studied. This may limit the ability to establish causal relationships between variables.
- Time-consuming: Case studies can be time-consuming to conduct, as they typically involve a detailed exploration and analysis of a specific case. This may limit the feasibility of conducting multiple case studies or conducting case studies in a timely manner.
- Resource-intensive: Case studies may require significant resources, including time, funding, and expertise. This may limit the ability of researchers to conduct case studies in resource-constrained settings.
About the author
Muhammad Hassan
Researcher, Academic Writer, Web developer
You may also like

Questionnaire – Definition, Types, and Examples

Observational Research – Methods and Guide

Quantitative Research – Methods, Types and...

Qualitative Research Methods

Explanatory Research – Types, Methods, Guide

Survey Research – Types, Methods, Examples

The Ultimate Guide to Qualitative Research - Part 1: The Basics

- Introduction and overview
- What is qualitative research?
- What is qualitative data?
- Examples of qualitative data
- Qualitative vs. quantitative research
- Mixed methods
- Qualitative research preparation
- Theoretical perspective
- Theoretical framework
- Literature reviews
Research question
- Conceptual framework
- Conceptual vs. theoretical framework
Data collection
- Qualitative research methods
- Focus groups
- Observational research
What is a case study?
Applications for case study research, what is a good case study, process of case study design, benefits and limitations of case studies.
- Ethnographical research
- Ethical considerations
- Confidentiality and privacy
- Power dynamics
- Reflexivity
Case studies
Case studies are essential to qualitative research , offering a lens through which researchers can investigate complex phenomena within their real-life contexts. This chapter explores the concept, purpose, applications, examples, and types of case studies and provides guidance on how to conduct case study research effectively.

Whereas quantitative methods look at phenomena at scale, case study research looks at a concept or phenomenon in considerable detail. While analyzing a single case can help understand one perspective regarding the object of research inquiry, analyzing multiple cases can help obtain a more holistic sense of the topic or issue. Let's provide a basic definition of a case study, then explore its characteristics and role in the qualitative research process.
Definition of a case study
A case study in qualitative research is a strategy of inquiry that involves an in-depth investigation of a phenomenon within its real-world context. It provides researchers with the opportunity to acquire an in-depth understanding of intricate details that might not be as apparent or accessible through other methods of research. The specific case or cases being studied can be a single person, group, or organization – demarcating what constitutes a relevant case worth studying depends on the researcher and their research question .
Among qualitative research methods , a case study relies on multiple sources of evidence, such as documents, artifacts, interviews , or observations , to present a complete and nuanced understanding of the phenomenon under investigation. The objective is to illuminate the readers' understanding of the phenomenon beyond its abstract statistical or theoretical explanations.
Characteristics of case studies
Case studies typically possess a number of distinct characteristics that set them apart from other research methods. These characteristics include a focus on holistic description and explanation, flexibility in the design and data collection methods, reliance on multiple sources of evidence, and emphasis on the context in which the phenomenon occurs.
Furthermore, case studies can often involve a longitudinal examination of the case, meaning they study the case over a period of time. These characteristics allow case studies to yield comprehensive, in-depth, and richly contextualized insights about the phenomenon of interest.
The role of case studies in research
Case studies hold a unique position in the broader landscape of research methods aimed at theory development. They are instrumental when the primary research interest is to gain an intensive, detailed understanding of a phenomenon in its real-life context.
In addition, case studies can serve different purposes within research - they can be used for exploratory, descriptive, or explanatory purposes, depending on the research question and objectives. This flexibility and depth make case studies a valuable tool in the toolkit of qualitative researchers.
Remember, a well-conducted case study can offer a rich, insightful contribution to both academic and practical knowledge through theory development or theory verification, thus enhancing our understanding of complex phenomena in their real-world contexts.
What is the purpose of a case study?
Case study research aims for a more comprehensive understanding of phenomena, requiring various research methods to gather information for qualitative analysis . Ultimately, a case study can allow the researcher to gain insight into a particular object of inquiry and develop a theoretical framework relevant to the research inquiry.
Why use case studies in qualitative research?
Using case studies as a research strategy depends mainly on the nature of the research question and the researcher's access to the data.
Conducting case study research provides a level of detail and contextual richness that other research methods might not offer. They are beneficial when there's a need to understand complex social phenomena within their natural contexts.
The explanatory, exploratory, and descriptive roles of case studies
Case studies can take on various roles depending on the research objectives. They can be exploratory when the research aims to discover new phenomena or define new research questions; they are descriptive when the objective is to depict a phenomenon within its context in a detailed manner; and they can be explanatory if the goal is to understand specific relationships within the studied context. Thus, the versatility of case studies allows researchers to approach their topic from different angles, offering multiple ways to uncover and interpret the data .
The impact of case studies on knowledge development
Case studies play a significant role in knowledge development across various disciplines. Analysis of cases provides an avenue for researchers to explore phenomena within their context based on the collected data.

This can result in the production of rich, practical insights that can be instrumental in both theory-building and practice. Case studies allow researchers to delve into the intricacies and complexities of real-life situations, uncovering insights that might otherwise remain hidden.
Types of case studies
In qualitative research , a case study is not a one-size-fits-all approach. Depending on the nature of the research question and the specific objectives of the study, researchers might choose to use different types of case studies. These types differ in their focus, methodology, and the level of detail they provide about the phenomenon under investigation.
Understanding these types is crucial for selecting the most appropriate approach for your research project and effectively achieving your research goals. Let's briefly look at the main types of case studies.
Exploratory case studies
Exploratory case studies are typically conducted to develop a theory or framework around an understudied phenomenon. They can also serve as a precursor to a larger-scale research project. Exploratory case studies are useful when a researcher wants to identify the key issues or questions which can spur more extensive study or be used to develop propositions for further research. These case studies are characterized by flexibility, allowing researchers to explore various aspects of a phenomenon as they emerge, which can also form the foundation for subsequent studies.
Descriptive case studies
Descriptive case studies aim to provide a complete and accurate representation of a phenomenon or event within its context. These case studies are often based on an established theoretical framework, which guides how data is collected and analyzed. The researcher is concerned with describing the phenomenon in detail, as it occurs naturally, without trying to influence or manipulate it.
Explanatory case studies
Explanatory case studies are focused on explanation - they seek to clarify how or why certain phenomena occur. Often used in complex, real-life situations, they can be particularly valuable in clarifying causal relationships among concepts and understanding the interplay between different factors within a specific context.

Intrinsic, instrumental, and collective case studies
These three categories of case studies focus on the nature and purpose of the study. An intrinsic case study is conducted when a researcher has an inherent interest in the case itself. Instrumental case studies are employed when the case is used to provide insight into a particular issue or phenomenon. A collective case study, on the other hand, involves studying multiple cases simultaneously to investigate some general phenomena.
Each type of case study serves a different purpose and has its own strengths and challenges. The selection of the type should be guided by the research question and objectives, as well as the context and constraints of the research.
The flexibility, depth, and contextual richness offered by case studies make this approach an excellent research method for various fields of study. They enable researchers to investigate real-world phenomena within their specific contexts, capturing nuances that other research methods might miss. Across numerous fields, case studies provide valuable insights into complex issues.
Critical information systems research
Case studies provide a detailed understanding of the role and impact of information systems in different contexts. They offer a platform to explore how information systems are designed, implemented, and used and how they interact with various social, economic, and political factors. Case studies in this field often focus on examining the intricate relationship between technology, organizational processes, and user behavior, helping to uncover insights that can inform better system design and implementation.
Health research
Health research is another field where case studies are highly valuable. They offer a way to explore patient experiences, healthcare delivery processes, and the impact of various interventions in a real-world context.

Case studies can provide a deep understanding of a patient's journey, giving insights into the intricacies of disease progression, treatment effects, and the psychosocial aspects of health and illness.
Asthma research studies
Specifically within medical research, studies on asthma often employ case studies to explore the individual and environmental factors that influence asthma development, management, and outcomes. A case study can provide rich, detailed data about individual patients' experiences, from the triggers and symptoms they experience to the effectiveness of various management strategies. This can be crucial for developing patient-centered asthma care approaches.
Other fields
Apart from the fields mentioned, case studies are also extensively used in business and management research, education research, and political sciences, among many others. They provide an opportunity to delve into the intricacies of real-world situations, allowing for a comprehensive understanding of various phenomena.
Case studies, with their depth and contextual focus, offer unique insights across these varied fields. They allow researchers to illuminate the complexities of real-life situations, contributing to both theory and practice.
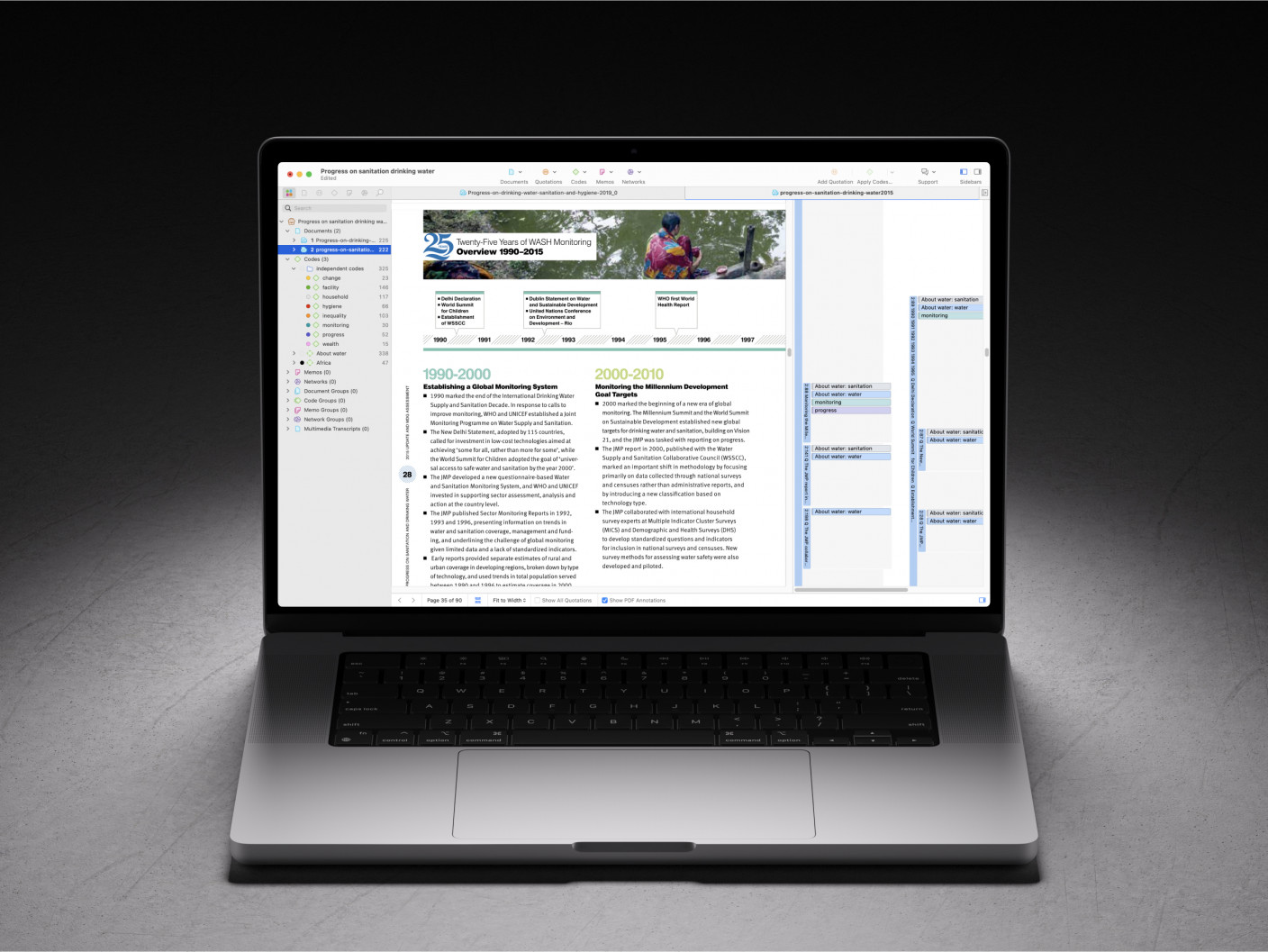
Whatever field you're in, ATLAS.ti puts your data to work for you
Download a free trial of ATLAS.ti to turn your data into insights.
Understanding the key elements of case study design is crucial for conducting rigorous and impactful case study research. A well-structured design guides the researcher through the process, ensuring that the study is methodologically sound and its findings are reliable and valid. The main elements of case study design include the research question , propositions, units of analysis, and the logic linking the data to the propositions.
The research question is the foundation of any research study. A good research question guides the direction of the study and informs the selection of the case, the methods of collecting data, and the analysis techniques. A well-formulated research question in case study research is typically clear, focused, and complex enough to merit further detailed examination of the relevant case(s).
Propositions
Propositions, though not necessary in every case study, provide a direction by stating what we might expect to find in the data collected. They guide how data is collected and analyzed by helping researchers focus on specific aspects of the case. They are particularly important in explanatory case studies, which seek to understand the relationships among concepts within the studied phenomenon.
Units of analysis
The unit of analysis refers to the case, or the main entity or entities that are being analyzed in the study. In case study research, the unit of analysis can be an individual, a group, an organization, a decision, an event, or even a time period. It's crucial to clearly define the unit of analysis, as it shapes the qualitative data analysis process by allowing the researcher to analyze a particular case and synthesize analysis across multiple case studies to draw conclusions.
Argumentation
This refers to the inferential model that allows researchers to draw conclusions from the data. The researcher needs to ensure that there is a clear link between the data, the propositions (if any), and the conclusions drawn. This argumentation is what enables the researcher to make valid and credible inferences about the phenomenon under study.
Understanding and carefully considering these elements in the design phase of a case study can significantly enhance the quality of the research. It can help ensure that the study is methodologically sound and its findings contribute meaningful insights about the case.
Ready to jumpstart your research with ATLAS.ti?
Conceptualize your research project with our intuitive data analysis interface. Download a free trial today.
Conducting a case study involves several steps, from defining the research question and selecting the case to collecting and analyzing data . This section outlines these key stages, providing a practical guide on how to conduct case study research.
Defining the research question
The first step in case study research is defining a clear, focused research question. This question should guide the entire research process, from case selection to analysis. It's crucial to ensure that the research question is suitable for a case study approach. Typically, such questions are exploratory or descriptive in nature and focus on understanding a phenomenon within its real-life context.
Selecting and defining the case
The selection of the case should be based on the research question and the objectives of the study. It involves choosing a unique example or a set of examples that provide rich, in-depth data about the phenomenon under investigation. After selecting the case, it's crucial to define it clearly, setting the boundaries of the case, including the time period and the specific context.
Previous research can help guide the case study design. When considering a case study, an example of a case could be taken from previous case study research and used to define cases in a new research inquiry. Considering recently published examples can help understand how to select and define cases effectively.
Developing a detailed case study protocol
A case study protocol outlines the procedures and general rules to be followed during the case study. This includes the data collection methods to be used, the sources of data, and the procedures for analysis. Having a detailed case study protocol ensures consistency and reliability in the study.
The protocol should also consider how to work with the people involved in the research context to grant the research team access to collecting data. As mentioned in previous sections of this guide, establishing rapport is an essential component of qualitative research as it shapes the overall potential for collecting and analyzing data.
Collecting data
Gathering data in case study research often involves multiple sources of evidence, including documents, archival records, interviews, observations, and physical artifacts. This allows for a comprehensive understanding of the case. The process for gathering data should be systematic and carefully documented to ensure the reliability and validity of the study.
Analyzing and interpreting data
The next step is analyzing the data. This involves organizing the data , categorizing it into themes or patterns , and interpreting these patterns to answer the research question. The analysis might also involve comparing the findings with prior research or theoretical propositions.
Writing the case study report
The final step is writing the case study report . This should provide a detailed description of the case, the data, the analysis process, and the findings. The report should be clear, organized, and carefully written to ensure that the reader can understand the case and the conclusions drawn from it.
Each of these steps is crucial in ensuring that the case study research is rigorous, reliable, and provides valuable insights about the case.
The type, depth, and quality of data in your study can significantly influence the validity and utility of the study. In case study research, data is usually collected from multiple sources to provide a comprehensive and nuanced understanding of the case. This section will outline the various methods of collecting data used in case study research and discuss considerations for ensuring the quality of the data.
Interviews are a common method of gathering data in case study research. They can provide rich, in-depth data about the perspectives, experiences, and interpretations of the individuals involved in the case. Interviews can be structured , semi-structured , or unstructured , depending on the research question and the degree of flexibility needed.
Observations
Observations involve the researcher observing the case in its natural setting, providing first-hand information about the case and its context. Observations can provide data that might not be revealed in interviews or documents, such as non-verbal cues or contextual information.
Documents and artifacts
Documents and archival records provide a valuable source of data in case study research. They can include reports, letters, memos, meeting minutes, email correspondence, and various public and private documents related to the case.

These records can provide historical context, corroborate evidence from other sources, and offer insights into the case that might not be apparent from interviews or observations.
Physical artifacts refer to any physical evidence related to the case, such as tools, products, or physical environments. These artifacts can provide tangible insights into the case, complementing the data gathered from other sources.
Ensuring the quality of data collection
Determining the quality of data in case study research requires careful planning and execution. It's crucial to ensure that the data is reliable, accurate, and relevant to the research question. This involves selecting appropriate methods of collecting data, properly training interviewers or observers, and systematically recording and storing the data. It also includes considering ethical issues related to collecting and handling data, such as obtaining informed consent and ensuring the privacy and confidentiality of the participants.
Data analysis
Analyzing case study research involves making sense of the rich, detailed data to answer the research question. This process can be challenging due to the volume and complexity of case study data. However, a systematic and rigorous approach to analysis can ensure that the findings are credible and meaningful. This section outlines the main steps and considerations in analyzing data in case study research.
Organizing the data
The first step in the analysis is organizing the data. This involves sorting the data into manageable sections, often according to the data source or the theme. This step can also involve transcribing interviews, digitizing physical artifacts, or organizing observational data.
Categorizing and coding the data
Once the data is organized, the next step is to categorize or code the data. This involves identifying common themes, patterns, or concepts in the data and assigning codes to relevant data segments. Coding can be done manually or with the help of software tools, and in either case, qualitative analysis software can greatly facilitate the entire coding process. Coding helps to reduce the data to a set of themes or categories that can be more easily analyzed.
Identifying patterns and themes
After coding the data, the researcher looks for patterns or themes in the coded data. This involves comparing and contrasting the codes and looking for relationships or patterns among them. The identified patterns and themes should help answer the research question.
Interpreting the data
Once patterns and themes have been identified, the next step is to interpret these findings. This involves explaining what the patterns or themes mean in the context of the research question and the case. This interpretation should be grounded in the data, but it can also involve drawing on theoretical concepts or prior research.
Verification of the data
The last step in the analysis is verification. This involves checking the accuracy and consistency of the analysis process and confirming that the findings are supported by the data. This can involve re-checking the original data, checking the consistency of codes, or seeking feedback from research participants or peers.
Like any research method , case study research has its strengths and limitations. Researchers must be aware of these, as they can influence the design, conduct, and interpretation of the study.
Understanding the strengths and limitations of case study research can also guide researchers in deciding whether this approach is suitable for their research question . This section outlines some of the key strengths and limitations of case study research.
Benefits include the following:
- Rich, detailed data: One of the main strengths of case study research is that it can generate rich, detailed data about the case. This can provide a deep understanding of the case and its context, which can be valuable in exploring complex phenomena.
- Flexibility: Case study research is flexible in terms of design , data collection , and analysis . A sufficient degree of flexibility allows the researcher to adapt the study according to the case and the emerging findings.
- Real-world context: Case study research involves studying the case in its real-world context, which can provide valuable insights into the interplay between the case and its context.
- Multiple sources of evidence: Case study research often involves collecting data from multiple sources , which can enhance the robustness and validity of the findings.
On the other hand, researchers should consider the following limitations:
- Generalizability: A common criticism of case study research is that its findings might not be generalizable to other cases due to the specificity and uniqueness of each case.
- Time and resource intensive: Case study research can be time and resource intensive due to the depth of the investigation and the amount of collected data.
- Complexity of analysis: The rich, detailed data generated in case study research can make analyzing the data challenging.
- Subjectivity: Given the nature of case study research, there may be a higher degree of subjectivity in interpreting the data , so researchers need to reflect on this and transparently convey to audiences how the research was conducted.
Being aware of these strengths and limitations can help researchers design and conduct case study research effectively and interpret and report the findings appropriately.

