

Java, Java, Java: Object-Oriented Problem Solving
(4 reviews)
Ralph Morelli, Trinity College
Ralph Walde, Trinity College
Copyright Year: 2016
Publisher: Ralph Morelli, Ralph Walde
Language: English
Formats Available
Conditions of use.
Learn more about reviews.
Reviewed by Onyeka Emebo, Assistant Professor, Virginia Tech on 12/28/21
The text adequately addresses areas under Object Oriented Programming using Java as a Programming Language for Introduction to Computer Science courses. It gently introduces basic concepts in computer, objects and java using problem solving... read more
Comprehensiveness rating: 5 see less
The text adequately addresses areas under Object Oriented Programming using Java as a Programming Language for Introduction to Computer Science courses. It gently introduces basic concepts in computer, objects and java using problem solving approaches and gradually builds up to more advanced Java technologies in such a simplified manner that can be easily understood. The text also provides a table of content at the beginning and a summary of points for each chapter with exercises.
Content Accuracy rating: 4
The text content is accurate, without errors and unbiased. There is however some links that needs to be updated.
Relevance/Longevity rating: 4
While the field of computer science with particular emphasis to programming as it relates to this text is constantly evolving, the approach taken by this text to teach the essentials is likely to persist. The code, tested in Java 8, should continue to work with new Java releases. Updates to the text can be done easily by the way it has been written.
Clarity rating: 5
The text is written in a clear and easy to understand manner. The objectives, explanations, examples and exercises are clear and easy to follow. The codes are well commented to aid readability.
Consistency rating: 4
The text is highly consistent in both structure and terminology. It starts each chapter with objectives and outline and concludes with summary, exercises and solutions. However, some codes within the chapters are put in figures while others are not, this could be confusing.
Modularity rating: 5
The text is divided in 17 chapters (0 - 16) and 8 appendices (A – H). Each chapter is further divided into sections and subsections. This breakdown makes it easier for instructors to apportion sections to students at different times within the course.
Organization/Structure/Flow rating: 5
The text is organized in a manner that is logical and it flows well from section to section. The structure makes navigation from chapter to chapter easier.
Interface rating: 3
I reviewed the PDF version and it looks good to a large extent. The links in the table of contents are working properly. There are clickable links within the text to different figures, sections, such as appendices, and external websites. However, there are some issues with some figure titles, e.g., figure 12, 1.10, 2.7, 2.10, 2.14, etc. are cut off. Some hyperlinks for some figures missing e.g., figure 2.8 and some figures don’t have titles.
Grammatical Errors rating: 5
The text contains no grammatical errors.
Cultural Relevance rating: 5
The text is culturally neutral. The examples are unbiased in the way it has been presented.
Reviewed by Ghaith Husari, Assistant Professor, East Tennessee State University on 4/17/20
This book covers Object-Oriented Programming under JAVA. It introduces the concepts of object-oriented programming and they are used for problem-solving. This book covers all the relevant areas of Object-Oriented Programming under Java. Also, it... read more
This book covers Object-Oriented Programming under JAVA. It introduces the concepts of object-oriented programming and they are used for problem-solving. This book covers all the relevant areas of Object-Oriented Programming under Java. Also, it covers more advanced topics such as socket programming and algorithms.
Content Accuracy rating: 5
The Object-Oriented concepts and implementation example shown in code samples are accurate and easy to learn as the code samples are aligned with the concept being discussed. Some links and URLs are out-dated but they have little to no impact on student learning. However, I would add a note that says "some of the links and URLs might not up-to-date. However, they can be found using search engines if necessary"
Programming languages get updated regularly to include new and easier functions to use. While it is impossible for a textbook to include every function, this textbook provides a great learning opportunity that allows students to build the muscle to be able to learn more about Java online. When it comes to Object-Oriented concepts, the book is extremely relevant and up-to-date
The textbook is very easy to understand and the code sample is both clear (code readability) and relevant.
Consistency rating: 5
The text and the terms it contains are consistent. Also, the textbook follows a consistent theme.
The textbook chapters are divided into sections and subsections that are shown also in the table of contents which can be used to visit each section.
The textbook consists of seventeen chapters that are organized in a logical manner. The more general concepts such as problem-solving and programing are placed at the beginning, then the chapters introduce the discuss Object-Oriented Programming come after the general chapters. The more advanced topics such as socket programming and data structures and algorithms come towards the end. This made a lot of sense to me.
Interface rating: 5
The textbook is easily accessible online and it can be downloaded to open with Edge or Adobe Reader without any problems.
No grammar issues have been noticed.
This textbook is neutral and unbiased.
Reviewed by Guanyu Tian, Assistant Professor, Fontbonne University on 6/19/18
This textbook covers Object-Oriented Programming with Java programming language pretty well. It starts with the concept of Objects and problem solving skills and then dive into Java programming language syntax. Overall, it appropriately covers all... read more
Comprehensiveness rating: 4 see less
This textbook covers Object-Oriented Programming with Java programming language pretty well. It starts with the concept of Objects and problem solving skills and then dive into Java programming language syntax. Overall, it appropriately covers all areas of the subject including the main principles of Object-Oriented Programming and Java programming language. In the later chapters, this textbook also introduces advanced topics such as concurrent programming, network/socket programming and data structures. The textbook provides table of contents at the beginning and index of terms at the end. Each chapter also provides a list of key words and a list of important concepts and technique terms.
Content Accuracy rating: 3
The content of the textbook is mostly accurate. Many URLs linked to Java documentations and APIs are not up-to-date.
Many URLs to Java references are not up-to-date and many online samples are not accessible. Nonetheless, the concepts of Object-Oriented Programming and Java programming language syntax are mostly current. Any updates to the contents of the textbook can be implemented with minimal effort.
The text is easy to understand. However, some of the texts are not displayed on adobe reader.
Consistency rating: 3
The text is consistent in terms of framework. Each chapter starts with introduction to a problem, and then discussion and design of the solution with UML diagrams; then Java is used to implement the solution(s). However, there is some level of inconsistency in terms of Java code samples. For example, some Java code examples use appropriate indentations and new lines, but some examples do not. This may confuse students.
Each chapter is divided into different sections and subsections. A student can go to each section of a chapter by clicking it in the Table of Contents.
Organization/Structure/Flow rating: 3
The topics in this text book are organized in a reasonable order. It starts with general concepts of computer and program design, then Objects and Java Programming Language, and then advanced topics in computer programming. It would be better if the textbook starts with Java programming language and then principles of Object Oriented programming.
Some of the texts are not displayed in the reviewer's adobe reader. Many diagrams and figures are poorly drawn. Overall, the interface of the book is one area that needs improvement.
No major grammar issues has been noticed.
The text of this textbook is a neutral and unbiased.
Overall, this textbook covers materials of Object-Oriented Programming with Java taught in first or second-year computer science course. However, the contents of Java programming language has not been up-to-date and the interface of the book is very poor compare to similar books the reviewer has used for learning and teaching the same materials. Some sample codes are not well written or inconsistent in terms of the use of indentation and new lines. Many URLs are obsolete and the web pages are not accessible.
Reviewed by Homer Sharafi, Adjunct Faculty Member, Northern Virginia Community College on 6/20/17
The textbook includes the material that is typically covered in a college-level CS1 course. Using an “early objects” approach and Java as the programming language, the authors go over problem-solving techniques based on object-oriented... read more
The textbook includes the material that is typically covered in a college-level CS1 course. Using an “early objects” approach and Java as the programming language, the authors go over problem-solving techniques based on object-oriented programming principles. In addition to an Index of terms towards the end of the text, each chapter summary includes the technical terms used, along with a bulleted-list of important points discussed in that chapter.
The computer science concepts and the accompanying sample code are accurate and error-free; however, the only issue is the fact that the URLs that make references to various aspects of Java, such as API documentation, JDK, and the Java Language Specification, have not been updated to reflect the fact that Sun Microsystems was acquired by Oracle back in 2010.
Like other software systems, Java is updated on a regular basis; nonetheless, the computer science concepts discussed in the textbook are based on standard undergraduate curriculum taught in a CS1 course. Therefore, any updates to the textbook would need to be with regard to the version of Java with minimal effort.
Clarity rating: 4
The authors deliver clear explanations of the computer science concepts and the accompanying Java language features.
There is a consistent theme throughout much of the text: A topic is introduced and discussed within the context of a problem. Its solution is then designed and explained using UML diagrams; finally, Java is used to illustrate how the solution is implemented on the computer.
Each chapter is divided into sections that can easily be identified within the table of contents. Therefore, it’s fairly easy for a student to pick and choose a section in a chapter and work on the other sections later. Throughout each chapter, there are self-study exercises to incrementally test understanding of the covered material. Solutions to those self-study exercises are then provided towards the end of the chapter. In addition, each chapter includes end-of-chapter exercises that can be used to assess one’s understanding of the computer science concepts as well as the various features of Java.
The book consists of seventeen chapters; however, a typical CS1 course would need the material in the first ten chapters only, and those chapters are set up in a logical manner, allowing one to go through the material sequentially. Depending on how fast he first ten chapters are covered during the course of a semester, an instructor may choose from the last seven chapters in the text to introduce more advanced topics in computer science and/or Java.
Interface rating: 1
The textbook can be accessed online or opened using Acrobat Reader with no problem. There are no issues, as long as navigation is done one page after another manually. However, when browsing through the table of contents (TOC) or the Index, the entries are not set up using any live links. That is, you cannot click on a page number associated with an item within the TOC or the Index to go directly to that page.
Grammatical Errors rating: 3
This reviewer did not come across any such issues, while going through the text.
This is a computing textbook, where the contents are presented using technical terms. Culturally, the textbook is completely neutral and unbiased in terms of how the material is presented.
Table of Contents
- 0 Computers, Objects, and Java
- 1 Java Program Design and Development
- 2 Objects: Defining, Creating, and Using
- 3 Methods: Communicating with Objects
- 4 Input/Output: Designing the User Interface
- 5 Java Data and Operators
- 6 Control Structures
- 7 Strings and String Processing
- 8 Inheritance and Polymorphism
- 9 Arrays and Array Processing
- 10 Exceptions: When Things Go Wrong
- 11 Files and Streams
- 12 Recursive Problem Solving
- 13 Graphical User Interfaces
- 14 Threads and Concurrent Programming
- 15 Sockets and Networking
- 16 Data Structures: Lists, Stacks, and Queues
Ancillary Material
- Ralph Morelli, Ralph Walde
About the Book
We have designed this third edition of Java, Java, Java to be suitable for a typical Introduction to Computer Science (CS1) course or for a slightly more advanced Java as a Second Language course. This edition retains the “objects first” approach to programming and problem solving that was characteristic of the first two editions. Throughout the text we emphasize careful coverage of Java language features, introductory programming concepts, and object-oriented design principles.
The third edition retains many of the features of the first two editions, including:
- Early Introduction of Objects
- Emphasis on Object Oriented Design (OOD)
- Unified Modeling Language (UML) Diagrams
- Self-study Exercises with Answers
- Programming, Debugging, and Design Tips.
- From the Java Library Sections
- Object-Oriented Design Sections
- End-of-Chapter Exercises
- Companion Web Site, with Power Points and other Resources
The In the Laboratory sections from the first two editions have been moved onto the book's Companion Web Site. Table 1 shows the Table of Contents for the third edition.
About the Contributors
Ralph Morelli, Professor of Computer Science Emeritus. Morelli has been teaching at Trinity College since 1985, the same year the computer science major was first offered. More recently, he was one of the Principal Investigators (PIs) for the Humanitarian Free and Open Source Software (HFOSS) project, an NSF-funded effort to get undergraduates engaged in building free and open source software that benefits the public. In summer 2011 a team of Trinity HFOSS students and faculty traveled to Haiti to build an open source mobile application that helps manage beneficiaries for a humanitarian aid organization. Currently Morelli is the PI of the Mobile CSP project, an NSF-funded effort to train high school teachers in CT and elsewhere to teach the emerging Advanced Placement CS Principles course that is being created by the College Board. The main goal of this NSF initiative is to increase access to computer science among underrepresented groups, including girls, African Americans, and Hispanic Americans. The Mobile CSP course teaches students to create mobile apps to serve their community. In summer 2014, a group of 20 Mobile CSP students spent their summer building mobile apps for the city of Hartford.