Ready to analyze your data with ATLAS.ti?
See how our intuitive software can draw key insights from your data with a free trial today.
- Open access
- Published: 27 June 2011
The case study approach
- Sarah Crowe 1 ,
- Kathrin Cresswell 2 ,
- Ann Robertson 2 ,
- Guro Huby 3 ,
- Anthony Avery 1 &
- Aziz Sheikh 2
BMC Medical Research Methodology volume 11 , Article number: 100 ( 2011 ) Cite this article
778k Accesses
1039 Citations
37 Altmetric
Metrics details
The case study approach allows in-depth, multi-faceted explorations of complex issues in their real-life settings. The value of the case study approach is well recognised in the fields of business, law and policy, but somewhat less so in health services research. Based on our experiences of conducting several health-related case studies, we reflect on the different types of case study design, the specific research questions this approach can help answer, the data sources that tend to be used, and the particular advantages and disadvantages of employing this methodological approach. The paper concludes with key pointers to aid those designing and appraising proposals for conducting case study research, and a checklist to help readers assess the quality of case study reports.
Peer Review reports
Introduction
The case study approach is particularly useful to employ when there is a need to obtain an in-depth appreciation of an issue, event or phenomenon of interest, in its natural real-life context. Our aim in writing this piece is to provide insights into when to consider employing this approach and an overview of key methodological considerations in relation to the design, planning, analysis, interpretation and reporting of case studies.
The illustrative 'grand round', 'case report' and 'case series' have a long tradition in clinical practice and research. Presenting detailed critiques, typically of one or more patients, aims to provide insights into aspects of the clinical case and, in doing so, illustrate broader lessons that may be learnt. In research, the conceptually-related case study approach can be used, for example, to describe in detail a patient's episode of care, explore professional attitudes to and experiences of a new policy initiative or service development or more generally to 'investigate contemporary phenomena within its real-life context' [ 1 ]. Based on our experiences of conducting a range of case studies, we reflect on when to consider using this approach, discuss the key steps involved and illustrate, with examples, some of the practical challenges of attaining an in-depth understanding of a 'case' as an integrated whole. In keeping with previously published work, we acknowledge the importance of theory to underpin the design, selection, conduct and interpretation of case studies[ 2 ]. In so doing, we make passing reference to the different epistemological approaches used in case study research by key theoreticians and methodologists in this field of enquiry.
This paper is structured around the following main questions: What is a case study? What are case studies used for? How are case studies conducted? What are the potential pitfalls and how can these be avoided? We draw in particular on four of our own recently published examples of case studies (see Tables 1 , 2 , 3 and 4 ) and those of others to illustrate our discussion[ 3 – 7 ].
What is a case study?
A case study is a research approach that is used to generate an in-depth, multi-faceted understanding of a complex issue in its real-life context. It is an established research design that is used extensively in a wide variety of disciplines, particularly in the social sciences. A case study can be defined in a variety of ways (Table 5 ), the central tenet being the need to explore an event or phenomenon in depth and in its natural context. It is for this reason sometimes referred to as a "naturalistic" design; this is in contrast to an "experimental" design (such as a randomised controlled trial) in which the investigator seeks to exert control over and manipulate the variable(s) of interest.
Stake's work has been particularly influential in defining the case study approach to scientific enquiry. He has helpfully characterised three main types of case study: intrinsic , instrumental and collective [ 8 ]. An intrinsic case study is typically undertaken to learn about a unique phenomenon. The researcher should define the uniqueness of the phenomenon, which distinguishes it from all others. In contrast, the instrumental case study uses a particular case (some of which may be better than others) to gain a broader appreciation of an issue or phenomenon. The collective case study involves studying multiple cases simultaneously or sequentially in an attempt to generate a still broader appreciation of a particular issue.
These are however not necessarily mutually exclusive categories. In the first of our examples (Table 1 ), we undertook an intrinsic case study to investigate the issue of recruitment of minority ethnic people into the specific context of asthma research studies, but it developed into a instrumental case study through seeking to understand the issue of recruitment of these marginalised populations more generally, generating a number of the findings that are potentially transferable to other disease contexts[ 3 ]. In contrast, the other three examples (see Tables 2 , 3 and 4 ) employed collective case study designs to study the introduction of workforce reconfiguration in primary care, the implementation of electronic health records into hospitals, and to understand the ways in which healthcare students learn about patient safety considerations[ 4 – 6 ]. Although our study focusing on the introduction of General Practitioners with Specialist Interests (Table 2 ) was explicitly collective in design (four contrasting primary care organisations were studied), is was also instrumental in that this particular professional group was studied as an exemplar of the more general phenomenon of workforce redesign[ 4 ].
What are case studies used for?
According to Yin, case studies can be used to explain, describe or explore events or phenomena in the everyday contexts in which they occur[ 1 ]. These can, for example, help to understand and explain causal links and pathways resulting from a new policy initiative or service development (see Tables 2 and 3 , for example)[ 1 ]. In contrast to experimental designs, which seek to test a specific hypothesis through deliberately manipulating the environment (like, for example, in a randomised controlled trial giving a new drug to randomly selected individuals and then comparing outcomes with controls),[ 9 ] the case study approach lends itself well to capturing information on more explanatory ' how ', 'what' and ' why ' questions, such as ' how is the intervention being implemented and received on the ground?'. The case study approach can offer additional insights into what gaps exist in its delivery or why one implementation strategy might be chosen over another. This in turn can help develop or refine theory, as shown in our study of the teaching of patient safety in undergraduate curricula (Table 4 )[ 6 , 10 ]. Key questions to consider when selecting the most appropriate study design are whether it is desirable or indeed possible to undertake a formal experimental investigation in which individuals and/or organisations are allocated to an intervention or control arm? Or whether the wish is to obtain a more naturalistic understanding of an issue? The former is ideally studied using a controlled experimental design, whereas the latter is more appropriately studied using a case study design.
Case studies may be approached in different ways depending on the epistemological standpoint of the researcher, that is, whether they take a critical (questioning one's own and others' assumptions), interpretivist (trying to understand individual and shared social meanings) or positivist approach (orientating towards the criteria of natural sciences, such as focusing on generalisability considerations) (Table 6 ). Whilst such a schema can be conceptually helpful, it may be appropriate to draw on more than one approach in any case study, particularly in the context of conducting health services research. Doolin has, for example, noted that in the context of undertaking interpretative case studies, researchers can usefully draw on a critical, reflective perspective which seeks to take into account the wider social and political environment that has shaped the case[ 11 ].
How are case studies conducted?
Here, we focus on the main stages of research activity when planning and undertaking a case study; the crucial stages are: defining the case; selecting the case(s); collecting and analysing the data; interpreting data; and reporting the findings.
Defining the case
Carefully formulated research question(s), informed by the existing literature and a prior appreciation of the theoretical issues and setting(s), are all important in appropriately and succinctly defining the case[ 8 , 12 ]. Crucially, each case should have a pre-defined boundary which clarifies the nature and time period covered by the case study (i.e. its scope, beginning and end), the relevant social group, organisation or geographical area of interest to the investigator, the types of evidence to be collected, and the priorities for data collection and analysis (see Table 7 )[ 1 ]. A theory driven approach to defining the case may help generate knowledge that is potentially transferable to a range of clinical contexts and behaviours; using theory is also likely to result in a more informed appreciation of, for example, how and why interventions have succeeded or failed[ 13 ].
For example, in our evaluation of the introduction of electronic health records in English hospitals (Table 3 ), we defined our cases as the NHS Trusts that were receiving the new technology[ 5 ]. Our focus was on how the technology was being implemented. However, if the primary research interest had been on the social and organisational dimensions of implementation, we might have defined our case differently as a grouping of healthcare professionals (e.g. doctors and/or nurses). The precise beginning and end of the case may however prove difficult to define. Pursuing this same example, when does the process of implementation and adoption of an electronic health record system really begin or end? Such judgements will inevitably be influenced by a range of factors, including the research question, theory of interest, the scope and richness of the gathered data and the resources available to the research team.
Selecting the case(s)
The decision on how to select the case(s) to study is a very important one that merits some reflection. In an intrinsic case study, the case is selected on its own merits[ 8 ]. The case is selected not because it is representative of other cases, but because of its uniqueness, which is of genuine interest to the researchers. This was, for example, the case in our study of the recruitment of minority ethnic participants into asthma research (Table 1 ) as our earlier work had demonstrated the marginalisation of minority ethnic people with asthma, despite evidence of disproportionate asthma morbidity[ 14 , 15 ]. In another example of an intrinsic case study, Hellstrom et al.[ 16 ] studied an elderly married couple living with dementia to explore how dementia had impacted on their understanding of home, their everyday life and their relationships.
For an instrumental case study, selecting a "typical" case can work well[ 8 ]. In contrast to the intrinsic case study, the particular case which is chosen is of less importance than selecting a case that allows the researcher to investigate an issue or phenomenon. For example, in order to gain an understanding of doctors' responses to health policy initiatives, Som undertook an instrumental case study interviewing clinicians who had a range of responsibilities for clinical governance in one NHS acute hospital trust[ 17 ]. Sampling a "deviant" or "atypical" case may however prove even more informative, potentially enabling the researcher to identify causal processes, generate hypotheses and develop theory.
In collective or multiple case studies, a number of cases are carefully selected. This offers the advantage of allowing comparisons to be made across several cases and/or replication. Choosing a "typical" case may enable the findings to be generalised to theory (i.e. analytical generalisation) or to test theory by replicating the findings in a second or even a third case (i.e. replication logic)[ 1 ]. Yin suggests two or three literal replications (i.e. predicting similar results) if the theory is straightforward and five or more if the theory is more subtle. However, critics might argue that selecting 'cases' in this way is insufficiently reflexive and ill-suited to the complexities of contemporary healthcare organisations.
The selected case study site(s) should allow the research team access to the group of individuals, the organisation, the processes or whatever else constitutes the chosen unit of analysis for the study. Access is therefore a central consideration; the researcher needs to come to know the case study site(s) well and to work cooperatively with them. Selected cases need to be not only interesting but also hospitable to the inquiry [ 8 ] if they are to be informative and answer the research question(s). Case study sites may also be pre-selected for the researcher, with decisions being influenced by key stakeholders. For example, our selection of case study sites in the evaluation of the implementation and adoption of electronic health record systems (see Table 3 ) was heavily influenced by NHS Connecting for Health, the government agency that was responsible for overseeing the National Programme for Information Technology (NPfIT)[ 5 ]. This prominent stakeholder had already selected the NHS sites (through a competitive bidding process) to be early adopters of the electronic health record systems and had negotiated contracts that detailed the deployment timelines.
It is also important to consider in advance the likely burden and risks associated with participation for those who (or the site(s) which) comprise the case study. Of particular importance is the obligation for the researcher to think through the ethical implications of the study (e.g. the risk of inadvertently breaching anonymity or confidentiality) and to ensure that potential participants/participating sites are provided with sufficient information to make an informed choice about joining the study. The outcome of providing this information might be that the emotive burden associated with participation, or the organisational disruption associated with supporting the fieldwork, is considered so high that the individuals or sites decide against participation.
In our example of evaluating implementations of electronic health record systems, given the restricted number of early adopter sites available to us, we sought purposively to select a diverse range of implementation cases among those that were available[ 5 ]. We chose a mixture of teaching, non-teaching and Foundation Trust hospitals, and examples of each of the three electronic health record systems procured centrally by the NPfIT. At one recruited site, it quickly became apparent that access was problematic because of competing demands on that organisation. Recognising the importance of full access and co-operative working for generating rich data, the research team decided not to pursue work at that site and instead to focus on other recruited sites.
Collecting the data
In order to develop a thorough understanding of the case, the case study approach usually involves the collection of multiple sources of evidence, using a range of quantitative (e.g. questionnaires, audits and analysis of routinely collected healthcare data) and more commonly qualitative techniques (e.g. interviews, focus groups and observations). The use of multiple sources of data (data triangulation) has been advocated as a way of increasing the internal validity of a study (i.e. the extent to which the method is appropriate to answer the research question)[ 8 , 18 – 21 ]. An underlying assumption is that data collected in different ways should lead to similar conclusions, and approaching the same issue from different angles can help develop a holistic picture of the phenomenon (Table 2 )[ 4 ].
Brazier and colleagues used a mixed-methods case study approach to investigate the impact of a cancer care programme[ 22 ]. Here, quantitative measures were collected with questionnaires before, and five months after, the start of the intervention which did not yield any statistically significant results. Qualitative interviews with patients however helped provide an insight into potentially beneficial process-related aspects of the programme, such as greater, perceived patient involvement in care. The authors reported how this case study approach provided a number of contextual factors likely to influence the effectiveness of the intervention and which were not likely to have been obtained from quantitative methods alone.
In collective or multiple case studies, data collection needs to be flexible enough to allow a detailed description of each individual case to be developed (e.g. the nature of different cancer care programmes), before considering the emerging similarities and differences in cross-case comparisons (e.g. to explore why one programme is more effective than another). It is important that data sources from different cases are, where possible, broadly comparable for this purpose even though they may vary in nature and depth.
Analysing, interpreting and reporting case studies
Making sense and offering a coherent interpretation of the typically disparate sources of data (whether qualitative alone or together with quantitative) is far from straightforward. Repeated reviewing and sorting of the voluminous and detail-rich data are integral to the process of analysis. In collective case studies, it is helpful to analyse data relating to the individual component cases first, before making comparisons across cases. Attention needs to be paid to variations within each case and, where relevant, the relationship between different causes, effects and outcomes[ 23 ]. Data will need to be organised and coded to allow the key issues, both derived from the literature and emerging from the dataset, to be easily retrieved at a later stage. An initial coding frame can help capture these issues and can be applied systematically to the whole dataset with the aid of a qualitative data analysis software package.
The Framework approach is a practical approach, comprising of five stages (familiarisation; identifying a thematic framework; indexing; charting; mapping and interpretation) , to managing and analysing large datasets particularly if time is limited, as was the case in our study of recruitment of South Asians into asthma research (Table 1 )[ 3 , 24 ]. Theoretical frameworks may also play an important role in integrating different sources of data and examining emerging themes. For example, we drew on a socio-technical framework to help explain the connections between different elements - technology; people; and the organisational settings within which they worked - in our study of the introduction of electronic health record systems (Table 3 )[ 5 ]. Our study of patient safety in undergraduate curricula drew on an evaluation-based approach to design and analysis, which emphasised the importance of the academic, organisational and practice contexts through which students learn (Table 4 )[ 6 ].
Case study findings can have implications both for theory development and theory testing. They may establish, strengthen or weaken historical explanations of a case and, in certain circumstances, allow theoretical (as opposed to statistical) generalisation beyond the particular cases studied[ 12 ]. These theoretical lenses should not, however, constitute a strait-jacket and the cases should not be "forced to fit" the particular theoretical framework that is being employed.
When reporting findings, it is important to provide the reader with enough contextual information to understand the processes that were followed and how the conclusions were reached. In a collective case study, researchers may choose to present the findings from individual cases separately before amalgamating across cases. Care must be taken to ensure the anonymity of both case sites and individual participants (if agreed in advance) by allocating appropriate codes or withholding descriptors. In the example given in Table 3 , we decided against providing detailed information on the NHS sites and individual participants in order to avoid the risk of inadvertent disclosure of identities[ 5 , 25 ].
What are the potential pitfalls and how can these be avoided?
The case study approach is, as with all research, not without its limitations. When investigating the formal and informal ways undergraduate students learn about patient safety (Table 4 ), for example, we rapidly accumulated a large quantity of data. The volume of data, together with the time restrictions in place, impacted on the depth of analysis that was possible within the available resources. This highlights a more general point of the importance of avoiding the temptation to collect as much data as possible; adequate time also needs to be set aside for data analysis and interpretation of what are often highly complex datasets.
Case study research has sometimes been criticised for lacking scientific rigour and providing little basis for generalisation (i.e. producing findings that may be transferable to other settings)[ 1 ]. There are several ways to address these concerns, including: the use of theoretical sampling (i.e. drawing on a particular conceptual framework); respondent validation (i.e. participants checking emerging findings and the researcher's interpretation, and providing an opinion as to whether they feel these are accurate); and transparency throughout the research process (see Table 8 )[ 8 , 18 – 21 , 23 , 26 ]. Transparency can be achieved by describing in detail the steps involved in case selection, data collection, the reasons for the particular methods chosen, and the researcher's background and level of involvement (i.e. being explicit about how the researcher has influenced data collection and interpretation). Seeking potential, alternative explanations, and being explicit about how interpretations and conclusions were reached, help readers to judge the trustworthiness of the case study report. Stake provides a critique checklist for a case study report (Table 9 )[ 8 ].
Conclusions
The case study approach allows, amongst other things, critical events, interventions, policy developments and programme-based service reforms to be studied in detail in a real-life context. It should therefore be considered when an experimental design is either inappropriate to answer the research questions posed or impossible to undertake. Considering the frequency with which implementations of innovations are now taking place in healthcare settings and how well the case study approach lends itself to in-depth, complex health service research, we believe this approach should be more widely considered by researchers. Though inherently challenging, the research case study can, if carefully conceptualised and thoughtfully undertaken and reported, yield powerful insights into many important aspects of health and healthcare delivery.
Yin RK: Case study research, design and method. 2009, London: Sage Publications Ltd., 4
Google Scholar
Keen J, Packwood T: Qualitative research; case study evaluation. BMJ. 1995, 311: 444-446.
Article CAS PubMed PubMed Central Google Scholar
Sheikh A, Halani L, Bhopal R, Netuveli G, Partridge M, Car J, et al: Facilitating the Recruitment of Minority Ethnic People into Research: Qualitative Case Study of South Asians and Asthma. PLoS Med. 2009, 6 (10): 1-11.
Article Google Scholar
Pinnock H, Huby G, Powell A, Kielmann T, Price D, Williams S, et al: The process of planning, development and implementation of a General Practitioner with a Special Interest service in Primary Care Organisations in England and Wales: a comparative prospective case study. Report for the National Co-ordinating Centre for NHS Service Delivery and Organisation R&D (NCCSDO). 2008, [ http://www.sdo.nihr.ac.uk/files/project/99-final-report.pdf ]
Robertson A, Cresswell K, Takian A, Petrakaki D, Crowe S, Cornford T, et al: Prospective evaluation of the implementation and adoption of NHS Connecting for Health's national electronic health record in secondary care in England: interim findings. BMJ. 2010, 41: c4564-
Pearson P, Steven A, Howe A, Sheikh A, Ashcroft D, Smith P, the Patient Safety Education Study Group: Learning about patient safety: organisational context and culture in the education of healthcare professionals. J Health Serv Res Policy. 2010, 15: 4-10. 10.1258/jhsrp.2009.009052.
Article PubMed Google Scholar
van Harten WH, Casparie TF, Fisscher OA: The evaluation of the introduction of a quality management system: a process-oriented case study in a large rehabilitation hospital. Health Policy. 2002, 60 (1): 17-37. 10.1016/S0168-8510(01)00187-7.
Stake RE: The art of case study research. 1995, London: Sage Publications Ltd.
Sheikh A, Smeeth L, Ashcroft R: Randomised controlled trials in primary care: scope and application. Br J Gen Pract. 2002, 52 (482): 746-51.
PubMed PubMed Central Google Scholar
King G, Keohane R, Verba S: Designing Social Inquiry. 1996, Princeton: Princeton University Press
Doolin B: Information technology as disciplinary technology: being critical in interpretative research on information systems. Journal of Information Technology. 1998, 13: 301-311. 10.1057/jit.1998.8.
George AL, Bennett A: Case studies and theory development in the social sciences. 2005, Cambridge, MA: MIT Press
Eccles M, the Improved Clinical Effectiveness through Behavioural Research Group (ICEBeRG): Designing theoretically-informed implementation interventions. Implementation Science. 2006, 1: 1-8. 10.1186/1748-5908-1-1.
Article PubMed Central Google Scholar
Netuveli G, Hurwitz B, Levy M, Fletcher M, Barnes G, Durham SR, Sheikh A: Ethnic variations in UK asthma frequency, morbidity, and health-service use: a systematic review and meta-analysis. Lancet. 2005, 365 (9456): 312-7.
Sheikh A, Panesar SS, Lasserson T, Netuveli G: Recruitment of ethnic minorities to asthma studies. Thorax. 2004, 59 (7): 634-
CAS PubMed PubMed Central Google Scholar
Hellström I, Nolan M, Lundh U: 'We do things together': A case study of 'couplehood' in dementia. Dementia. 2005, 4: 7-22. 10.1177/1471301205049188.
Som CV: Nothing seems to have changed, nothing seems to be changing and perhaps nothing will change in the NHS: doctors' response to clinical governance. International Journal of Public Sector Management. 2005, 18: 463-477. 10.1108/09513550510608903.
Lincoln Y, Guba E: Naturalistic inquiry. 1985, Newbury Park: Sage Publications
Barbour RS: Checklists for improving rigour in qualitative research: a case of the tail wagging the dog?. BMJ. 2001, 322: 1115-1117. 10.1136/bmj.322.7294.1115.
Mays N, Pope C: Qualitative research in health care: Assessing quality in qualitative research. BMJ. 2000, 320: 50-52. 10.1136/bmj.320.7226.50.
Mason J: Qualitative researching. 2002, London: Sage
Brazier A, Cooke K, Moravan V: Using Mixed Methods for Evaluating an Integrative Approach to Cancer Care: A Case Study. Integr Cancer Ther. 2008, 7: 5-17. 10.1177/1534735407313395.
Miles MB, Huberman M: Qualitative data analysis: an expanded sourcebook. 1994, CA: Sage Publications Inc., 2
Pope C, Ziebland S, Mays N: Analysing qualitative data. Qualitative research in health care. BMJ. 2000, 320: 114-116. 10.1136/bmj.320.7227.114.
Cresswell KM, Worth A, Sheikh A: Actor-Network Theory and its role in understanding the implementation of information technology developments in healthcare. BMC Med Inform Decis Mak. 2010, 10 (1): 67-10.1186/1472-6947-10-67.
Article PubMed PubMed Central Google Scholar
Malterud K: Qualitative research: standards, challenges, and guidelines. Lancet. 2001, 358: 483-488. 10.1016/S0140-6736(01)05627-6.
Article CAS PubMed Google Scholar
Yin R: Case study research: design and methods. 1994, Thousand Oaks, CA: Sage Publishing, 2
Yin R: Enhancing the quality of case studies in health services research. Health Serv Res. 1999, 34: 1209-1224.
Green J, Thorogood N: Qualitative methods for health research. 2009, Los Angeles: Sage, 2
Howcroft D, Trauth E: Handbook of Critical Information Systems Research, Theory and Application. 2005, Cheltenham, UK: Northampton, MA, USA: Edward Elgar
Book Google Scholar
Blakie N: Approaches to Social Enquiry. 1993, Cambridge: Polity Press
Doolin B: Power and resistance in the implementation of a medical management information system. Info Systems J. 2004, 14: 343-362. 10.1111/j.1365-2575.2004.00176.x.
Bloomfield BP, Best A: Management consultants: systems development, power and the translation of problems. Sociological Review. 1992, 40: 533-560.
Shanks G, Parr A: Positivist, single case study research in information systems: A critical analysis. Proceedings of the European Conference on Information Systems. 2003, Naples
Pre-publication history
The pre-publication history for this paper can be accessed here: http://www.biomedcentral.com/1471-2288/11/100/prepub
Download references
Acknowledgements
We are grateful to the participants and colleagues who contributed to the individual case studies that we have drawn on. This work received no direct funding, but it has been informed by projects funded by Asthma UK, the NHS Service Delivery Organisation, NHS Connecting for Health Evaluation Programme, and Patient Safety Research Portfolio. We would also like to thank the expert reviewers for their insightful and constructive feedback. Our thanks are also due to Dr. Allison Worth who commented on an earlier draft of this manuscript.
Author information
Authors and affiliations.
Division of Primary Care, The University of Nottingham, Nottingham, UK
Sarah Crowe & Anthony Avery
Centre for Population Health Sciences, The University of Edinburgh, Edinburgh, UK
Kathrin Cresswell, Ann Robertson & Aziz Sheikh
School of Health in Social Science, The University of Edinburgh, Edinburgh, UK
You can also search for this author in PubMed Google Scholar
Corresponding author
Correspondence to Sarah Crowe .
Additional information
Competing interests.
The authors declare that they have no competing interests.
Authors' contributions
AS conceived this article. SC, KC and AR wrote this paper with GH, AA and AS all commenting on various drafts. SC and AS are guarantors.
Rights and permissions
This article is published under license to BioMed Central Ltd. This is an Open Access article distributed under the terms of the Creative Commons Attribution License ( http://creativecommons.org/licenses/by/2.0 ), which permits unrestricted use, distribution, and reproduction in any medium, provided the original work is properly cited.
Reprints and permissions
About this article
Cite this article.
Crowe, S., Cresswell, K., Robertson, A. et al. The case study approach. BMC Med Res Methodol 11 , 100 (2011). https://doi.org/10.1186/1471-2288-11-100
Download citation
Received : 29 November 2010
Accepted : 27 June 2011
Published : 27 June 2011
DOI : https://doi.org/10.1186/1471-2288-11-100
Share this article
Anyone you share the following link with will be able to read this content:
Sorry, a shareable link is not currently available for this article.
Provided by the Springer Nature SharedIt content-sharing initiative
- Case Study Approach
- Electronic Health Record System
- Case Study Design
- Case Study Site
- Case Study Report
BMC Medical Research Methodology
ISSN: 1471-2288
- General enquiries: [email protected]

Research Writing and Analysis
- NVivo Group and Study Sessions
- SPSS This link opens in a new window
- Statistical Analysis Group sessions
- Using Qualtrics
- Dissertation and Data Analysis Group Sessions
- Defense Schedule - Commons Calendar This link opens in a new window
- Research Process Flow Chart
- Research Alignment Chapter 1 This link opens in a new window
- Step 1: Seek Out Evidence
- Step 2: Explain
- Step 3: The Big Picture
- Step 4: Own It
- Step 5: Illustrate
- Annotated Bibliography
- Literature Review This link opens in a new window
- Systematic Reviews & Meta-Analyses
- How to Synthesize and Analyze
- Synthesis and Analysis Practice
- Synthesis and Analysis Group Sessions
- Problem Statement
- Purpose Statement
- Conceptual Framework
- Theoretical Framework
- Quantitative Research Questions
- Qualitative Research Questions
- Trustworthiness of Qualitative Data
- Analysis and Coding Example- Qualitative Data
- Thematic Data Analysis in Qualitative Design
- Dissertation to Journal Article This link opens in a new window
- International Journal of Online Graduate Education (IJOGE) This link opens in a new window
- Journal of Research in Innovative Teaching & Learning (JRIT&L) This link opens in a new window
Writing a Case Study

What is a case study?

A Case study is:
- An in-depth research design that primarily uses a qualitative methodology but sometimes includes quantitative methodology.
- Used to examine an identifiable problem confirmed through research.
- Used to investigate an individual, group of people, organization, or event.
- Used to mostly answer "how" and "why" questions.
What are the different types of case studies?

Note: These are the primary case studies. As you continue to research and learn
about case studies you will begin to find a robust list of different types.
Who are your case study participants?

What is triangulation ?
Validity and credibility are an essential part of the case study. Therefore, the researcher should include triangulation to ensure trustworthiness while accurately reflecting what the researcher seeks to investigate.

How to write a Case Study?
When developing a case study, there are different ways you could present the information, but remember to include the five parts for your case study.

Was this resource helpful?
- << Previous: Thematic Data Analysis in Qualitative Design
- Next: Journal Article Reporting Standards (JARS) >>
- Last Updated: May 3, 2024 8:12 AM
- URL: https://resources.nu.edu/researchtools

To read this content please select one of the options below:
Please note you do not have access to teaching notes, a systematic qualitative case study: questions, data collection, nvivo analysis and saturation.
Qualitative Research in Organizations and Management
ISSN : 1746-5648
Article publication date: 20 August 2020
Issue publication date: 23 February 2021
The study aims to explore the case study method with the formation of questions, data collection procedures and analysis, followed by how and on which position the saturation is achieved in developing a centralized Shariah governance framework for Islamic banks in Bangladesh.
Design/methodology/approach
Using purposive and snowball sampling procedures, data have been collected from 17 respondents who are working in the central bank and Islamic banks of Bangladesh through face-to-face and semi-structured interviews.
The study claims that researchers can form the research questions by using “what” question mark in qualitative research. Besides, the qualitative research and case study could explore the answers of “what” questions along with the “why” and “how” more broadly, descriptively and extensively about a phenomenon. Similarly, saturation can be considered attaining the ultimate point of data collection by the researchers without adding anything in the databank. Overall, this study proposes three stages of saturation: First, information redundancy. Second, referring the respondents (already considered in the study) without knowing anything about the data collection and their responses. Third, through the NVivo open coding process due to the decrease of reference or quotes in a certain position or in the saturation position as a result of fewer outcomes or insufficient information. The saturation is thus achieved in the diversified positions, i.e. three respondents for regulatory, nine for Shariah scholars and officers and five for the experts concerning the responses and respondents.
Research limitations/implications
The study has potential implications on the qualitative research method, including the case study, saturation process and points, NVivo analysis and qualitative questions formation.
Originality/value
This research defines a case study with the inclusion of “what” and illustrates the saturation process in diverse positions. The qualitative research questions can also be formed with “what” in addition “why” and “how”.
- Qualitative research
Acknowledgements
The author would like to thank both Editors, Associate Editor Dr. Amon Barros and anonymous reviewers for their valuable time, constructive comments and suggestions for the improvement of the manuscript. A special thanks to Dr. Mohd Mursyid Arshad, Senior Lecturer at Faculty of Educational Studies, Universiti Putra Malaysia, Malaysia for his suggestions and unconditional help in the NVivo data analysis process of this research project. The study does not receive any specific fund or research grant.
Alam, M.K. (2021), "A systematic qualitative case study: questions, data collection, NVivo analysis and saturation", Qualitative Research in Organizations and Management , Vol. 16 No. 1, pp. 1-31. https://doi.org/10.1108/QROM-09-2019-1825
Emerald Publishing Limited
Copyright © 2020, Emerald Publishing Limited
Related articles
We’re listening — tell us what you think, something didn’t work….
Report bugs here
All feedback is valuable
Please share your general feedback
Join us on our journey
Platform update page.
Visit emeraldpublishing.com/platformupdate to discover the latest news and updates
Questions & More Information
Answers to the most commonly asked questions here
Thank you for visiting nature.com. You are using a browser version with limited support for CSS. To obtain the best experience, we recommend you use a more up to date browser (or turn off compatibility mode in Internet Explorer). In the meantime, to ensure continued support, we are displaying the site without styles and JavaScript.
- View all journals
- My Account Login
- Explore content
- About the journal
- Publish with us
- Sign up for alerts
- Data Descriptor
- Open access
- Published: 03 May 2024
A dataset for measuring the impact of research data and their curation
- Libby Hemphill ORCID: orcid.org/0000-0002-3793-7281 1 , 2 ,
- Andrea Thomer 3 ,
- Sara Lafia 1 ,
- Lizhou Fan 2 ,
- David Bleckley ORCID: orcid.org/0000-0001-7715-4348 1 &
- Elizabeth Moss 1
Scientific Data volume 11 , Article number: 442 ( 2024 ) Cite this article
583 Accesses
8 Altmetric
Metrics details
- Research data
- Social sciences
Science funders, publishers, and data archives make decisions about how to responsibly allocate resources to maximize the reuse potential of research data. This paper introduces a dataset developed to measure the impact of archival and data curation decisions on data reuse. The dataset describes 10,605 social science research datasets, their curation histories, and reuse contexts in 94,755 publications that cover 59 years from 1963 to 2022. The dataset was constructed from study-level metadata, citing publications, and curation records available through the Inter-university Consortium for Political and Social Research (ICPSR) at the University of Michigan. The dataset includes information about study-level attributes (e.g., PIs, funders, subject terms); usage statistics (e.g., downloads, citations); archiving decisions (e.g., curation activities, data transformations); and bibliometric attributes (e.g., journals, authors) for citing publications. This dataset provides information on factors that contribute to long-term data reuse, which can inform the design of effective evidence-based recommendations to support high-impact research data curation decisions.
Similar content being viewed by others
SciSciNet: A large-scale open data lake for the science of science research
Data, measurement and empirical methods in the science of science

Interdisciplinarity revisited: evidence for research impact and dynamism
Background & summary.
Recent policy changes in funding agencies and academic journals have increased data sharing among researchers and between researchers and the public. Data sharing advances science and provides the transparency necessary for evaluating, replicating, and verifying results. However, many data-sharing policies do not explain what constitutes an appropriate dataset for archiving or how to determine the value of datasets to secondary users 1 , 2 , 3 . Questions about how to allocate data-sharing resources efficiently and responsibly have gone unanswered 4 , 5 , 6 . For instance, data-sharing policies recognize that not all data should be curated and preserved, but they do not articulate metrics or guidelines for determining what data are most worthy of investment.
Despite the potential for innovation and advancement that data sharing holds, the best strategies to prioritize datasets for preparation and archiving are often unclear. Some datasets are likely to have more downstream potential than others, and data curation policies and workflows should prioritize high-value data instead of being one-size-fits-all. Though prior research in library and information science has shown that the “analytic potential” of a dataset is key to its reuse value 7 , work is needed to implement conceptual data reuse frameworks 8 , 9 , 10 , 11 , 12 , 13 , 14 . In addition, publishers and data archives need guidance to develop metrics and evaluation strategies to assess the impact of datasets.
Several existing resources have been compiled to study the relationship between the reuse of scholarly products, such as datasets (Table 1 ); however, none of these resources include explicit information on how curation processes are applied to data to increase their value, maximize their accessibility, and ensure their long-term preservation. The CCex (Curation Costs Exchange) provides models of curation services along with cost-related datasets shared by contributors but does not make explicit connections between them or include reuse information 15 . Analyses on platforms such as DataCite 16 have focused on metadata completeness and record usage, but have not included related curation-level information. Analyses of GenBank 17 and FigShare 18 , 19 citation networks do not include curation information. Related studies of Github repository reuse 20 and Softcite software citation 21 reveal significant factors that impact the reuse of secondary research products but do not focus on research data. RD-Switchboard 22 and DSKG 23 are scholarly knowledge graphs linking research data to articles, patents, and grants, but largely omit social science research data and do not include curation-level factors. To our knowledge, other studies of curation work in organizations similar to ICPSR – such as GESIS 24 , Dataverse 25 , and DANS 26 – have not made their underlying data available for analysis.
This paper describes a dataset 27 compiled for the MICA project (Measuring the Impact of Curation Actions) led by investigators at ICPSR, a large social science data archive at the University of Michigan. The dataset was originally developed to study the impacts of data curation and archiving on data reuse. The MICA dataset has supported several previous publications investigating the intensity of data curation actions 28 , the relationship between data curation actions and data reuse 29 , and the structures of research communities in a data citation network 30 . Collectively, these studies help explain the return on various types of curatorial investments. The dataset that we introduce in this paper, which we refer to as the MICA dataset, has the potential to address research questions in the areas of science (e.g., knowledge production), library and information science (e.g., scholarly communication), and data archiving (e.g., reproducible workflows).
We constructed the MICA dataset 27 using records available at ICPSR, a large social science data archive at the University of Michigan. Data set creation involved: collecting and enriching metadata for articles indexed in the ICPSR Bibliography of Data-related Literature against the Dimensions AI bibliometric database; gathering usage statistics for studies from ICPSR’s administrative database; processing data curation work logs from ICPSR’s project tracking platform, Jira; and linking data in social science studies and series to citing analysis papers (Fig. 1 ).
Steps to prepare MICA dataset for analysis - external sources are red, primary internal sources are blue, and internal linked sources are green.
Enrich paper metadata
The ICPSR Bibliography of Data-related Literature is a growing database of literature in which data from ICPSR studies have been used. Its creation was funded by the National Science Foundation (Award 9977984), and for the past 20 years it has been supported by ICPSR membership and multiple US federally-funded and foundation-funded topical archives at ICPSR. The Bibliography was originally launched in the year 2000 to aid in data discovery by providing a searchable database linking publications to the study data used in them. The Bibliography collects the universe of output based on the data shared in each study through, which is made available through each ICPSR study’s webpage. The Bibliography contains both peer-reviewed and grey literature, which provides evidence for measuring the impact of research data. For an item to be included in the ICPSR Bibliography, it must contain an analysis of data archived by ICPSR or contain a discussion or critique of the data collection process, study design, or methodology 31 . The Bibliography is manually curated by a team of librarians and information specialists at ICPSR who enter and validate entries. Some publications are supplied to the Bibliography by data depositors, and some citations are submitted to the Bibliography by authors who abide by ICPSR’s terms of use requiring them to submit citations to works in which they analyzed data retrieved from ICPSR. Most of the Bibliography is populated by Bibliography team members, who create custom queries for ICPSR studies performed across numerous sources, including Google Scholar, ProQuest, SSRN, and others. Each record in the Bibliography is one publication that has used one or more ICPSR studies. The version we used was captured on 2021-11-16 and included 94,755 publications.
To expand the coverage of the ICPSR Bibliography, we searched exhaustively for all ICPSR study names, unique numbers assigned to ICPSR studies, and DOIs 32 using a full-text index available through the Dimensions AI database 33 . We accessed Dimensions through a license agreement with the University of Michigan. ICPSR Bibliography librarians and information specialists manually reviewed and validated new entries that matched one or more search criteria. We then used Dimensions to gather enriched metadata and full-text links for items in the Bibliography with DOIs. We matched 43% of the items in the Bibliography to enriched Dimensions metadata including abstracts, field of research codes, concepts, and authors’ institutional information; we also obtained links to full text for 16% of Bibliography items. Based on licensing agreements, we included Dimensions identifiers and links to full text so that users with valid publisher and database access can construct an enriched publication dataset.