Ralph Walde. Dr. Walde has given Trinity 28 years of distinguished service, first as a Professor of Mathematics and now as a Professor of Computer Science. He was instrumental in helping to establish and nourish computing at Trinity and was one of the founding members of the Computer Science Department.
Contribute to this Page
What is object-oriented programming? OOP explained in depth
Object-oriented programming (OOP) is a fundamental programming paradigm used by nearly every developer at some point in their career. OOP is the most popular programming paradigm used for software development and is taught as the standard way to code for most of a programmer’s educational career. Another popular programming paradigm is functional programming, but we won’t get into that right now.
Today we will break down the basics of what makes a program object-oriented so that you can start to utilize this paradigm in your algorithms, projects, and interviews.
Now, let’s dive into these OOP concepts and tutorials!
Here’s what will be covered:
What is Object-Oriented Programming?
Building blocks of oop.
- Four principles of OOP
- What to learn next
Object-Oriented Programming (OOP) is a programming paradigm in computer science that relies on the concept of classes and objects . It is used to structure a software program into simple, reusable pieces of code blueprints (usually called classes), which are used to create individual instances of objects. There are many object-oriented programming languages, including JavaScript, C++ , Java , and Python .
OOP languages are not necessarily restricted to the object-oriented programming paradigm. Some languages, such as JavaScript, Python, and PHP, all allow for both procedural and object-oriented programming styles.
A class is an abstract blueprint that creates more specific, concrete objects. Classes often represent broad categories, like Car or Dog that share attributes . These classes define what attributes an instance of this type will have, like color , but not the value of those attributes for a specific object.
Classes can also contain functions called methods that are available only to objects of that type. These functions are defined within the class and perform some action helpful to that specific object type.
For example, our Car class may have a repaint method that changes the color attribute of our car. This function is only helpful to objects of type Car , so we declare it within the Car class, thus making it a method.
Class templates are used as a blueprint to create individual objects . These represent specific examples of the abstract class, like myCar or goldenRetriever . Each object can have unique values to the properties defined in the class.
For example, say we created a class, Car , to contain all the properties a car must have, color , brand , and model . We then create an instance of a Car type object, myCar to represent my specific car. We could then set the value of the properties defined in the class to describe my car without affecting other objects or the class template. We can then reuse this class to represent any number of cars.
Benefits of OOP for software engineering
- OOP models complex things as reproducible, simple structures
- Reusable, OOP objects can be used across programs
- Polymorphism allows for class-specific behavior
- Easier to debug, classes often contain all applicable information to them
- Securely protects sensitive information through encapsulation
How to structure OOP programs
Let’s take a real-world problem and conceptually design an OOP software program.
Imagine running a dog-sitting camp with hundreds of pets where you keep track of the names, ages, and days attended for each pet.
How would you design simple, reusable software to model the dogs?
With hundreds of dogs, it would be inefficient to write unique entries for each dog because you would be writing a lot of redundant code. Below we see what that might look like with objects rufus and fluffy .
As you can see above, there is a lot of duplicated code between both objects. The age() function appears in each object. Since we want the same information for each dog, we can use objects and classes instead.
Grouping related information together to form a class structure makes the code shorter and easier to maintain.
In the dogsitting example, here’s how a programmer could think about organizing an OOP:
- Create a class for all dogs as a blueprint of information and behaviors (methods) that all dogs will have, regardless of type. This is also known as the parent class .
- Create subclasses to represent different subcategories of dogs under the main blueprint. These are also referred to as child classes .
- Add unique attributes and behaviors to the child classes to represent differences
- Create objects from the child class that represent dogs within that subgroup
The diagram below represents how to design an OOP program by grouping the related data and behaviors together to form a simple template and then creating subgroups for specialized data and behavior.
The Dog class is a generic template containing only the structure of data and behaviors common to all dogs as attributes.
We then create two child classes of Dog , HerdingDog and TrackingDog . These have the inherited behaviors of Dog ( bark() ) but also behavior unique to dogs of that subtype.
Finally, we create objects of the HerdingDog type to represent the individual dogs Fluffy and Maisel .
We can also create objects like Rufus that fit under the broad class of Dog but do not fit under either HerdingDog or TrackingDog .
Next, we’ll take a deeper look at each of the fundamental building blocks of an OOP program used above:
In a nutshell, classes are essentially user-defined data types . Classes are where we create a blueprint for the structure of methods and attributes. Individual objects are instantiated from this blueprint.
Classes contain fields for attributes and methods for behaviors. In our Dog class example, attributes include name & birthday , while methods include bark() and updateAttendance() .
Here’s a code snippet demonstrating how to program a Dog class using the JavaScript language.
Remember, the class is a template for modeling a dog, and an object is instantiated from the class representing an individual real-world item.
Enjoying the article? Scroll down to sign up for our free, bi-monthly newsletter.
Objects are, unsurprisingly, a huge part of OOP! Objects are instances of a class created with specific data. For example, in the code snippet below, Rufus is an instance of the Dog class.
When the new class Dog is called:
- A new object is created named rufus
- The constructor runs name & birthday arguments, and assigns values
Programming vocabulary: In JavaScript, objects are a type of variable. This may cause confusion because objects can be declared without a class template in JavaScript, as shown at the beginning. Objects have states and behaviors. The state of an object is defined by data: things like names, birthdates, and other information you’d want to store about a dog. Behaviors are methods the object can undertake.
| N/A | What is it? | Information Contained | Actions | Example |
|---|---|---|---|---|
| Classes | Blueprint | Attributes | Behaviors defined through methods | Dog Template |
| Objects | Instance | State, Data | Methods | Rufus, Fluffy |
Attributes are the information that is stored. Attributes are defined in the Class template. When objects are instantiated, individual objects contain data stored in the Attributes field.
The state of an object is defined by the data in the object’s attributes fields. For example, a puppy and a dog might be treated differently at a pet camp. The birthday could define the state of an object and allow the software to handle dogs of different ages differently.
Methods represent behaviors. Methods perform actions; methods might return information about an object or update an object’s data. The method’s code is defined in the class definition.
When individual objects are instantiated, these objects can call the methods defined in the class. In the code snippet below, the bark method is defined in the Dog class, and the bark() method is called on the Rufus object.
Methods often modify, update or delete data. Methods don’t have to update data though. For example, the bark() method doesn’t update any data because barking doesn’t modify any of the attributes of the Dog class: name or birthday .
The updateAttendance() method adds a day the Dog attended the pet-sitting camp. The attendance attribute is important to keep track of for billing Owners at the end of the month.
Methods are how programmers promote reusability and keep functionality encapsulated inside an object. This reusability is a great benefit when debugging. If there’s an error, there’s only one place to find it and fix it instead of many.
The underscore in _attendance denotes that the variable is protected and shouldn’t be modified directly. The updateAttendance() method changes _attendance .
Four Principles of OOP
The four pillars of object-oriented programming are:
- Inheritance: child classes inherit data and behaviors from the parent class
- Encapsulation: containing information in an object, exposing only selected information
- Abstraction: only exposing high-level public methods for accessing an object
- Polymorphism: many methods can do the same task
Inheritance
Inheritance allows classes to inherit features of other classes. Put another way, parent classes extend attributes and behaviors to child classes. Inheritance supports reusability .
If basic attributes and behaviors are defined in a parent class, child classes can be created, extending the functionality of the parent class and adding additional attributes and behaviors.
For example, herding dogs have the unique ability to herd animals. In other words, all herding dogs are dogs, but not all dogs are herding dogs. We represent this difference by creating a child class HerdingDog from the parent class Dog , and then adding the unique herd() behavior.
The benefits of inheritance are programs can create a generic parent class and then create more specific child classes as needed. This simplifies programming because instead of recreating the structure of the Dog class multiple times, child classes automatically gain access to functionalities within their parent class.
In the following code snippet, child class HerdingDog inherits the method bark from the parent class Dog , and the child class adds an additional method, herd() .
Notice that the HerdingDog class does not have a copy of the bark() method. It inherits the bark() method defined in the parent Dog class.
When the code calls fluffy.bark() method, the bark() method walks up the chain of child to parent classes to find where the bark method is defined.
Note: Parent classes are also known as superclasses or base classes. The child class can also be called a subclass, derived class, or extended class.
In JavaScript, inheritance is also known as prototyping . A prototype object is a template for another object to inherit properties and behaviors. There can be multiple prototype object templates, creating a prototype chain.
This is the same concept as the parent/child inheritance. Inheritance is from parent to child. In our example, all three dogs can bark, but only Maisel and Fluffy can herd.
The herd() method is defined in the child HerdingDog class, so the two objects, Maisel and Fluffy , instantiated from the HerdingDog class have access to the herd() method.
Rufus is an object instantiated from the parent class Dog , so Rufus only has access to the bark() method.
| Object | Instantiated from Class | Parent Class | Methods |
|---|---|---|---|
| Rufus | Dog | N/A | bark() |
| Maisel | Herding Dog | Dog | bark(), herd() |
| Fluffy | Herding Dog | Dog | bark(), herd() |
Encapsulation
Encapsulation means containing all important information inside an object , and only exposing selected information to the outside world. Attributes and behaviors are defined by code inside the class template.
Then, when an object is instantiated from the class, the data and methods are encapsulated in that object. Encapsulation hides the internal software code implementation inside a class and hides the internal data of inside objects.
Encapsulation requires defining some fields as private and some as public.
- Private/ Internal interface: methods and properties accessible from other methods of the same class.
- Public / External Interface: methods and properties accessible from outside the class.
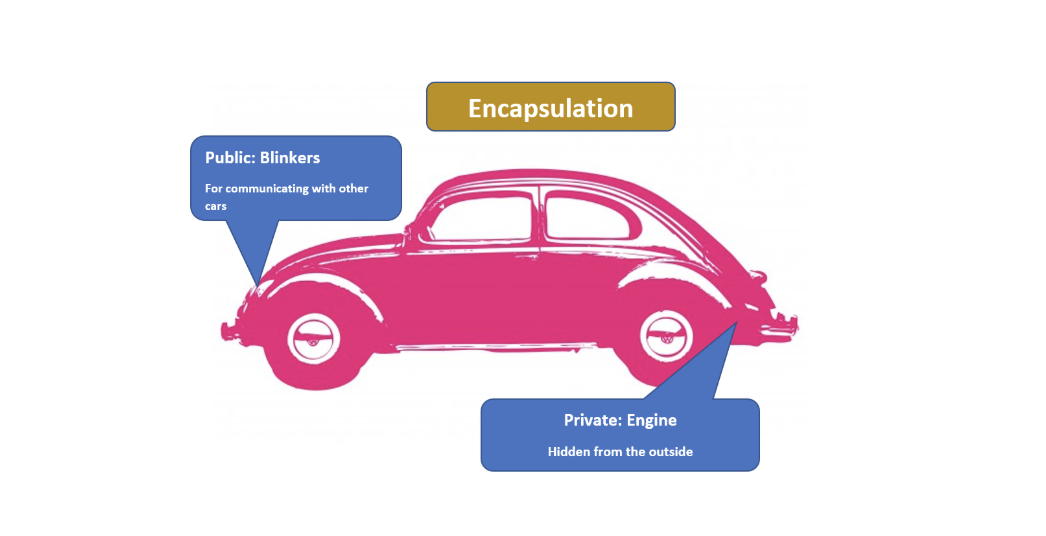
Let’s use a car as a metaphor for encapsulation. The information the car shares with the outside world, using blinkers to indicate turns, are public interfaces. In contrast, the engine is hidden under the hood.
It’s a private, internal interface. When you’re driving a car down the road, other drivers require information to make decisions, like whether you’re turning left or right. However, exposing internal, private data like the engine temperature would confuse other drivers.
Learn in-demand tech skills in half the time
Mock Interview
Skill Paths
Assessments
Learn to Code
Tech Interview Prep
Generative AI
Data Science
Machine Learning
GitHub Students Scholarship
Early Access Courses
For Individuals
Try for Free
Gift a Subscription
Become an Author
Become an Affiliate
Earn Referral Credits
Cheatsheets
Frequently Asked Questions
Privacy Policy
Cookie Policy
Terms of Service
Business Terms of Service
Data Processing Agreement
Copyright © 2024 Educative, Inc. All rights reserved.

What Is Object-Oriented Programming?

- Share article on Twitter
- Share article on Facebook
- Share article on LinkedIn
Every programming language has its own syntax and features, and many of them also use different paradigms or styles of writing and organizing code.
The most common programming paradigms are procedural, functional, and object-oriented programming. Object-oriented is the most popular, and the one most often taught in programming courses.
Object-oriented programming is a software development approach that focuses on defining and sculpting named classes as entities with attributes and behaviors. One key benefit of object-oriented programming? It makes reusing and maintaining code easier. Ahead, we’ll break down what you need to know about object-oriented programming and the courses to take if you want to get started.
Learn something new for free
- Learn OOP with Python
Learn JavaScript
The building blocks of object-oriented programming .
The object-oriented programming paradigm uses the following building blocks to structure an application:
Classes
Classes are user-defined data types used as a blueprint or template for the objects a software program will use in its operation. Classes define the methods and attributes that each object created from them has. Most object-oriented programming languages use classes, though some (like Go , for example) do not.
Modern JavaScript has classes now, but it didn’t originally. It first used a similar concept called prototypes.
Here’s an example class in JavaScript:
Objects
In an object-oriented language that uses classes, objects are instances of those classes created with specific data. To create an object with the Cat class above, we would use the following code:
const myCat = new Cat('Morris', 'Tabby');
When the myCat object is created, it calls the constructor method with the parameters we specify and sets the name and type attributes of the object. We get the following output when we call the methods we’ve defined above:
Methods
Methods are functions stated inside a class that define the behavior of the objects created from the class. They perform actions like returning information about the object or modifying the data contained in the object. The Cat class we created above has two methods: speak() and getTag() .
Attributes
Attributes are variables defined inside a class that describe what data the objects created from the class will contain. In our Cat class, we have two attributes: name and type . It’s common to set these attributes in the constructor of the class as we did above.
The main principles of object-oriented programming
There are four primary principles of object-oriented programming, including encapsulation, abstraction, inheritance, and polymorphism.
Inheritance
Inheritance allows a class to inherit the features of other classes. The original class is called the parent class, and the class inheriting the features is called the child class. Inheritance provides reusability. The child class can also add new attributes and methods.
Inheritance is often used to create generic parent classes and child classes that have more specific functionality. Here’s an example using our Cat class as a parent class:
This new Tiger class has all the methods and attributes of the original Cat class but also has a huntGazelle() method.
Encapsulation
This principle means that all the important data and functionality of an object is contained within that object. Only select information that is needed outside of the object is exposed to the outside world. When an object is created from a class, the methods and attributes are encapsulated inside the object. Encapsulation also hides the implementation of this code inside the object.
Encapsulation requires that you define some attributes and methods as public or private. “Public” dictates that the attributes and methods can be accessed, modified, or executed from the outside. “Private” limits access to use from inside the object. Attributes and methods can also be defined as protected. This means that classes that inherit from the parent class can also access these attributes and methods, just like the parent class.
Encapsulation also adds a layer of security by preventing attributes from being changed or methods from being executed by the outside world, which can cause unintended data corruption. Here’s an example:
The sound attribute is hidden from the outside world in this class. This ensures that the class can’t be modified by other code, like code to make the cat bark.
Abstraction
Abstraction is a means for providing a higher-level interface for interacting with objects. It extends the encapsulation principle by making only key attributes visible to a user and hiding the remaining complexity. This suggests that the complexity of the actual object can be represented by a simple class with a limited number of methods you can execute or attributes you can access.
One way to imagine the concept of abstraction is to think about driving a car. To make the car turn right, you only have to turn the steering wheel right. The driver doesn’t have to know how the tires, rack and pinion, or power steering pump works — they just turn the wheel. Having to manage all of those other things while driving the car would cause chaos and a lot of accidents.
Polymorphism
Polymorphism means objects can share behaviors and can take on more than one form. So far, we have created two classes: Cat and Tiger . If another part of our program has a random list of objects created from these classes, we know we can loop through them and call the speak() method on any of them. Because of polymorphism, we know that any of these objects contain that method.
With inheritance, a child object can also override the functionality of the parent object. Remember when we created the Tiger class, but the tiger still meowed like a cat? We can fix that by creating the class like this instead:
Here we simply override the speak() method of the parent Cat class, and now our tiger will roar. Inheritance is what allows methods and attributes to carry over, but polymorphism allows those elements to take another form in a new class.
The benefits of object-oriented programming
There are many reasons the object-oriented paradigm is the most popular programming paradigm. Here are some of the main benefits:
- You can represent complex objects with simple, reproducible classes.
- The same object you create in one object-oriented program can be reused in other software.
- You can use polymorphism to define class-specific behavior.
- By encapsulating all the information about an object within the object, object-oriented software is easy to debug.
- Encapsulation protects data from being modified from unexpected events and actions.
Which programming languages are object-oriented?
Simula, which was developed in the 1960s, was the first object-oriented programming language and influenced many of the programming languages we have today. While some languages are either purely procedural or functional, most of the popular ones support the object-oriented programming style in some way. Here are some of those languages:
- Java is a general-purpose programming language used widely in enterprise development and is object-oriented.
- Python is a popular programming language used for a wide variety of tasks that supports object-oriented, procedural, and functional programming.
- Ruby is what is called a “pure” object-oriented language where everything in a program is an object.
- JavaScript is an object-oriented language that used prototypes instead of classes in its earlier days.
- C++ was created as an extension of the C programming language and is designed to be object-oriented.
- C# is an object-oriented language developed by Microsoft to run either in the .NET framework or the cross-platform .NET Core framework.
- Go is an object-oriented programming language that doesn’t have classes. Instead, you build up objects using composition.
Learn more about object-oriented programming
Learning object-oriented programming can change how you think about code and make you a better developer. By breaking up the requirements of a complex project into reusable classes, you can simplify the coding process, make your code more organized, and make it easier to debug.
You can learn the basics of object-oriented programming in any of the courses below:
Related courses
Learn python 3.
Each of these courses was created for beginners. So don’t worry if you know nothing about coding or very little about technology now. The course you choose will start by introducing you to the concepts of programming, teach you the fundamentals of the programming language itself, and leave you with multiple projects that will look great in your technical portfolio .
Subscribe for news, tips, and more
Related articles.

The Most Important Soft Skill for Developers & How to Get Better at It
Try these problem-solving strategies the next time you’re feeling stuck.

Learn Essential Professional Skills in 70+ New Free Courses
Improve your soft skills like communication, leadership, and problem solving in these new free courses.

12 JavaScript Code Challenges for Beginners
These 12 JavaScript code challenges are an excellent way to put your new knowledge to the test and continue building your coding skills.

What is C# Used For?
C# is a popular programming language that’s similar to C and C++. Learn what it’s used for, what you can do with it, and how to get started.
Object-Oriented Programming- concepts and problem solving.
Riyan Pahuja
The world consists of objects. Each object has its own behaviour and characteristics. Imagine how hard it would be to build an aeroplane if we had to design everything from scratch, including reinventing the wheel, vulcanizing rubber and hardening plastic etc. Fortunately, we have stored the information common to all air crafts previously and simply use it which saves a huge amount of time and reduces the complexity. This is exactly the concept on which the object-oriented paradigm is built. Common characteristics between objects is stored in a class and then objects are built as their instances.
Problem Solving
Computers were designed to solve problems that human would usually take a lot of time to solve. Hence, this makes problem solving a core domain of computer science and what a programmer must learn. We can call computer programmers as problem solvers and in order to solve a problem they must:
1. Represent and understand the data(information) that describes the problem.
2. Map the steps to use the information to solve the problem.
In computer science, problem solving has the following 6 steps,
1. Understanding the problem
2. Formulating a model
3. Developing an algorithm
4. Writing a subsequent program
5. Testing and improving the program
6. Evaluating the solution.
For example:
Write a program to calculate the average of the grades of a student.
1. Understanding the problem:
The question has asked to find the mean of all the given grades of a student
2. Formulating a model:
Average = grade1 + grade2 + …. + gradeN / number of records
3. Developing an algorithm:
grades_array = grades, sum=0 for grade in grade array add grades -> sum average <- sum / length(grades_array)
A program is written following the above algorithm in the programming language of choice.
The program is tested against all kinds of data including but not limited to corner cases that may break the algorithm such as the length of the array being returned as 0.
6. Evaluating the solution
The solution is evaluated and checked whether the output is correct or not.
When we are asked to perform a task, we require a set of instructions to perform that task. These instructions can be previously stored in the memory or explicitly stated at the time of task assignment. An algorithm is just a fancy name for a set of instructions.
Programmers use algorithms to tell a machine how to perform a certain task. For example: If a human is asked to get a stack of papers off the table, the instructions given would be, go to the table, turn towards the stack of papers, pick up the papers. Similarly, when a task is assigned to a computer/machine we need to provide it a set of instruction or algorithm in short to achieve a successful result in the said task.
A good programmer can define the necessary steps to give to a computer for completion of a task. However, a computer is bound by the limited set of possible steps. For example, given a set of number, it can add them. But if it is required to calculate the mean of the given set, the task is beyond its capability. A programmer would need to specify the steps for it to achieve this,
1. Add the numbers and save the result in a variable.
2. Calculate the length of the set and store it in the variable
3. Divide the sum variable by the length variable and store the result in a third variable.
4. Convey the result.
Note: Step 2 requires another set of instructions to be completed and is not within the capability of a computer.
Object Oriented Programming
A brief history.
The first ever object-oriented language invented was named Simula. Ole-Johan dal and Nygaard laid the foundation stone of object-oriented programming that is now the dominating version of programming in the modern day. Through their design Simula 1 was born. Simula 1 along with Simula 67 was awarded the IEEE von Neuman medal in 2002. Simula 1 programming language had neither classes nor inheritance, however Simula 67 introduced the idea of the “fundamentals of the object-oriented programming”.
Samlltalk-72, which was an early version of Smalltalk, refined the idea of objects as little computers. Tim Rentsch in his paper named “object-oriented programming”, published in 1982, said
“The immediate ancestor of object-oriented programming is the programming language Simula. The Smalltalk programming language system carried the object-oriented paradigm to a smoother model.” (Rentsch)
What is Object Oriented Programming?
Object Oriented programming, which may be thought as a new concept in the programming world by many was developed in the 1960s along with most of its concepts used in the present.
Object Oriented programming breaks down a program into various tasks which are then assigned to different objects. Considering a real-world example, Mike has been some experiencing some issues with his computer which he cannot fix on his own. He would need the help of an engineer provided by the manufacturing company. Mikes contacts the technical support and requests for an engineer to be sent to his home for fixing the issues. The technical support then does the required for assigning an engineer to this task. The engineer arrives at Mike’ s house and fixes the computer and takes his leave. In this example Mike uses an object/agent (technical support) to pass the message to the engineer. It is important to take note on how Mike does not know or need to know how the technical support contacted the engineer and assigned him the task. Then the engineer then does the assigned task and takes his leave. We must note again that Mike does not know how the computer was fixed by the engineer. This is concept is referred to as abstraction.
The concept of object-oriented programming dictates building reusable code and having the willingness of using code built by other. Technical support is a code built by someone and was used by Mike and can also be used by others for similar purposes.
Concepts of Object-Oriented Programming.
1. Method and Methods
In the example presented in the previous section Mike passes a message to technical support for calling upon a function. Similarly, in the OOP we pass messages to objects to call upon methods that would do a specific task for us. A task(method) is called upon when we pass a message to an object with some additional information called arguments. A method is only called by an object if the method has the same name as the message passed.
l. Message Vs Procedure Calls
Both consist of well-defined steps of action to perform a task after a request has been made. However, A message requires a receiver(object) to call upon a method to perform a task. A procedure call requires none such receiver. The method to call upon for the task is at the sole discretion of the receiver(object).