Gather study usage data
ICPSR maintains a relational administrative database, DBInfo, that organizes study-level metadata and information on data reuse across separate tables. Studies at ICPSR consist of one or more files collected at a single time or for a single purpose; studies in which the same variables are observed over time are grouped into series. Each study at ICPSR is assigned a DOI, and its metadata are stored in DBInfo. Study metadata follows the Data Documentation Initiative (DDI) Codebook 2.5 standard. DDI elements included in our dataset are title, ICPSR study identification number, DOI, authoring entities, description (abstract), funding agencies, subject terms assigned to the study during curation, and geographic coverage. We also created variables based on DDI elements: total variable count, the presence of survey question text in the metadata, the number of author entities, and whether an author entity was an institution. We gathered metadata for ICPSR’s 10,605 unrestricted public-use studies available as of 2021-11-16 ( https://www.icpsr.umich.edu/web/pages/membership/or/metadata/oai.html ).
To link study usage data with study-level metadata records, we joined study metadata from DBinfo on study usage information, which included total study downloads (data and documentation), individual data file downloads, and cumulative citations from the ICPSR Bibliography. We also gathered descriptive metadata for each study and its variables, which allowed us to summarize and append recoded fields onto the study-level metadata such as curation level, number and type of principle investigators, total variable count, and binary variables indicating whether the study data were made available for online analysis, whether survey question text was made searchable online, and whether the study variables were indexed for search. These characteristics describe aspects of the discoverability of the data to compare with other characteristics of the study. We used the study and series numbers included in the ICPSR Bibliography as unique identifiers to link papers to metadata and analyze the community structure of dataset co-citations in the ICPSR Bibliography 32 .
Process curation work logs
Researchers deposit data at ICPSR for curation and long-term preservation. Between 2016 and 2020, more than 3,000 research studies were deposited with ICPSR. Since 2017, ICPSR has organized curation work into a central unit that provides varied levels of curation that vary in the intensity and complexity of data enhancement that they provide. While the levels of curation are standardized as to effort (level one = less effort, level three = most effort), the specific curatorial actions undertaken for each dataset vary. The specific curation actions are captured in Jira, a work tracking program, which data curators at ICPSR use to collaborate and communicate their progress through tickets. We obtained access to a corpus of 669 completed Jira tickets corresponding to the curation of 566 unique studies between February 2017 and December 2019 28 .
To process the tickets, we focused only on their work log portions, which contained free text descriptions of work that data curators had performed on a deposited study, along with the curators’ identifiers, and timestamps. To protect the confidentiality of the data curators and the processing steps they performed, we collaborated with ICPSR’s curation unit to propose a classification scheme, which we used to train a Naive Bayes classifier and label curation actions in each work log sentence. The eight curation action labels we proposed 28 were: (1) initial review and planning, (2) data transformation, (3) metadata, (4) documentation, (5) quality checks, (6) communication, (7) other, and (8) non-curation work. We note that these categories of curation work are very specific to the curatorial processes and types of data stored at ICPSR, and may not match the curation activities at other repositories. After applying the classifier to the work log sentences, we obtained summary-level curation actions for a subset of all ICPSR studies (5%), along with the total number of hours spent on data curation for each study, and the proportion of time associated with each action during curation.
Data Records
The MICA dataset 27 connects records for each of ICPSR’s archived research studies to the research publications that use them and related curation activities available for a subset of studies (Fig. 2 ). Each of the three tables published in the dataset is available as a study archived at ICPSR. The data tables are distributed as statistical files available for use in SAS, SPSS, Stata, and R as well as delimited and ASCII text files. The dataset is organized around studies and papers as primary entities. The studies table lists ICPSR studies, their metadata attributes, and usage information; the papers table was constructed using the ICPSR Bibliography and Dimensions database; and the curation logs table summarizes the data curation steps performed on a subset of ICPSR studies.
Studies (“ICPSR_STUDIES”): 10,605 social science research datasets available through ICPSR up to 2021-11-16 with variables for ICPSR study number, digital object identifier, study name, series number, series title, authoring entities, full-text description, release date, funding agency, geographic coverage, subject terms, topical archive, curation level, single principal investigator (PI), institutional PI, the total number of PIs, total variables in data files, question text availability, study variable indexing, level of restriction, total unique users downloading study data files and codebooks, total unique users downloading data only, and total unique papers citing data through November 2021. Studies map to the papers and curation logs table through ICPSR study numbers as “STUDY”. However, not every study in this table will have records in the papers and curation logs tables.
Papers (“ICPSR_PAPERS”): 94,755 publications collected from 2000-08-11 to 2021-11-16 in the ICPSR Bibliography and enriched with metadata from the Dimensions database with variables for paper number, identifier, title, authors, publication venue, item type, publication date, input date, ICPSR series numbers used in the paper, ICPSR study numbers used in the paper, the Dimension identifier, and the Dimensions link to the publication’s full text. Papers map to the studies table through ICPSR study numbers in the “STUDY_NUMS” field. Each record represents a single publication, and because a researcher can use multiple datasets when creating a publication, each record may list multiple studies or series.
Curation logs (“ICPSR_CURATION_LOGS”): 649 curation logs for 563 ICPSR studies (although most studies in the subset had one curation log, some studies were associated with multiple logs, with a maximum of 10) curated between February 2017 and December 2019 with variables for study number, action labels assigned to work description sentences using a classifier trained on ICPSR curation logs, hours of work associated with a single log entry, and total hours of work logged for the curation ticket. Curation logs map to the study and paper tables through ICPSR study numbers as “STUDY”. Each record represents a single logged action, and future users may wish to aggregate actions to the study level before joining tables.
Entity-relation diagram.
Technical Validation
We report on the reliability of the dataset’s metadata in the following subsections. To support future reuse of the dataset, curation services provided through ICPSR improved data quality by checking for missing values, adding variable labels, and creating a codebook.
All 10,605 studies available through ICPSR have a DOI and a full-text description summarizing what the study is about, the purpose of the study, the main topics covered, and the questions the PIs attempted to answer when they conducted the study. Personal names (i.e., principal investigators) and organizational names (i.e., funding agencies) are standardized against an authority list maintained by ICPSR; geographic names and subject terms are also standardized and hierarchically indexed in the ICPSR Thesaurus 34 . Many of ICPSR’s studies (63%) are in a series and are distributed through the ICPSR General Archive (56%), a non-topical archive that accepts any social or behavioral science data. While study data have been available through ICPSR since 1962, the earliest digital release date recorded for a study was 1984-03-18, when ICPSR’s database was first employed, and the most recent date is 2021-10-28 when the dataset was collected.
Curation level information was recorded starting in 2017 and is available for 1,125 studies (11%); approximately 80% of studies with assigned curation levels received curation services, equally distributed between Levels 1 (least intensive), 2 (moderately intensive), and 3 (most intensive) (Fig. 3 ). Detailed descriptions of ICPSR’s curation levels are available online 35 . Additional metadata are available for a subset of 421 studies (4%), including information about whether the study has a single PI, an institutional PI, the total number of PIs involved, total variables recorded is available for online analysis, has searchable question text, has variables that are indexed for search, contains one or more restricted files, and whether the study is completely restricted. We provided additional metadata for this subset of ICPSR studies because they were released within the past five years and detailed curation and usage information were available for them. Usage statistics including total downloads and data file downloads are available for this subset of studies as well; citation statistics are available for 8,030 studies (76%). Most ICPSR studies have fewer than 500 users, as indicated by total downloads, or citations (Fig. 4 ).
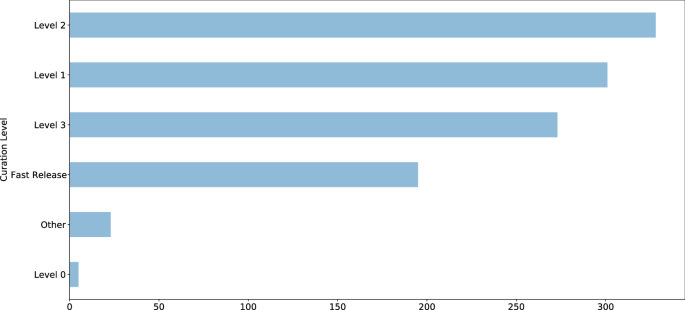
ICPSR study curation levels.
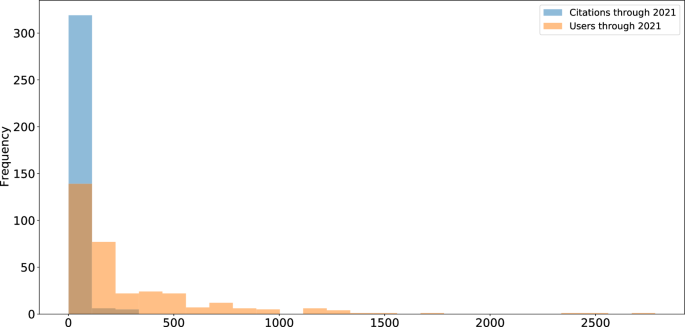
ICPSR study usage.
A subset of 43,102 publications (45%) available in the ICPSR Bibliography had a DOI. Author metadata were entered as free text, meaning that variations may exist and require additional normalization and pre-processing prior to analysis. While author information is standardized for each publication, individual names may appear in different sort orders (e.g., “Earls, Felton J.” and “Stephen W. Raudenbush”). Most of the items in the ICPSR Bibliography as of 2021-11-16 were journal articles (59%), reports (14%), conference presentations (9%), or theses (8%) (Fig. 5 ). The number of publications collected in the Bibliography has increased each decade since the inception of ICPSR in 1962 (Fig. 6 ). Most ICPSR studies (76%) have one or more citations in a publication.
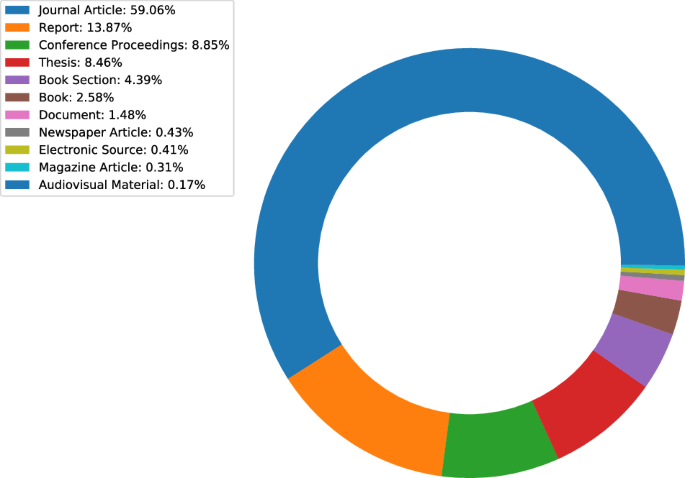
ICPSR Bibliography citation types.
ICPSR citations by decade.
Usage Notes
The dataset consists of three tables that can be joined using the “STUDY” key as shown in Fig. 2 . The “ICPSR_PAPERS” table contains one row per paper with one or more cited studies in the “STUDY_NUMS” column. We manipulated and analyzed the tables as CSV files with the Pandas library 36 in Python and the Tidyverse packages 37 in R.
The present MICA dataset can be used independently to study the relationship between curation decisions and data reuse. Evidence of reuse for specific studies is available in several forms: usage information, including downloads and citation counts; and citation contexts within papers that cite data. Analysis may also be performed on the citation network formed between datasets and papers that use them. Finally, curation actions can be associated with properties of studies and usage histories.
This dataset has several limitations of which users should be aware. First, Jira tickets can only be used to represent the intensiveness of curation for activities undertaken since 2017, when ICPSR started using both Curation Levels and Jira. Studies published before 2017 were all curated, but documentation of the extent of that curation was not standardized and therefore could not be included in these analyses. Second, the measure of publications relies upon the authors’ clarity of data citation and the ICPSR Bibliography staff’s ability to discover citations with varying formality and clarity. Thus, there is always a chance that some secondary-data-citing publications have been left out of the bibliography. Finally, there may be some cases in which a paper in the ICSPSR bibliography did not actually obtain data from ICPSR. For example, PIs have often written about or even distributed their data prior to their archival in ICSPR. Therefore, those publications would not have cited ICPSR but they are still collected in the Bibliography as being directly related to the data that were eventually deposited at ICPSR.
In summary, the MICA dataset contains relationships between two main types of entities – papers and studies – which can be mined. The tables in the MICA dataset have supported network analysis (community structure and clique detection) 30 ; natural language processing (NER for dataset reference detection) 32 ; visualizing citation networks (to search for datasets) 38 ; and regression analysis (on curation decisions and data downloads) 29 . The data are currently being used to develop research metrics and recommendation systems for research data. Given that DOIs are provided for ICPSR studies and articles in the ICPSR Bibliography, the MICA dataset can also be used with other bibliometric databases, including DataCite, Crossref, OpenAlex, and related indexes. Subscription-based services, such as Dimensions AI, are also compatible with the MICA dataset. In some cases, these services provide abstracts or full text for papers from which data citation contexts can be extracted for semantic content analysis.
Code availability
The code 27 used to produce the MICA project dataset is available on GitHub at https://github.com/ICPSR/mica-data-descriptor and through Zenodo with the identifier https://doi.org/10.5281/zenodo.8432666 . Data manipulation and pre-processing were performed in Python. Data curation for distribution was performed in SPSS.
He, L. & Han, Z. Do usage counts of scientific data make sense? An investigation of the Dryad repository. Library Hi Tech 35 , 332–342 (2017).
Article Google Scholar
Brickley, D., Burgess, M. & Noy, N. Google dataset search: Building a search engine for datasets in an open web ecosystem. In The World Wide Web Conference - WWW ‘19 , 1365–1375 (ACM Press, San Francisco, CA, USA, 2019).
Buneman, P., Dosso, D., Lissandrini, M. & Silvello, G. Data citation and the citation graph. Quantitative Science Studies 2 , 1399–1422 (2022).
Chao, T. C. Disciplinary reach: Investigating the impact of dataset reuse in the earth sciences. Proceedings of the American Society for Information Science and Technology 48 , 1–8 (2011).
Article ADS Google Scholar
Parr, C. et al . A discussion of value metrics for data repositories in earth and environmental sciences. Data Science Journal 18 , 58 (2019).
Eschenfelder, K. R., Shankar, K. & Downey, G. The financial maintenance of social science data archives: Four case studies of long–term infrastructure work. J. Assoc. Inf. Sci. Technol. 73 , 1723–1740 (2022).
Palmer, C. L., Weber, N. M. & Cragin, M. H. The analytic potential of scientific data: Understanding re-use value. Proceedings of the American Society for Information Science and Technology 48 , 1–10 (2011).
Zimmerman, A. S. New knowledge from old data: The role of standards in the sharing and reuse of ecological data. Sci. Technol. Human Values 33 , 631–652 (2008).
Cragin, M. H., Palmer, C. L., Carlson, J. R. & Witt, M. Data sharing, small science and institutional repositories. Philosophical Transactions of the Royal Society A: Mathematical, Physical and Engineering Sciences 368 , 4023–4038 (2010).
Article ADS CAS Google Scholar
Fear, K. M. Measuring and Anticipating the Impact of Data Reuse . Ph.D. thesis, University of Michigan (2013).
Borgman, C. L., Van de Sompel, H., Scharnhorst, A., van den Berg, H. & Treloar, A. Who uses the digital data archive? An exploratory study of DANS. Proceedings of the Association for Information Science and Technology 52 , 1–4 (2015).
Pasquetto, I. V., Borgman, C. L. & Wofford, M. F. Uses and reuses of scientific data: The data creators’ advantage. Harvard Data Science Review 1 (2019).
Gregory, K., Groth, P., Scharnhorst, A. & Wyatt, S. Lost or found? Discovering data needed for research. Harvard Data Science Review (2020).
York, J. Seeking equilibrium in data reuse: A study of knowledge satisficing . Ph.D. thesis, University of Michigan (2022).
Kilbride, W. & Norris, S. Collaborating to clarify the cost of curation. New Review of Information Networking 19 , 44–48 (2014).
Robinson-Garcia, N., Mongeon, P., Jeng, W. & Costas, R. DataCite as a novel bibliometric source: Coverage, strengths and limitations. Journal of Informetrics 11 , 841–854 (2017).
Qin, J., Hemsley, J. & Bratt, S. E. The structural shift and collaboration capacity in GenBank networks: A longitudinal study. Quantitative Science Studies 3 , 174–193 (2022).
Article PubMed PubMed Central Google Scholar
Acuna, D. E., Yi, Z., Liang, L. & Zhuang, H. Predicting the usage of scientific datasets based on article, author, institution, and journal bibliometrics. In Smits, M. (ed.) Information for a Better World: Shaping the Global Future. iConference 2022 ., 42–52 (Springer International Publishing, Cham, 2022).
Zeng, T., Wu, L., Bratt, S. & Acuna, D. E. Assigning credit to scientific datasets using article citation networks. Journal of Informetrics 14 , 101013 (2020).
Koesten, L., Vougiouklis, P., Simperl, E. & Groth, P. Dataset reuse: Toward translating principles to practice. Patterns 1 , 100136 (2020).
Du, C., Cohoon, J., Lopez, P. & Howison, J. Softcite dataset: A dataset of software mentions in biomedical and economic research publications. J. Assoc. Inf. Sci. Technol. 72 , 870–884 (2021).
Aryani, A. et al . A research graph dataset for connecting research data repositories using RD-Switchboard. Sci Data 5 , 180099 (2018).
Färber, M. & Lamprecht, D. The data set knowledge graph: Creating a linked open data source for data sets. Quantitative Science Studies 2 , 1324–1355 (2021).
Perry, A. & Netscher, S. Measuring the time spent on data curation. Journal of Documentation 78 , 282–304 (2022).
Trisovic, A. et al . Advancing computational reproducibility in the Dataverse data repository platform. In Proceedings of the 3rd International Workshop on Practical Reproducible Evaluation of Computer Systems , P-RECS ‘20, 15–20, https://doi.org/10.1145/3391800.3398173 (Association for Computing Machinery, New York, NY, USA, 2020).
Borgman, C. L., Scharnhorst, A. & Golshan, M. S. Digital data archives as knowledge infrastructures: Mediating data sharing and reuse. Journal of the Association for Information Science and Technology 70 , 888–904, https://doi.org/10.1002/asi.24172 (2019).
Lafia, S. et al . MICA Data Descriptor. Zenodo https://doi.org/10.5281/zenodo.8432666 (2023).
Lafia, S., Thomer, A., Bleckley, D., Akmon, D. & Hemphill, L. Leveraging machine learning to detect data curation activities. In 2021 IEEE 17th International Conference on eScience (eScience) , 149–158, https://doi.org/10.1109/eScience51609.2021.00025 (2021).
Hemphill, L., Pienta, A., Lafia, S., Akmon, D. & Bleckley, D. How do properties of data, their curation, and their funding relate to reuse? J. Assoc. Inf. Sci. Technol. 73 , 1432–44, https://doi.org/10.1002/asi.24646 (2021).
Lafia, S., Fan, L., Thomer, A. & Hemphill, L. Subdivisions and crossroads: Identifying hidden community structures in a data archive’s citation network. Quantitative Science Studies 3 , 694–714, https://doi.org/10.1162/qss_a_00209 (2022).
ICPSR. ICPSR Bibliography of Data-related Literature: Collection Criteria. https://www.icpsr.umich.edu/web/pages/ICPSR/citations/collection-criteria.html (2023).
Lafia, S., Fan, L. & Hemphill, L. A natural language processing pipeline for detecting informal data references in academic literature. Proc. Assoc. Inf. Sci. Technol. 59 , 169–178, https://doi.org/10.1002/pra2.614 (2022).
Hook, D. W., Porter, S. J. & Herzog, C. Dimensions: Building context for search and evaluation. Frontiers in Research Metrics and Analytics 3 , 23, https://doi.org/10.3389/frma.2018.00023 (2018).
https://www.icpsr.umich.edu/web/ICPSR/thesaurus (2002). ICPSR. ICPSR Thesaurus.
https://www.icpsr.umich.edu/files/datamanagement/icpsr-curation-levels.pdf (2020). ICPSR. ICPSR Curation Levels.
McKinney, W. Data Structures for Statistical Computing in Python. In van der Walt, S. & Millman, J. (eds.) Proceedings of the 9th Python in Science Conference , 56–61 (2010).
Wickham, H. et al . Welcome to the Tidyverse. Journal of Open Source Software 4 , 1686 (2019).
Fan, L., Lafia, S., Li, L., Yang, F. & Hemphill, L. DataChat: Prototyping a conversational agent for dataset search and visualization. Proc. Assoc. Inf. Sci. Technol. 60 , 586–591 (2023).
Download references
Acknowledgements
We thank the ICPSR Bibliography staff, the ICPSR Data Curation Unit, and the ICPSR Data Stewardship Committee for their support of this research. This material is based upon work supported by the National Science Foundation under grant 1930645. This project was made possible in part by the Institute of Museum and Library Services LG-37-19-0134-19.
Author information
Authors and affiliations.
Inter-university Consortium for Political and Social Research, University of Michigan, Ann Arbor, MI, 48104, USA
Libby Hemphill, Sara Lafia, David Bleckley & Elizabeth Moss
School of Information, University of Michigan, Ann Arbor, MI, 48104, USA
Libby Hemphill & Lizhou Fan
School of Information, University of Arizona, Tucson, AZ, 85721, USA
Andrea Thomer
You can also search for this author in PubMed Google Scholar
Contributions
L.H. and A.T. conceptualized the study design, D.B., E.M., and S.L. prepared the data, S.L., L.F., and L.H. analyzed the data, and D.B. validated the data. All authors reviewed and edited the manuscript.
Corresponding author
Correspondence to Libby Hemphill .
Ethics declarations
Competing interests.
The authors declare no competing interests.
Additional information
Publisher’s note Springer Nature remains neutral with regard to jurisdictional claims in published maps and institutional affiliations.
Rights and permissions
Open Access This article is licensed under a Creative Commons Attribution 4.0 International License, which permits use, sharing, adaptation, distribution and reproduction in any medium or format, as long as you give appropriate credit to the original author(s) and the source, provide a link to the Creative Commons licence, and indicate if changes were made. The images or other third party material in this article are included in the article’s Creative Commons licence, unless indicated otherwise in a credit line to the material. If material is not included in the article’s Creative Commons licence and your intended use is not permitted by statutory regulation or exceeds the permitted use, you will need to obtain permission directly from the copyright holder. To view a copy of this licence, visit http://creativecommons.org/licenses/by/4.0/ .
Reprints and permissions
About this article
Cite this article.
Hemphill, L., Thomer, A., Lafia, S. et al. A dataset for measuring the impact of research data and their curation. Sci Data 11 , 442 (2024). https://doi.org/10.1038/s41597-024-03303-2
Download citation
Received : 16 November 2023
Accepted : 24 April 2024
Published : 03 May 2024
DOI : https://doi.org/10.1038/s41597-024-03303-2
Share this article
Anyone you share the following link with will be able to read this content:
Sorry, a shareable link is not currently available for this article.
Provided by the Springer Nature SharedIt content-sharing initiative
Quick links
- Explore articles by subject
- Guide to authors
- Editorial policies
Sign up for the Nature Briefing newsletter — what matters in science, free to your inbox daily.
- Open access
- Published: 13 May 2024
Bridging the gap between research evidence and its implementation in public health practice: case studies of embedded research model
- Abisope Akintola 1 , 3 ,
- Dorothy Newbury-Birch 2 &
- Stephanie Kilinc 2
BMC Public Health volume 24 , Article number: 1299 ( 2024 ) Cite this article
Metrics details
To investigate the potential of embedded research in bridging the gap between research evidence and its implementation in public health practice.
Using a case study methodology, semi-structured interviews were conducted with 4 embedded researchers, 9 public health practitioners, and 4 other stakeholders (2 teachers and 2 students) across four case study sites. Sites and individuals were purposively selected. Sites included two local authorities, one secondary school, and one sports organisation. Thematic data analysis was adopted to analyse the qualitative data.
Four themes were identified: (1) building and maintaining relationships, (2) working with stakeholders, (3) informing practice, and (4) critical reflection.
Conclusions
Embedded researchers build and maintain relationships with practitioners and other stakeholders to produce research. Evidence from the co-produced research informs future practice and research to improve service and delivery rendered to the public. Thus, embedded researchers use their role to bridge the research evidence - implementation gap in public health practice.
Peer Review reports
Implementation science is widely recognised as a study of methods to adopt and utilise evidence-based interventions in specific locations or settings to improve the health of the population [ 1 ]. However, the gap between research evidence and its implementation in public health practice is still globally recognised [ 2 ]. According to scholars, some of the factors associated with the problem of inadequate implementation of research evidence in practice could either originate from the researchers or the practitioners [ 3 , 4 , 5 ]. This implies that both researchers and practitioners could be responsible for the creation of the gap between research evidence and its implementation in public health practice.
Evidence suggests that lack of access to research evidence is one of the barriers to the implementation of research evidence in practice [ 6 , 7 , 8 ]. One report suggests that increased connectivity between researchers and practitioners would enhance the practitioners’ accessibility to research evidence [ 9 ]. The report explained further that creating some forums where practitioners and researchers could interact would not only bring about easy access to relevant research evidence, but also would serve as a means to share learning, and link researchers and practitioners who have a common interest. Similarly, other scholars report that increasing the interaction between researchers and practitioners among other factors could facilitate the use of research-based evidence in practice [ 10 , 11 ]. To that end, there is a need to increase the opportunities for practitioners and researchers to interact in order to facilitate the utilisation of research evidence in public health practice.
As there are many identified barriers to the use of research evidence in practice, the disparity between the context and the language by which researchers and practitioners operate has also been identified as one of the barriers. The incompatibility in the language spoken by the researchers with respect to the scientific methods and the evidence generated could be ambiguous for practitioners [ 12 ]. Therefore, to overcome this challenge, scholars advise that practitioners and researchers should work collaboratively from the onset of the research while putting into consideration each other’s differences [ 13 , 14 ]. Furthermore, it has been recommended that researchers need to present their research findings and explain the relevance to solving practical problems to the practitioners in a simple language without ambiguity [ 15 ]. This suggests a need for an approach that would involve practitioners and researchers undertaking the research agenda together, and also a need for effectively communicating research findings and their relevance in a simple language to the practitioners.
The context in which the researchers operate could also serve as a challenge to the utilisation of research evidence in practice [ 9 ]. As such, competing pressures such as teaching commitments and publishing academic papers [ 16 ] could pose a challenge to the researchers’ involvement in practical problems that could inform their research questions. Hence, there is a need for an approach for researchers to be more involved in practical problems to facilitate the conduction of research that is relevant and applicable to problem solving. It was noted that not all researchers have the relevant skills to conduct co-produced research [ 17 ]. There is a need to create opportunities for researchers who have relevant skills to co-produce research, to conduct research with suitable practitioners.
On the other hand, organisational factors such as time constraints are contributing factors to the gap between research evidence and practice as most practitioners do not have the skills nor the time needed to implement research outcomes in practice [ 18 ]. To tackle these challenges, some studies recommend continuous training and commitment to quality health delivery on the part of practitioners. They also recommended advancements in technological decision support systems as instruments to combat barriers between research evidence and practice [ 19 , 20 ]. There is an argument that achieving these may be difficult as a result of inadequate funds in health services [ 21 ]. Hence, there is a need for the adoption of a method that will bring about building the capacity of the practitioners towards conducting research that is achievable based on the available budget.
Furthermore, the disparity of influence and power between academics and practitioners could be responsible for the wide gap between research and practice [ 22 ]. This means the relationship between academic researchers and practitioners plays a vital role in the use of research evidence. Therefore, there is a need for a method that would enhance or build mutually beneficial relationships between academic researchers and practitioners to bridge the ‘research evidence-implementation’ gap.
The separation of the development of research evidence from the places it is to be used contributes to the challenges of using research evidence in practice [ 23 ]. This implies that the creation of research knowledge where it is to be utilised could bridge the ‘research evidence-implementation’ gap. As such, co-production has been recommended by scholars to bridge the ‘research evidence-implementation’ gap as co-production involves the collaborative working between the researchers and the practitioners [ 24 ]. Hence, the adoption of co-production to produce public health knowledge by researchers, practitioners, and other stakeholders in non-clinical settings [ 13 , 25 ]. This is essential in tackling the challenges of inadequate implementation of research evidence in public health settings.
Being involved in co-production could result in reputational risk for the researcher involved as the researcher could be used by politicians to enhance authenticity to their political stand [ 26 ]. Thus, being viewed to approve such a political stand can limit the researcher’s ability to work only with a certain political group – this can also impact the researcher’s personal safety [ 27 ]. Also, this can impact negatively on the credibility of the co-production findings as it might be viewed as biased and not a true representation but a narrative to back up a political viewpoint, thus generating “policy-based evidence” [ 28 ] rather than “research-based evidence”. On the other hand, policy-makers might be at risk of sharing sensitive information while participating in co-production work [ 29 ] such as disclosing political errors.
Also, co-production can be costly as it usually involves the stakeholders travelling to the co-production site. This could be viewed as challenging for those that are involved in the co-production project, as their presence at meetings for the co-production work is seen as crucial. Also, funding and sustainability of co-production can pose a great risk to the adoption of co-production [ 48 ]. However, the challenges associated with co-production can be overcome if stakeholders are involved and are carried along at every stage of co-production, from design to implementation [ 30 ]. The success of co-production depends on but is not limited to the following: the individuals involved; how clear the aims and objectives of the project are to all those involved, and how duties are allocated [ 31 ]. This also suggests a need to critically analyse the role of stakeholders involved in co-production to overcome the challenges associated with co-production, to achieve success.
Embedded research, also known as ‘researcher-in-residence’, is becoming popular as a type of co-production research [ 3 ]. Different authors used different terminologies for embedded researchers such as insider researcher [ 32 ], knowledge broker [ 33 , 34 ], or scholar-practitioner [ 35 ]. Within an embedded research model, one of the distinguishing features is that the researcher is located in the host organisation as a member of staff to carry out a research agenda with the host organisation’s staff, and at the same time maintaining affiliation with an academic institution [ 36 , 37 , 38 , 39 ]. In this paper we investigate how an embedded research model can help bridge the gap between research evidence and its implementation in public health practice.
We conducted qualitative case studies and drew data from semi-structured interviews with four embedded researchers, nine public health practitioners, and four other stakeholders (two teachers and two students) across four case study sites including two local authorities (Sites one and two), one secondary school (Site three), and one sports organisation (Site four) in the Northeast of England.
One of the advantages of qualitative research is the ability to generate rich in-depth data or knowledge that can serve as a basis for health and social practices being effective and relevant to the contexts they are applied to [ 40 ]. We adopted a qualitative multi-site case study to understand the context by providing in-depth description and analysis within sites and as well by comparing data between sites in order to identify the similarities and differences between the sites explored [ 41 ]. Thus, this will assist to maximise the applicability of the findings on how an embedded research model can help bridge the gap between research evidence and its implementation in other similar settings.
In site one, the embedded research project aimed to understand and make recommendations regarding population changes, and service needs, including health, education, housing, and social care, in the local communities. In site two, an embedded researcher works at the local authority to provide research support to the local authority’s public health team to secure their targets which include commissioning evidence-based services and interventions, and promotion of healthy lifestyles. Site three conducted an embedded research project to explore the academic and health impact of the recent changes to the General Certificate of Secondary Education (GCSE) system on both staff and students. Site four was established to encourage more people to engage in physical activities to improve their health and well-being. In order to improve the service rendered to the public, an embedded researcher was employed in site four to co-produce research with the sports organisation members of staff. All the embedded researchers across the four case study sites were PhD holders. The amount of time spent in their respective host organisations varied from one hour per fortnight to two and a half days a week to suit the embedded researchers and the host organisations. The embedded researchers’ positions were funded either by the University they are affiliated with, or their host organisation.
Purposive snowball sampling was used in this study. Requests for participants and sites who could volunteer to be part of the study were sent out via relevant professional contacts and networks. The participants and sites that volunteered to take part in this research were asked to assist in the search for participants and/or sites by circulating the study’s details to those who might meet the study’s criteria and would be willing to take part in the study. The inclusion criteria were: (1) being a public health embedded researcher, and (2) being a public health practitioner or stakeholder who is working or has worked with a public health embedded researcher. Potential participants were assessed for eligibility before being interviewed. A total of 17 participants were recruited for the interviews across the four case study sites. The sample size would have been larger than 17 but for the Covid-19 pandemic. Ethical approval was obtained from the Teesside University School of Health and Life Sciences Research Governance and Ethics Committee in November 2019. Data was collected between November 2019 and April 2020.
To facilitate participation, participants were offered alternative modes of interview for their convenience: face-to-face, telephone, and Skype-based interviews. The Covid-19 pandemic occurred during the interview period, but most interviews conducted before COVID-19 were face-to-face. All interviews conducted during the pandemic (March 2020 and onwards) were either Skype or telephone-based, as advised by the Ethics department at Teesside University and as per the requirements of the interviewees’ workplaces. Before each interview, oral and written informed consent was obtained from each participant. Each participant was asked to complete two copies of the consent form, one for their own records and one for the researcher.
Following each interview, a reflective note was taken to identify what went well and what could be done differently in the next interview. Since there were three categories of interview participants – embedded researchers (ERs), public health practitioners (PHPs), and other stakeholders (students (STs) and teachers (TRs)–three sets of interviews were prepared. Although the interview questions were nearly the same for each category of participants, some of the interview questions differed in the way they were structured. Here is an example of how a question was worded differently depending on the participant: (ERs) Can you cite an example where you have built practitioners and other stakeholders’ confidence to conduct their own research? (PHPs, TRs, and STs) Can you cite an example where an embedded researcher has built your confidence to conduct your own research? A full outline of the interview guide is in Appendix .
A summary of each interview was noted in a research diary for reference. Details noted included where each interview took place, the date of the interview, the length of the interview and how the interviewee responded to questions. Each interview lasted between 40 and 90 min. The interviews were recorded, and data was transcribed. We analysed data using inductive thematic analysis [ 42 ] to allow new themes besides the preconceived ones to emerge from the coding of the interviews. Trustworthiness of the analysis was assessed by triangulating between data sources.
Four themes emerged from the analysis of the interview data on the potential of embedded research in bridging the gap between research evidence and its implementation in public health practice: (1) building and maintaining relationships (2) working with stakeholders, (3) informing practice, and (4) critical reflection.
Building and maintaining relationships
All participants across the four case study sites, irrespective of their age, years of experience, or education, recounted the significance of this theme to the embedded research projects in their respective sites. They articulated the benefits of the role of the embedded researchers in building and maintaining relationships with the public health practitioners and other stakeholders to facilitate the co-production of research evidence. They all agreed that building and maintaining relationships played a vital role in the utilisation of the co-produced research evidence and in the closing of the gap between research evidence and its implementation. Overall, the strategies adopted by the embedded researchers to achieve this theme were identified as: (1) building internal/external relationships and sharing skills, and 2) maintaining regular contact with practitioners and other stakeholders.
Building internal/external relationships and sharing skills
Participants agreed that the embedded researchers’ role entails having diverse connections built on good relationships. These relationships assist the embedded researchers in connecting their partners to other relevant organisations such as academic institutions and third sector agencies.
“I think some of that is around having this kind of good grounding so sort of beginning the role with already having made, a lot of kind of contacts, a lot of sort of good relationships been built. [..] I have a line manager in the council, who was the project manager for the first phase so we’ve got that continuity there [..] I also have an academic supervisor who is also my kind of my line manager from the academic side” [ERsite1] .
“I can say that’s [having connections] actually key because they are straddling both worlds. [..] not somebody who sat in the academic institution who didn’t understand the wider context. I think these roles are really key in bridging the institutions” [PHP2site1] .
It was clear that building relationships and connecting the ‘two worlds’ is not only advantageous to both institutions but also assisted the embedded researchers to seek support from both their academic supervisor at the University they were employed and the local authority (LA) they are working with. Therefore, this enables the embedded researchers to be supported fully to carry out their role successfully. It was also recognised that while embedded researchers play their role in building relationships and connecting relevant organisations, the role assisted them to understand the context in which research evidence is to be utilised. Thus, the relevance of research evidence to the host organisation facilitates its use.
This relationship-building was seen as crucial to the success of the role, and it was felt that these relationships could determine the success of any work carried out.
“[..] I would go as far to say I think it’s the relationship that’s built with the individuals who developed that project was important. [..] are the most important elements of co-production” [ERsite2] .
This implies that lack of relationship-building between researchers and public health practitioners can serve as a barrier to embedded research project. Furthermore, it was evident that the relationship built with the stakeholders who were involved in the embedded research was crucial to the projects. For instance, an embedded researcher from site two used her skills to build relationships with the volunteers that participated in the project.
“She [embedded researcher] has been there longer, excellent relationships with the volunteers, that helped to build and shape this project, so she has a very useful experience in terms of relationship-building” [PHP6site2] .
Thus, this assisted in structuring the work which had a positive impact on the project. This two-way relationship with other organisations, including the local universities and research participants, was seen as a benefit of embedded research.
Findings showed that embedded researchers used their contacts and good relationships to facilitate the sharing of skills useful in carrying out embedded research projects and also enable working with other academics at the University.
“[..] even for me just working as an individual in that organisation, I don’t know everything about the research, but because you are linked with the University, that gives an avenue to ask questions and link up with people with expertise to then support an evaluation” [ERsite2] .
These connections and relationships, therefore, enable the sharing of skills useful to co-produce relevant high-quality research evidence useful to host organisations and policy makers.
Within this current study, it was clear that if the embedded researchers were not located or had spent time in the sites, they felt it would be difficult for them to build relationships, and understand the context in which the co-produced research is to be utilised.
“So, having the researcher embedded within in what we do, the researcher has the understanding of the project, and initially she has been with it from the start to finish, so she understands the journey that’s been on, and she understands why it’s been done, how it’s been done [..] So, I think, so the embedded researcher role in what we do is infallible resource really” [ PHP1site4 ] .
The ‘embeddedness’ gave the researchers an understanding of the projects they were involved in. As such, the embedded researchers were seen as ‘insiders’ and their ‘embeddedness’ was seen as key to the success of the work.
It is worth noting that the amount of time spent by the embedded researchers in their respective host organisation varied and was negotiated at the sites to suit the embedded researchers and the host organisations.
“[..] I was familiar with quite a lot of people but obviously kind of being there regularly I have got to know them much better basically. [..] I mean it really varies; I would say probably kind of at least a couple of days in a week” [ERsite1] .
“Being embedded within their team I spend half of the week working within the organisation. It’s been a real pleasure to work alongside them” [ERsite2] .
“ So, we tend to have meetings where I will go in for a few hours at a time. I would probably say, maybe an hour in a fortnight ” [ERsite3] .
“[..] I spend two and a half days working within the organisation. [..] you want to be seen as part of that team and not somebody who just pops up every now and again” [ERsite4] .
However, building relationships and sharing skills was not seen as without its challenges with some tension between roles and expectations.
“[..] it has become trickier splitting myself now between the organisations as they all have their roles and expectations on how they want things to be done” [ ERsite2] .
“The structure can be quite challenging as well, but probably [..] just having that balance in the relationships with the organisation you are working for and the organisation you are evaluating for. And I think yeah you have got to have that one, but that is a challenge of working in large organisation” [PHP6site2] .
The embedded researchers from sites one and two found there was some tension in working in both ‘worlds’ as a result of the responsibilities associated with it, such as building relationships, and balancing diverse responsibilities. This is due to their dual affiliation as such, they are expected to manage a large workload, managing both successfully. A practitioner from site two added that the structure of the organisations the embedded researcher works could also be a challenge, therefore, it is important for an embedded researcher to be able to discuss this with both sides in order that they balance the relationships between the host organisation and the academic institution.
Another notable challenge is having to manage diverse expectations including the ability to balance competing interests of the different organisations.
“There is sort of difference in expectations because I think from the academic point of view, [..] we want publications, we want things that give us an academic output, whereas someone who works in the school is not going to be bothered about that sort of things. They have to see where it positively affects their school, [..] so I think having that difference in agendas on what you want to achieve from this school research can be quite hard to manage. [..] you want different things from this piece of research is quite hard, and make sure that both sides are happy at the end of the day, and I think we did that quite well” [ERsite3] .
For instance, an embedded researcher from the school stated that the expectations from the embedded research project did differ. That is, while part of the aim of the academic input was to publish the outcome of the project to improve or boost their academic output, the school aimed for a practical positive impact of the project on the school, such as improvement in students’ engagement in academic activities. Hence, it was essential to balance the competing interests of the school and the academic side of the embedded research project.
Maintaining regular contact with practitioners and other stakeholders
Based on the participants’ experiences, the embedded researchers built relationships with the practitioners and other stakeholders by maintaining regular contact.
“I think what we did was to help build that relationship. It was not just a telephone conversation just to discuss. We actually worked side by side so there was time to actually do that embedded research. We spent time in the office, we spent like one or two days a week” [PHP1site2] .
“Yeah, but then we did send them emails and stuff, in between [..] yeah we did have time outside of the face to face sessions and sending stuff to the teachers to encourage them, ‘can you remind the students that we have got to do this week’, we have got to get this done by then, so I would say obviously we had the face to face sessions but then we had email correspondence as well” [ERsite3] .
The practitioners from site two reported that the embedded researcher maintained regular contact by face to face, or by telephone. They further explained that they worked side by side with the embedded researcher to build relationships. This implies that if the practitioners and the embedded researcher were not chanced to work together, which assisted in maintaining regular contact, it would have been difficult to build relationships. Thus, this widens the gap between academia and practice. The embedded researchers had similar experiences. For instance, an embedded researcher from site three (school) confirmed that she maintained regular contact to build relationships with the students and the teachers by email and face to face. This shows that it is important to develop project strategies in order to maintain regular contact with the practitioners and other stakeholders to build relationships.
According to the embedded researchers, building mutually beneficial relationships was achieved by maintaining regular contact not only with the stakeholders but also with their academic supervisors which enabled the embedded researchers to have the necessary support to achieve their role.
“I mean knowing that I do have kind of the support at the University to draw on and also have a kind of a good working relationship with my line manager in the council as well really. I don’t feel that I am lacking in any kind of support, which is a good kind of place to be in yeah. So I have monthly meetings in the University and that’s very much really useful in times of keeping track of some of the other parts of my roles so around kind of trying to ensure that we can get some like academic publications and things like that so yeah” [ERsite1] .
Another strategy that was mentioned regarding how the embedded researchers maintained regular contact to build relationships with the practitioners and other stakeholders was ‘attending formal meetings’.
“Interestingly, the researcher has always been on the co-production committee and she attends the meetings, so she is excellent, much better than me because she has been there longer, [..] that helped to build and shape this project [..]” [PHP6site2] .
“So, I have to go to all their team meetings that’s gonna help you form a lot of relationships. Meetings are where the real connection starts to happen. So, you have to invest that time ” [ERsite4] .
As well as making use of formal meeting, the embedded researchers adopted ‘informal conversations’ to maintain regular contact to build relationships with the public health practitioners and other stakeholders.
“For me, I am quite like a chatty person and I think that’s like the characteristics of an embedded researcher. You need somebody who is easy to get on with lots of different people. You need to have that ability to do that. Otherwise, you gonna struggle to form a relationship especially if you aren’t there as often as what you would be if it’s a full-time job” [ ERsite4] .
A practitioner from the sports organisation added that engaging in informal conversations also helped in building a trustworthy relationship with the embedded researcher.
“[..] We have that relationship and some other things you can visit, particularly when things get tough, it’s easy enough to fall back on different conversations on sport [..] These conversations increase our relationship and trust, we trust each other” [PHP1site4] .
The practitioner further explained that he has a good relationship with the embedded researcher and so they engage in informal conversations at difficult times thereby developing a relationship that is based on trust.
Working with stakeholders
Results showed that the embedded researchers build and maintain relationships with the practitioners, and with other stakeholders in order to effectively work together to produce research. This, therefore, facilitated the production and the use of the co-produced research evidence at the embedded sites and helped close the gap between research evidence and its implementation as results were shared quickly with all those that were involved. All participants across the four case study sites unanimously agreed that this theme is one of the primary roles of an embedded researcher, and the strategies identified include: (1) co-producing research, and (2) building research capacity.
Co-producing research
The participants confirmed that they worked together to identify, plan, and conduct research intended to help the host organisations improve their services and meet the needs of the communities with which they work.
“We liaise with the researcher to develop the initial kind of overview of that population [..] the researcher supports us in developing the initial questions, the questionnaire, and the initial research” [PHP1site4] .
“[..] embedding research into the public health team. [..] then helping us to explore the questionnaires. The embedded researcher helps us with the development of that work including the formulae and evaluation for the intervention. We design and develop and embed and undertake the research together. She is very much a part of the team and a core within the team” [PHP4site2] .
“[..] So, really it’s about giving us the exposure to that sort of research. Well, honestly, I have learnt how to conduct research” [ST1site3] .
The participants acknowledged that working together to co-produce research with the embedded researchers encouraged adjustments to and engagement with research-related activities. Furthermore, embedded research was considered a cost-effective research approach.
“ I have been out in a couple of beneficiary interviews with the researcher. Certainly, I would not normally get involved with going out to see clients, but I have gone out a couple of times with the researcher, so that was interesting” [PHP5site2] .
“[..] the embedded researcher worked alongside the public health practitioners [..] how to shape some of the evaluations, including how to be really clear about the methodology, the approach [..] And how to write protocol [..] So, I think that was the aim of it, it was to ensure that we have much more effective and cost-effective research ” [PHP2site1] .
One public health practitioner reported that she participated in several research activities with the embedded researcher at site two. She recognised that working with the researcher enabled her to do research work that she would not have ordinarily done. This suggests that not working together with practitioners to co-produce research may potentially prevent practitioners from being meaningfully involved in the research process. In such situations, the gap between the development and implementation of research evidence may actually become wider. One practitioner from site one explained that embedded research was adopted in the LA so that the authority could conduct cost-effective research. This only further indicates that having an embedded researcher on-site working collaboratively with practitioners and stakeholders to conduct cost-effective research can help bridge the research implementation gap.
However, it was noted that the process of co-producing research between the embedded researchers and the public health practitioners and other stakeholders also facilitated shared learning.
“Despite the fact that we went in obviously thinking of teaching them but the fact that we can learn from them about what was important to them, what was important to young pupils in schools, and how to speak to young pupils because that is schooling in itself. [..] and I think also you learn new skills [..] so I think you get sort of practical experience and learn new skills sort of more practical skills I suppose, not just research skills, so yeah that is why I think I say it’s the most important thing” [ERsite3] .
“[..] and when I have been out with staff members, they will ask questions that I would never have thought of asking, because of their knowledge at work. [..] I have been learning a lot as well from the staff, and that shows the importance of doing it together” [ ERsite2] .