Mike could have asked his friend to fix his computer and could have gotten a satisfactory outcome. But the method used by this friend would have been different than the one used by the technical support. Mike could have also asked a plumber to fix his computer, but the plumber might not have the appropriate method to perform the task and would put forward an appropriate error message.
In context of computers, the method that is called upon depends upon the receiver. Different receiver may call upon different method to solve the same task. The presence of this receiver that acts as a middleman is what differentiates message passing from procedure calls.
2. Classes and Objects.
Objects: Objects act as receivers. They receive messages from the program and use them to call upon method for performing tasks. Objects contain not only methods but also data. Objects provide security to the data by not disclosing any data marked as private to the user. In the example, the technical support does not reveal the internal working to Mike, they simply receive the request and perform the task. In this scenario Mike does not know what data is used for the completion of the request. Similarly, in OOP the object does not let the user know what data it contains and how it is using it.
Classes: Classes act as a blueprint for an object. They define the behaviour and inner working of the object. All the objects derived from a class must follow the same behaviour. Technical support operator that talked to Mike in the above example was an object that followed the behaviour that was defined by a class which may be called technical support staff. All the other technical support staff communicating with a customer would also follow the same behaviour defined by the class.
Example code:
In the above given code TechSupport is the class that dictates the behaviour of any object that is based on this class. Operator1 is the object that follows the design that has been laid down by the class TechSupport. A message is passed to the object which then receives the message and matches it with a corresponding method which is thereafter called and performs a task.
Objects can also be created within the same class.
Sample code:
In the above code the object is defined within the same class and then carries out the task successfully.
3. Inheritance
A lot of objects. in the real world, contain a lot of similarities and may follow the same behaviour. Let us consider a class Human. Now a man and a woman are two objects that are both part of the class Human. They both have various similar characteristic and behaviour. They both consume food, talk, see, hear etc. However, they both also contain some dissimilarities, like body structure, reproductive organs etc. Now due to these differences we cannot have man and women be instances of the same class. So, one way to approach this would be to create two different classes for man and women. But then there would also be a lot of repetitive code that for the two classes due to the similarities. So, to solve this we could define a super class called Human that would contain the code for the similar characteristics and behaviour of the two classes and then derive these two classes from the super class (parent class). The sub classes (child classes) would contain the code from the super class and would have the ability to override it if need be or add some of its own code. This ability of OOP is called inheritance.
The above code demonstrates how inheritance works. The class Man and Woman is derived from the super class Human. Both Man and Woman contain the method sleep() of the Human class and are able to call upon it. They also redefine the method shave according to their own needs. This is called method overriding.
4. Polymorphism
Polymorphism is one of the most important characteristics of an object-oriented programming language. It refers to one object taking many forms i.e., using one thing for performing different tasks.
Method overriding: In the above example we saw two derived classes using the same function shave() to perform two different tasks. This is called run time polymorphism or method overriding.
Method Overloading: When we define more than one method with the same name in the same class to different method, we call it method overriding. An object-oriented programming language differentiates between the two method by the number or type of parameters passed in the method. If the number of parameters does not differ an error message will be generated. Let us take an example: Mary and Ajay were asked to cook a meal for the guests that were arriving for dinner. Mary cooked a wonderful dish of Chicken Curry whereas Ajay cooked a delicious Pasta. Mary and Ajay cooked quite different things and followed different instructions. However, the message passed to both was the same that is “cook a meal”. Similarly, when the message that needs to be passed to an object is similar, but the task needs to be carried out a differently bases on the specifications of the task we use method overloading.
As it is evident from the code the same name for two different methods is used. The two methods print 2 different things however they differ by the type of the parameters passed to the method.
Virtual Functions: A virtual function allows the base class to override a function defined in the parent class. If a function in base class is not defined as virtual then the base class will not override that function. In programming languages such as C++, to achieve rum time polymorphism that is method overriding the parent class method must be defined as virtual. However, in programming language such as Java, all the method are defined as virtual by default.
Abstract classes: An abstract class acts as super class from which more specific classes can be derived. It defines general methods and forces the sub classes to override them. For example, all cars contain a drive function, a neutral function and a reverse function. But how they implement it can be quite different among different brands and different models. A lower model of Maruti car may have a shift drive model and the upper model of the same car may have an automatic drive model. In OOP we can define Maruti as an abstract class that forces all it is sub classes that would the car models to have a drive function in it. In languages such as Java the method should be declared abstract whereas languages such as C++ require the function to be declared virtual. A function that is declared as virtual and as not body is known as pure virtual function. The abstract method of Java can be considered as a pure virtual function.
Note: An abstract class can contain both abstract and non-abstract methods. However, it will throw an error if an abstract method is not overridden in the sub class.
5. Abstraction & Encapsulation:
Abstraction is a concept of dealing with the action without worrying about the details of the process of the action. Abstraction has been discussed before in this paper however let us reiterate. Considering a previous example, where Mike contacted the technical support for assistance with his computer. Mike is not informed about how the engineer was contacted, how the engineer reached to Mike’s home and how the computer was fixed. Mike was spared from the details of the process. Similarly, in the world of OOP the objects receive the message, call the method and the method does its job and user does not know how the action was performed by the method.
Objects consist of both data and methods. The data can only be accessed and modified by the object’s methods. This bundling of data and methods together is called encapsulation. Data encapsulation provides added security to the data and prevents it from being modified by anything other than the methods of the object to which that belongs. In the fixing the computer example, the technical support operator must have data, such as customer phone number, employee phone number, customer address etc., encapsulated with the functions they can perform that were used together to contact the engineer and get him/her to Mike’s house.
Advantages of Object-Oriented Programming
Object Oriented Programming has been around for decades now and has gone through evolution to becomes what it is in the modern day. But the inherent concepts such as objects, classes, abstraction, encapsulation etc remain unchanged. We should also keep in mind that different programming languages may have their own implementation of the OOPs concepts.
Here are a few advantages of object-oriented programming without dependence on any specific language.
1. The real world is made up of objects and each object has its own behaviour and characteristics. Using object-oriented programming we can represent real world problems and solve them in a much more efficient manner. This paper has represented several real-world problems and how it is solved using objects and classes.
2. Object oriented programming provides higher data security as it bundles data and methods together and only allows the data to be accessed and modified by the methods. It also only gives the user necessary information and hides all the unnecessary details making it more user friendly. Recall in how technical support officer did not trouble Mike with ant of the unnecessary information about how the engineer will get there and do his job.
3. In object-oriented programming we can write reusable code using inheritance which not only makes our code more concise and requires less space but also makes it much more readable. Recall how we were able to use the same method that was written in the Human class for both its sub classes, Man and Woman.
4. As codes is modular it is easier to debug. As all objects are independent i.e., they do not dependent on any of the other objects for execution we can quickly and very easily figure out where the problem in our code is. If the engineer has not arrived at Mike’s house it would have been easy for company to figure out that the problem must have been in the technical support class.
5. Using polymorphism, we can override or overload a method to make it perform more than one task. Polymorphism gives the code the super ability to shape shift into something else. Recall how the ‘shave’ method was made to do different things depending upon which object called it and how Mary and Ajay were able to cook different things using the ‘cook’ method.
6. Object oriented programming language require less space to store the code as most of the objects are created at run time when they are called and are destroyed after they have successfully accomplished their purpose.
Popularity of Object-Oriented Programming and Its Problems
Object oriented programming is a fairly popular concept. And it had become even popular now that it has been followed up by object-oriented analysis and object-oriented design. However, this concept can be hard to understand for new programmers or programmers who have usually coded in functional programming paradigm or procedural programming languages only. This causes the programming world to be split in two sections, the one who has adopted object-oriented programming and one who hates it. It is not only new programmers who are against the idea of object-oriented programming but some experienced programmers such as, Ilya Suzdalnitski, who is a senior full stack developer at Replicon has called OOP a “Trillion-dollar disaster” (Suzdalnitski, 2019). People believe that object-oriented programming is a paradigm for elite programmers whereas the code base is mostly edited by average programmers since they are more in numbers. This requirement of elite programmers, who are harder keep around, may cause the paradigm to fail over time.
However, no matter how much object-oriented programming is hated by experienced or novice programmers the success of object programming languages such as Java and C++ are undeniable.
Even previously functional programming(scripting) languages such as JavaScript have now added classes in their ES6 update. Also, the major dependency of app development, web development and other development paradigms on object-oriented programming languages such as Java, Kotlin, Python and not to mention the promotion of these languages by big dominating companies such as Google and Facebook will be stopping the object-oriented programming paradigm from dying out.
Object oriented programming has gained so much popularity that it does not seem to stop. Most of the problems in real life are being solved using this paradigm. Even though, object-oriented programming may not be very well understood by everyone it is an undeniable fact that it has made revolutionary changes in the programming world. This paper tries to explain each terminology and concept in relation to their real-life usage which proves its importance in the real-world problem solving. It is essential to understand how the paradigm works and effect the problem before selecting it to reach the solution.
1. https://docs.oracle.com/javase/tutorial/java/concepts/index.html
2.Object-oriented programming: Some history, and challenges for the next fifty years. Andrew P. Black, Portland State University.
3.Object-oriented programming and its concepts. Ashwin Urdhwareshe, Department of Technology Management, University of Bridgeport.
4. Introduction to Network Simulator NS2 (second edition). Teerawat Issariyakul Ekram Hossain
5.Object-Oriented Programming. Tim Rentsch, Computer Science Department, University of Southern California.
6.Data abstraction, data encapsulation and object-oriented programming. A. Toni Cohen, Department of Computer and Information Sciences, University of Delaware.

Written by Riyan Pahuja
Studying engineering as information technology major.
Text to speech
Advanced Object-Oriented Programming in Java – Full Book

Java is a go-to language for many programmers, and it's a critical skill for any software engineer. After learning Java, picking up other programming languages and advanced concepts becomes much easier.
In this book, I'll cover the practical knowledge you need to move from writing basic Java code to designing and building resilient software systems.
Many top companies rely on Java, so understanding it is essential, not just for tech jobs but also if you're considering starting your own business.
Looking to move up in your career? Contributing to open-source projects can be a smart move. This guide will also help you with the advanced skills you'll need to become an open-source Java developer and get noticed by employers.
And finally, the book will help you stay current with the latest in technology as you learn about the Java behind AI, big data, and cloud computing. You'll learn to create high-performance Java applications that are fast, efficient, and reliable.
Prerequisites
Before diving into the advanced concepts covered in this book, it is essential to have a solid foundation in Java fundamentals and Object-Oriented Programming (OOP).
This guide builds upon the knowledge and skills acquired in my previous book Learn Java Fundamentals – Object-Oriented Programming .
Here are the key prerequisites:
Strong Understanding of Java Basics
- Syntax and Structure : Familiarity with Java syntax and basic programming constructs.
- Basic Programming Concepts : Proficiency in writing and understanding simple Java programs.
Proficiency in Object-Oriented Programming Concepts
- Classes and Objects : Deep understanding of classes, objects, and their interactions.
- Inheritance and Polymorphism : Knowledge of how inheritance and polymorphism are implemented in Java.
- Encapsulation and Abstraction : Ability to encapsulate data and utilize abstraction in program design.
Experience with Java Data Types and Operators
- Primitive and Non-primitive Data Types : Comfort with using various data types in Java.
- Operators : Familiarity with arithmetic, relational, and logical operators.
Control Structures and Error Handling
- Control Flow Statements : Proficiency in using if , else , switch , and loop constructs.
- Exception Handling : Basic understanding of handling exceptions in Java.
Basic Understanding of Java APIs and Libraries
- Familiarity with using standard Java libraries and APIs for common tasks.
This guide assumes that you have already mastered these fundamental concepts and are ready to explore more advanced topics in Java programming.
This book will delve into complex topics that require a strong foundation in basic OOP principles, along with familiarity with Java's core features and functionalities.
How this Book Will Help You:
- Position yourself as a top candidate for senior Java developer roles, ready to tackle high-stakes projects and lead innovative software development initiatives.
- Transform you into an expert in high-demand areas such as concurrency and network programming, making you an invaluable asset to any team.