One embedded researcher from site three (school) reported that although their aim was to teach the students how to conduct research, they were able to learn what was important to the young people among other things from the students. Another embedded researcher from site two shared a similar experience and confirmed that during the co-production work, the public health practitioners used their tacit knowledge of their field to ask relevant questions that had not occurred to her. Since the practitioners are more knowledgeable than the researcher regarding actual on-site practices, they added substantial value to the project. This indicates just how much learning is a two-way process, and demonstrates co-production of knowledge which involves the amalgamation of the practitioners’ tacit knowledge and the researchers’ explicit knowledge.
Researchers were explicitly recognised for their ability to co-produce research with the public health practitioners and other stakeholders. Thus, the co-produced research was jointly owned by those involved in the embedded research projects. As the research was co-produced with the intention to assist the organisations to improve the service they render to the public, thus, the embedded researchers’ role assisted in facilitating the utilisation of research evidence. In addition, given the embedded research projects focused on meeting the needs of the host organisations, there were no instances where there were conflicts related to the research emerged.
Building research capacity
The embedded researchers explained that they conducted training, and other developmental activities to help develop the practitioners’ and other stakeholders’ research skill-set.
“I have done a kind of number of training sessions with staff and actually with volunteers that will want to get involved in collecting data [..] so I have run workshops, training workshop, so that means that when I go out there for collection the staff can come and do it with me” [ERsite4] .
“[..] another element of my role is to deliver training to staff around the use of data around the benefits of collecting relevant information, how that information can be used to inform practice in decisions and planning and things like that, we just had a conference couple of weeks ago which was very much about kind of sharing the learning and then sort of getting people involved in the work that we do really, so they are my kind of key targets really” [ ERsite1] .
Research-based training were offered by the embedded researchers in a variety of forms, such as using workshop training, one to one training and through seminars and conferences. For instance, an embedded researcher from site four (sports organisation) reported that she taught the practitioners to collect data at a training workshop that she organised. She explained that this training assisted the embedded research project because it helped the practitioners to get involved in the data collection phase as they had the skills from the training. Similarly, another embedded researcher from site one reported that getting the practitioners involved in the embedded research work facilitated the sharing of learning, which was one of her main goals while working at the LA. This particular researcher trained the public health practitioners to collect data and taught them how research evidence can inform practical decision making.
The participants agreed that working together with the embedded researchers strengthened their ability to conduct high-quality research capable of benefiting their respective organisations.
“ It also allowed us to utilise and build the capacity of public health practitioners who would often not undertake any research for some time” [PHP2site1] .
“So, it’s more like continuous professional development [..] So, the research skills are learnt such that at the end of the day, next time the research could be conducted independently, even if we didn’t have somebody coming from the outside. That’s the whole approach [..] is for developing public health practitioners to the extent that research can be conducted in a rigorous manner” [PHP1site1] .
“I think probably when I attended two beneficiary interviews with her and just seeing how to speak to people when you are asking them questions so there is a way to ask the questions so that they understand, probably by listening to the researcher at that point I sort of learnt how” [ PHP5site2] .
As the above suggests, the embedded researchers encouraged some practitioners who would ordinarily not participate in research to engage in research activities. This implies that working together with researchers may be a significant facilitator to building practitioners’ research capacity and closing the research implementation gap. The absence of an embedded researcher may even serve to widen the gap. Indeed, the public health practitioners observed that working with embedded researchers could eventually build their research capacity to independently conduct high-quality research in the future.
Overall, it was clear that the participants were aware of the importance of working together with embedded researchers, and the researchers were acknowledged for their ability to assist greatly with research-related training and support to build their research capacity. It would have been difficult for these organisations to generate high-quality on-site research if the embedded researchers had not been present. Consequently, the embedded researchers helped work to close the research evidence implementation gap.
Informing practice
The embedded researchers built and maintained relationships with the practitioners and other stakeholders to work together with them to co-produce research. The participants from the four case study sites reflected upon how the embedded researchers informed the sites of relevant research-based evidence, which helped in the development of future practice and research. By doing so, the embedded researchers bridged the gap between the discovery and implementation of research-based evidence. The results showed that all participants across all the four case study sites, irrespective of age, years of experience, and education, agreed that the role of the embedded researchers includes this theme.
The strategies adopted by the embedded researchers include: (1) identifying challenges in the host organisations, (2) utilising research experience, (3) implementing research evidence, (4) disseminating findings, identifying future research areas, and applying for funding, (5) presenting and publishing findings.
Identifying challenges in the host organisations
Participants agreed that the research skills of the embedded researchers are essential to the process of identifying the practical challenges facing the research sites. For instance, an embedded researcher used their research skill to unravel the root cause of the challenges facing a school (site three) through a thorough investigation by developing and conducting relevant research with the students and the teachers.
“[…] the GSCE reforms of the time that was taking place, it was causing a significant amount of stress and pressure for the teachers. In the first instance, teachers were having to grasp new skills at work, they were having to understand the new curriculum and subject knowledge. Some of the teachers weren’t particularly strong, there was a level of undue pressure and stress being put on the students, so pupils nationally were having to learn lots of different contents, they were sort of taken away the security blankets of things like modular testing in course work and what that meant was that students will now have to recall so much more knowledge in exam conditions” [TR1site3] .
Following the identification of these challenges, research-based recommendations were offered through the co-production research. By using research evidence to help tackle the school’s challenges, the researcher bridged the gap between the discovery and implementation of research-based evidence.
Utilising research experience
It is worth noting that the embedded researchers used their research experience to inform their host organisations of relevant existing and newly co-produced research evidence. The embedded researchers’ research-related expertise and the time they spent searching for relevant evidence were both seen as useful to the public health practitioners and other stakeholders.
“The beauty is that because it is their bread and butter, doing reviews and searching for evidence […] one of the things the embedded researcher did to help me with it was to do that literature review [..] it would have taken me much longer [..], so that’s the benefit [..] it is their strength and their experience and skills which they have got and which we may not have and the time to do it which we may not also have because we are constantly under the treadmill” [ PHP1site1] .
It was evident that the practitioners’ busy work schedules often restrict their ability to develop and implement their own research skills. Thankfully, the embedded researchers were able to assist the practitioners by using their research skills to overcome research-related challenges, and in the process taught them how to look for research evidence effectively. This, therefore, facilitates the implementation of evidence-based practice. The implication of this is that practitioners’ lack of research skills and time would have served as a barrier for evidence-based practice in the research sites.
It was clear that the research-based evidence searched for, or co-produced by the embedded researchers and the public health practitioners including other stakeholders was used to inform practice and make positive changes. Evidence showed that the embedded researchers had informed the host organisations of relevant research evidence and had used their research experience and skills to make research-based recommendations. In other words, the embedded researchers made valuable research evidence, and knowledge accessible. As such, this brought about desirable changes that improved service and delivery in the research sites.
“ So the way this works here is that you do the final report which has the recommendations in form of what we feel there should be changes to in practice, and that goes to their public management team and then they will look at that” [ERsite2] .
Furthermore, the embedded researchers also discussed how they helped make positive on-site changes occur. For instance, an embedded researcher from site two reported that positive changes were made in practice after developing recommendations in the form of a report submitted for management’s approval. It was clear that the practitioners take evidence-based advice from the embedded researcher to improve the quality of the services being offered to the public. Thus, this closes the gap between research evidence and its implementation.
Implementing research evidence
The interviews inquired as to how research-based evidence was translated into practice at the four research sites. As the interview process continued, it became clear that desired changes and improvements were achieved through the on-site application of research-based evidence. The results showed that across the four research sites, this process did indeed happen.
“[..] as it is very much about kind of being a resource to implement the recommendations and embed kind of the key findings from the research, again my role is trying to get some of these things into practice really so its embedded research but the main one of the main things is around embedding the recommendations as well, so that’s sort of work my role is around doing” [ ERsite1] .
“ [..] at the same time, it also helps the researcher coming in to understand what goes on in practice so that you don’t just go and conduct a piece of research that goes on the shelves. [..] So we would then need to weigh the evidence and the circumstances under which we are going to implement an intervention but we still take advice from the researcher on the evidence of what works. They could advice on what works [..] It’s more about the outcome of research being used to influence practice for quality improvement” [ PHP1site1] “There are changes that are made with how they recruit their staff for the delivery staff […] that changes were made and that was in practice, and they also kind of put it in a set of recommendations as to the ones to be delivered in schools” [ERsite4] .
Participants reported that the embedded researchers recommended existing research evidence, co-produced research evidence with the intent of informing practice, and also used relevant evidence to help improve service and delivery. In other words, the role of embedded researchers provided accessibility to research-based evidence that was utilised to develop solutions to on-site challenges and create positive change.
Disseminating findings, identifying future research areas, and applying for funding
The embedded researchers reported that having to present reports to diverse audiences prompted them to produce easily understandable, user-friendly reports that did not rely heavily on academic language.
“[..] so I have quarterly reports that I have to produce which has to be user-friendly and appeal to a various range of agencies within the organisation [..] we had, basically we have had quite a few different presentations to different kind of groups or the senior management team and departmental teams and things which was about and sharing the results and recommendations, we have follow-ups sort of things from that” [ ERsite1] .
“[..] Yeah, just into writing report so she will do like verbal update or she provides like some blueprints in an email ” [PHP5site2] .
The reports created by the embedded researchers avoided scientific terms that might be difficult for public health practitioners and other stakeholders to understand. Furthermore, practitioners and other stakeholders were informed of relevant research evidence in an unambiguous way. It is important to add that it would have been difficult for the embedded researchers to appropriately simplify their language if they had not had the opportunity to spend time on-site becoming familiar with the language used by the practitioners and stakeholders.
The participants also reported that the embedded research projects effectively discovered potential areas for future research. By making suggestions regarding future research, the embedded researchers furthered each host organisation’s potential to engage in relevant, change-creating research.
“[..] then the research outcomes were used to inform the next phase, so obviously that was the first phase, which we felt was really successful and worked really well, so then we took those sort of the things we learnt to the next phase” [ERsite3] .
For example, an embedded researcher from site three (school) stated that the first phase of their embedded research project was such a success that the findings of the first phase informed the direction of the second phase, thereby ensuring continuous research activities in the school.
Furthermore, participants agreed that the outcomes of the embedded research projects assisted with the application for future funding.
“[..] the results of the work that we did has been kind of used in terms of future funding opportunities, for providing data, providing kind of context information that was used in sort of proposals and in bids pushing and for applying for future funding” [ERsite1] .
It was evident that the presence of the embedded researchers in their host organisations encouraged the push to apply for funding to develop projects. This, therefore, facilitates continuous engagement in research activities. The practitioners felt that the role of the embedded researchers is crucial to producing funding applications and program development.
Presenting and publishing findings
Once embedded researchers succeeded at co-producing relevant on-site research evidence with practitioners and other stakeholders, and offering practical solutions to on-site challenges, it became clear that it would be necessary to present and publish the outcomes of the projects. Consequently, embedded researchers used their academic skills to publish the findings with practitioners and other stakeholders as co-authors. One of the benefits of publication is that published research can inform the host organisation, and other organisations facing similar challenges. Another significance of the role of embedded research pertaining to this, is that as the embedded research project is co-produced by both the embedded researcher and the host organisation, the findings from the research are jointly owned by both parties. This also assisted in integrating research into the host organisations culture.
“We wrote a book chapter with their names on the published book chapter. We got all of them involved with the writing of the chapter [..] that makes a sort of massive difference ” [ERsite3] .
“We co-authored a chapter of a book. We used the findings to create a book chapter but all of us has input into it including the researchers” [ST2site3] .
For example, participants from site three (school) reported that a book chapter based on co-produced research that they had worked on with the embedded researcher had been published [ 43 ]. Co-produced and co-published research evidence informs the school and research community of the institutional value of embedded research projects. The embedded researcher from site three (school) added that the names of the students and staff involved in the research and writing processes were included in the book chapter. The book chapter was co-edited by both an academic and a public health consultant. This publication has made a tremendous positive difference to how a school labelled as ‘deprived’ views itself. Indeed, being involved in the co-production of valuable research has encouraged both students and teachers.
To further explore how embedded researchers can inform public health practice, the participants were asked whether any other evidence-sharing processes had been used by the embedded researchers. The embedded researchers in this study were connected to more than one organisation. Consequently, they have access to organisations with information that can benefit public health practitioners and other stakeholders. The participants felt that participating in other organisations helped the embedded researchers fulfil their role as the discoverers and sharers of information. The participants viewed this role of the embedded researcher in their sites important as it informs them of the latest research evidence and activities in the field. This could also be seen as a way to sustain evidence-based practice in the sites. As the practitioners are regularly informed of the latest relevant evidence by attending research-based programmes, it facilitates the integration of research into the host organisations’ culture.
“When I see opportunities for conferences or local events, I will send an email or circulating them, there might be public health conference, it might be a Fuse conference that’s linked in erm linked in heavily with the thing we have worked on and I circulate that to the staff member, to say here is an opportunity” [ERsite2] .
For instance, an embedded researcher from site two stated that she regularly informed the practitioners of programmes and events presenting research relevant to their practice. By attending such events, practitioners can stay informed and up to date and are more likely to make changes to their practice based on timely research evidence. Consequently, the findings of this study indicate that staying familiar with the latest relevant research is one of the ways to close the gap between the discovery and implementation of research-based evidence.
Overall, it was evident that the embedded researchers’ ability to inform the organisations with relevant co-produced research evidence, and the ability to identify relevant information and opportunities and then circulate these to public health practitioners and stakeholders helped to inform the sites in creating relevant, research-based changes to benefit their public health practices. The positive outcomes they generated indicate that the role of embedded researchers can seriously contribute to closing the gap between the discovery and implementation of research-based evidence in the research sites.
Critical reflection
Twelve out of seventeen participants across the four sites discussed this theme as part of the role of the embedded researcher in their respective organisations. Participants felt that critical reflection was an important process an embedded researcher must engage in throughout the ‘journey’ of becoming an agent of closing the gap between research evidence and its implementation in practice. The identified strategy adopted by the embedded researchers within this theme is continuous reflection.
“I constantly reflect on my role to know what I am doing right, and what can be done differently” [ERsite1] .
“I have to spend really more time reflecting” [ERsite2] .
“It might be while you drive home [..] might be in the shower [..] might be when I take the dog out for a walk and tea time to reflect because you do need time to reflect on your research, on your methodology [..] about what the findings need to show [..] at times my bag is full of paper everywhere, millions of notes in here and I have to open and jot down some questions so that I won’t forget them because they are so important” [ERsite4] .
“I think it’s always good to sort of like reflect on what we have done, how we do things I personally want to think about whether I could have done things better […] so I think it’s quite important to sort of reflect on how you have done things, and how you could do things in the future, like what lessons you have learnt, I think it’s important to sort of reflect, to sort of think more about how you have done things and whether it could be practiced in the future” [ERsite3] .
Overall, the participants agreed that reflection helps embedded researchers assess their roles and constantly improve their work. Therefore, reflection is crucial to successfully co-producing research and closing the research implementation gap.
All participants, irrespective of their age, working experience and education, acknowledged that the relationships between the people involved in an embedded research project are crucial to the project’s success. This is in keeping with those made in previous studies that have concluded that building and maintaining mutually beneficial relationships with practitioners and other stakeholders significantly helps embedded researchers co-produce public health knowledge in non-clinical settings [ 33 , 44 ]. The study participants were also unanimous in their view that the ‘embeddedness’ of the researchers, or the degree to which they become part of or spend time within the host organisation, is significant. A higher degree of embeddedness appears to lead to the development of beneficial relationships and also helps researchers develop a better understanding of organisational contexts, that in turn leads to the development of effective solutions and useful, co-produced research. Notably, becoming embedded to a significant degree helps others see the researchers as part of the team. Previous studies have also indicated it is the duty of the embedded researcher to become part of the host organisation by working collaboratively with practitioners and other stakeholders [ 17 , 45 ].
Although the amount of time each embedded researcher spent within their host organisation varied, the interview data gathered from all sites confirmed that embedded researchers felt they were able to develop meaningful relationships with the host organisation. The National Institute for Health Research (NIHR) embedded research team reported similar findings and observed that the amount of time spent within an organisation can depend on the intensity of a project [ 46 ].
Among other strategies, informal conversations with the practitioners and other stakeholders also assisted the embedded researchers to build relationships. This was confirmed only by the embedded researchers in case study sites two and four who had worked in the host organisations for more than three years. This might be because the embedded researchers from the local authority (site two) and the sports organisation (site four) had worked and familiarised themselves with the members of the host organisation staff. Consequently, this could have facilitated easier informal conversations, unlike the embedded researcher in site one who has just spent seven months in the site. This confirms that it takes time for embedded researchers to build trustworthy relationships in the host organisation and they recommend an ‘introductory period’ of a minimum of three months for familiarisation before an embedded research project starts [ 39 ]. This was beneficial to the three case studies explored in an earlier study as it allowed the embedded researchers to familiarise themselves with their host organisations and as well build relationships with the host organisations’ staff [ 39 ]. This also aligns with the view of other scholars that an ‘introductory period’ is important before the commencement of an embedded research project [ 44 ]. It is worth noting that the practicability of an ‘introductory period’ may depend on the agreement between the parties involved.
Furthermore, embedded researchers must build relationships not only with practitioners and other stakeholders, but also with their academic supervisors. Having a successful relationship with the academic supervisor can help the embedded researcher overcome the challenges that arise as a consequence of having a dual affiliation and needing to manage diverse expectations and competing interests. The embedded researchers interviewed in this study had the support of their academic supervisors. Thanks to the vast experience of their supervisors, they are often excellent at mitigating unforeseen challenges. Indeed, among other factors, the success of an embedded researcher depends on the relationship between the researcher and his or her academic supervisor [ 13 , 39 ].
The interview participants recounted that it is important to work together to co-produce relevant research which is useful to the organisations. Other scholars have similarly concluded that embedded researchers work with members of their host organisations to identify, plan, and conduct research that will meet the needs of the organisation [ 36 ]. By working collaboratively, embedded researchers were able to train the practitioners and other stakeholders and improve their ability to help co-produce meaningful and valuable research that can be used to implement evidence-based adjustments to on-site practices.
The findings of this study indicate that working together produces meaningful research and also teaches practitioners and other stakeholders who assist embedded researchers, how to conduct research. Similarly, an earlier study concluded that embedded researchers encourage practitioners and other stakeholders to participate in research activities and increase an organisation’s capacity to conduct research [ 17 ]. In other words, the collaborative work that accompanies embedded research helps close the research implementation gap. However, it was noted in this current qualitative inquiry that having the right researchers assisted in carrying out the projects successfully. This is similar to an earlier study that argue that having the right combination of researchers and practitioners in co-production is crucial to the success of such project [ 13 ]. Also, other scholars pointed out that not all researchers have the relevant skills to conduct co-produced research [ 17 ]. Therefore, it is essential to have the right combination of researchers, practitioners, and other stakeholders while working together to co-produce research to ensure its success.
Based on the current qualitative inquiry, the role of the embedded researchers includes informing practice by making recommendations and positive changes that utilise both existing and newly co-produced research evidence. Doing so makes research evidence more accessible to public health practitioners and other stakeholders and ultimately improves service and delivery. An earlier study similarly revealed that informing practice has been identified as a way by which embedded researchers communicate new and existing relevant research evidence and integrate research findings into practice [ 3 ].
As discussed earlier, two of the factors responsible for the gap between the discovery and implementation of research evidence are the disparity between the language spoken by the researchers and practitioners and the complexity of the language spoken by researchers, which is often include scientific jargon. Such complex language can be difficult for practitioners to understand or lead to ambiguities in interpretation [ 12 ]. To discover whether language differences was an issue in this study, the interviews included questions regarding how research evidence and recommendations were communicated to public health practitioners and other stakeholders. These questions were designed to create an understanding of how the embedded researchers had communicated. The interviews revealed that the embedded researchers communicated research outcomes and recommendations effectively to the practitioners by using simple, unambiguous language. Using such language helped make research evidence more accessible to the practitioners.
Providing evidence for reports and future funding applications was identified as an important part of the embedded researchers’ work within their host organisations [ 17 , 47 ]. The interview participants agreed that the researchers sometimes helped secure funds needed to conduct research at the host organisation. Doing so encouraged each host organisation’s staff to participate in research that could prove useful to the organisation in the future.
Critical reflection helps embedded researchers evaluate the role they play within their host organisation and keep track of their progress [ 33 , 48 ]. In other words, reflection helps researchers identify and improve upon the areas that are not meeting expectations and discover what approaches are working successfully. This corresponds with the findings from this current qualitative inquiry. The interview participants acknowledged that the embedded researchers continuously reflect on their role and their work in order to identify what is and is not working. This assists embedded researchers to think of ways to apply acquired learning to daily on-site practice to improve their role in the co-production of research to bridge the gap between research evidence and its implementation in public health practice.
Limitations of the study
One of the limitations of this study was the sample size. A total of 17 participants was recruited for this study, although the sample size would have been larger than 17 but for the COVID-19 pandemic. Another consideration of this piece of work, being qualitative research, was subjectivity. The information provided by the participants was based on their point of view. Hence, it might be difficult to objectively verify the qualitative information provided to ensure that accurate information was provided by the participant regarding the phenomenon of interest. Nevertheless, some practical measures were undertaken to ensure the credibility of this work. Data triangulation and site triangulation [ 49 ] were adopted in this study. These were done to increase the confidence in the outcome of the qualitative multi-site case study.
Overall, the success that the embedded researchers experienced, including building relationships, co-producing research, translating research into practical changes, evaluating projects, and informing future public health practices as well as future research, justifies increasing the amount of embedded research being conducted in public health practice. Embedded researchers also bring the tremendous benefit of strengthening the research capacities of public health practitioners and other stakeholders by providing research-based training and support. Such developments have the ability to prove the potential of embedded research projects. Finally, the relevant research-based recommendations made from the co-produced research guided by the embedded researchers are used to inform practice. The positive outcomes generated by the embedded research process indicate that embedded researchers can meaningfully contribute to closing the gap between the discovery and implementation of research evidence.
Availability of data and materials
The datasets generated and/or analysed during the current study are not publicly available. They are available from the corresponding author on reasonable request, subject to approval from the Teesside University School of Health and Life Sciences Research Governance and Ethics Committee.
Lobb R, Colditz GA. Implementation science and its application to population health. Annu Rev Public Health. 2013;34:235–51.
Article PubMed PubMed Central Google Scholar
Di Ruggiero E, Viehbeck S, Greyson D. Knowledge utilization and exchange. Oxford: Oxford University Press—Oxford Bibliographies in Public Health; 2017.
Google Scholar
Marshall M, Pagel C, French C, Utley M, Allwood D, Fulop N, Pope C, Banks V, Goldman A. Moving improvement research closer to practice: the researcher in residence model. BMJ Qual Saf. 2014;23:801–5.
Chew S, Armstrong N, Martin G. Institutionalising knowledge brokering as a sustainable knowledge translation solution in healthcare: how can it work in practice? Evid Policy. 2013;9:335–51.
Article Google Scholar
Proudfoot A, Mcauley D, Hind M, Griffith M. Translational research: what does it means, what has it delivered and what it might deliver? Curr Opin Crit Care. 2011;17:495–503.
Article PubMed Google Scholar
Albert MA, Fretheim A, Maiga D. Factors influencing the utilization of research findings by health policymakers in a developing country: the selection of mali’s essential medicines. Health Res Policy Syst. 2007;5:2.
Armstrong R, Doyle J, Lamb C, Waters E. Multi-sectoral health promotion and public health: the role of evidence. J Public Health. 2006;28(2):168–72.
Bunn F. Strategies to promote the impact of systematic reviews on healthcare policy: a systematic review of the literature. Evid Policy. 2011;7:428.
Allen T, Grace C, Martin S. From analysis to action: connecting research and local government in an age of austerity. Report of the local government knowledge navigator. London: Local Government Association; 2014.
Campbell D, Donald B, Moore G, Frew D. Evidence check: knowledge brokering to commission research reviews for policy. Evid Policy. 2011;7(1):97–107.
Dobbins M, Robeson P, Ciliska D, Hanna S, Cameron R, O’mara L, et al. A description of a Knowledge Broker Role implemented as part of a randomized controlled trial evaluating three knowledge translation strategies. Implement Sci. 2009;4:23.
Friese B, Bogenschneider K. The Voice of experience: how social scientists communicate family research to policymakers. Fam Relat. 2009;58(2):229–43.
Newbury-birch D, Allan K. Co-creating and co-producing Research evidence: a guide for practitioners and academics in Health, Social Care and Education Settings. London and New York: Routledge; 2019.
Book Google Scholar
Van der graaf P, Forrest L, Adams J, Shucksmith J, White M. How do public health professionals view and engage with research? A qualitative interview study and stakeholder workshop engaging public health professionals and researchers. BMC Public Health. 2017;17:892.
Hobin EP, Riley B, Hayward S, Ruggiero ED, Birdsell J. Maximising the use of evidence: exploring the Intersection between Population health intervention research and knowledge translation from a Canadian perspective. Evid Policy. 2012;8(1):97–115.
Oliver K, Kothari A, Mays N. The dark side of coproduction: do the costs outweigh the benefits for health research? Health Res Policy Syst. 2019;17:33.
Wong S. Tales from the frontline: the experiences of early childhood practitioners working with an ‘Embedded’ research team. Eval Program Plann. 2009;32:99–108.
Fathimath S, David E, Helen B. Nurses’ perceptions of barriers and facilitators to implement EBP in the Maldives. Adv Nurs. 2014;2014:7. Article ID 698604.
Aszkenasy OM, Dawson D, Gill M, Haines A, Patterson DLH. Audit of direct access cardiac investigations: experience in an inner london health district. J R Soc Med. 1994;87:588–90.
Article CAS PubMed PubMed Central Google Scholar
Davis DA, Thomson MA, Oxman AD, Haynes RB. Changing physician performance: a systematic review of the effect of educational strategies. J Am Med Assoc. 1995;274:700–5.
Article CAS Google Scholar
Sutton M. How to get the best health outcome for a given amount of money. BMJ. 1997;1997(315):47–9.
Rycroft-malone J. From knowing to doing: from the academy to practice, comment on the many meanings of evidence: implications for the translational science agenda in healthcare. Int J Health Policy Manag. 2014;2:1–2.
Walshe K, Davies H. Health research, development and innovation in England from 1988 to 2013: from Research production to knowledge mobilization. J Health Serv Res. 2013;18:1–12.
Ryan B. Coproduction: option or obligation? Aust J Public Adm. 2012;71:314–24.
Groundwater-smith S, Mockler N. The knowledge building school: from the outside in, from the inside out. Change Transform Educ. 2002;5:15–24.
Himmrich J. How should academics interact with policy makers? Lessons on building a long-term advocacy strategy. LSE Impact Blog. 2016. Available at: How should academics interact with policy makers? Lessons on building a long-term advocacy strategy. | Impact of Social Sciences (lse.ac.uk). Accessed 15/01/2022.
Zevallos Z. Protecting activist academics against public harassment. Other Sociologist. 2017. Available at: Protecting Activist Academics Against Public Harassment – The Other Sociologist. Accessed 15/01/2022.
Davey SG, Ebrahim S, Frankel S. How policy informs the evidence. BMJ. 2001;322(7280):184–5.
Maybin J. How proximity and trust are key factors in getting research to feed into policymaking. LSE Impact Blog. 2016. Available at: How proximity and trust are key factors in getting research to feed into policymaking | Impact of Social Sciences (lse.ac.uk). Accessed 15/01/2022.
Rycroft-malone J, Burton CR, Bucknall T, Graham ID, Hutchinson AM, Stacey D. Collaboration and co-production of knowledge in healthcare: opportunities and challenges. Int J Health Policy Manage. 2016;5(4):221–3.
Hegger D, Dieperink C. Toward successful joint knowledge production for Climate Change Adaptation: lessons from six Regional projects in the Netherlands. Ecol Soc. 2014;19(2):34.
Brannick T, Coghlan D. Defense of being native: the case for insider academic research. Organ Res Methods. 2007;10:59–74.
Langeveld K, Stronks K, Harting J. Use of a Knowledge Broker to establish healthy public policies in a city district: a developmental evaluation. BMC Public Health. 2016;16:271.
Yost J, Dobbins M, Traynor R, Decorby K, Workentine S, Greco L. Tools to support evidence-informed public health decision making. BMC Public Health. 2014;14:728.
Smith LS, Wilkins N. Mind the gap: approaches to addressing the research-to-practice, practice-to-research chasm. J Public Health Manage Pract. 2018;24:S6–11.
Mcginity R, Salokangas M. Introduction: “Embedded Research” as an Approach into academia for emerging researchers. Management in Education. 2014;28:3–5.
Dixon-woods M, Martin G. Does quality improvement improve quality? Future. Hosp J. 2016;3:191–4.
Dixon-woods M, Mcnicol S, Martin G. Ten challenges in improving quality in healthcare: lessons from the Health foundation’s programme evaluations and relevant literature. BMJ Qual Saf. 2012;21:876–84.
Vindrola-padros C, Eyre L, Baxter H, et al. Addressing the challenges of knowledge co-production in quality improvement: learning from the implementation of the researcher-in-residence model. BMJ Qual Saf. 2019;28:67–73.
Polit D, Beck C. Generalization in quantitative and qualitative research: myths and strategies. Int J Nurs Stud. 2010;47:1451–8.
Jenkins EK, Slemon A, Haines-saah RJ, Oliffe J. A Guide to multisite qualitative analysis. Qual Health Res. 2018;28(12):1969–77.
Braun V, Clarke V. Using thematic analysis in psychology. Qualitative Res Psychol. 2006;3(2):77–101.
Hayden MC, Waller G, Hodgson A, Brown S, Harris S, Miller K, Barber D, Hudson L, Newbury-Birch D. ‘Pupils, Teachers and Academics Working Together on a Research Project Examining How Students and Teachers Feel About the New GCSEs’, in Newbury-Birch and Allan. Co-creating and Co-producing Research Evidence: A Guide for Practitioners and Academics in Health, Social Care and Education Settings. London and New York: Routledge, Taylor & Francis Group; 2019.
Lewis S, Russell A. Being embedded: a way forward for ethnographic research. Ethnography. 2011;12:398–416.
Rowley H. Going beyond procedure: engaging with the ethical complexities of being an embedded researcher. Manage Educ. 2014;28:19–24.
Embedded research. https://www.embeddedresearch.org.uk . (No date). Accessed 22 Nov 2023.
Jenness V. Pluto, prisons, and plaintiffs: notes on systematic back-translation from an embedded researcher. Soc Probl. 2008;55:1–22.
Duggan J. Critical friendship and critical orphanship: embedded research of an english local authority initiative. Manage Educ. 2014;28(1):12–8.
Denzin N. The Research Act: A Theoretical Introduction to Sociological Methods (2nd edition). New York: McGraw Hill; 1978.
Download references
Acknowledgements
We thank the participants for sharing their expertise and time. We are grateful for the contribution of Ronnie Ramlogan who supported us in the preparation of this manuscript.
This research received no external funding.
Author information
Authors and affiliations.
School of Health and Life Science, Teesside University, Middlesbrough, UK
Abisope Akintola
School of School of Social Sciences, Humanities & Law, Teesside University, Middlesbrough, UK
Dorothy Newbury-Birch & Stephanie Kilinc
Manchester Institute of Innovation Research, Alliance Manchester Business School, University of Manchester, Manchester, UK
You can also search for this author in PubMed Google Scholar
Contributions
This study is part of AA’s PhD work, as such, AA conducted this piece of work with the supervision of DNB and SK.
Corresponding author
Correspondence to Abisope Akintola .
Ethics declarations
Ethics approval and consent to participate.
Ethical approval was obtained from the Teesside University School of Health and Life Sciences Research Governance and Ethics Committee. All methods were carried out in accordance with relevant research guidelines and regulations. The participants were informed about the purpose of the research, the voluntary nature of participation, and their right to withdraw at any time without any consequences. The anonymity and privacy of the participants were guaranteed throughout the study. Informed written and verbal consent was obtained from the participants before the interviews.
Consent for publication
Not applicable.
Competing interests
The authors declare no competing interests.
Additional information
Publisher’s note.
Springer Nature remains neutral with regard to jurisdictional claims in published maps and institutional affiliations.
Interview schedule for embedded researchers
Role identification and background information about the embedded research initiative.
What is your role in your organisation? Prompt - Job title, Daily task, Responsibilities. B) How long have you been in this role? C) Can you tell me about your background and what you do? Prompt -The journey so far- How do you get to where you are now? D) As an embedded researcher where is your academic affiliation?
How long has your embedded research initiative been going on in your organisation? B) Do you know the rationale for employing an embedded researcher in your organisation? C) Who funds your project? D)What is the management arrangement?
Moving on to look at the embedded research initiative more specifically
What is the aim of the embedded research project you are involved in? B) How many hours/days do you spend in your host organisation in a week, and in the academic institution? C) Why? D) How often do you contact your academic supervisor?
How has embedded research gone so far in your organisation? B) How many people are involved in the co-production/embedded research you are involved in? or who do you work with? C) How many embedded researchers are involved in the project? Prompt - How many professionals/stakeholders?
What are your views and experience of embedded research? Prompt - what have you learnt? What, if anything, has helped? (Why do you say that?) What, if anything, has been more difficult or challenging? (Why do you say that)? What difference has embedded research made in your organisation? (so if embedded research has been useful, why and how?)
Looking more specifically at the role of the embedded researcher in the organisation
What is your role, as an embedded researcher in bridging the gap between research evidence and its implementation in practice? Prompts - How do you inform practice with research evidence? How do you communicate research evidence to practitioners and other stakeholders to facilitate its use in practice? B) Does your role involve the translation of research evidence into practice? If yes, what is the process? can you please cite an example? What evidence-sharing methods or processes do you use?
Can you think of any changes in practice/policy as a result of research evidence being used? Prompt – What role did you play? Who was involved? What changed? How? For who?
Tell me what you think are the benefits of working as an embedded researcher? Why do you say that? B) How do you manage the dual affiliation? Prompt -what are the benefits (What has helped?) and also what are the challenges?
Tell me what you think are the challenges of working as an embedded researcher? Prompt - Why do you say that? B) What are the barriers to data sharing, if any?
Do you think building mutually beneficial relationships with the host organisation staff is important to the success of an embedded research project? If yes, Why? B) How do you build relationships with the host organisation’s staff?
Can you cite an example of where you have built practitioners and other stakeholders’ confidence in conducting their own research?
Does your role requires managing research funds? If yes, how do you manage this?
How often do you reflect on your role? Prompt- To know what works and what needs to be improved? Why is this important?
Do you think the development of a toolkit on the role of embedded research in bridging the gap between research evidence and its implementation in public health practice would be useful? If yes, Why and how do you think it could be used in practice?”
Any top tips for other researchers considering embedded research?
Please don’t mention names, but can you think of any potential participants- people you are working with or have worked with that you can pass on the details of this research? B) Would you be happy to be contacted afterward to circulate details of this research to those you have identified, to see if they will be willing to participate in this research?
Rights and permissions
Open Access This article is licensed under a Creative Commons Attribution 4.0 International License, which permits use, sharing, adaptation, distribution and reproduction in any medium or format, as long as you give appropriate credit to the original author(s) and the source, provide a link to the Creative Commons licence, and indicate if changes were made. The images or other third party material in this article are included in the article's Creative Commons licence, unless indicated otherwise in a credit line to the material. If material is not included in the article's Creative Commons licence and your intended use is not permitted by statutory regulation or exceeds the permitted use, you will need to obtain permission directly from the copyright holder. To view a copy of this licence, visit http://creativecommons.org/licenses/by/4.0/ . The Creative Commons Public Domain Dedication waiver ( http://creativecommons.org/publicdomain/zero/1.0/ ) applies to the data made available in this article, unless otherwise stated in a credit line to the data.
Reprints and permissions
About this article
Cite this article.
Akintola, A., Newbury-Birch, D. & Kilinc, S. Bridging the gap between research evidence and its implementation in public health practice: case studies of embedded research model. BMC Public Health 24 , 1299 (2024). https://doi.org/10.1186/s12889-024-18727-z
Download citation
Received : 05 January 2024
Accepted : 28 April 2024
Published : 13 May 2024
DOI : https://doi.org/10.1186/s12889-024-18727-z
Share this article
Anyone you share the following link with will be able to read this content:
Sorry, a shareable link is not currently available for this article.
Provided by the Springer Nature SharedIt content-sharing initiative
- Public health
- Embedded research
- Research-based evidence
- Co-production
- Research evidence- implementation gap
BMC Public Health
ISSN: 1471-2458
- Submission enquiries: [email protected]
- General enquiries: [email protected]
Have a language expert improve your writing
Run a free plagiarism check in 10 minutes, automatically generate references for free.
- Knowledge Base
- Methodology
- Data Collection Methods | Step-by-Step Guide & Examples
Data Collection Methods | Step-by-Step Guide & Examples
Published on 4 May 2022 by Pritha Bhandari .
Data collection is a systematic process of gathering observations or measurements. Whether you are performing research for business, governmental, or academic purposes, data collection allows you to gain first-hand knowledge and original insights into your research problem .
While methods and aims may differ between fields, the overall process of data collection remains largely the same. Before you begin collecting data, you need to consider:
- The aim of the research
- The type of data that you will collect
- The methods and procedures you will use to collect, store, and process the data
To collect high-quality data that is relevant to your purposes, follow these four steps.
Table of contents
Step 1: define the aim of your research, step 2: choose your data collection method, step 3: plan your data collection procedures, step 4: collect the data, frequently asked questions about data collection.
Before you start the process of data collection, you need to identify exactly what you want to achieve. You can start by writing a problem statement : what is the practical or scientific issue that you want to address, and why does it matter?
Next, formulate one or more research questions that precisely define what you want to find out. Depending on your research questions, you might need to collect quantitative or qualitative data :
- Quantitative data is expressed in numbers and graphs and is analysed through statistical methods .
- Qualitative data is expressed in words and analysed through interpretations and categorisations.
If your aim is to test a hypothesis , measure something precisely, or gain large-scale statistical insights, collect quantitative data. If your aim is to explore ideas, understand experiences, or gain detailed insights into a specific context, collect qualitative data.
If you have several aims, you can use a mixed methods approach that collects both types of data.
- Your first aim is to assess whether there are significant differences in perceptions of managers across different departments and office locations.
- Your second aim is to gather meaningful feedback from employees to explore new ideas for how managers can improve.
Prevent plagiarism, run a free check.
Based on the data you want to collect, decide which method is best suited for your research.
- Experimental research is primarily a quantitative method.
- Interviews , focus groups , and ethnographies are qualitative methods.
- Surveys , observations, archival research, and secondary data collection can be quantitative or qualitative methods.
Carefully consider what method you will use to gather data that helps you directly answer your research questions.
When you know which method(s) you are using, you need to plan exactly how you will implement them. What procedures will you follow to make accurate observations or measurements of the variables you are interested in?
For instance, if you’re conducting surveys or interviews, decide what form the questions will take; if you’re conducting an experiment, make decisions about your experimental design .
Operationalisation
Sometimes your variables can be measured directly: for example, you can collect data on the average age of employees simply by asking for dates of birth. However, often you’ll be interested in collecting data on more abstract concepts or variables that can’t be directly observed.
Operationalisation means turning abstract conceptual ideas into measurable observations. When planning how you will collect data, you need to translate the conceptual definition of what you want to study into the operational definition of what you will actually measure.
- You ask managers to rate their own leadership skills on 5-point scales assessing the ability to delegate, decisiveness, and dependability.
- You ask their direct employees to provide anonymous feedback on the managers regarding the same topics.
You may need to develop a sampling plan to obtain data systematically. This involves defining a population , the group you want to draw conclusions about, and a sample, the group you will actually collect data from.
Your sampling method will determine how you recruit participants or obtain measurements for your study. To decide on a sampling method you will need to consider factors like the required sample size, accessibility of the sample, and time frame of the data collection.
Standardising procedures
If multiple researchers are involved, write a detailed manual to standardise data collection procedures in your study.
This means laying out specific step-by-step instructions so that everyone in your research team collects data in a consistent way – for example, by conducting experiments under the same conditions and using objective criteria to record and categorise observations.
This helps ensure the reliability of your data, and you can also use it to replicate the study in the future.
Creating a data management plan
Before beginning data collection, you should also decide how you will organise and store your data.
- If you are collecting data from people, you will likely need to anonymise and safeguard the data to prevent leaks of sensitive information (e.g. names or identity numbers).
- If you are collecting data via interviews or pencil-and-paper formats, you will need to perform transcriptions or data entry in systematic ways to minimise distortion.
- You can prevent loss of data by having an organisation system that is routinely backed up.
Finally, you can implement your chosen methods to measure or observe the variables you are interested in.
The closed-ended questions ask participants to rate their manager’s leadership skills on scales from 1 to 5. The data produced is numerical and can be statistically analysed for averages and patterns.
To ensure that high-quality data is recorded in a systematic way, here are some best practices:
- Record all relevant information as and when you obtain data. For example, note down whether or how lab equipment is recalibrated during an experimental study.
- Double-check manual data entry for errors.
- If you collect quantitative data, you can assess the reliability and validity to get an indication of your data quality.
Data collection is the systematic process by which observations or measurements are gathered in research. It is used in many different contexts by academics, governments, businesses, and other organisations.
When conducting research, collecting original data has significant advantages:
- You can tailor data collection to your specific research aims (e.g., understanding the needs of your consumers or user testing your website).
- You can control and standardise the process for high reliability and validity (e.g., choosing appropriate measurements and sampling methods ).
However, there are also some drawbacks: data collection can be time-consuming, labour-intensive, and expensive. In some cases, it’s more efficient to use secondary data that has already been collected by someone else, but the data might be less reliable.
Quantitative research deals with numbers and statistics, while qualitative research deals with words and meanings.
Quantitative methods allow you to test a hypothesis by systematically collecting and analysing data, while qualitative methods allow you to explore ideas and experiences in depth.
Reliability and validity are both about how well a method measures something:
- Reliability refers to the consistency of a measure (whether the results can be reproduced under the same conditions).
- Validity refers to the accuracy of a measure (whether the results really do represent what they are supposed to measure).
If you are doing experimental research , you also have to consider the internal and external validity of your experiment.
In mixed methods research , you use both qualitative and quantitative data collection and analysis methods to answer your research question .
Operationalisation means turning abstract conceptual ideas into measurable observations.
For example, the concept of social anxiety isn’t directly observable, but it can be operationally defined in terms of self-rating scores, behavioural avoidance of crowded places, or physical anxiety symptoms in social situations.
Before collecting data , it’s important to consider how you will operationalise the variables that you want to measure.
Cite this Scribbr article
If you want to cite this source, you can copy and paste the citation or click the ‘Cite this Scribbr article’ button to automatically add the citation to our free Reference Generator.
Bhandari, P. (2022, May 04). Data Collection Methods | Step-by-Step Guide & Examples. Scribbr. Retrieved 13 May 2024, from https://www.scribbr.co.uk/research-methods/data-collection-guide/
Is this article helpful?