- Build a portfolio of impressive projects, from dynamic web applications to sophisticated mobile games, showcasing your advanced Java skills to potential employers.
- Learn to write code that's not only functional but exceptionally clean and efficient, adhering to the best practices that define expert-level Java programming.
- Engage with a community of like-minded developers, and by the end of this guide, you’ll not only gain knowledge but also a network of peers to collaborate with on future Java endeavors.
- Equip yourself with advanced problem-solving skills that enable you to dissect and overcome real-world software development challenges with innovative solutions.
- Stay ahead of the curve by mastering the latest Java features and frameworks that will define the future of software development.
- Prepare yourself to achieve Java certification, validating your skills and knowledge in a way that's recognized across the industry.
- Gain the confidence to contribute to open-source projects or even start your own, with the deep understanding of Java that this guide provides.
You're embarking on a journey to master Java Object-Oriented Programming, a skill that paves the way for diverse opportunities in software engineering. This guide will lay a foundation for you to transition from writing code to building robust software systems.
With these advanced skills, you're poised to contribute to open-source projects, qualify for top Java developer roles, and stay ahead in the tech industry. Your path from learning to leading in the Java community starts here. Let's begin.
Table of Contents
Chapter 1: unit testing and debugging.
- Chapter 2. File Handling and Input/Output (I/O)
Chapter 3: Deadlocks and How to Avoid Them
Chapter 4: java design patterns, chapter 5: how to optimize java code for speed and efficiency.
- Chapter 6: Concurrent Data Structures and Algorithms
Chapter 7: Fundamentals of Java Security
Chapter 8: secure communication in java.

In software development, unit testing and debugging play a vital role in ensuring the quality and reliability of your code. These practices provide a reliable means to verify the correctness of your code, allowing you to identify and address errors or bugs that may hinder its intended functionality.
Unit testing allows you to systematically test individual units of your code, such as functions or methods, applying pressure through tests to ensure their proper functioning.
By conducting these tests, you can establish a reliable method to validate the behavior of your code. This not only instills confidence in your work but also allows you to catch and address potential issues early on, making the development process more efficient.
To become an efficient software engineer, it is crucial to prioritize unit testing and debugging as integral parts of your software development workflow. By doing so, you can ensure the stability and effectiveness of your codebase, providing practical advice that will help you deliver high-quality software.
Fundamentals of Unit Testing
Java, with its rich ecosystem and extensive support for testing frameworks, offers a fertile ground for implementing unit testing practices. In this section, you'll learn about Java's testing landscape, highlighting essential tools and frameworks like JUnit.
JUnit is a widely used testing framework that provides a comprehensive set of features and functionalities to facilitate the creation and execution of high-quality unit tests in Java.
By leveraging tools like JUnit, you can confirm the effectiveness and efficiency of your testing efforts, leading to the development of robust and reliable Java applications.
Examples for unit testing include isolation, repeatability, and simplicity. When conducting unit tests, it is important to focus on testing the beginning, middle, and end of your functions.
By separating each key area and stress testing it, you can ensure thorough testing of your code. This approach aligns with the principles of the scientific method, where you aim to test all crucial aspects of your functions to achieve reliable and accurate results.
Unit Testing Examples
To illustrate unit testing in Java using JUnit, let's create some practical examples. We'll focus on a simple Java class and how we can apply unit testing to it, adhering to principles like isolation, repeatability, and simplicity.
Suppose we have a Java class named Calculator with a couple of basic mathematical operations:
Using JUnit, we will write test cases that individually test each method of the Calculator class.
First, include JUnit in your project. If you're using Maven, add the following dependency to your pom.xml :
Now, let's create test cases:
In these test cases, we follow the principles of unit testing:
- Isolation : Each test method ( testAdd and testSubtract ) is independent of others. They test specific functionalities of the Calculator class. This is what you want to do, test each case systematically and separately.
- Repeatability : These tests can be run multiple times, and they will produce the same results, ensuring consistent behavior of the methods being tested.
- Simplicity : The tests are straightforward and focused solely on the method they are meant to test. For instance, testAdd only tests the add method.
How to Write Helpful Unit Tests
When crafting unit tests, it's essential to approach them with a clear and systematic strategy. This involves following certain guidelines and asking pertinent questions to ensure comprehensive and effective testing.
Here’s an outline to guide you through the process:
Create a New Object
Firstly, for each test, create a new instance of the object you're testing. This ensures that each test is independent and unaffected by the state changes caused by other tests. In Java, this typically looks like this:
Use Assertions:
Utilize JUnit's assertion methods like assertEquals , assertTrue , and so on to verify the outcomes of your test. These assertions form the crux of your test, as they validate whether the object's behavior matches expectations. For example:
Initiate Several Objects:
In some cases, it may be necessary to initiate several objects to simulate more complex interactions. This is particularly useful when testing how different components of your application interact with each other. For instance:
Key Guidelines and Questions for Writing Tests
- What is the expected outcome? Clearly define what result you expect from the method you're testing. This guides your assertion statements.
- Are the tests independent? Ensure each test can run independently of the others, without relying on shared states or data.
- Are edge cases covered? Include tests for boundary conditions and edge cases, not just the typical or average scenarios. This is key for creating reliable software.
- Is each test simple and focused? Aim for simplicity. Each test should ideally check one aspect or behavior of your method.
- How does the method behave under different inputs? Test a variety of inputs, including valid, invalid, and edge cases, to ensure your method handles them correctly.
- Is the test repeatable and consistent? Your tests should produce the same results every time they're run, under the same conditions.
- Are the test names descriptive? Name your tests clearly to indicate what they are testing. For example, testEmptyListReturnsZero() is more informative than testList() .
- Are you checking for exceptions? Where applicable, write tests to check that your method throws the expected exceptions under certain conditions.
Following these guidelines ensures that your unit tests are robust, reliable, and provide a comprehensive assessment of your code's functionality.
Practical Unit Testing Scenarios and Case Studies
Here are examples of Java code snippets that demonstrate real-world scenarios and case studies related to array manipulation, along with the corresponding unit tests using JUnit. These examples illustrate common challenges and how to address them through effective unit testing and debugging.
Sort a List of Products
Scenario : A Java method sorts an array of Product objects based on their price.
Product Class:
Sorting Method:
Find the Maximum Value in an Array
Scenario : A method is supposed to find the maximum value in an array, but it's returning incorrect results.
Method with Bug:
Debugging and Fixing:
The issue is in the for-loop, which incorrectly starts from index 1 instead of 0. Correcting the loop to start from index 0 fixes the bug. Corrected Method:
These examples show how unit testing can reveal bugs in real-world scenarios and guide developers in debugging and fixing issues related to array manipulation in Java.
Unit Testing Best Practices
When it comes to writing and maintaining unit tests in Java, there are several best practices that can help ensure the effectiveness and reliability of your tests.
First and foremost, it is crucial to focus on test isolation. Each unit test should be independent of others, meaning that they should test specific functionalities of the code in isolation. This allows for a more systematic and targeted approach to testing, making it easier to identify and fix any issues that may arise.
By keeping tests isolated, you can ensure that changes made to one test do not inadvertently affect the results of other tests.
Another important best practice is to prioritize test repeatability. Tests should be designed in such a way that they can be run multiple times, producing the same results each time.
This ensures consistent behavior and allows for easy identification of any changes or regressions in the code. By making tests repeatable, you can have confidence in the stability and reliability of your codebase.
Simplicity is also key when it comes to writing unit tests. Each test should be focused solely on the method or functionality it is meant to test.
By keeping tests simple and concise, you can improve readability and maintainability. Additionally, simple tests are easier to understand and debug, making it quicker to identify and fix any issues that may arise.
When writing unit tests, it is important to consider edge cases and boundary conditions. These are scenarios that may not be covered by typical or average test cases.
By including tests for edge cases, you can ensure that your code handles these situations correctly and avoid potential bugs or errors. Testing these extreme scenarios is crucial for creating reliable and robust software.
Test names should be descriptive and indicative of what is being tested. This helps improve the readability and understandability of the tests, making it easier for other developers to navigate and interpret them.
Clear and concise test names also serve as documentation for the behavior and functionality being tested.
In addition to these best practices, it is essential to follow a systematic and comprehensive approach to unit testing. This involves asking pertinent questions and following guidelines to ensure comprehensive and effective testing.
Questions such as "What is the expected outcome?" and "Are the tests independent?" help guide the creation of thorough and reliable unit tests.
These practices will help ensure the stability and effectiveness of your codebase, allowing you to deliver high-quality software that meets the highest standards of functionality and reliability.
Hands-On Exercises for Unit Testing in Java
Beginner level: exercise & solution, exercise: testing a sum function.
Create a function sumArray that takes an array of integers and returns the sum of all the elements. Write a unit test to validate that the function correctly sums the array elements.
Solution with Code:
Intermediate Level: Exercise & Solution
Exercise: testing array equality.
Create a function arraysEqual that compares two arrays of integers and returns true if they are equal (same elements in the same order) and false otherwise. Write a unit test to validate the function's behavior for equal and unequal arrays.
Advanced Level: Exercise & Solution
Exercise: testing array rotation.
Create a function rotateArray that takes an array and a positive integer k , and rotates the array to the right by k places. Write a unit test to validate the function's behavior for different values of k .
Each example provides a clear task, solution, and comments to guide the learner through the process of writing and understanding unit tests in Java.
These exercises range from basic array operations to more complex tasks like array rotation, covering different aspects of array manipulation and testing.
Additional Unit Testing Resources
- Java Unit Testing Guide
- What is Debugging?
- How to Debug Java Code
- A Beginner's Guide to Testing

Chapter 2: File Handling and Input/Output (I/O)
File handling in java using filewriter and filereader.
File handling is an essential aspect of programming, especially when it comes to reading from and writing to files.
In Java, file handling is accomplished using various classes and methods provided by the language's standard library. One such set of classes is FileWriter and FileReader , which are specifically designed for handling textual data.
This chapter explores the concepts and techniques involved in file handling using FileWriter and FileReader in Java.
We will discuss the importance of character streams and why choosing the right stream, such as FileWriter and FileReader , is crucial for working with textual data. We'll also delve into the constructors and methods of these classes, explore practical demonstrations, and provide exercises to enhance your understanding and proficiency in Java file handling.
What is FileWriter ?
FileWriter is a class in Java that is used for writing character-based data to a file. It is a subclass of the OutputStream class, which allows for the writing of byte-based data.
FileWriter is specifically designed for handling textual data and provides convenient methods for writing characters, character arrays, and strings to a file.
Constructors of FileWriter :
There are several constructors available in FileWriter for creating instances of the class. These constructors provide flexibility in specifying the file to be written, the character encoding to be used, and the buffer size for efficient writing. The constructors include options for passing a File object, a FileDescriptor, or a String representing the file path.
It is important to choose the appropriate constructor based on the specific use case. For example, using the File constructor allows for easy manipulation of file properties, while the String-based constructor provides a more convenient way to specify the file path. Also, specifying the character encoding and buffer size can greatly impact the performance and behavior of the FileWriter .
Methods of FileWriter :
FileWriter provides various methods for writing data to a file. The key methods include write() , flush() , and close() .
The write() method allows for writing single characters, character arrays, and strings to the file. It provides flexibility in appending data to an existing file or overwriting the content of the file.
The flush() method is used to flush any buffered data to the file. This ensures that all data is written immediately and not held in memory.
The close() method is used to close the FileWriter and release any system resources associated with it. It is important to always close the FileWriter after writing to ensure that all data is properly written and resources are freed.
Enhancing Performance with BufferedWriter:
To improve the performance of writing data to a file, you can use FileWriter in conjunction with BufferedWriter . BufferedWriter is a class that provides buffering capabilities, reducing the number of system calls and improving overall efficiency.
By wrapping the FileWriter with a BufferedWriter , data can be written to a buffer first, and then flushed to the file when necessary. This reduces the overhead of frequent disk writes and can significantly enhance the performance of file writing operations.
What is FileReader ?
FileReader is an important class in Java that specializes in reading character streams from a file. It is a subclass of the InputStreamReader class, which is responsible for converting byte streams into character streams.
FileReader inherits the functionality of InputStreamReader and provides additional methods specifically designed for reading textual data from a file.
Constructors of FileReader
FileReader offers several constructors that allow for different file access scenarios. These constructors provide flexibility in specifying the file to be read, the character encoding to be used, and the buffer size for efficient reading.
You can choose the appropriate constructor depending on your use case. For example, a FileReader instance can be created by passing a File object, a FileDescriptor, or a String representing the file path.
Methods of FileReader
FileReader provides various methods for reading data from a file. The read() method is the primary method used for reading characters from a file. It returns the next character in the file as an integer value, or -1 if the end of the file has been reached.
FileReader also provides a close() method to release any system resources associated with the FileReader instance. It also allows for handling IOExceptions, which are exceptions that may occur during file reading operations.
Java Code to Demonstrate FileWriter
Hands-on exercises and real-world applications, how to write to a file using filewriter.
Task : Create a program to write a list of students' names to a text file.
Exercise : Modify the program to append new students to the existing list without overwriting the current data.
How to Read from a File using FileReader
Task : Create a program to read the contents of the "students.txt" file created above and display them on the console.
Now, let's look at some practical code examples for common pitfalls in file handling using Java's FileWriter and FileReader classes, along with solutions:
File Not Found:
- Pitfall : Attempting to read from or write to a file that doesn't exist.
- Solution : Always check if the file exists before performing read/write operations. Use the File class to create a new file if it does not exist.
Incorrect File Paths:
- Pitfall : Using incorrect file paths leading to FileNotFoundException .
- Solution : Use absolute paths for clarity or ensure the relative path is correct. Pay attention to cross-platform path separators.
Resource Leakage:
- Pitfall : Not closing FileWriter or FileReader properly, which can lead to resource leakage.
- Solution : Use try-with-resources to ensure that file resources are automatically closed.
Overwriting File Content:
- Pitfall : Accidentally overwriting existing file content.
- Solution : Use the FileWriter constructor that allows for appending content ( new FileWriter("filename.txt", true) ).
Character Encoding Issues:
- Pitfall : Issues with character encoding leading to corrupted file data.
- Solution : Be aware of the platform's default charset. Specify charset explicitly if handling non-text files or special character sets.
Buffering for Performance:
- Pitfall : Inefficient file writing/reading operations.
- Solution : Use BufferedWriter or BufferedReader for efficient reading and writing operations.
These examples demonstrate practical solutions to overcome common challenges encountered in file handling in Java.
File handling is a fundamental aspect of programming, and in Java, it can be effectively accomplished using the FileWriter and FileReader classes.
FileWriter is specifically designed for writing character-based data to a file, offering convenient methods for writing characters, character arrays, and strings. On the other hand, FileReader specializes in reading character streams from a file, providing additional methods for reading textual data.
Byte Streams vs Character Streams
In this section, you'll learn about the concept of streams in Java. Streams are an essential part of the Java I/O (Input/Output) model, allowing the transfer of data between a program and an external source or destination.
There are two main types of streams in Java: Byte Streams and Character Streams.
Byte Streams are used for 8-bit byte operations and are commonly employed for reading and writing binary data. They are particularly useful when dealing with files or streams that contain non-textual information, such as images or audio files.
Examples of key Java classes associated with Byte Streams include FileInputStream and FileOutputStream .
On the other hand, Character Streams are designed for 16-bit Unicode operations and are primarily used for reading and writing textual data. They are especially suitable when working with text files or when you need to handle character-based input or output.
Important Java classes for Character Streams include FileReader and FileWriter .
Advantages and Limitations of Byte and Character Streams
To effectively utilize Byte Streams and Character Streams in your Java programs, here are some practical recommendations:
- Choose the appropriate stream type based on the nature of your data. If you are working with binary data or non-textual information, Byte Streams provide efficient operations for handling such data. But if your application primarily deals with textual data, such as log files or user-generated content, Character Streams are the recommended choice.
- Use the appropriate Java classes associated with each stream type. For Byte Streams, use classes like FileInputStream and FileOutputStream for reading from and writing to files. For Character Streams, use classes like FileReader and FileWriter for reading and writing text data.
- Handle exceptions properly and close streams to avoid resource leaks. This ensures smooth data transfer and manipulation, enhancing the overall performance and reliability of your Java applications.
Byte Stream and Character Stream Code Examples
Here's an advanced code example that demonstrates the use of Byte Streams and Character Streams in Java:
In this code example, we have two sections: one demonstrating the use of Byte Streams and another demonstrating the use of Character Streams.
For Byte Streams, we use FileInputStream to read binary data from an input file ( input.txt ). We read the data in chunks using a byte buffer and process the data (in this case, encrypting it). Then, we use FileOutputStream to write the encrypted data to an output file ( output.txt ).
For Character Streams, we use FileReader to read text data from the same input file. We read the data line by line using a BufferedReader , process the data (in this case, converting it to uppercase), and use FileWriter and BufferedWriter to write the processed data to the output file.
These examples showcase the practical use of Byte Streams and Character Streams for handling binary and textual data, respectively.
Remember to handle exceptions properly and close the streams after use to ensure efficient and reliable stream-based operations in your Java programs.
When choosing between Byte Streams and Character Streams in Java, consider the nature of your data and the specific requirements of your application.
For non-textual or binary data, use Byte Streams. For textual data, use Character Streams. Handle exceptions properly and close streams after use.
By understanding the advantages and limitations of each stream type, you can make informed decisions and ensure efficient data processing in your Java applications.
How to Handle Exceptions in I/O
Java exception basics.
In the realm of Java programming, understanding exceptions is crucial for writing reliable and maintainable code. Exceptions in Java refer to conditions that disrupt the normal flow of a program. They are classified based on their nature to handle errors or exceptional situations that arise during runtime.
Java handles exceptions using "try-catch" blocks, allowing programmers to isolate and manage error conditions effectively. This understanding is key to anticipating and addressing potential issues, leading to more robust code.
Familiarity with the wide range of Java exceptions is important for precise error reporting and targeted handling. Best practices in throwing exceptions include adhering to Java’s syntax and guidelines, and judicious use of custom exceptions to improve code clarity and maintainability.
Exception handling extends beyond "try-catch" blocks. The "finally" block is used for cleanup operations, ensuring resource release regardless of exception occurrence. Nested try-catch structures provide fine-grained control over error management.
Anatomy of a Java Exception
In Java, we can use the try-catch blocks to isolate and handle exceptions. Here's an example:
By catching the exception, we can gracefully recover from error conditions and prevent our program from crashing.
Java provides a wide range of exception types to choose from. Let's say we have a method that reads data from a file. We can handle specific exceptions that might occur, such as FileNotFoundException and IOException . Here's an example:
By handling specific exceptions, we can provide more precise error reporting and targeted exception handling.
In addition to try-catch blocks, we can use the finally block for cleanup operations. For example, if we open a file in the try block, we can ensure that the file is properly closed in the finally block, regardless of whether an exception occurs. Here's an example:
Nested try-catch structures provide fine-grained control over error management. We can handle exceptions at different levels, depending on the specific needs of our program. Here's an example:
By understanding these concepts and applying best practices, we can write robust and error-resistant Java code.
Remember to keep code simplicity in mind. By applying practical advice and taking action, reliable and maintainable Java applications can be built.
Throwing Exceptions
When it comes to handling exceptions in Java, it is essential to understand the syntax for throwing exceptions, creating custom exceptions, and following best practices.
To throw an exception in Java, you can use the throw keyword followed by the exception object. This allows you to explicitly indicate that a specific error condition has occurred. For example:
By throwing exceptions, you can provide more detailed and meaningful error messages to assist in troubleshooting and debugging.
Creating custom exceptions in Java enables you to handle specific error scenarios in a more precise and targeted manner. By extending the Exception class or one of its subclasses, you can define your own exception types. For example:
Custom exceptions can be useful for encapsulating complex logic or specific error conditions within your code. They improve code readability and make it easier to identify and handle exceptional situations.
To ensure effective exception handling, it is important to follow best practices. Here are a few recommendations:
- Be specific in exception handling : Catch exceptions at the right level of abstraction to handle them appropriately. Consider the specific exception types that can be thrown and handle them accordingly.
- Provide meaningful error messages : Exception messages should clearly indicate the cause and context of the error. This helps developers understand and resolve issues more efficiently.
- Keep exception handling minimal : Only catch exceptions that you can handle effectively. Rethrowing or propagating exceptions may be necessary in some cases to allow higher-level code to handle them appropriately.
- Clean up resources : Use the finally block to release resources that were acquired within a try block, ensuring proper cleanup regardless of whether an exception occurs.
- Log exceptions : Logging exceptions helps in diagnosing and troubleshooting issues. Include relevant information such as stack traces, input values, and any other contextual details that may assist in resolving the problem.
Here's an advanced code example that demonstrates exception handling in Java:
In this example, the FileProcessor class has a method processFile() that reads lines from a file. It uses a try-with-resources block to automatically close the BufferedReader after processing the file. If the file is not found or an error occurs while reading the file, the corresponding exceptions ( FileNotFoundException and IOException ) are caught and handled. The exceptions are also rethrown to allow the higher-level code (in this case, the main() method) to handle them if needed.
Unchecked Exceptions
Unchecked exceptions are exceptions that do not require explicit handling by the programmer. They are subclasses of the RuntimeException class or its subclasses.
Unchecked exceptions are often caused by programming errors or unexpected conditions that may occur during runtime. Examples of unchecked exceptions include NullPointerException , ArrayIndexOutOfBoundsException , and IllegalArgumentException .
When dealing with unchecked exceptions, it is important to follow best practices to prevent these exceptions from occurring. This includes validating inputs and ensuring proper error handling and defensive programming.
Checked Exceptions
Checked exceptions are exceptions that must be explicitly handled or declared in the method signature using the throws keyword. They are subclasses of the Exception class (excluding subclasses of RuntimeException ).
Checked exceptions are typically used for conditions that are beyond the control of the program, such as I/O errors or network failures. Examples of checked exceptions include IOException , SQLException , and FileNotFoundException .
When handling checked exceptions, it is important to consider the appropriate handling strategy based on the specific situation. This may involve wrapping the checked exception in a custom unchecked exception, logging the exception, or propagating the exception to higher-level code for handling.
Example Code – Unchecked and Checked Exceptions
Here are additional examples that demonstrate the handling of unchecked and checked exceptions:
Unchecked Exception Example:
In this example, the divide method calculates the result of dividing the dividend by the divisor . If the divisor is zero, an unchecked exception of type ArithmeticException is thrown. This ensures that the code explicitly handles the case where division by zero occurs.
Checked Exception Example:
In this example, the readFile method reads the contents of a file specified by the fileName parameter. The method declares that it may throw an IOException (a checked exception) using the throws keyword. This allows the caller of the method to handle the exception or propagate it further up the call stack.
Understanding the differences between unchecked and checked exceptions is essential for effective exception handling in Java. By following best practices, handling exceptions appropriately, and considering the specific needs of your application, you can write robust and reliable Java code.
Remember to continuously improve your exception handling skills and stay up to date with industry best practices to ensure the highest quality in your code.
Real-World Examples of Exception Handling:
Here are some additional code examples for each of the topics we've just discussed:
Practical Applications in Java Applications:
Common scenarios for exception handling:, learning from real-world cases:.
These examples demonstrate various scenarios where exception handling is commonly applied in Java applications. The comments in the code provide explanations and instructions for each scenario.
Remember to adapt the code to your specific needs and handle exceptions according to your application's requirements.
Advanced Exception Handling Techniques
When it comes to advanced exception handling techniques in Java, there are several key aspects to consider.
Utilizing the throws Keyword: The throws keyword is used to indicate that a method may throw a particular exception. By declaring checked exceptions in the method signature, we can ensure that the calling code handles or propagates the exception.
This has a significant impact on code design and maintenance. Proper use of the throws keyword promotes clarity and forces developers to consider exception handling requirements upfront. It also allows for more modular and flexible code, as exceptions can be handled at different levels in the call stack.