Pritha Bhandari
Other students also liked, qualitative vs quantitative research | examples & methods, triangulation in research | guide, types, examples, what is a conceptual framework | tips & examples.
Cross-jurisdictional Data Transfer in Health Research: Stakeholder Perceptions on the Role of Law
- Original Paper
- Open access
- Published: 11 May 2024
Cite this article
You have full access to this open access article

- Hui Yun Chan ORCID: orcid.org/0000-0001-6084-0261 1 ,
- Hui Jin Toh 1 &
- Tamra Lysaght 1
31 Accesses
Explore all metrics
Large data-intensive health research programmes benefit from collaboration amongst researchers who may be located in different institutions and international contexts. However, complexities in navigating privacy frameworks and data protection laws across various jurisdictions pose significant challenges to researchers seeking to share or transfer data outside of institutional boundaries. Research on the awareness of data protection and privacy laws amongst stakeholders is limited. Our qualitative study, drawn from a larger project in Singapore, revealed insights into stakeholders’ perceptions of the role of law in cross-national health data research. Stakeholders in our study demonstrated a range of perceptions regarding the role of data protection law in governing the collection and transfer of health data for research. The main criticisms included inadequate legal protection to data and lack of uniformed data protection standards. Despite these criticisms, participants recognised the importance of data protection law in supporting cross-border data transfers and proposed measures to improve perceived limitations of existing laws. These measures include strengthening existing legal framework, establishing contractual agreements and imposing severe punishments for data misuse.
Avoid common mistakes on your manuscript.
Multiparty collaborations involving researchers from different institutions and countries are becoming increasingly common (Perrino et al. 2013 ; UNESCO 2017 ; Jean-Quartier et al. 2022 ; Kashyap 2022 ). This trend is supported by an availability of big data and data linkage technologies. Whilst most international collaborations are occurring between European countries and the US, these partnerships have now broadened to include countries located in the global south and Southeast Asia (Research, Innovation and Enterprise Secretariat 2020 ; Ministry of Health 2022 ; Smart Nation Singapore 2023 ). Singapore, a city-state in Southeast Asia (SEA), invests in local research and development initiatives and international collaborations (National Research Foundation 2023 ) with UK and Australia in the fields of human health, sustainability, trade, smart nation and digital economy (Kamalski and Plume 2013 ; White 2021 ). For these investments to succeed, effective data transfer across institutional and international borders is crucial to ensure that applicable data protection obligations are fulfilled, which contributes to generating trustworthiness in economic and research cooperations.
One of the key factors affecting cross-border data transfer is the presence of regulatory frameworks that researchers need to comply with. Research involving health data, including potentially sensitive health data, is broadly governed by laws relating to human biomedical research, data protection or privacy laws and research ethics guidelines (Scheibner et al. 2020 ; Xiang and Cai 2021 ). Although there are regulatory protections to address privacy concerns, health research involving many researchers in different countries has challenged existing privacy laws that may not adequately address risks arising from these activities (Kloss et al. 2018 ; McGraw and Mandl 2021 ). Yet, legislation regulating data protection has faced challenges in striking the right balance between protecting individuals from privacy harms without creating excessive burdens on research (Fears et al. 2014 ) that may generate public benefits.
The range of individuals who have interests in being protected from the harms of privacy and data breaches includes users, contributors and beneficiaries of health and research services. As their data are being used or repurposed for health research that is likely to benefit scientific advancements, whether in the short or long term, their perceptions regarding the role of law and the broader regulatory environment matter. This is because their continued support and willingness to participate in data sharing and transfer activities for health research have significant implications, which in turn affect the continuity of research activities that are beneficial to the population.
Empirical studies on stakeholder awareness of privacy and data protection laws have found mixed results. A study on the General Data Protection Regulation (GDPR) in 28 European countries (Rughinis et al. 2022 ) broadly suggests that awareness of the law generally correlates with the level of education, occupation and age. Another study comparing data protection awareness between UK and German populations showed a strong emphasis on data protection and security (Pleger et al. 2021 ). Recent research similarly focused on GDPR awareness amongst European study participants (Vukovic et al. 2022 ). These studies collectively provide largely European-centric perspectives and are potentially less relevant to address concerns that could arise in collaborations between SEA and European or American counterparts (Trade 2014 ).
Studies that are focused on regions in Europe, North America, and Oceania have political and cultural attributes that prioritise certain values and interests over others, most notably privacy and personal liberties. These priorities are often reflected broadly in the laws of these regions, including the GDPR and national data protection and privacy laws. Although these values are broadly recognised as important in societies, they may not necessarily be the primary focus in SEA. SEA countries often have different expressions of socio-cultural values and interests that may be understood as more communitarian compared to the individualism often expressed in Anglo-American countries.
Prior research from SEA has explored stakeholder perspectives from Cambodia and Vietnam on matters promoting data sharing across borders such as better understanding of disease epidemiology in public health emergencies (Liverani et al. 2018 ), healthcare advancements, and future personal health benefits (Kalkman et al. 2019 ). Obstacles and concerns to cross-border data sharing include differences in national structures and rules that govern data transfer, imbalances in capacities and power (Liverani et al. 2018 ), apprehension about privacy and security protections (Kalkman et al. 2019 ), potential breaches of confidentiality and misuse of data in controversial research or through exploitations (Majumder et al. 2016 ; Kalkman et al. 2019 ). Whilst providing valuable insights into factors influencing data sharing practises in SEA, these studies do not shed light on the extent of stakeholder awareness regarding the role of law in cross-border data sharing or transfer.
The lack of research on this topic could be due to the lack of resourcing capacity in the region, the perceived importance of data protection and privacy laws in the population or general acceptance of existing inadequate privacy laws. Exploring the level of awareness of the role of law in cross-border data transfer amongst stakeholders is essential to identify gaps in knowledge about the role of data protection law in international data transfer, rectify these gaps and prevent any continuity of undesirable practises.
In the context of Singapore, the Personal Data Protection Act 2012 (PDPA) broadly regulates the collection, use and disclosure of personal data with the aim of protecting the personal data of individuals whilst permitting their use for accepted purposes. This intends to create a balance between protecting data from misuse, sustaining population trust in organisations that collect and use their data and promote a trusted business environment for Singapore. The PDPA provides guidance for international data transfer under Sect. 26, supported further by Personal Data Protection Regulations 2021. The PDPA allows transfer of personal data outside Singapore if specific requirements are met to provide a comparable standard of data protection (Sect. 26). The Regulations provide further requirements on how these conditions could be met.
International collaborations raise questions about how data protection laws apply in cross-border data transfers, which are important considerations for a city-state like Singapore that is heavily invested in scientific developments. For example, under the PDPA, organisations that intend to transfer personal data abroad must ensure that the recipient is legally bound by the law, or under contractual obligations, corporate rules or any other types of agreement that would provide a comparable standard of data protection under the PDPA (e.g. if the recipient of personal data holds specific certification such as the Asia Pacific Economic Cooperation Cross Border Privacy Rules System). It is essential for individuals who are responsible for legal compliance to possess an accurate understanding of the applicable law and being aware of the implications to their work. Given the importance of data protection laws in governing the use, collection and transfer of health data across jurisdictional borders, it is important to understand stakeholders’ perceptions and attitudes towards the role of law in international collaborations involving cross-border data transfer.
This qualitative study explores stakeholder perceptions of the law within a health data research ecosystem in Singapore. This study was undertaken as the first stage of mixed methods research aimed at developing an ethical code to guide the collection, use and transfer of potentially sensitive health data in Singapore for researchers at the Future Health Technologies (FHT) programme (Lysaght et al. 2023 ). The FHT is an international research collaboration between the Singapore National Research Foundation and ETH-Zurich (The Swiss Federal Institute of Technology), which established the Singapore-ETH Centre (SEC) to improve health through digital health technologies.
Through pre-existing networks, we identified five groups of stakeholders representing data contributors, data generators, data resources, data facilitators and professional data users. From April to June 2022, we conducted semi-structured interviews with these stakeholders who were invited to participate via email. Written informed consent was obtained prior to the interview. Participants were given SGD$42 token of appreciation. Ethics approval for the protocol was obtained from the Institutional Review Board of the National University of Singapore (NUS-IRB-2022–46).
Interviews were conducted either in person or online according to participant preferences. The interview guide (see Annex 1) was developed with reference to findings from the internal mapping exercise conducted with FHT researchers and our prior studies (Lysaght et al. 2020 , 2021 ; Ong et al. 2021 ; Ballantyne et al. 2022 ). Topics are related to (i) health data sensitivity, (ii) international data sharing for research and (iii) regulation and governance. The topic guide was piloted with two senior researchers with experience in qualitative interviews and in health law and ethics. Prompts were used in the interviews to encourage the participants to consider the questions further and elaborate on their responses if necessary. The interviewers took field notes during the interviews and summarised their reflections with each other after each interview.
Interviews were audio-recorded and transcribed ad verbatim. Transcripts were pseudo-anonymised being transferred to NVivo 12 (QSR International) for analysis. Data were coded for qualitative thematic analysis (Miles and Huberman 1994 ) by the two study team members (HYC and HJT) independently, and codes were compared to identify any discrepancies. Meetings were then held between both members to resolve the discrepancies. The analysis occurred alongside the collection of interviews, and we stopped recruiting after reaching thematic saturation. Thematic saturation was reached when no new relevant themes and their relation to each other were identified (Corbin and Strauss 2014 ). The coding tree from our previous studies (Lysaght et al. 2020 ; Ong et al. 2021 ) was applied to the analysis and was built as new concepts and themes emerged. Codes were merged into broader themes and subthemes and presented to a senior researcher (TL) over several meetings. During these meetings, the senior researcher (TL) reviewed the interview data to ensure consistency in analysis across various themes. We used the Consolidated Criteria for Reporting Qualitative Research (COREQ) guidelines to report on the results.
Of the 37 potential stakeholders who were invited, 28 agreed to participate, 7 declined due to a lack of availability, and the remaining 2 did not respond. We recruited 28 stakeholders from the five groups: data contributors ( N = 5), data generators ( N = 8), data resources ( N = 4), data facilitators ( N = 6), and professional data users ( N = 5). Data contributors were represented by consumer or patient advocates and drawn from local patient support networks. Data generators included researchers working across the FHT programme in both Singapore and Switzerland. Data sources were comprised of hospital data controllers or data access guardians who have authority to grant or refuse permissions to requests to access data in their control. Data facilitators were regulators, industry stakeholders and in relation to the FHT programme, those in charge of establishing IT infrastructure and data security measures. Professional data users comprised of clinicians and industry partners of the FHT programme. Of the 28 interviews, 15 were held online, and the average duration of each interview was 82 min.
The main themes that emerged were related to adequacy perceptions towards local data protection law in safeguarding data privacy in cross-border data transfer and proposals for solutions to strengthen data protection law. Participants expressed a range of views regarding the PDPA, from the law being seen as adequate in some respects, such as establishing minimum standards of compliance, to expressions of ambiguity in terms of scope, coverage and definitions, and ineffectiveness in protecting consumers from service providers who collect vast amounts of unnecessary information that would have been contrary to the GDPR. More participants expressed inadequacies of current data protection law in protecting transferred or shared data. The views were classified under (a) adequacy of existing laws, (b) weaknesses of current laws and (c) limited awareness and accurate understanding of data protection laws.
Participants’ perceptions of the role of law were made within a broader context pertaining to collecting potentially sensitive information for health research and their experience with international data sharing for research through collaborations with local and overseas research institutions. Their attitudes towards the role of data protection laws, particularly the PDPA, are therefore expressed in connection with a perceived ease or difficulty with navigating the legal requirements and the strength and weaknesses of existing local data protection laws in protecting potentially sensitive information in health research.
Additionally, the views from participants that revealed a spectrum of adequacy perceptions towards local data protection law in safeguarding data privacy during cross-border transfer were made in response to broader probes related to the reputation of particular jurisdictions in data protection and the adequacy of laws existing in those jurisdictions in protecting personal data. Responses towards strengthening weaknesses of the PDPA are likely to result from an interest in improving transparency and accountability in the legal framework for collecting and transferring health information.
Spectrums of adequacy perceptions towards local data protection law in safeguarding data privacy in cross-border data transfer
Existing data protection laws are adequate in protecting shared data for research
Some participants from the professional data users’ group were satisfied with current data protection laws in Singapore in protecting shared data. Participants who expressed that the PDPA provides sufficient protection to data referred to the ease of conducting research under the PDPA. According to these participants, the PDPA has established a minimum standard of protection, resulting in a right balance between providing guidance for legal compliance and enabling the conduct of research.
‘…when an institution is dealing with data in Singapore, they are held accountable according to the Singaporeans regulations and law. Same when you do something in Switzerland, if you hold data, something goes wrong, you’re held accountable according to these laws’.—P17
Data protection laws are reactive, vague and provide limited protection and enforcement
Participants from primarily data generators and resources groups who criticised the PDPA expressed that its developments often lagged behind technological advancements, resulting in the inability to proactively prevent data breaches. Participants attributed the law’s reactivity to its complaint-based approach, citing a lack of awareness of the law in the population, hampering the process of raising complaints and resulting in weak legal enforcement. Additionally, these participants expressed their doubts about the PDPA’s clarity in definitional coverage and scope relating to identifiable and non-identifiable data, which permitted varying interpretations on the identifiability of the data, potentially leading to exploitation risks.
‘Our enforcement model is based purely on complaints. That means if there’s a data breach, and we complain about it, then they will be fined la. So the law is satisfactory for, is sufficient for people who are more “gung ho” (determined and enthusiastic in Hokkien), and who are willing to take risks, and the law is sufficient for people who are risk averse, because it does not, it does not give you a legal standard. It basically just says make sure there is no patient data that is re-identifiable. But it won’t tell you what that means exactly’.—P6 ‘… So I do think that a certain level, it affords a minimum level of protection for individuals, and if you read the legislation carefully right, it’s actually quite ambiguous in several areas, right’.—P7
Some participants from the data generator and data facilitator groups expressed that they were often required to provide more information than necessary in Singapore compared to other countries when signing up for services. This approach could potentially widen the opportunities for collected data to be unlawfully accessed. The lack of legal enforcement of the law was also cited as contributing to its weakness.
I’m getting spam calls spam texts all the time. And I’m wondering, how is that possible. And so makes me question whether, you know, your information is really protected and unregulated, you know. A lot of the time as well, you know, if you want to, if you want to find out about a service, you've got to provide all your personal details and not quite clear why. So that people give more information that they might not necessarily need. And that would be against GDPR. So I wonder, then whether the data protection policy here is sufficient enough.—P2
Participants expressed various views about the PDPA’s adequacy in protecting shared or transferred data. Amongst the participants who claimed that the PDPA does not provide sufficient data protection, they described the PDPA and related guidelines as lacking in clarity. However, participants who have prior experience collaborating with overseas partners and have transferred anonymised data did not consider the PDPA as problematic, as long as the data were not personally identifiable.
The researchers interviewed generally did not think it would be possible to reidentify an individual where anonymised data were used, although one participant cautioned that data can never be truly anonymised. When probed further, the participant responded that reverse engineering techniques could result in re-identification of individuals because of the existence of another ‘key’ to access identifiable information.
Limited awareness and accurate understanding about data protection and the PDPA
When asked about how data research is regulated in Singapore, all participants were aware of the PDPA. However, they demonstrated a range of awareness when probed about specific knowledge regarding the PDPA. Most participants were unable to articulate the application of the PDPA when probed. Amongst the minority from data resources group who expressed some familiarity with the PDPA, they expressed that Singaporeans generally lack awareness about the PDPA or have limited knowledge about the law.
‘So when I work with government agencies, or maybe even private sector clients, they might not be as knowledgeable about all these policies. Or maybe even government sector, they might not know it until some person from the compliance department come and say, Oh, actually, you need to do that’.—P25 ‘I know some basics (of the data protection law), whichever was told in SEC (Singapore-ETH Centre), upon joining in SEC how data is shared and what is the protocol. I think it is PDPA compliance. So those basic things I know but I don’t really know the fine print, if you ask me to dictate some term I will not know’.—P4
None of the participants mentioned the Public Sector (Governance) Act 2018, which applies to government sectors in matters relating to data protection by the public sector in Singapore. This law provides a framework for the government in matters relating to data sharing and disclosure of personal information for the purpose of delivering public services to the population. Some participants’ misconceptions about the PDPA emerged in several aspects. Examples ranged from the view that data transfer is not permissible at all under the PDPA, to the PDPA as a routine training course that formed part of employment onboarding processes without necessarily appreciating its importance and a lack of familiarity with PDPC decisions that applied the principles of the PDPA.
‘I believe our understanding has been that in this project, no data can leave Singapore basically. That is we’re working under that assumption, at least. Or at least that will require some permissions, I suppose… Otherwise, we would probably have just processed all the data on the computer clusters that we have at ETH, but we’re going through this painful process of setting up our own clusters of SECure servers at the NUS site, in order to be able to process all data within it in Singapore…’ — P23
Section 26 of the PDPA provides for legal mechanisms to transfer data outside of Singapore; however, none of the participants expressed an awareness of this legal provision or mentioned the possibility of data transfer under the PDPA. A few participants from data generators group expressed that researchers are ‘overregulated’ compared to the private sectors under the PDPA due to the necessity to comply with data protection laws and institutional review boards research requirements. These participants who are researchers and have sought ethics approval for research projects expressed that private commercial companies appeared to have greater ‘flexibility’ in gathering consumer data without burdensome regulatory oversight, unlike researchers. This perception could have arisen from the challenges researchers face in fulfilling administrative requirements when gathering research data from individuals. Research involving human subjects could include highly sensitive information, thus requiring greater oversight from ethics committee compared to private companies that are broadly collecting personal information in return for providing services. This difference in perception could have resulted in additional compliance ‘burdens’ being perceived as limitations of the law in supporting cross-jurisdictional data transfer.
‘And it should be the other area where it doesn’t seem to be regulated, that’s the area for me that they (the regulators) should be shutting down on. These, you know, these analytical companies that just take your information and use it, I find that quite dangerous, you know, companies getting huge advantages, economically as well. Whereas people doing research are typically extremely ethical about what they do. They’re very careful, they adhere to regulation, you know, and they look after the data properly, right? They don’t abuse it, they’re not making a profit out of it, there’s no conflict of interest’.—P21
Proposed solutions to strengthen the law
Participants were asked to identify potential non-legal measures that would allow health information sharing for research. In response, most of them identified the government as the responsible body to ensure that proper data collection and transfer procedures are in place. Some participants favoured government involvement in international research collaborations involving data transfer, such as forming public–private partnerships. Additionally, participants proposed that laws should be enforced with stronger accountability in response to perceived insufficiencies of the PDPA through various means such as contractual agreements, audits and selecting reputable research partners. Another suggested measure was transferring data only with a clear, necessary purpose (e.g. lack of local resources requiring overseas expertise) and strong public benefit.
‘So the use of the data is for the benefit of the project, or the service, or the individual or the society or whatever. And that remains the same and how, like it’s been used in a good way, right? But then if you’ve got all these data, and you’re like, oh, I can give this to someone else who can then go in and sell it for some other purpose to make a profit or to do something else with it, then that's not okay to me’.—P2
When asked about measures to resolve weaknesses of the law, participants proposed heavier fines for data misuse and breach, proactive monitoring to ensure adherence to data protection measures and penalties for failure to comply with protective measures. Some participants recommended strengthening current data protection laws and applicable policies. They referred to specific privacy-related standards such as Health Insurance Portability and Accountability Act (HIPAA) to improve the limitations of the PDPA.
‘International data sharing. I think what has always been an issue is the cross recognition, right? Of course, we have our PDPA. Europe has the GDPR and the US has the HIPAA. How the standards talk to each other? I think that’s why it’s a bit challenging in the Data Protection world to find an equivalence because it really depends on your social, what your society and culture beliefs about why it is sensitive’.—P26
One of the reasons cited was the benefit of referring to examples to assist people in implementing the PDPA concerning data collection and transfer, such as expectations of security measures. Examples cited include how to ensure data are secured (e.g. securely locked in metal cabinets), which would assure companies that they are properly securing their data. A further suggestion was creating a special commission to guide implementers in interpreting the law to assist with compliance.
Additionally, participants expressed complications in assessing the risks arising from sharing and transferring data and potential benefits from such activities. Although participants expressed concerns about risks from sharing and transfer (e.g. data breaches or security lapses), they reasoned that these risks were inevitable. What was important to them was the response to breaches. This reaction seemed to follow from their trust in the government as a trustworthy actor despite previous incidents of breaches. Participants who favoured this view expressed the need to strike a balance between the risks from transferring data overseas and benefits from research using transferred data.
‘From the healthcare angle, there is definite benefits to access the use of data. And even though in the past there are cases where data are abused with malicious intent, it is still acceptable risk’.—P20
Some researcher participants expressed the lack of standardised global data protection guidelines as complicating collaborations with international partners and challenging in implementing accountability when data breaches occur as the PDPA is not recognised outside of Singapore. Despite this view, they recognised the challenge in standardising laws and regulations on data privacy and protection across countries given differences in socio-cultural and political contexts.
Most participants expressed support for the use of legally binding contractual agreements (e.g. research collaboration agreements) with overseas partners to address accountability concerns. These participants explained that specific terms and conditions such as purpose of use, references to existing data protection policies and penalties for non-compliance could be included in these agreements. They added that contractual agreements provide the opportunity for parties to demonstrate their intention to comply with the agreement in the data sharing and transfer relationship.
This study is aimed at exploring the perceptions stakeholders have towards data protection laws and their impacts on research in Singapore. Previous studies have explored the perceptions of stakeholders on the role of data protection or the extent of awareness of privacy laws relating to health research. A study exploring stakeholder perspectives on the enablers and barriers of the GDPR for cross-border health data sharing in Europe (Vukovic et al. 2022 ) revealed positive perceptions towards the GDPR in facilitating the secondary use of health data in relation to user rights over their data, including existing laws governing data privacy and sharing. Barriers include perceived lengthy times for completing the process of data access, an increase in workload and differences with domestic legislations and differing interpretations to data access. These aspects were not reflected in our study, most likely due to differences between GDPR and PDPA requirements relating to how potentially sensitive data are treated under these rules.
Challenges with Implementing the PDPA in relation to Data Protection
In terms of stakeholders’ attitudes regarding how the PDPA has been implemented, there were some similarities with prior studies investigating public expectations about data protection laws. A study exploring public preferences for using identifiable data without consent in the light of differences in data protection laws in the US showed the need to align these laws with public preferences that are supportive of data use for research and public health. The study further revealed that researchers felt unreasonably burdened by uncertainties in implementation of laws governing the sharing of health data, as they were frequently ill-equipped to deal with this aspect of their data sharing activities (Genevieve et al. 2021 ).
Our analysis indicated similar attitudes amongst some participants, which revealed some uncertainties regarding the application of the law and an absence of alignments between participants’ expectation of the PDPA and its implementation relating to the scope of application and enforcement. This could have contributed to greater expressions of dissatisfactions about the efficacy of the PDPA. Participants from data generators group were more likely to be concerned about meeting the legal requirements surrounding data transfer, whilst data contributors were interested in understanding how their data could be protected under the law and implications arising from any likely harms associated with sharing these data for research. The former could be due to familiarity with seeking ethical approvals in their research and the necessity of ensuring compliance with current laws.
The divergences in priorities could potentially translate to distinct expectations regarding the law. It can be postulated that the views expressed by our participants were informed by their backgrounds ranging from patient support networks, scientists researching in digital health technologies, data controllers in hospitals, regulators, clinicians and industry representatives. The multidisciplinary nature of their perspectives could thus potentially influence their expectations about the PDPA and affect the way they apply the requirements of the PDPA or related privacy laws in their professional work.
The PDPA was initially introduced to implement the Do-Not-Call Registry (PDPC 2013 ), but has since developed to accommodate growing privacy concerns, evidenced by the publication of guidance notes and decisions by the Personal Data Protection Commission (PDPC). However, our participants appeared unaware of enforcement decisions against companies that breached PDPA obligations (PDPC 2023b ) or the availability of complaints for data breaches relating to data protection, do-not-call, unlicensed loans or online gambling and government data incident reporting platform (PDPC 2023c ). Although the publication of these decisions is intended to demonstrate that PDPA compliance is vital, it is unknown to what extent the populations are aware of these decisions and the implications to their lives. These decisions however assist commercial companies in meeting their obligations under the PDPA in relation to data collection, transfer and protection standards.
The participants’ dissatisfaction regarding the fines for PDPA breaches could be attributed to the focus on economic growth and innovations from international collaborations within Singapore, where data protection rules that are considered as obstructing health research might deter overseas institutions from collaborating with Singapore (BSA 2020 ). As a result, an ‘acceptable’ trade-off is a perceived ‘weaker’ protection level (or minimum protection standards) but meets the minimum protection standards that are conducive for commercial companies or scientific research. Policy makers in Singapore therefore need to navigate this trade-off carefully by considering economic growth, international collaborations, and the importance of safeguarding individuals’ privacy.
The limitations of the PDPA are seen by participants as an obstacle to genuine data protection. It could be valuable for public outreach activities (PDPC 2023a ) to widen PDPA awareness, including educating the public about ways to protect their personal data from being misused, consistent with one of the functions of the PDPC. The Personal Data Protection Commission (PDPC) plays an important role in a range of matters related to data protection, such as promoting awareness of data protection in Singapore, providing advisory and consultancy services relevant to data protection, enforcing the PDPA, conducting educational activities relating to data protection and managing cooperation with other organisations in areas of data protection. Perhaps this approach could assist in realigning public expectations about the PDPA and its implementation and to enable the public to acquire a better understanding of the PDPA and the role of the PDPC.
A majority of the participants who expressed dissatisfaction with the PDPA and its implementation governing the collection, use and transfer of potentially sensitive information remain interested in its role and proposed measures to strengthen the law. The recommendation to introduce higher fines for data breaches is consistent with recent amendments to the PDPA (Amendment) Act 2020. The change to the law under Sect. 48J(3) of the PDPA provides a higher imposition of penalties for data breaches from $1 million to 10% of the organisation’s annual turnover for organisations with over $10 million annual turnover and $1 million for all other cases.
Further, Sect. 48J(6) of the PDPA enables the PDPC to consider a range of matters in determining the amount of financial penalty such as the proportionality and efficacy of the financial penalties, or any previous non-compliance and the nature, gravity and duration of non-compliance. These amendments could be better received by the stakeholders, as it allows for fair consideration of individual cases rather than a one-size-fits-all approach. The amendments also reflected a recognition that data breaches are harmful to affected individuals and the penalties are intended to deter future breaches or seen to be acting justly for the harm caused to the affected people. Such a recognition may resonate better with stakeholders as it fosters a perception that the law is responsive to the concerns and rights of individuals whose data are compromised.
Overall, these amendments are likely to change participants’ perception of PDPA enforcement by positioning it as a more formidable and responsive framework. The emphasis on substantial penalties for non-compliance suggests a commitment to ensuring greater protection for individuals, which could instil confidence in the effectiveness of the PDPA in safeguarding personal data. However, the true impact will depend on how effectively these measures are implemented and enforced in practise.
Trade-off considerations between privacy and research benefits from cross-border data transfer appeared to be a persistent challenge (Sarabdeen and Moonesar 2018 ; Schmit et al. 2021 ). A study investigating stakeholder perspectives about the Protection of Personal Information Act 2013 in South Africa (Staunton et al. 2021 ) showed tensions between strengthening data protection and using personal data for care delivery and research, raising concerns that need to be addressed through increasing an understanding of the law in data protection, improving accountability and transparency in data use. Tensions that arose in the study reflected similar trade-off considerations as expressed by our study participants. This aspect further highlighted the difficulty in striking a balance between ensuring appropriate privacy protection for data that are subject to cross-border transfers and enabling international research to continue.
Comparisons between the PDPA, the GDPR and the HIPAA as Data Protection Standards
The influence of UK-US privacy frameworks and data protection approaches appeared to be high in some of our participants. This perception seemed to comport with studies on the GDPR, which was said to provide better data protection schemes compared to national laws (Gabel and Hickman 2019 ; Robichaud 2020 ; Pop 2023 ). This could be due to a greater uniformity within the European region in implementation and enforcement of the laws, supported by guidance to deal with any inconsistencies in application (Gabel and Hickman 2019 ; Saunders and Reifman 2021 ). References to European-centric privacy framework rather than domestic regional standards, such as the Asia Pacific regional standard to data protection that was introduced under the APEC Privacy Framework in 2016 (APEC Privacy Framework 2005 ), could be attributed to past or existing collaborations with research partners who are primarily located in European countries or the USA, thus necessitating compliance with these data protection standards.