Exception Chaining and Cause Analysis: Exception chaining involves linking exceptions together to provide a comprehensive view of the error chain. By utilizing exception chaining, we can identify the root cause of an exception and facilitate effective troubleshooting.
Techniques such as logging stack traces and analyzing exception causes enable us to gain insights into the underlying issues.
Real-world use cases for exception chaining include debugging complex scenarios and providing detailed error reports to aid in issue resolution.
Familiarize yourself with various best practices : Writing robust and error-resistant code involves following best practices for exception handling. It is important to handle exceptions at the appropriate level of abstraction, providing meaningful error messages and logging relevant information.
Avoiding common mistakes, such as catching exceptions unnecessarily or swallowing exceptions, ensures that exceptions are properly addressed.
Logging and Diagnosing Exceptions: Logging exceptions plays a vital role in diagnosing and troubleshooting issues. By integrating logging with exception handling, we can capture valuable information such as stack traces, input values, and contextual details. This facilitates efficient debugging and helps in resolving problems effectively.
Utilizing tools and strategies for effective logging and diagnosis enhances the error analysis process and aids in producing actionable insights.
Advanced Scenarios: By employing techniques such as multi-catch blocks or handling exceptions at different levels, we can effectively manage multiple exceptions.
Resource management in exceptions is another crucial aspect, ensuring that resources are properly released even in the presence of exceptions.
Exception handling in concurrent programming requires careful synchronization and error handling strategies to maintain data integrity and prevent race conditions.
Advanced and Custom Exception Handling Case Studies:
Analyzing real-world examples of exception handling can provide valuable insights. By studying industry cases, we can learn from successful approaches and identify common patterns. Analyzing exception handling patterns allows us to apply proven techniques and adapt them to our specific needs.
By solving complex problems with exception handling, we can develop expertise in handling challenging scenarios and build robust applications.
Remember, when writing code, it is important to keep it simple and concise. Use clear and straightforward examples to illustrate concepts. By applying practical advice and continuously improving your exception handling skills, you can develop reliable and maintainable Java applications.
Here's an example code snippet that demonstrates the use of custom exceptions and exception handling techniques:
In this example, the FileValidator class demonstrates the use of a custom exception, FileValidationException , which is thrown when a file fails validation. The validateFile method catches any IOException that occurs during file validation and rethrows it as a FileValidationException to provide a clear and meaningful error message. The Main class demonstrates the handling of the custom exception, allowing for specific error reporting and appropriate exception handling.
By applying these techniques and principles, you can effectively handle exceptions in Java and develop high-quality code. Remember to always strive for simplicity, clarity, and continuous improvement in your exception handling practices.

Deadlock is a situation in Java multithreading where two or more threads are blocked forever, waiting for each other to release resources. Understanding deadlock is crucial for writing robust concurrent code.
There are four necessary and sufficient conditions for a deadlock to occur: mutual exclusion, hold and wait, no preemption, and circular wait.
- Mutual exclusion means that a resource can only be used by one thread at a time.
- Hold and wait refers to a situation where a thread holds a resource and is waiting to acquire another resource.
- No preemption implies that resources cannot be forcefully taken away from a thread.
- Circular wait occurs when a cycle of threads exists, where each thread is waiting for a resource that is held by another thread in the cycle.
To better illustrate this concept, consider the following code snippet:
In this example, two threads call method1 and method2 concurrently. If one thread acquires resource1 and waits for resource2 , while the other thread acquires resource2 and waits for resource1 , a deadlock occurs.
To avoid deadlocks, it is essential to carefully manage resources and their acquisition order. One practical approach is to ensure a consistent and predefined order for acquiring locks. By avoiding circular wait and ensuring a consistent lock ordering, deadlocks can be prevented.
Remember to always minimize lock contention and unnecessary locks. Additionally, utilize concurrency utilities such as ReentrantLock and Semaphore to manage locks effectively.
Deadlock Example
Complex deadlock scenarios involve intricate situations where multiple threads and resources are entangled, making detection and resolution more challenging. Let's explore an example to better understand this concept in the context of Java programming.
Consider the following code snippet that demonstrates a potential deadlock scenario:
In this example, three threads, let's call them Thread A, Thread B, and Thread C, call method1 and method2 concurrently. If Thread A acquires resource1 and waits for resource2 , Thread B acquires resource2 and waits for resource3 , and Thread C acquires resource3 and waits for resource1 , a complex deadlock occurs. All threads are stuck in a state of indefinite waiting, unable to proceed.
To avoid such complex deadlocks, it becomes even more crucial to carefully manage resources and their acquisition order.
One practical approach is to establish a consistent and predefined order for acquiring locks. By doing so, we can prevent circular wait conditions and ensure a smooth execution of concurrent code.
To solve this issue, you need to ensure that all methods acquire the locks in the same order. Here’s the corrected code:
In this corrected code, both method1 and method2 acquire locks on resource1 , resource2 , and resource3 in the same order, which prevents the deadlock. This strategy is known as lock ordering — a simple yet effective way to prevent deadlocks.
It’s a good practice to always acquire locks in the same order throughout your program. This way, if a thread holds one lock and requests another, you can be sure that no other threads are holding or requesting locks in the opposite order. This eliminates the circular wait condition, and thus, the deadlock.
Remember, the order of releasing the locks doesn’t matter in preventing deadlocks. It’s the order of acquiring locks that’s crucial.
To resolve the potential deadlock in the provided example, we can modify the order of acquiring locks in either method1 or method2 . By consistently acquiring resources in the same order across all methods, we eliminate the possibility of circular wait and mitigate the risk of deadlock.
How to Detect and Analyze Deadlocks
To detect deadlocks in Java, you can analyze thread dumps. Thread dumps provide valuable information about the state of threads, including their locks and waiting conditions. By carefully examining the thread dump, you can identify if any threads are stuck in a deadlock situation.
One useful tool for deadlock detection is the jstack command. This command allows you to generate a thread dump of a Java application. You can then analyze the thread dump to identify any potential deadlocks.
Here's an example of how you can use the jstack command to detect deadlocks in a Java application:
In this command, <pid> represents the process ID of the Java application. By running this command, you will obtain a thread dump that can be analyzed for deadlock situations.
By being proactive in detecting deadlocks and utilizing tools like jstack , you can quickly identify and address potential issues in your Java code.
Remember, when it comes to deadlocks, prevention is key. Be mindful of your resource acquisition order and avoid circular wait conditions. Additionally, consider using concurrency utilities like ReentrantLock and Semaphore to manage locks effectively.
How to Resolve Deadlocks
To resolve deadlocks, there are two main strategies you can employ: breaking the deadlock cycle and refactoring the code to eliminate circular wait conditions.
Breaking the deadlock cycle involves identifying the resources involved in the deadlock and implementing a strategy to break the cycle.
One approach is to define a global ordering of resources and ensure that all threads acquire resources in the same order. By doing so, you eliminate the possibility of circular wait and allow the threads to proceed without deadlock.
Here's an example of how you can break the deadlock cycle:
In this example, we have modified the code to ensure that both method1 and method2 acquire resources in the same order: resource1 followed by resource2 . By maintaining this consistent lock ordering across all methods, we break the deadlock cycle and allow the threads to execute without deadlock.
Another strategy is to refactor the code to eliminate circular wait conditions. This involves restructuring the code to remove the dependency between resources that leads to deadlock. By carefully analyzing the resource dependencies and redesigning the code, you can eliminate the possibility of circular wait and prevent deadlocks.
Here's an example:
In this refactored code, we have removed the nested locks and ensured that each resource is acquired and released independently. By doing so, we eliminate the possibility of circular wait and mitigate the risk of deadlock.
How to Prevent Deadlocks
Avoiding nested locks:.
To prevent deadlock conditions, avoid using nested locks in your code. Nested locks occur when a thread acquires a lock while holding another lock. This can lead to a situation where multiple threads are waiting for each other to release the locks they hold, resulting in a deadlock.
Instead of using nested locks, consider restructuring your code to acquire locks in a more organized and controlled manner. By acquiring locks one at a time and releasing them promptly, you can minimize the chances of deadlocks occurring. Let's take a look at an example:
In this example, the code has been refactored to eliminate nested locks. Each method now acquires and releases a single lock independently. This approach ensures that threads can execute their operations without getting stuck in a deadlock situation.
Lock Ordering:
Consistent ordering of lock acquisition is another effective technique to prevent deadlocks. By establishing a predefined order for acquiring locks across all threads, you eliminate the possibility of circular wait conditions.
When designing your code, carefully analyze the dependencies between resources and determine a logical order for acquiring locks. By consistently following this order, you ensure that threads acquire locks in a predictable manner, minimizing the risk of deadlocks.
Consider the following example:
In this code snippet, both method1 and method2 acquire locks in the same order: first lock1 and then lock2 . By consistently following this lock acquisition order across all methods, you eliminate the possibility of circular wait conditions and ensure a smooth execution of concurrent code.
Timeouts and Try-Lock:
Using timeouts and try-lock mechanisms can help you avoid indefinite waiting, which can potentially lead to deadlocks.
By setting a timeout on lock acquisition attempts or using try-lock methods, you can prevent threads from waiting indefinitely for a lock to become available.
In this revised code, the methods method1 and method2 use a try-lock mechanism to acquire locks. If a lock is not immediately available, the thread does not wait indefinitely but proceeds to perform other operations. This approach helps prevent deadlocks by ensuring that threads do not get stuck waiting for locks indefinitely.
By following these practical techniques, such as avoiding nested locks, establishing consistent lock ordering, and utilizing timeouts and try-lock mechanisms, you can significantly reduce the risk of deadlocks in your Java multithreading code.
Best Practices for Avoiding Deadlocks
To minimize lock contention and avoid unnecessary locks, it is important to follow best practices in Java multithreading. By using these techniques, you can improve the efficiency and performance of your concurrent code.
Minimize the Scope of Locks
One effective practice is to minimize the scope of locks. Only synchronize the critical sections of code that require exclusive access to shared resources. By reducing the number of code blocks that are synchronized, you can minimize the chances of contention and improve the overall throughput.
Use Thread Joins Wisely
Another useful practice is to use thread joins wisely. Thread joining is a mechanism that allows one thread to wait for the completion of another thread.
But it's important to be cautious when using thread joins, as incorrect usage can lead to deadlocks. Make sure to avoid situations where threads are waiting indefinitely for each other to complete, as this can result in a deadlock. Instead, carefully design your code to ensure proper synchronization and coordination between threads.
Use Concurrency Utilities
Java provides several concurrency utilities, such as ReentrantLock , Semaphore , and other synchronization classes, that can help manage locks effectively. These utilities offer more flexibility and control over locking mechanisms compared to traditional synchronized blocks.
For example, ReentrantLock allows for finer-grained locking and enables features like fairness and interruptibility. Similarly, Semaphore provides a convenient way to control access to shared resources by limiting the number of threads allowed to enter a critical section simultaneously.
Here's an example code snippet that demonstrates the use of ReentrantLock :
In this example, the ReentrantLock is used to synchronize the critical section of code. By acquiring the lock before entering the critical section and releasing it afterward, you ensure exclusive access to shared resources.
Advanced Deadlock Topics
Deadlocks can occur not only within a single JVM but also in distributed systems. It is important to broaden our understanding of deadlocks to include their occurrence in distributed environments. In such scenarios, multiple processes or nodes may compete for shared resources, leading to potential deadlocks.
To address deadlocks in distributed systems, it is crucial to carefully design the communication and coordination mechanisms between nodes.
One effective approach is to utilize message-based communication protocols, such as asynchronous messaging or event-driven architectures. These protocols can help minimize the chances of resource contention and reduce the risk of deadlocks.
Also, modern Java features and frameworks offer valuable tools to address deadlock and concurrency issues.
For example, the CompletableFuture class provides a convenient way to handle asynchronous computations and avoid blocking threads. By leveraging CompletableFuture and other similar features, you can ensure efficient and non-blocking execution of concurrent code.
Let's take a look at an example code snippet that demonstrates the use of CompletableFuture :
In this example, the CompletableFuture class is used to perform asynchronous computations. By using the supplyAsync method, you can execute the computations in a separate thread and obtain a CompletableFuture object that represents the result. This approach helps minimize the chances of deadlocks by avoiding the blocking of threads.