Additionally, although comparisons were frequently made between the PDPA and the GDPR, the views varied depending upon participants’ experiences in applying PDPA and the context in which they are implemented. For instance, some participants from data generator group demonstrated inaccurate understanding about the PDPA whilst others had very limited awareness of the content other than the existence of the law. A lack of clear articulation of how the law is applied amongst some participants could have arisen from an environment where legal compliance with data protection is delegated to legal departments. The lack of knowledge likely influenced their views about how data are collected and transferred under the PDPA and the adequacy of the protection to their data. A report (National Board of Trade 2014 ) describing the knowledge of data protection regulations amongst companies in Sweden revealed a similar variation of awareness of the local data protection law. The report noted that whilst the surveyed companies were aware of the law, their interpretations differed resulting in a lack of accurate comprehension of how the rules implicate their business operations. This in turn could affect the safety of their customers’ personal data whilst operating their businesses.
Although several participants perceived the HIPAA’s articulation of privacy standards as more helpful compared to the PDPA, it is unclear whether they are aware of the lack of the HIPAA’s adequacy privacy standard (similar to the PDPA, which is not considered to have adequacy equivalence). Currently, only a limited number of jurisdictions are assessed as possessing privacy adequacy standards corresponding to GDPR standards (European Commission n.d ), such as Switzerland, New Zealand, the Republic of Korea and the US (but limited to commercial parties in the EU-US Data Privacy Framework). Whilst a survey in 2022 revealed an increase in awareness of data privacy laws in Singaporean consumers (SMEhorizon 2022 ), the findings were self-reported and they might have misconceptions about data privacy laws, similar to our participants.
Important implications for Singapore include the need for targeted awareness campaigns to address potential misconceptions and improve understanding of data privacy laws. This could include educational initiatives, communication strategies, and potentially regulatory measures to ensure that individuals and businesses are accurately informed about their rights and responsibilities under data protection laws. In addition, considering the global scope of data transfers and privacy standards, Singapore could consider exploring opportunities to better align its regulations with international frameworks to improve adequacy equivalence.
Our participants’ preference for contractual agreements in establishing obligations and expectations between research collaborators is aligned with current practises for cross-border research collaborations. Researchers perceived these agreements as flexible, adaptive and secure to protect the interests of the parties because they can negotiate the terms and conditions (Hallinan et al. 2021 ). Specific contractual terms covering data access or sharing may be included in separate data access/use agreements as safeguards for data sharing obligations (Mazor et al. 2017 ; Kalkman et al. 2019 ). Whilst these agreements are perceived as a form of accountability when data breaches occur, their efficacy may be limited by trans-territorial applications of the law relating to enforceability. There are other practical and legal limitations to ensuring accountability of third parties in the event of a breach such as determining appropriate compensations or responsible parties (Van Asbroeck 2019 ; OCED 2023 ). These limitations are consistent with participants’ expressed doubts about the extent of actual compliance with agreements.
Limitations and Future Research
This study has several limitations. First, most of the participants representing researchers from different nationalities may have limited knowledge and awareness of local data transfer or data protection laws. References to data protection laws are thus often made to more well-known frameworks such as the GDPR and the HIPAA. However, a group of participants comprising local expertise in data protection has provided a local understanding of their work experience in implementing data protection and transfer requirements.
Participants have a varied understanding and knowledge of the PDPA which presented a spectrum of views regarding its adequacy in data protection and data transfer for research. Their understanding of the law is highly influenced by their personal and work experience, which is generally accepted as not representative of the population. Further studies with a bigger sample of similar stakeholders may be able to validate this point. Nonetheless, the interviews have yielded rich responses from study participants that enabled the research team to have a clearer understanding of law-related awareness and perceptions in cross-jurisdictional health data transfers.
Additionally, as this study explored perspectives in Singapore with its unique culture and political environment, the results may not be generalisable to other countries but is sufficiently valuable to prompt discussions and further research on the relevance of data protection laws in facilitating cross-border data transfers. Further research could include evaluating the practical impact of the PDPA on facilitating or hindering cross-border health data transfers. In particular, it could involve assessing the effectiveness of the law in achieving its intended objectives, as well as identifying any challenges or gaps that may exist in the current regulatory framework. Another potential area of future research would be to conduct longitudinal studies to measure changes in awareness, perceptions and compliance with the PDPA over time. This can help policymakers anticipate and address emerging issues as the digital landscape and technologies evolve.
Our study showed that stakeholders perceived data protection laws as playing an important role in cross-border data transfer despite some inadequacies. Criticisms regarding the PDPA are often directed at the lack of clarity in its scope and definitions for researchers and the perceived lack of enforcement to penalise data misuse or breaches. However, some stakeholders’ perceptions of the law were influenced by an inaccurate understanding and misconception about the law. It is therefore important to increase awareness on data protection laws for stakeholders who are working in the health research ecosystems and the public generally. Attention could be drawn to highlighting the efforts of the PDPC in enforcing data protection laws through publication of decisions regarding data protection breaches by companies in Singapore. Participants advocated the need for strengthening enforcement on existing data protection laws, ensuring accountability of overseas collaborators through legally binding contractual agreements and imposing greater punishments for contravening contractual obligations relevant to data protection.
Data Availability
The data that support the findings of this study are available on request from the authors.
APEC. 2005. APEC privacy framework. Asia-Pacific Economic Cooporation ,December 2005. https://www.apec.org/publications/2005/12/apec-privacy-framework . Accessed 10 Apr 2023.
Ballantyne, Angela, Tamra Lysaght, Hui Jin Toh, Serene Ong, Andrew Lau, G. Owen Schaefer, Vicki Xafis, E Shyong Tai, Ainsley J. Newson, Stacy Carter, Chris Degeling, and Annette Braunack-Mayer. 2022. Sharing precision medicine data with private industry: outcomes of a citizens’ jury in Singapore. Big Data & Society 9: 20539517221108988. https://doi.org/10.1177/20539517221108988 .
Article Google Scholar
BSA. 2020. Singapore’s review of the PDPA and its opportunity for leadership in the region. DPO Connect , 31 August 2020. https://www.pdpc.gov.sg/-/media/Files/PDPC/DPO-Connect/August-20/Singapores-Review-of-the-PDPA-and-its-Opportunity-for-Leadership-in-the-Region . Accessed 12 Apr 2023.
Corbin, Juliet, and Anselm Strauss. 2014. Basics of qualitative research: techniques and procedures for developing grounded theory . Thousand Oaks, CA: SAGE.
Google Scholar
European Commission. n.d. Adequacy decision: how the EU determines if a non-EU country has an adequate level of data protection. https://commission.europa.eu/law/law-topic/data-protection/international-dimension-data-protection/adequacy-decisions_en#:~:text=The%20European%20Commission%20has%20so,commercial%20organisations%20participating%20in%20the . Accessed 2 Apr 2023.
Fears, R., H. Brand, R. Frackowiak, P.-P. Pastoret, R. Souhami, and B. Thompson. 2014. Data protection regulation and the promotion of health research: getting the balance right. QJM: An International Journal of Medicine 107: 3–5. https://doi.org/10.1093/qjmed/hct236 .
Gabel, Detlev, and Tim Hickman. 2019. GDPR guide to national implementation: a practical guide to national GDPR compliance requirements across the EEA. White & Case , 13 November 2019. https://www.whitecase.com/insight-our-thinking/gdpr-guide-national-implementation . Accessed 2 Apr 2023.
Genevieve, Lester Darryl, Andrea Martani, Thomas Perneger, Tenzin Wangmo, and Bernice Simone Elger. 2021. Systemic fairness for sharing health data: perspectives from Swiss stakeholders. Frontiers in Public Health 9: 669463. https://doi.org/10.3389/fpubh.2021.669463 .
Hallinan, Dara, Alexander Bernier, Anne Cambon-Thomsen, Francis P. Crawley, Diana Dimitrova, Claudia Bauzer Medeiros, Gustav Nilsonne, Simon Parker, Brian Pickering, and Stéphanie. Rennes. 2021. International transfers of personal data for health research following Schrems II: A problem in need of a solution. European Journal of Human Genetics - Nature 29: 1502–1509. https://doi.org/10.1038/s41431-021-00893-y .
Jean-Quartier, Claire, Miguel Rey Mazón, Mario Lovrić, and Sarah Stryeck. 2022. Collaborative data use between private and public stakeholders—a regional case study. Data 7: 20. https://doi.org/10.3390/data7020020 .
Kalkman, Shona, Johannes van Delden, Amitava Banerjee, Benoît Tyl, Menno Mostert, and Ghislaine van Thiel. 2019. Patients’ and public views and attitudes towards the sharing of health data for research: A narrative review of the empirical evidence. Journal of Medical Ethics 48: 3–13. https://doi.org/10.1136/medethics-2019-105651 .
Kamalski, Judith, and Andrew Plume 2013. Comparative benchmarking of European and US research collaboration and researcher mobility . Science Europe, and Elsevier. https://snowballmetrics.com/wp-content/uploads/2022/07/SE_and_Elsevier_Report_Final.pdf . Accessed 20 Mar 2023.
Kashyap, Karthik. 2022. Data collaboration between businesses to increase in the future. Spiceworks , 19 August 2022. https://www.spiceworks.com/tech/data-management/articles/data-collaboration-between-businesses-will-increase-in-the-future/ . Accessed 20 Mar 2023.
Kloss, Linda L., Melanie S. Brodnik, and Laurie A. Rinehart-Thompson. 2018. Access and disclosure of personal health information: A challenging privacy landscape in 2016–2018. Yearbook of Medical Informatics 27: 60–66. https://doi.org/10.1055/s-0038-1667071 .
Liverani, Marco, Srey Teng, Minh Sat Le, and Richard Coker. 2018. Sharing public health data and information across borders: lessons from Southeast Asia. Global Health 14: 1–12. https://doi.org/10.1186/s12992-018-0415-0 .
Lysaght, Tamra, Angela Ballantyne, Vicki Xafis, Serene Ong, Gerald Owen Schaefer, Jeffrey Min Than Ling, Ainsley J. Newson, Ing Wei Khor, and E. Shyong Tai. 2020. “Who is watching the watchdog?”: ethical perspectives of sharing health-related data for precision medicine in Singapore. BMC Medical Ethics 19: 118. https://doi.org/10.1186/s12910-020-00561-8 .
Lysaght, Tamra, Angela Ballantyne, Hui Jin Toh, Andrew Lau, Serene Ong, Owen Schaefer, Makoto Shiraishi, Willem van den Boom, Vicki Xafis, and E. Shyong Tai. 2021. Trust and trade-offs in sharing data for precision medicine: a national survey of Singapore. Journal of Personalized Medicine 11: 921. https://doi.org/10.3390/jpm11090921 .
Lysaght, Tamra, Hui Yun Chan, James Scheibner, Hui Jin Toh, and Bernadette Richards. 2023. An ethical code for collecting, using and transferring sensitive health data: outcomes of a modified Policy Delphi process in Singapore. BMC Medical Ethics 24: 78. https://doi.org/10.1186/s12910-023-00952-7 .
Majumder, Mary A., Robert Cook-Deegan, and Amy L. McGuire. 2016. Beyond our borders? Public resistance to global genomic data sharing. PLOS Biology 14: e2000206. https://doi.org/10.1371/journal.pbio.2000206 .
Mazor, Kathleen M., Allison Richards, Mia Gallagher, David E. Arterburn, Marsha A. Raebel, W. Benjamin Nowell, Jeffrey R. Curtis, Andrea R. Paolino, and Sengwee Toh. 2017. Stakeholders’ views on data sharing in multi-center studies. Journal of Comparative Effectiveness Research 6: 537–547. https://doi.org/10.2217/cer-2017-0009 .
McGraw, Deven, and Kenneth D. Mandl. 2021. Privacy protections to encourage use of health-relevant digital data in a learning health system. NPJ Digital Medicine 4: 2. https://doi.org/10.1038/s41746-020-00362-8 .
Miles, Matthew B., and A. Michael Huberman. 1994. Qualitative data analysis: an expanded sourcebook . Thousand Oaks, CA: SAGE.
Ministry of Health Singapore. 2022. Investing in enablers and infrastructure to support healthcare transformation. https://www.moh.gov.sg/news-highlights/details/investing-in-enablers-and-infrastructure-to-support-healthcare-transformation#:~:text=The%20Ministry%20of%20Health%20(MOH,future%2Dproof%20the%20healthcare%20system . Accessed 7 Apr 2023.
National Board of Trade. 2014. No transfer, no trade – the importance of cross-border data transfers for companies based in Sweden, 1st ed. https://unctad.org/system/files/non-official-document/dtl_ict4d2016c01_Kommerskollegium_en.pdf . Accessed 25 Apr 2024.
National Research Foundation Singapore. 2023. Corporate laboratories. https://www.nrf.gov.sg/programmes/corp-labs/ . Accessed 10 Apr 2023.
OCED. 2023. Risks and challenges of data access and sharing. https://www.oecd-ilibrary.org/sites/15c62f9c-en/index.html?itemId=/content/component/15c62f9c-en . Accessed 7 Apr 2023.
Ong, Serene, Jeffrey Ling, Angela Ballantyne, Tamra Lysaght, and Vicki Xafis. 2021. Perceptions of ‘precision’ and ‘personalised’ medicine in Singapore and associated ethical issues. Asian Bioethics Review 13: 179–194. https://doi.org/10.1007/s41649-021-00165-3 .
PDPC. 2013. Do not call registry to be launched by 2 January 2014. Personal data protection commission Singapore. Personal Data Protection Commission , 30 September 2023. https://www.pdpc.gov.sg/-/media/Files/PDPC/PDF-Files/Press-Room/2013/media-release---dnc-business-rules-(300913).pdf . Accessed 20 Mar 2023.
PDPC. 2023a. About us. https://www.pdpc.gov.sg/Who-We-Are/About-Us . Accessed 29 Mar 2023.
PDPC. 2023b. Commission’s decisions. https://www.pdpc.gov.sg/Commissions-Decisions . Accessed 29 Mar 2023.
PDPC. 2023c. Complaints and reviews. https://www.pdpc.gov.sg/complaints-and-reviews . Accessed 29 Mar 2023.
Perrino, Tatiana, George Howe, Anne Sperling, William Beardslee, Irwin Sandler, David Shern, Hilda Pantin, Sheila Kaupert, Nicole Cano, Gracelyn Cruden, Frank Bandiera, and C. Hendricks Brown. 2013. Advancing science through collaborative data sharing and synthesis. Perspectives on Psychological Science 8: 433–444. https://doi.org/10.1177/1745691613491579 .
Pleger, Lyn E., Katharina Guirguis, and Alexander Mertes. 2021. Making public concerns tangible: an empirical study of German and UK citizens’ perception of data protection and data security. Computers in Human Behavior 122: 106830. https://doi.org/10.1016/j.chb.2021.106830 .
Pop, Cristina. 2023. EU vs US: what are the differences between their data privacy laws? Endpoint Protector , 15 November 2023 . https://www.endpointprotector.com/blog/eu-vs-us-what-are-the-differences-between-their-data-privacy-laws/ . Accessed 25 Apr 2024.
Research, Innovation and Enterprise Secretariat. 2020. Research, innovation and enterprise 2025 plan . Singapore: National Research Foundation. https://file.go.gov.sg/rie-2025-handbook.pdf . Accessed 20 Mar 2023.
Robichaud, Francois. 2020. Comparing GDPR to other privacy laws. Borealis , 3 November 2020. https://www.boreal-is.com/blog/comparing-gdpr-to-other-privacy-laws/ . Accessed 19 Apr 2023.
Rughinis, Razvan, Cosima Rughiniș, Simona Nicoleta Vulpe, and Daniel Rosner. 2022. From social netizens to data citizens: variations of GDPR awareness in 28 European countries. Computer Law & Security Review 42: 105585. https://doi.org/10.1016/j.clsr.2021.105585 .
Sarabdeen, Jawahitha, and Immauel Moonesar. 2018. Privacy protection laws and public perception of data privacy: the case of Dubai e-health care services. Benchmarking: An International Journal 25: 1883–1902. https://doi.org/10.1108/BIJ-06-2017-0133 .
Saunders, David, and Suzanne Reifman. 2021. The case for a global data privacy adequacy standard. iapp , 27 April 2021. https://iapp.org/news/a/the-case-for-a-global-data-privacy-adequacy-standard/ . Accessed 29 Mar 2023.
Scheibner, James, Marcello Ienca, Sotiria Kechagia, Juan Ramon Troncoso-Pastoriza, Jean Louis Raisaro, Jean-Pierre Hubaux, Jacques Fellay, and Effy Vayena. 2020. Data protection and ethics requirements for multisite research with health data: a comparative examination of legislative governance frameworks and the role of data protection technologies. Journal of Law and the Biosciences 7: lsaa010. https://doi.org/10.1093/jlb/lsaa010 .
Schmit, Cason, Theodoros Giannouchos, Mahin Ramezani, Qi Zheng, Michael A. Morrisey, and Hye-Chung Kum. 2021. US privacy laws go against public preferences and impede public health and research: survey study. Journal of Medical Internet Research 23: e25266. https://doi.org/10.2196/25266 .
Smart Nation. 2023. Digital economy. https://www.smartnation.gov.sg/about-smart-nation/digital-economy/ . Accessed 20 Mar 2023.
SMEhorizon. 2022. Singapore consumers increasingly concerned over personal data. https://www.smehorizon.com/singapore-consumers-increasingly-concerned-over-personal-data/ . Accessed 20 Mar 2023.
Staunton, Clara, Kathrina Tschigg, and Gayle Sherman. 2021. Data protection, data management, and data sharing: Stakeholder perspectives on the protection of personal health information in South Africa. PLoS ONE 16: e0260341. https://doi.org/10.1371/journal.pone.0260341 .
UNESCO. 2017. International scientific collaboration has become a must, says report. https://www.unesco.org/en/articles/international-scientific-collaboration-has-become-must-says-report . Accessed 20 Mar 2023.
Van Asbroeck, Benoit. 2019. Big data & issues & opportunities: data sharing agreements. Bird & Bird , 31 March 2019. https://www.twobirds.com/en/insights/2019/global/big-data-and-issues-and-data-sharing-agreements . Accessed 20 Mar 2023.
Vukovic, Jakov, Damir Ivankovic, Claudia Habl, and Jelena Dimnjakovic. 2022. Enablers and barriers to the secondary use of health data in Europe: general data protection regulation perspective. Archives of Public Health 80: 115. https://doi.org/10.1186/s13690-022-00866-7 .
White, Karen. 2021. Publications output: U.S. trends and international comparisons. National Science Foundation, 28 October 2021. https://ncses.nsf.gov/pubs/nsb20214 . Accessed 20 Mar 2023.
Xiang, Dingyi, and Wei Cai. 2021. Privacy protection and secondary use of health data: strategies and methods. BioMed Research International 2021: 6967166. https://doi.org/10.1155/2021/6967166 .
Download references
Acknowledgements
The research was conducted at the Future Health Technologies programme which was established collaboratively between ETH Zurich and the National Research Foundation Singapore.
This research is supported by the National Research Foundation, Singapore under its Campus for Research Excellence and Technological Enterprise (CREATE) programme.
Author information
Authors and affiliations.
Centre for Biomedical Ethics, Yong Loo Lin School of Medicine, National University of Singapore, Singapore
Hui Yun Chan, Hui Jin Toh & Tamra Lysaght
You can also search for this author in PubMed Google Scholar
Corresponding author
Correspondence to Hui Yun Chan .
Ethics declarations
Ethical approval.
Ethics review for this study was obtained from the National University of Singapore – Institutional Review Board (IRB) (NUS-IRB-2022–46).
Consent to Participate
Informed consent was obtained from all participants. All methods were performed in accordance with relevant guidelines and regulations.
Consent for Publication
Not applicable.
Competing Interests
The authors declare no competing interests.
Additional information
Publisher's note.
Springer Nature remains neutral with regard to jurisdictional claims in published maps and institutional affiliations.
Interview Guide
Introduction and build rapport
Discuss participants’ professional background and experience with data research, if any
Health data sensitivity
Explore what types of health-related information participants would consider as ‘sensitive’ (e.g. medical records, clinical diagnoses, hospital stays, mental health status, pathology test results, and whole genome sequences) and contrast with potentially sensitive non-health information (e.g. financial/banking statements) and health data collected from mobile phone apps, wearable devices, IoTs, contact tracing, etc.
Probe on what makes certain types of health information ‘sensitive’ or not, if there are different levels of sensitivity, and if there should be greater levels of restrictions on who can access such information. If so, what sorts of restrictions?
International data sharing for research
Explore participants’ views about sensitive and non-sensitive health information being stored on cloud servers that are accessible to international collaborators at publicly funded research institutions/universities overseas and contrast with industry collaborators having access to the data or if the data are sold to commercial company that is developing medical products
Probe on whether the purpose of the research matters, or the country or region where the collaborators are located (e.g. the USA or EU country vs. China or North Korea), the prestige or visibility of the university/institution or company
Explore the conditions that participants would allow sensitive health information to be stored in Singapore and shared with international collaborators (e.g. IRB review, public benefit, removing personal identifiers, and informed consent)
Regulation and governance
Establish how much participants know about how data research is regulated in Singapore and whether they believe the regulations are sufficient for sensitive health information, however that is understood
Probe on matters of consent and understanding about the trade-offs in requiring informed consent every time data are shared/accessed with the added costs of recontacting participants multiple times and risks of reidentification
Identify any non-legal measures that could be put in place to allow sharing of health information for research (both locally and overseas) without needing to reconsent each time
Probe for the contours of what types of research is acceptable (e.g. disease specific and product development) or unacceptable (e.g. heritable genome editing and human cloning), and the sorts of public benefits that can be expected (or not) from research with patient health information
Probe on matters of transparency and accountability and what measures are reasonable and feasible for researchers to access patient health information without obtaining informed consent each time
Rights and permissions
Open Access This article is licensed under a Creative Commons Attribution 4.0 International License, which permits use, sharing, adaptation, distribution and reproduction in any medium or format, as long as you give appropriate credit to the original author(s) and the source, provide a link to the Creative Commons licence, and indicate if changes were made. The images or other third party material in this article are included in the article's Creative Commons licence, unless indicated otherwise in a credit line to the material. If material is not included in the article's Creative Commons licence and your intended use is not permitted by statutory regulation or exceeds the permitted use, you will need to obtain permission directly from the copyright holder. To view a copy of this licence, visit http://creativecommons.org/licenses/by/4.0/ .
Reprints and permissions
About this article
Chan, H.Y., Toh, H.J. & Lysaght, T. Cross-jurisdictional Data Transfer in Health Research: Stakeholder Perceptions on the Role of Law. ABR (2024). https://doi.org/10.1007/s41649-024-00283-8
Download citation
Received : 25 October 2023
Revised : 18 January 2024
Accepted : 07 February 2024
Published : 11 May 2024
DOI : https://doi.org/10.1007/s41649-024-00283-8
Share this article
Anyone you share the following link with will be able to read this content:
Sorry, a shareable link is not currently available for this article.
Provided by the Springer Nature SharedIt content-sharing initiative
- Data ethics
- Data protection law
- Data sharing
- Health data
- International data transfer
- Research ethics
- Find a journal
- Publish with us
- Track your research
- Open access
- Published: 09 May 2024
Examining the feasibility of assisted index case testing for HIV case-finding: a qualitative analysis of barriers and facilitators to implementation in Malawi
- Caroline J. Meek 1 , 2 ,
- Tiwonge E. Mbeya Munkhondya 3 ,
- Mtisunge Mphande 4 ,
- Tapiwa A. Tembo 4 ,
- Mike Chitani 4 ,
- Milenka Jean-Baptiste 2 ,
- Dhrutika Vansia 4 ,
- Caroline Kumbuyo 4 ,
- Jiayu Wang 2 ,
- Katherine R. Simon 4 ,
- Sarah E. Rutstein 5 ,
- Clare Barrington 2 ,
- Maria H. Kim 4 ,
- Vivian F. Go 2 &
- Nora E. Rosenberg 2
BMC Health Services Research volume 24 , Article number: 606 ( 2024 ) Cite this article
97 Accesses
Metrics details
Assisted index case testing (ICT), in which health care workers take an active role in referring at-risk contacts of people living with HIV for HIV testing services, has been widely recognized as an evidence-based intervention with high potential to increase status awareness in people living with HIV. While the available evidence from eastern and southern Africa suggests that assisted ICT can be an effective, efficient, cost-effective, acceptable, and low-risk strategy to implement in the region, it reveals that feasibility barriers to implementation exist. This study aims to inform the design of implementation strategies to mitigate these feasibility barriers by examining “assisting” health care workers’ experiences of how barriers manifest throughout the assisted ICT process, as well as their perceptions of potential opportunities to facilitate feasibility.
In-depth interviews were conducted with 26 lay health care workers delivering assisted ICT in Malawian health facilities. Interviews explored health care workers’ experiences counseling index clients and tracing these clients’ contacts, aiming to inform development of a blended learning implementation package. Transcripts were inductively analyzed using Dedoose coding software to identify and describe key factors influencing feasibility of assisted ICT. Analysis included multiple rounds of coding and iteration with the data collection team.
Participants reported a variety of barriers to feasibility of assisted index case testing implementation, including sensitivities around discussing ICT with clients, privacy concerns, limited time for assisted index case testing amid high workloads, poor quality contact information, and logistical obstacles to tracing. Participants also reported several health care worker characteristics that facilitate feasibility (knowledge, interpersonal skills, non-stigmatizing attitudes and behaviors, and a sense of purpose), as well as identified process improvements with the potential to mitigate barriers.
Conclusions
Maximizing assisted ICT’s potential to increase status awareness in people living with HIV requires equipping health care workers with effective training and support to address and overcome the many feasibility barriers that they face in implementation. Findings demonstrate the need for, as well as inform the development of, implementation strategies to mitigate barriers and promote facilitators to feasibility of assisted ICT.
Trial registration
NCT05343390. Date of registration: April 25, 2022.
Peer Review reports
Introduction
To streamline progress towards its goal of ending AIDS as a public health threat by 2030, the Joint United Nations Programme on HIV/AIDS (UNAIDS) launched a set of HIV testing and treatment targets [ 1 ]. Adopted by United Nations member states in June 2021, the targets call for 95% of all people living with HIV (PLHIV) to know their HIV status, 95% of all PLHIV to be accessing sustained antiretroviral therapy (ART), and 95% of all people receiving ART to achieve viral suppression by 2025 [ 2 ]. Eastern and southern Africa has seen promising regional progress towards these targets in recent years, and the region is approaching the first target related to status awareness in PLHIV- in 2022, 92% of PLHIV in the region were aware of their status [ 3 ]. However, several countries in the region lag behind [ 4 ], and as 2025 approaches, it is critical to scale up adoption of evidence-based interventions to sustain and accelerate progress.
Index case testing (ICT), which targets provision of HIV testing services (HTS) for sexual partners, biological children, and other contacts of known PLHIV (“index clients”), is a widely recognized evidence-based intervention used to identify PLHIV by streamlining testing efforts to populations most at risk [ 5 , 6 , 7 ]. Traditional approaches to ICT rely on passive referral, in which index clients invite their contacts for testing [ 5 ]. However, the World Health Organization (WHO) and the President’s Emergency Plan for HIV/AIDS Relief (PEPFAR) have both recommended assisted approaches to ICT [ 6 , 8 , 9 , 10 ], in which health care workers (HCWs) take an active role in referral of at-risk contacts for testing, due to evidence of improved effectiveness in identifying PLHIV compared to passive approaches [ 10 , 11 , 12 , 13 , 14 ]. As a result, there have been several efforts to scale assisted ICT throughout eastern and southern Africa in recent years [ 15 , 16 , 17 , 18 , 19 , 20 ]. In addition to evidence indicating that assisted ICT can be effective in increasing HIV testing and case-finding [ 16 , 17 , 21 , 22 , 23 , 24 ], implementation evidence [ 25 ] from the region suggests that assisted ICT can be an efficient [ 14 ], acceptable [ 5 , 13 , 15 , 18 , 20 , 21 , 26 ], cost-effective [ 27 ], and low-risk [ 21 , 22 , 24 , 28 , 29 ] strategy to promote PLHIV status awareness. However, the few studies that focus on feasibility, or the extent to which HCWs can successfully carry out assisted ICT [ 25 ], suggest that barriers exist to feasibility of effective implementation [ 18 , 19 , 20 , 30 , 31 , 32 ]. Developing informed implementation strategies to mitigate these barriers requires more detailed examination of how these barriers manifest throughout the assisted ICT process, as well as of potential opportunities to facilitate feasibility, from the perspective of the HCWs who are doing the “assisting”.
This qualitative analysis addresses this need for further detail by exploring “assisting” HCWs’ perspectives of factors that influence the feasibility of assisted ICT, with a unique focus on informing development of effective implementation strategies to best support assisted ICT delivery in the context of an implementation science trial in Malawi.
This study was conducted in the Machinga and Balaka districts of Malawi. Malawi is a country in southeastern Africa in which 7.1% of the population lives with HIV and 94% of PLHIV know their status [ 4 ]. Machinga and Balaka are two relatively densely populated districts in the southern region of Malawi [ 33 ] with HIV prevalence rates similar to the national average [ 34 ]. We selected Machinga and Balaka because they are prototypical of districts in Malawi implementing Ministry of Health programs with support from an implementing partner.
Malawi has a long-established passive ICT program, and in 2019 the country also adopted an assisted component, known as voluntary assisted partner notification, as part of its national HIV testing policy [ 32 ]. In Malawi, ICT is conducted through the following four methods, voluntarily selected by the index client: 1) passive referral, in which HCWs encourage the index client to refer partners for voluntary HTS, 2) contract referral, in which HCWs establish an informal ‘contract’ with index clients that agrees upon a date that the HCW can contact the contact clients if they have not yet presented for HTS; 3) provider referral, in which HCWs contact and offer voluntary HTS to contact clients; and 3) dual referral, in which HCWs accompany and provide support to index clients in disclosing their status and offering HTS to their partners [ 8 ].
While Malawi has one of the lowest rates of qualified clinical HCWs globally (< 5 clinicians per 100,000 people) [ 35 ], the country has a strong track record of shifting HTS tasks to lay HCWs, who have been informally trained to perform certain health care delivery functions but do not have a formal professional/para-professional certification or tertiary education degree, in order to mitigate this limited medical workforce capacity [ 32 , 36 ]. In Malawi, lay HCW roles include HIV Diagnostic Assistants (who are primarily responsible for HIV testing and counseling, including index case counseling) and community health workers (who are responsible for a wider variety of tasks, including index case counseling and contact tracing) [ 32 ]. Non-governmental organization implementing partners, such as the Tingathe Program, play a critical role in harnessing Malawian lay HCW capacity to rapidly and efficiently scale up HTS, including assisted ICT [ 32 , 37 , 38 , 39 ].
Study design
Data for this analysis were collected as part of formative research for a two-arm cluster randomized control trial examining a blended learning implementation package as a strategy for building HCW capacity in assisted ICT [ 40 ]. Earlier work [ 32 ] established the theoretical basis for testing the blended learning implementation package, which combines individual asynchronous modules with synchronous small-group interactive sessions to enhance training and foster continuous quality improvement. The formative research presented in this paper aimed to further explore factors influencing feasibility of the assisted ICT from the perspective of HCWs in order to inform development of the blended learning implementation package.
Prior to the start of the trial (October-December 2021), the research team conducted 26 in-depth interviews (IDIs) with lay HCWs at 14 of the 34 facilities included in the parent trial. We purposively selected different types of facilities (hospitals, health centers, and dispensaries) in both districts and from both randomization arms, as this served as a qualitative baseline for a randomized trial. Within these facilities, we worked with facility supervisors to purposively select HCWs who were actively engaged in Malawi’s ICT program from the larger sample of HCWs eligible for the parent trial (had to be at least 18 years old, employed full-time at one of the health facilities included in the parent trial, and involved in counseling index clients and/or tracing their contacts). The parent trial enrolled 306 HCWs, who were primarily staff hired by Tingathe Program to support facilities implementing Malawi’s national HIV program.
Data collection
IDIs were conducted by three trained Malawian interviewers in a private setting using a semi-structured guide. IDIs were conducted over the phone when possible ( n = 18) or in-person at sites with limited phone service ( n = 8). The semi-structured guide was developed for this study through a series of rigorous, iterative discussions among the research team (Additional file 1 ). The questions used for this analysis were a subset of a larger interview. The interview guide questions for this analysis explored HCWs’ experiences with assisted ICT, including barriers and facilitators to implementation. Probing separately about the processes of counseling index clients and tracing their contacts, interviewers asked questions such as “What is the first thing that comes to mind when you think of counseling index clients/tracing contacts?”, “What aspects do you [like/not like] about…?” and “What do your colleagues say about…?”. When appropriate, interviewers probed further about how specific factors mentioned by the participant facilitate or impede the ICT implementation experience.
The IDIs lasted from 60–90 min and were conducted in Chichewa, a local language in Malawi. Eleven audio recordings were transcribed verbatim in Chichewa before being translated into English and 15 recordings were directly translated and transcribed into English. Interviewers summarized each IDI after it was completed, and these summaries were discussed with the research team routinely.
Data analysis
The research team first reviewed all of the interview summaries individually and then met multiple times to discuss initial observations, refining the research question and scope of analysis. A US-based analyst (CJM) with training in qualitative analysis used an inductive approach to develop a codebook, deriving broad codes from the implementation factors mentioned by participants throughout their interviews. Along with focused examination of the transcripts, she consulted team members who had conducted the IDIs with questions or clarifications. CJM regularly met with Malawian team members (TEMM, MM, TAT) who possess the contextual expertise necessary to verify and enhance meaning. She used the Dedoose (2019) web application to engage in multiple rounds of coding, starting with codes representing broad implementation factors and then further refining the codebook as needed to capture the nuanced manifestations of these barriers and facilitators. Throughout codebook development and refinement, the analyst engaged in memoing to track first impressions, thought processes, and coding decisions. The analyst presented the codebook and multiple rounds of draft results to the research team. All transcripts and applied codes were also reviewed in detail by additional team members (MJB, DV). Additional refinements to the codebook and results interpretations were iteratively made based on team feedback.
Ethical clearance
Ethical clearance was provided by UNC’s IRB, Malawi’s National Health Sciences Research Committee, and the Baylor College of Medicine IRB. Written informed consent was obtained from all participants in the main study and interviewers confirmed verbal consent before starting the IDIs.
Participant characteristics are described in Table 1 below.
Factors influencing feasibility of assisted ICT: barriers and facilitators
Participants described a variety of barriers and facilitators to feasibility of assisted ICT, manifesting across the index client counseling and contact client tracing phases of the implementation process. Identified barriers included sensitivities around discussing ICT with clients, privacy concerns, limited time for ICT amid high workloads, poor quality contact information, and logistical obstacles to tracing. In addition to these barriers, participants also described several HCW characteristics that facilitated feasibility: ICT knowledge, interpersonal skills, positive attitudes towards clients, and sense of purpose. Barriers and facilitators are mapped to the ICT process in Fig. 1 and described in greater detail in further sections.
Conceptual diagram mapping feasibility barriers and facilitators to the ICT process
Feasibility barriers
Sensitivities around discussing ict with clients.
Participants described ICT as a highly sensitive topic to approach with clients. Many expressed a feeling of uncertainty around how open index clients will be to sharing information about their contacts, as well as how contacts will react when approached for HTS. When asked about difficult aspects of counseling index clients, many HCWs mentioned clients’ hesitance or declination to participate in assisted ICT and share their contacts. Further, several HCWs mentioned that some index clients would provide false contact information. These index client behaviors were often attributed to confidentiality concerns, fear of unwanted status disclosure, and fear of the resulting implications of status disclosure: “They behave that way because they think you will be telling other people about their status…they also think that since you know it means their life is done, you will be looking at them differently .” Populations commonly identified as particularly likely to hesitate, refuse, or provide false information included youth (described as “ shy ” “ thinking they know a lot ” and “ difficult to reveal their contacts ”) and newly diagnosed clients (“it may be hard for them to accept [their HIV diagnosis]” ). One participant suggested that efforts to pair index clients with same-sex HCWs could make them more comfortable to discuss their contacts.
When asked about the first things that come to mind when starting to trace contacts, many participants discussed wondering how they will be received by the contact and preparing themselves to approach the contact. When conducting provider or contract referral, HCWs described a variety of challenging reactions that can occur when they approach a contact for HTS- including delay or refusal of testing, excessive questioning about the identity of the index client who referred them for testing, and even anger or aggression. Particularly mentioned in the context of male clients, these kinds of reactions can lead to stress and uncertain next steps for HCWs: “I was very tensed up. I was wondering to myself what was going to happen…he was talking with anger.”
Participants also noted the unique sensitivities inherent in conducting dual referral and interacting with sexual partners of index clients, explaining that HIV disclosure can create acute conflict in couples due to perceived blame and assumptions of infidelity. They recounted these scenarios as particularly difficult to navigate, with high stakes that require high-quality counseling skills: “sometimes if you do not have good counseling the marriage happens to get to an end.” . Some participants discussed concern about index client risk of intimate partner violence (IPV) upon partner disclosure: “they think that if they go home and [disclose their HIV status], the marriage will end right there, or for some getting to a point of [being] beaten.”
Privacy concerns
Participants also reported that clients highly value privacy, which can be difficult to secure throughout the ICT process. In the facility, while participants largely indicated that counseling index clients was much more successful when conducted in a private area, many reported limited availability of private counseling space. One participant described this challenge: “ if I’m counseling an index client and people keep coming into the room…this compromises the whole thing because the client becomes uncomfortable in the end.” Some HCWs mentioned working around this issue through use of screens, “do-not-disturb” signs, outdoor spots, and tents.
Participants also noted maintaining privacy as a challenge when tracing contact clients in the field, as they sometimes find clients in a situation that is not conducive to private conversations. One participant described: “ we get to the house and find that there are 4, 5 people with our [contact client]…it doesn’t go well…That is a mission gone wrong. ” Participants also noted that HCWs are also often easily recognizable in the community due to their bikes and cars, which exacerbates the risk of compromising privacy. To address privacy challenges in the community, participants reported strategies to increase discretion, including dressing to blend in with the community, preparing an alternate reason to be looking for the client, and offering HTS to multiple people or households to avoid singling out one person.
Limited time for ICT amid high workloads
Some participants indicated that strained staffing capacity leads HCWs to have to perform multiple roles, expressing challenges in balancing their ICT work with their other tasks. As one participant described, “Sometimes it is found that you are assigned a task here at the hospital to screen anyone who comes for blood testing, but you are also supposed to follow up [with] the contacts the same day- so it becomes a problem…you fail to follow up [with] the contacts.” Some also described being the only, or one of few staff responsible for ICT: “You’re doing this work alone, so you can see that it is a big task to do it single-handedly.” The need to counsel each index client individually, as a result of confidentiality concerns, further increases workload for the limited staff assigned to this work. Further, HCWs often described contact tracing in the field as time-consuming and physically taxing, which leaves them less time and energy for counseling. Many HCWs noted the need to hire more staff dedicated to ICT work.
High workloads also resulted in shorter appointments and less time to counsel index clients, which participants reported limits the opportunity for rapport that facilitates openness or probes for detailed information about sexual partners. Participants emphasized the importance of having enough time to meaningfully engage with index clients: “For counseling you cannot have a limit to say, ‘I will talk to him for 5 min only.’ …That is not counseling then. You are supposed to stay up until…you feel that this [person] is fulfilled.” . In addition, high workload can reduce the capacity of HCWs to deliver quality counseling: “So you find that as you go along with the counseling, you can do better with the first three clients but the rest, you are tired and you do short cuts.”
High workloads also lead to longer queues, which may deter clients from coming into the clinic or cause them to leave before receiving services: “Sometimes because of shortage of staff, it happens that you have been assigned a certain task that you were supposed to do but at the same time there are clients who were supposed to be counseled. As a result, because you spent more time on the other task as a result you lose out some of the clients because you find that they have gone.” In response to long queues, several participants described ‘fast-tracking’ contact clients who come in for HTS in effort to maximize case-finding by prioritizing those who have been identified as at risk of HIV.
Poor quality contact information
Participants repeatedly discussed the importance of eliciting accurate information about a person’s sexual partners, including where, when, and how to best contact them. As one participant said, “ Once the index has given us the wrong information then everything cannot work, it becomes wrong…if he gives us full information [with] the right details then everything becomes successful and happens without a problem. ” Adequate information is a critical component of the ICT process, and incorrect or incomplete information delays or prevents communication with contact clients.
Inadequate information, which can include incorrect or incomplete names, phone numbers, physical addresses, and contextual details, can arise from a variety of scenarios. Most participants mentioned index clients providing incorrect information as a concern. This occurred either intentionally to avoid disclosure or unintentionally if information was not known. Poor quality contact information also results from insufficient probing and poor documentation, which is often exacerbated by aforementioned HCW time and energy constraints. In one participant’s words, “The person who has enlisted the contact…is the key person who can make sure that our tracing is made easy.” Participants noted the pivotal role of the original HCW who first interacts with the index client in not only eliciting correct locator information but also eliciting detailed contextual information. For example, details about a contact client’s profession are helpful to trace the client at a time when they will likely be at home. Other helpful information included nicknames, HIV testing history, and notes about confidentiality concerns.
Logistical obstacles to tracing
Some contact clients are reached by phone whereas others must be physically traced in the community. Some participants reported difficulty with tracing via phone, frequently citing network problems and lack of sufficient airtime allocated by the facility. Participants also reported that some clients were unreachable by phone, necessitating physical tracing. Physically tracing a contact client requires a larger investment of resources than phone tracing, especially when the client lives at a far distance from the clinic. Participants frequently discussed having to travel far distances to reach contact clients, an issue some saw as exacerbated by people who travel to clinics at far distances due to privacy concerns.
While most participants reported walking or biking to reach contact clients in the community, some mentioned using a motorcycle or Tingathe vehicle. However, access to vehicles is often limited and these transportation methods require additional expenses for fuel. Walking or biking was also reported to expose HCWs to inclement weather, including hot or rainy seasons, and potential safety risks such as violence.
Participants reported that traveling far distances can be physically taxing and time-consuming, sometimes rendering them too tired or busy to attend to other tasks. Frequent travel influenced HCW morale, particularly when a tracing effort did not result in successfully recruiting a contact client. Participants frequently described this perception of wasted time and energy as “ painful ”, with the level of distress often portrayed as increasing with the distance travelled. As one HCW said, “You [can] find out that he gave a false address. That is painful because it means you have done nothing for the person, you travelled for nothing.”
HCWs described multiple approaches used to strategically allocate limited resources for long distances. These approaches included waiting to physically trace until there are multiple clients in a particular area, reserving vehicle use for longer trips, and coordinating across HCWs to map out contact client locations. HCWs also mentioned provision of rain gear and sun protection to mitigate uncomfortable travel. Another approach involved allocating contact tracing to HCWs based in the same communities as the contact clients.
Feasibility facilitators
Hcw knowledge about ict.
Participants reported that HCWs with a thorough understanding of ICT’s rationale and purpose can facilitate client openness. Clients were more likely to engage with HCWs about assisted ICT if they understood the benefits to themselves and their loved ones. One HCW stated, “If the person understands why we need the information, they will give us accurate information.”
Participants also discussed the value of deep HCW familiarity with ICT procedures and processes, particularly regarding screening clients for IPV and choosing referral method. One participant described the importance of clearly explaining various referral methods to clients: “So…people come and choose the method they like…when you explain things clearly it is like the index client is free to choose a method which the contact can use for testing”. Thorough knowledge of available referral methods allows HCWs to actively engage with index clients to discuss strategies to refer contacts in a way that fits their unique confidentiality needs, which was framed as particularly important when IPV is identified as a concern. Multiple participants suggested the use of flipcharts or videos, saying these would save limited HCW time and energy, fill information gaps, and provide clients with a visual aid to supplement the counseling. Others suggested recurring opportunities for training, to continuously “refresh” their ICT knowledge in order to facilitate implementation.
HCW interpersonal skills
In addition, HCWs’ ability to navigate sensitive conversations about HIV was noted as a key facilitator of successful implementation. Interpersonal skills were mentioned as mitigating the role’s day-to-day uncertainty by preparing HCWs to engage with clients, especially newly diagnosed clients: “ I need to counsel them skillfully so that they understand what I mean regardless that they have just tested positive for HIV.”
When discussing strategies to build HCW skills in counseling index clients and tracing contact clients, participants suggested establishing regular opportunities to discuss challenges and share approaches to address these challenges: “ I think that there should be much effort on the [HCWs] doing [ICT]. For example, what do I mean, they should be having a meeting with the facility people to ask what challenges are you facing and how can we end them?”. Another participant further elaborated, saying “We should be able to share experiences with our [colleagues] so that we can all learn from one another. And also, there are other people who are really brilliant at their job. Those people ought to come visit us and see how we are doing. That is very motivating.”
HCW non-stigmatizing attitudes and behaviors
Participants also highlighted the role of empathy and non-judgement in building trust with clients: “ Put yourself in that other person’s shoes. In so doing, the counseling session goes well. Understanding that person, that what is happening to them can also happen to you. ”. Participants viewed trust-building as critical to facilitating client comfort and openness: “if they trust you enough, they will give you the right information.” Further, participants associated HCW assurance of confidentiality with promoting trust and greater information sharing: “ Also assuring them on the issue of confidentiality because confidentiality is a paramount. If there will not be confidentiality then the clients will not reveal.”
HCW sense of purpose
Lastly, several participants reported that a sense of purpose and desire to help people motivated them to overcome the challenges of delivering assisted ICT. One participant said, “ Some of these jobs are a ministry. Counseling is not easy. You just need to tell yourself that you are there to help that person. ” Many seemed to take comfort in the knowledge that their labors, however taxing, would ultimately allow people to know their status, take control of their health, and prevent the spread of HIV. Participants framed the sense of fulfillment from successful ICT implementation as a mitigating factor amidst challenges: “ If [the contact client] has accepted it then I feel that mostly I have achieved the aim of being in the health field…that is why it is appealing to me ”.
Participants described a variety of barriers to assisted ICT implementation, including sensitivities around discussing ICT with clients, privacy concerns, limited time for ICT amid high workloads, poor quality contact information, and logistical obstacles to tracing. These barriers manifested across each step of the process of counseling index clients and tracing contacts. However, participants also identified HCW characteristics and process improvements that can mitigate these barriers.
Further, participants’ descriptions of the assisted ICT process revealed the intimately interconnected nature of factors that influence feasibility of assisted ICT. Sensitivities around HIV, privacy limitations, time constraints, and HCW characteristics all contribute to the extent to which counseling index clients elicits adequate information to facilitate contact tracing. Information quality has implications for HCW capacity, as inadequate information can lead to wasted resources, including HCW time and energy, on contact tracing. The opportunity cost of wasted efforts, which increases as the distance from which the contact client lives from the clinic increases, depletes HCW morale. The resulting acceleration of burnout, which is already fueled by busy workloads and the inherent uncertainty of day-to-day ICT work, further impairs HCW capacity to effectively engage in quality counseling that elicits adequate information from index clients. This interconnectedness suggests that efforts to mitigate barriers at any step of the assisted ICT process may have the potential to ripple across the whole process.
Participants’ descriptions of client confidentiality and privacy concerns, as well as fear of consequences of disclosure, align with previous studies that emphasize stigma as a key barrier to assisted ICT [ 15 , 18 , 19 , 20 , 30 , 31 ] and the overall HIV testing and treatment cascade [ 41 ]. Our findings suggest that anticipated stigma, or the fear of discrimination upon disclosure [ 42 ], drives several key barriers to feasibility of assisted ICT implementation. Previous studies also highlight the key role of HCWs in mitigating barriers related to anticipated stigma; noting the key role of HCW ICT knowledge, interpersonal skills, and non-stigmatizing attitudes/behaviors in securing informed consent from clients for ICT, tailoring the referral strategy to minimize risk to client confidentiality and safety, building trust and rapport with the client, and eliciting accurate contact information from index clients to facilitate contact tracing [ 18 , 19 , 20 , 30 ].
Our findings also reflect previous evidence of logistical challenges related to limited time, space, and resources that can present barriers to feasibility for HCWs [ 18 , 19 , 20 , 30 , 31 ]. Participants in the current study described these logistical challenges as perpetuating HCW burnout, making it harder for them to engage in effective counseling. Cumulative evidence of barriers across different settings (further validated by this study) suggests that assisted ICT implementation may pose greater burden on HCWs than previously thought [ 7 ]. However, our findings also suggest that strategic investment in targeted implementation strategies has the potential to help overcome these feasibility barriers.
In our own work, these findings affirmed the rationale for and informed the development of the blended learning implementation package tested in our trial [ 40 , 43 ]. Findings indicated the need for evidence-based training and support to promote HCW capacity to foster facilitating characteristics. Participants discussed the value of "refresher" opportunities in building knowledge, as well as the value of learning from other’s experiences. The blended learning implementation package balances both needs by providing time for HCWs to master ICT knowledge and skills with a combination of asynchronous, digitally delivered content (which allows for continuous review as a "refresher") and in-person sessions (which allow for sharing, practicing, and feedback). Our findings also highlight the value of flexible referral methods that align with the client’s needs, so our training content includes a detailed description of each referral method process. Further, our training content emphasizes client-centered, non-judgmental counseling as our findings add to cumulative evidence of stigma as a key barrier to assisted ICT implementation [ 41 ].
In addition, participants frequently mentioned informal workarounds currently in use to mitigate barriers or offered up ideas for potential solutions to try. Our blended learning implementation package streamlines these problem-solving processes by offering monthly continuous quality improvement sessions at each facility in our enhanced arm. These sessions allow for structured time to discuss identified barriers, share ideas to mitigate barriers, and develop solutions for sustained process improvement tailored to their specific setting. Initial focus areas for continuous quality improvement discussions include use of space, staffing, allocation of airtime and vehicles, and documentation, which were identified as barriers to feasibility in the current study.
Our study provides a uniquely in-depth examination of HCWs’ experiences implementing assisted ICT, exploring how barriers can manifest and interact with each other at each step of the process to hinder successful implementation. Further, our study has a highly actionable focus on informing development of implementation strategies to support HCWs implementing assisted ICT. Our study also has limitations. Firstly, while our sole focus on HCWs allowed for deeper exploration of assisted ICT from the perspective of those actually implementing it on the ground, this meant that our analysis did not include perspectives of index or contact clients. In addition, we did not conduct sub-group analyses as interpretation of results would be limited by our small sample size.
Assisted ICT has been widely recognized as an evidence-based intervention with high promise to increase PLHIV status awareness [ 5 , 6 , 7 , 10 , 12 , 13 , 14 , 15 , 16 , 17 , 18 , 19 , 20 , 21 , 23 , 24 , 26 , 27 , 28 , 29 ], which is important as countries in eastern and southern Africa strive to reach global UNAIDS targets. Study findings support cumulative evidence that HCWs face a variety of feasibility barriers to assisted ICT implementation in the region; further, the study’s uniquely in-depth focus on the experiences of those doing the “assisting” enhances understanding of how these barriers manifest and informs the development of implementation strategies to mitigate these barriers. Maximizing assisted ICT’s potential to increase HIV testing requires equipping HCWs with effective training and support to address and overcome the many feasibility barriers they face in implementation. Findings demonstrate the need for, as well as inform the development of, implementation strategies to mitigate barriers and promote facilitators to feasibility of assisted ICT.
Availability of data and materials
Qualitative data on which this analysis is based, as well as data collection materials and codebooks, are available from the last author upon reasonable request. The interview guide is included as an additional file.
Abbreviations
Acquired Immunodeficiency Syndrome
Antiretroviral Therapy
Health Care Worker
Human Immunodeficiency Virus
HIV Testing Services
Index Case Testing
In-Depth Interview
Intimate Partner Violence
Institutional Review Board
President’s Emergency Plan for HIV/AIDS Relief
People Living With HIV
Joint United Nations Programme on HIV/AIDS
World Health Organization
UNAIDS. Prevailing against pandemics by putting people at the centre. Geneva: UNAIDS; 2020.
Google Scholar
Frescura L, Godfrey-Faussett P, Feizzadeh AA, El-Sadr W, Syarif O, Ghys PD, et al. Achieving the 95 95 95 targets for all: A pathway to ending AIDS. PLoS One. 2022;17(8):e0272405.
Article CAS PubMed PubMed Central Google Scholar
UNAIDS. UNAIDS global AIDS update 2023: The path that ends AIDS. New York: United Nations; 2023.
Book Google Scholar
UNAIDS. UNAIDS data 2023. Geneva: Joint United Nations Programme on HIV/AIDS; 2023.
Kahabuka C, Plotkin M, Christensen A, Brown C, Njozi M, Kisendi R, et al. Addressing the first 90: A highly effective partner notification approach reaches previously undiagnosed sexual partners in Tanzania. AIDS Behav. 2017;21(8):2551–60.
Article PubMed PubMed Central Google Scholar
Lasry A, Medley A, Behel S, Mujawar MI, Cain M, Diekman ST, et al. Scaling up testing for human immunodeficiency virus infection among contacts of index patients - 20 countries, 2016–2018. MMWR Morb Mortal Wkly Rep. 2019;68(21):474–7.
Onovo A, Kalaiwo A, Agweye A, Emmanuel G, Keiser O. Diagnosis and case finding according to key partner risk populations of people living with HIV in Nigeria: A retrospective analysis of community-led index partner testing services. EClinicalMedicine. 2022;43:101265.
World Health Organization (WHO). Guidelines on HIV self-testing and partner notification : supplement to Consolidated guidelines on HIV testing services. 2016. https://apps.who.int/iris/bitstream/handle/10665/251655/9789241549868-eng.pdf?sequence=1 . Accessed 19 Apr 2024.
Watts H. Why PEPFAR is going all in on partner notification services. 2019. https://programme.ias2019.org/PAGMaterial/PPT/1934_117/Why%20PEPFAR%20is%20all%20in%20for%20PNS%2007192019%20rev.pptx . Accessed 19 Apr 2024.
Dalal S, Johnson C, Fonner V, Kennedy CE, Siegfried N, Figueroa C, et al. Improving HIV test uptake and case finding with assisted partner notification services. AIDS. 2017;31(13):1867–76.
Article PubMed Google Scholar
Mathews C, Coetzee N, Zwarenstein M, Lombard C, Guttmacher S, Oxman A, et al. A systematic review of strategies for partner notification for sexually transmitted diseases, including HIV/AIDS. Int J STD AIDS. 2002;13(5):285–300.
Hogben M, McNally T, McPheeters M, Hutchinson AB. The effectiveness of HIV partner counseling and referral services in increasing identification of HIV-positive individuals a systematic review. Am J Prev Med. 2007;33(2 Suppl):S89-100.
Brown LB, Miller WC, Kamanga G, Nyirenda N, Mmodzi P, Pettifor A, et al. HIV partner notification is effective and feasible in sub-Saharan Africa: opportunities for HIV treatment and prevention. J Acquir Immune Defic Syndr. 2011;56(5):437–42.
Sharma M, Ying R, Tarr G, Barnabas R. Systematic review and meta-analysis of community and facility-based HIV testing to address linkage to care gaps in sub-Saharan Africa. Nature. 2015;528(7580):S77-85.
Edosa M, Merdassa E, Turi E. Acceptance of index case HIV testing and its associated factors among HIV/AIDS Clients on ART follow-up in West Ethiopia: A multi-centered facility-based cross-sectional study. HIV AIDS (Auckl). 2022;14:451–60.
PubMed Google Scholar
Williams D, MacKellar D, Dlamini M, Byrd J, Dube L, Mndzebele P, et al. HIV testing and ART initiation among partners, family members, and high-risk associates of index clients participating in the CommLink linkage case management program, Eswatini, 2016–2018. PLoS ONE. 2021;16(12):e0261605.
Remera E, Nsanzimana S, Chammartin F, Semakula M, Rwibasira GN, Malamba SS, et al. Brief report: Active HIV case finding in the city of Kigali, Rwanda: Assessment of voluntary assisted partner notification modalities to detect undiagnosed HIV infections. J Acquir Immune Defic Syndr. 2022;89(4):423–7.
Article CAS PubMed Google Scholar
Quinn C, Nakyanjo N, Ddaaki W, Burke VM, Hutchinson N, Kagaayi J, et al. HIV partner notification values and preferences among sex workers, fishermen, and mainland community members in Rakai, Uganda: A qualitative study. AIDS Behav. 2018;22(10):3407–16.
Monroe-Wise A, Maingi Mutiti P, Kimani H, Moraa H, Bukusi DE, Farquhar C. Assisted partner notification services for patients receiving HIV care and treatment in an HIV clinic in Nairobi, Kenya: a qualitative assessment of barriers and opportunities for scale-up. J Int AIDS Soc. 2019;22 Suppl 3(Suppl Suppl 3):e25315.
Liu W, Wamuti BM, Owuor M, Lagat H, Kariithi E, Obong’o C, et al. “It is a process” - a qualitative evaluation of provider acceptability of HIV assisted partner services in western Kenya: experiences, challenges, and facilitators. BMC Health Serv Res. 2022;22(1):616.
Myers RS, Feldacker C, Cesar F, Paredes Z, Augusto G, Muluana C, et al. Acceptability and effectiveness of assisted human immunodeficiency virus partner services in Mozambique: Results from a pilot program in a public. Urban Clinic Sex Transm Dis. 2016;43(11):690–5.
Rosenberg NE, Mtande TK, Saidi F, Stanley C, Jere E, Paile L, et al. Recruiting male partners for couple HIV testing and counselling in Malawi’s option B+ programme: an unblinded randomised controlled trial. Lancet HIV. 2015;2(11):e483–91.
Mahachi N, Muchedzi A, Tafuma TA, Mawora P, Kariuki L, Semo BW, et al. Sustained high HIV case-finding through index testing and partner notification services: experiences from three provinces in Zimbabwe. J Int AIDS Soc. 2019;22 Suppl 3(Suppl Suppl 3):e25321.
Cherutich P, Golden MR, Wamuti B, Richardson BA, Asbjornsdottir KH, Otieno FA, et al. Assisted partner services for HIV in Kenya: a cluster randomised controlled trial. Lancet HIV. 2017;4(2):e74–82.
Proctor E, Silmere H, Raghavan R, Hovmand P, Aarons G, Bunger A, et al. Outcomes for implementation research: conceptual distinctions, measurement challenges, and research agenda. Adm Policy Ment Health. 2011;38(2):65–76.
Kamanga G, Brown L, Jawati P, Chiwanda D, Nyirenda N. Maximizing HIV partner notification opportunities for index patients and their sexual partners in Malawi. Malawi Med J. 2015;27(4):140–4.
Rutstein SE, Brown LB, Biddle AK, Wheeler SB, Kamanga G, Mmodzi P, et al. Cost-effectiveness of provider-based HIV partner notification in urban Malawi. Health Policy Plan. 2014;29(1):115–26.
Wamuti BM, Welty T, Nambu W, Chimoun FT, Shields R, Golden MR, et al. Low risk of social harms in an HIV assisted partner services programme in Cameroon. J Int AIDS Soc. 2019;22 Suppl 3(Suppl Suppl 3):e25308.
Henley C, Forgwei G, Welty T, Golden M, Adimora A, Shields R, et al. Scale-up and case-finding effectiveness of an HIV partner services program in Cameroon: an innovative HIV prevention intervention for developing countries. Sex Transm Dis. 2013;40(12):909–14.
Klabbers RE, Muwonge TR, Ayikobua E, Izizinga D, Bassett IV, Kambugu A, et al. Health worker perspectives on barriers and facilitators of assisted partner notification for HIV for refugees and Ugandan nationals: A mixed methods study in West Nile Uganda. AIDS Behav. 2021;25(10):3206–22.
Mugisha N, Tirera F, Coulibaly-Kouyate N, Aguie W, He Y, Kemper K, et al. Implementation process and challenges of index testing in Cote d’Ivoire from healthcare workers’ perspectives. PLoS One. 2023;18(2):e0280623.
Rosenberg NE, Tembo TA, Simon KR, Mollan K, Rutstein SE, Mwapasa V, et al. Development of a Blended Learning Approach to Delivering HIV-Assisted Contact Tracing in Malawi: Applied Theory and Formative Research. JMIR Form Res. 2022;6(4):e32899.
Government of Malawi National Statistical Office. 2018 Malawi population and housing census : main report. 2019. https://malawi.unfpa.org/sites/default/files/resource-pdf/2018%20Malawi%20Population%20and%20Housing%20Census%20Main%20Report%20%281%29.pdf . Accessed 19 April 2024.
Wolock TM, Flaxman S, Chimpandule T, Mbiriyawanda S, Jahn A, Nyirenda R, et al. Subnational HIV incidence trends in Malawi: large, heterogeneous declines across space. medRxiv (PREPRINT). 2023. https://www.ncbi.nlm.nih.gov/pmc/articles/PMC9915821/ . Accessed 19 Apr 2024.
World Health Organization (WHO). Medical doctors (per 10,000). 2020. https://www.who.int/data/gho/data/indicators/indicator-details/GHO/medical-doctors-(per-10-000-population . Accessed 19 Apr 2024.
Flick RJ, Simon KR, Nyirenda R, Namachapa K, Hosseinipour MC, Schooley A, et al. The HIV diagnostic assistant: early findings from a novel HIV testing cadre in Malawi. AIDS. 2019;33(7):1215–24.
Kim MH, Ahmed S, Buck WC, Preidis GA, Hosseinipour MC, Bhalakia A, et al. The Tingathe programme: a pilot intervention using community health workers to create a continuum of care in the prevention of mother to child transmission of HIV (PMTCT) cascade of services in Malawi. J Int AIDS Soc. 2012;15(Suppl 2):17389.
Simon KR, Hartig M, Abrams EJ, Wetzel E, Ahmed S, Chester E, et al. The Tingathe Surge: a multi-strategy approach to accelerate HIV case finding in Malawi. Public Health Action. 2019;9(3):128–34.
Ahmed S, Kim MH, Dave AC, Sabelli R, Kanjelo K, Preidis GA, et al. Improved identification and enrolment into care of HIV-exposed and -infected infants and children following a community health worker intervention in Lilongwe, Malawi. J Int AIDS Soc. 2015;18(1):19305.
Tembo TA, Mollan K, Simon K, Rutstein S, Chitani MJ, Saha PT, et al. Does a blended learning implementation package enhance HIV index case testing in Malawi? A protocol for a cluster randomised controlled trial. BMJ Open. 2024;14(1):e077706.
Nyblade L, Mingkwan P, Stockton MA. Stigma reduction: an essential ingredient to ending AIDS by 2030. Lancet HIV. 2021;8(2):e106–13.
Nyblade L, Stockton M, Nyato D, Wamoyi J. Perceived, anticipated and experienced stigma: exploring manifestations and implications for young people’s sexual and reproductive health and access to care in North-Western Tanzania. Cult Health Sex. 2017;19(10):1092–107.
Tembo TA, Simon KR, Kim MH, Chikoti C, Huffstetler HE, Ahmed S, et al. Pilot-Testing a Blended Learning Package for Health Care Workers to Improve Index Testing Services in Southern Malawi: An Implementation Science Study. J Acquir Immune Defic Syndr. 2021;88(5):470–6.
Download references
Acknowledgements
We are grateful to the Malawian health care workers who shared their experiences through in-depth interviews, as well as to the study team members in Malawi and the United States for their contributions.
Research reported in this publication was funded by the National Institutes of Health (R01 MH124526) with support from the University of North Carolina at Chapel Hill Center for AIDS Research (P30 AI50410) and the Fogarty International Center of the National Institutes of Health (D43 TW010060 and R01 MH115793-04). The funders had no role in trial design, data collection and analysis, decision to publish or preparation of the manuscript.
Author information
Authors and affiliations.
RTI International, Research Triangle Park, NC, USA
Caroline J. Meek
Gillings School of Global Public Health, University of North Carolina at Chapel Hill, Chapel Hill, NC, USA
Caroline J. Meek, Milenka Jean-Baptiste, Jiayu Wang, Clare Barrington, Vivian F. Go & Nora E. Rosenberg
Kamuzu University of Health Sciences, Blantyre, Malawi
Tiwonge E. Mbeya Munkhondya
Baylor College of Medicine Children’s Foundation, Lilongwe, Malawi
Mtisunge Mphande, Tapiwa A. Tembo, Mike Chitani, Dhrutika Vansia, Caroline Kumbuyo, Katherine R. Simon & Maria H. Kim
Department of Medicine, Division of Infectious Diseases, University of North Carolina at Chapel Hill, Chapel Hill, NC, USA
Sarah E. Rutstein
You can also search for this author in PubMed Google Scholar
Contributions
TAT, KRS, SER, MHK, VFG, and NER contributed to overall study conceptualization, with CJM, CB, and NER leading conceptualization of the analysis presented in this study. Material preparation and data collection were performed by TEMM, MM, TAT, MC, and CK. Analysis was led by CJM with support from MJB and DV. The first draft of the manuscript was written by CJM with consultation from NER, TEMM, MM, TAT, MJB, and DV. JW provided quantitative analysis support for participant characteristics. All authors commented on previous versions of the manuscript. All authors read and approved the final manuscript.
Corresponding author
Correspondence to Caroline J. Meek .
Ethics declarations
Ethics approval and consent to participate.
Ethical clearance was provided by the Malawi National Health Science Research Committee (NHSRC; #20/06/2566), University of North Carolina Institution Review Board (UNC IRB; #20–1810) and the Baylor College of Medicine institutional review board (Baylor IRB; H-48800). The procedures used in this study adhere to the tenets of the Declaration of Helsinki. Written informed consent for participation was obtained from all study participants prior to enrollment in the parent study. Interviewers also engaged in informal verbal discussion of consent immediately ahead of in-depth interviews.
Consent for publication
Not applicable. No identifying information is included in the manuscript.
Competing interests
The authors declare no competing interests.
Additional information
Publisher’s note.
Springer Nature remains neutral with regard to jurisdictional claims in published maps and institutional affiliations.
Supplementary Information
Supplementary material 1., rights and permissions.
Open Access This article is licensed under a Creative Commons Attribution 4.0 International License, which permits use, sharing, adaptation, distribution and reproduction in any medium or format, as long as you give appropriate credit to the original author(s) and the source, provide a link to the Creative Commons licence, and indicate if changes were made. The images or other third party material in this article are included in the article's Creative Commons licence, unless indicated otherwise in a credit line to the material. If material is not included in the article's Creative Commons licence and your intended use is not permitted by statutory regulation or exceeds the permitted use, you will need to obtain permission directly from the copyright holder. To view a copy of this licence, visit http://creativecommons.org/licenses/by/4.0/ . The Creative Commons Public Domain Dedication waiver ( http://creativecommons.org/publicdomain/zero/1.0/ ) applies to the data made available in this article, unless otherwise stated in a credit line to the data.
Reprints and permissions
About this article
Cite this article.
Meek, C.J., Munkhondya, T.E.M., Mphande, M. et al. Examining the feasibility of assisted index case testing for HIV case-finding: a qualitative analysis of barriers and facilitators to implementation in Malawi. BMC Health Serv Res 24 , 606 (2024). https://doi.org/10.1186/s12913-024-10988-z
Download citation
Received : 31 August 2023
Accepted : 12 April 2024
Published : 09 May 2024
DOI : https://doi.org/10.1186/s12913-024-10988-z
Share this article
Anyone you share the following link with will be able to read this content:
Sorry, a shareable link is not currently available for this article.
Provided by the Springer Nature SharedIt content-sharing initiative
- HIV testing and counseling
- Index case testing
- Assisted partner notification services
- Implementation science
- Health care workers
BMC Health Services Research
ISSN: 1472-6963
- General enquiries: [email protected]

COMMENTS
The case study is a data collection method in which in-depth descriptive information. about specific entities, or cases, is collected, organized, interpreted, and presented in a. narrative format ...
In a case study research, multiple methods of data collection are used, as it involves an in-depth study of a phenomenon. It must be noted, as highlighted by Yin , a case study is not a method of data collection, rather is a research strategy or design to study a social unit.
The data collection method should be selected based on the research questions and the nature of the case study phenomenon. Analyze the data: The data collected from the case study should be analyzed using various techniques, such as content analysis, thematic analysis, or grounded theory.
While many books and articles guide various qualitative research methods and analyses, there is currently no concise resource that explains and differentiates among the most common qualitative approaches. We believe novice qualitative researchers, students planning the design of a qualitative study or taking an introductory qualitative research course, and faculty teaching such courses can ...
Although case studies have been discussed extensively in the literature, little has been written about the specific steps one may use to conduct case study research effectively (Gagnon, 2010; Hancock & Algozzine, 2016).Baskarada (2014) also emphasized the need to have a succinct guideline that can be practically followed as it is actually tough to execute a case study well in practice.
A case study protocol outlines the procedures and general rules to be followed during the case study. This includes the data collection methods to be used, the sources of data, and the procedures for analysis. Having a detailed case study protocol ensures consistency and reliability in the study.
the case study method favors the collection of data in natural settings, compared with relying on "derived" data (Bromley, 1986, p. 23)—for example, responses to a researcher's instruments in an experiment or responses to questionnaires in a survey.
Revised on November 20, 2023. A case study is a detailed study of a specific subject, such as a person, group, place, event, organization, or phenomenon. Case studies are commonly used in social, educational, clinical, and business research. A case study research design usually involves qualitative methods, but quantitative methods are ...
One of the main stages in a research study is data collection that enables the researcher to find answers to research questions. Data collection is the process of collecting data aiming to gain insights ... It means the findings of case studies can be used just for the same issues as the general patterns for different studies. Qualitative ...
Data Collection | Definition, Methods & Examples. Published on June 5, 2020 by Pritha Bhandari.Revised on June 21, 2023. Data collection is a systematic process of gathering observations or measurements. Whether you are performing research for business, governmental or academic purposes, data collection allows you to gain first-hand knowledge and original insights into your research problem.
A case study is a research approach that is used to generate an in-depth, multi-faceted understanding of a complex issue in its real-life context. It is an established research design that is used extensively in a wide variety of disciplines, particularly in the social sciences. A case study can be defined in a variety of ways (Table 5 ), the ...
A Case study is: An in-depth research design that primarily uses a qualitative methodology but sometimes includes quantitative methodology. Used to examine an identifiable problem confirmed through research. Used to investigate an individual, group of people, organization, or event. Used to mostly answer "how" and "why" questions.
The article describes the decisions that need to be made in planning case study research and then presents examples of how case studies can be used in several performance technology applications. The advantages and disadvantages of case studies as a data collection method are discussed and guidelines for their use are given. Volume 46, Issue 7.
The article describes the decisions that need to be made in planning case study research and then presents examples of how case studies can be used in several performance technology applications. The advantages and disadvantages of case studies as a data collection method are discussed and guidelines for their use are given. References ( ). . ...
Case study research is typically extensive; it draws on multiple methods of data collection and involves multiple data sources. The researcher begins by identifying a specific case or set of cases to be studied. Each case is an entity that is described within certain parameters, such as a specific time frame, place, event, and process.
Case study research in information systems. Graeme Shanks, Nargiza Bekmamedova, in Research Methods (Second Edition), 2018. Data collection and analysis. Case study research typically includes multiple data collection techniques and data are collected from multiple sources. Data collection techniques include interviews, observations (direct and participant), questionnaires, and relevant ...
The study aims to explore the case study method with the formation of questions, data collection procedures and analysis, followed by how and on which position the saturation is achieved in developing a centralized Shariah governance framework for Islamic banks in Bangladesh.,Using purposive and snowball sampling procedures, data have been ...
1. Case study is a research strategy, and not just a method/technique/process of data collection. 2. A case study involves a detailed study of the concerned unit of analysis within its natural setting. A de-contextualised study has no relevance in a case study research. 3. Since an in-depth study is conducted, a case study research allows the ...
This paper introduces a dataset developed to measure the impact of archival and data curation decisions on data reuse. The dataset describes 10,605 social science research datasets, their curation ...
Aim To investigate the potential of embedded research in bridging the gap between research evidence and its implementation in public health practice. Methods Using a case study methodology, semi-structured interviews were conducted with 4 embedded researchers, 9 public health practitioners, and 4 other stakeholders (2 teachers and 2 students) across four case study sites. Sites and individuals ...
The following data collection methods were used to enable triangulation of data and form the case studies. Professional learning days - Teachers and some school leaders attended four sessions across a calendar year conducted in 2021 to upskill teachers in contemporary thinking about child-centred transitions, FoK and FoI, engaging families ...
Step 2: Choose your data collection method. Based on the data you want to collect, decide which method is best suited for your research. Experimental research is primarily a quantitative method. Interviews, focus groups, and ethnographies are qualitative methods. Surveys, observations, archival research, and secondary data collection can be ...
A case study is a research approach that is used to generate an in-depth, multi-faceted understanding of a complex issue in its real-life context. It is an established research design that is used extensively in a wide variety of disciplines, particularly in the social sciences. A case study can be defined in a variety of ways (Table.
This qualitative study explores stakeholder perceptions of the law within a health data research ecosystem in Singapore. This study was undertaken as the first stage of mixed methods research aimed at developing an ethical code to guide the collection, use and transfer of potentially sensitive health data in Singapore for researchers at the Future Health Technologies (FHT) programme (Lysaght ...
The data collection sources will be used to track what was done for the various activities along with the student's attendance in the case where they may miss an instruction time which can affect the research and students progress. Research for implementing articulation strategies within the instruction is limited.
The data used in this study comes from a research project examining the sustainability of a community health insurance (CHI) scheme in Ethiopia. ... MH led the conceptualization and design of the study, data collection, data management, data analysis, and report writing. The author read and approved the final manuscript.
Background Assisted index case testing (ICT), in which health care workers take an active role in referring at-risk contacts of people living with HIV for HIV testing services, has been widely recognized as an evidence-based intervention with high potential to increase status awareness in people living with HIV. While the available evidence from eastern and southern Africa suggests that ...