Imagine you're an architect tasked with building a variety of houses, from simple one-bedroom homes to complex mansions with intricate designs.
Just like in architecture, where a set of blueprints offers proven solutions for building robust and aesthetically pleasing structures, Java Design Patterns provide software developers with time-tested methodologies and blueprints for crafting efficient and scalable software applications.
Why Java design patterns are still important in Software Development:
- Universal Blueprint for Problem-Solving : Think of design patterns as the Swiss Army knife in a developer's toolkit. They are like those secret recipes that chefs pass down through generations – each pattern is a recipe for solving a specific design problem in a proven way.
- Timeless Relevance : Like the classic principles of art that never go out of style, Java Design Patterns have stood the test of time. They are like the underlying principles of physics that remain constant, irrespective of the evolving technological landscape.
- Enhances Communication : Using design patterns is akin to musicians using sheet music. They provide a universal language for developers. This shared vocabulary cuts through complexity, much like a well-drawn map simplifies navigation in unknown terrain.
- Principles of Good Design Embedded : These patterns are more than just templates – they are a manifestation of wisdom gathered over decades, much like the principles of good governance that stand the test of time in societies.
- Maintenance and Evolution : Imagine building with LEGO blocks. Design patterns allow software to be as adaptable and maintainable as rearranging LEGO structures, ensuring that systems can evolve gracefully as requirements change.
Overview of Java Design Patterns
- Singleton Pattern : Like a unique key to an exclusive club, this pattern ensures that there's only one instance of a class, providing a single point of access to it.
- Factory Method Pattern : Picture a master artisan who creates a template for an artifact. Subsequent artisans follow this template but add their unique touch, much like this pattern allows for creating objects with a common interface.
- Abstract Factory Pattern : This pattern is like a blueprint for a series of factories; each factory creates objects that, while different, share some common traits.
- Builder Pattern : Imagine a kit for building a model airplane. You can choose different parts for different versions of the plane. The Builder pattern lets you construct complex objects step-by-step, like using such a kit.
- Prototype Pattern : This is like having a master copy, and instead of building from scratch, you make duplicates of this master copy as needed.
- Adapter Pattern : Think of this as a travel adapter that lets you charge your phone anywhere in the world; the Adapter pattern allows otherwise incompatible interfaces to work together.
- Composite Pattern : Much like a painter who sees no difference between a single brushstroke and a complex mosaic, this pattern lets you treat individual objects and compositions uniformly.
- Proxy Pattern : Like a gatekeeper who controls access to a VIP, the Proxy pattern acts as an intermediary, controlling access to another object.
- Observer Pattern : It’s like a news alert service; whenever something newsworthy happens, you get notified. This pattern allows objects to notify others about changes in their state.
- Strategy Pattern : Imagine you’re a strategist in a game, constantly changing your tactics based on the situation. The Strategy pattern lets software change its algorithms dynamically, much like a strategist adapts their approach to shifting conditions on the battlefield.
Each of these design patterns is a tool in the software developer's toolbox, ready to be deployed to tackle specific types of problems. By understanding and utilizing these patterns, developers can create software that is not only robust and efficient but also elegant and easy to maintain.
Just like the right tool can make a difficult task easy, the right design pattern can simplify complex coding challenges and lead to more effective and maintainable code.
Let's explore each of these patterns in more detail in the following sections, uncovering the secrets of their enduring power and versatility in the world of software development.
1. Singleton Pattern
The Singleton pattern addresses the problem of managing access to a resource that should have only one instance, such as a database connection. It ensures that only one instance of a class is created and provides a global access point to that instance. The Singleton pattern restricts object creation for a class to a single instance, which is managed by the class itself.
Singleton pattern is like having a key that unlocks a special treasure room. The key is unique and there can only be one key to access the treasure room. No matter how many people have the key, they all have access to the same treasure room. This ensures that everyone uses the same instance of the treasure room and prevents multiple instances from being created.
In Java, you can implement the Singleton pattern using a private constructor, a static method to return the instance, and a private static field to hold the single instance. Here's an example:
Using the Singleton pattern provides controlled access to the single instance, ensuring that all parts of the system use the same instance. However, it can be challenging to debug due to its global nature.
When using the Singleton pattern, consider its impact on a multi-threaded environment. Synchronization is necessary to make the getInstance() method thread-safe and prevent multiple instances from being created concurrently.
Keep in mind that design patterns are not strict rules to follow, but rather guidelines that can be adapted to fit your needs. Use them wisely and consider the trade-offs they entail in terms of complexity and maintainability.
2. Factory Method Pattern
The Factory Method pattern addresses the need for creating objects through an interface while allowing subclasses to determine the specific type of objects to be instantiated. It promotes loose coupling by delegating the responsibility of object creation to subclasses.
Imagine a scenario where different chefs are preparing their own versions of a dish. Each chef represents a subclass in the Factory Method pattern, and the dish represents the object being created. The interface acts as the recipe or guidelines for creating the dish.
Here's an example in Java:
In this example, the Product interface defines the method use() , which represents the behavior of the created objects. The ConcreteProductA and ConcreteProductB classes implement this interface and provide their own implementations of the use() method.
The Creator class is an abstract class that acts as the factory. It declares the createProduct() method, which is responsible for creating the specific type of product. The doSomething() method demonstrates how the factory method is used to create and use the product.
By using the Factory Method pattern, you gain flexibility in object creation. You can easily introduce new subclasses to create different types of products without modifying the existing code. But keep in mind that introducing too many subclasses can introduce complexity and make the code harder to maintain.
An analogy for the Factory Method pattern is like having a restaurant with different chefs specializing in various dishes. The restaurant provides the interface, specifying the general guidelines for creating the dishes. Each chef represents a subclass that creates their unique version of the dish based on the provided guidelines.
Design patterns are not strict rules to follow, but rather guidelines that can be adapted to fit your needs. Use them wisely, considering the trade-offs they entail in terms of complexity and maintainability.
3. Abstract Factory Pattern
The Abstract Factory pattern addresses the problem of creating families of related or dependent objects without specifying their concrete classes. It allows the creation of objects through interfaces, promoting consistency among products while allowing flexibility in their implementation.
Imagine different car factories producing various car models. Each factory represents a concrete factory in the Abstract Factory pattern, and the car models represent the related objects being created. The abstract factory acts as the blueprint or guidelines for creating these car models.
To implement the Abstract Factory pattern in Java, you can define an abstract factory interface that declares methods for creating the related objects. Each concrete factory implements this interface and provides its own implementation of the creation methods. The product interfaces represent the different types of objects that can be created by the factories.
In this example, the AbstractFactory interface declares methods for creating ProductA and ProductB objects. The ConcreteFactory1 and ConcreteFactory2 classes implement this interface and provide their own implementations of the creation methods.
The ProductA and ProductB interfaces represent the different types of objects that can be created by the factories. The ConcreteProductA1 , ConcreteProductA2 , ConcreteProductB1 , and ConcreteProductB2 classes implement these interfaces and provide their own implementations of the behavior.
By using the Abstract Factory pattern, you can create families of related objects without specifying their concrete classes. This promotes consistency among the created objects and allows for easy interchangeability between different implementations. But keep in mind that introducing too many concrete factories and products can increase complexity, so use this pattern judiciously.
4. Builder Pattern
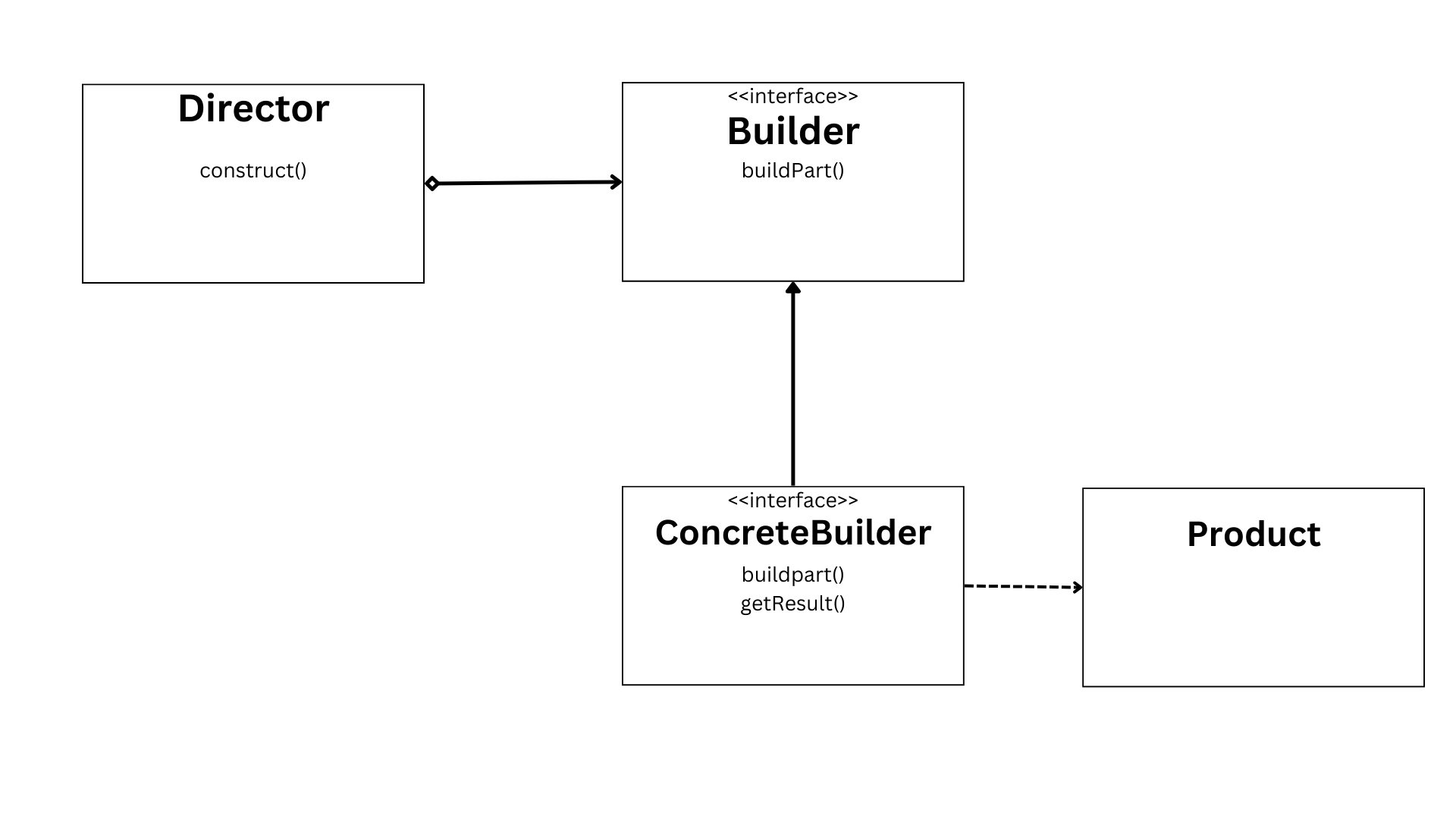
The Builder pattern is a creational design pattern that solves the problem of creating complex objects with multiple parts and configurations. It separates the construction of an object from its representation, allowing step-by-step creation of complex objects.
Imagine building a house with different construction plans. Each plan represents a concrete builder in the Builder pattern, and the house represents the complex object being created. The director acts as the blueprint or guidelines for constructing the house.
To implement the Builder pattern in Java, you can define a builder interface that declares methods for building different parts of the object. Each concrete builder implements this interface and provides its own implementation of the construction methods. The director class coordinates the construction process by invoking the builder's methods.
In this example, the Builder interface declares methods for building different parts of the complex object. The ConcreteBuilder class implements this interface and provides its own implementation of the construction methods. The Director class coordinates the construction process by invoking the builder's methods in a specific order.
By using the Builder pattern, you have more control over the construction of complex objects, allowing you to build them step by step. This pattern is particularly useful when creating objects with many optional or varied parts. However, keep in mind that introducing too many builders can increase complexity, so use this pattern judiciously.
5. Prototype Pattern
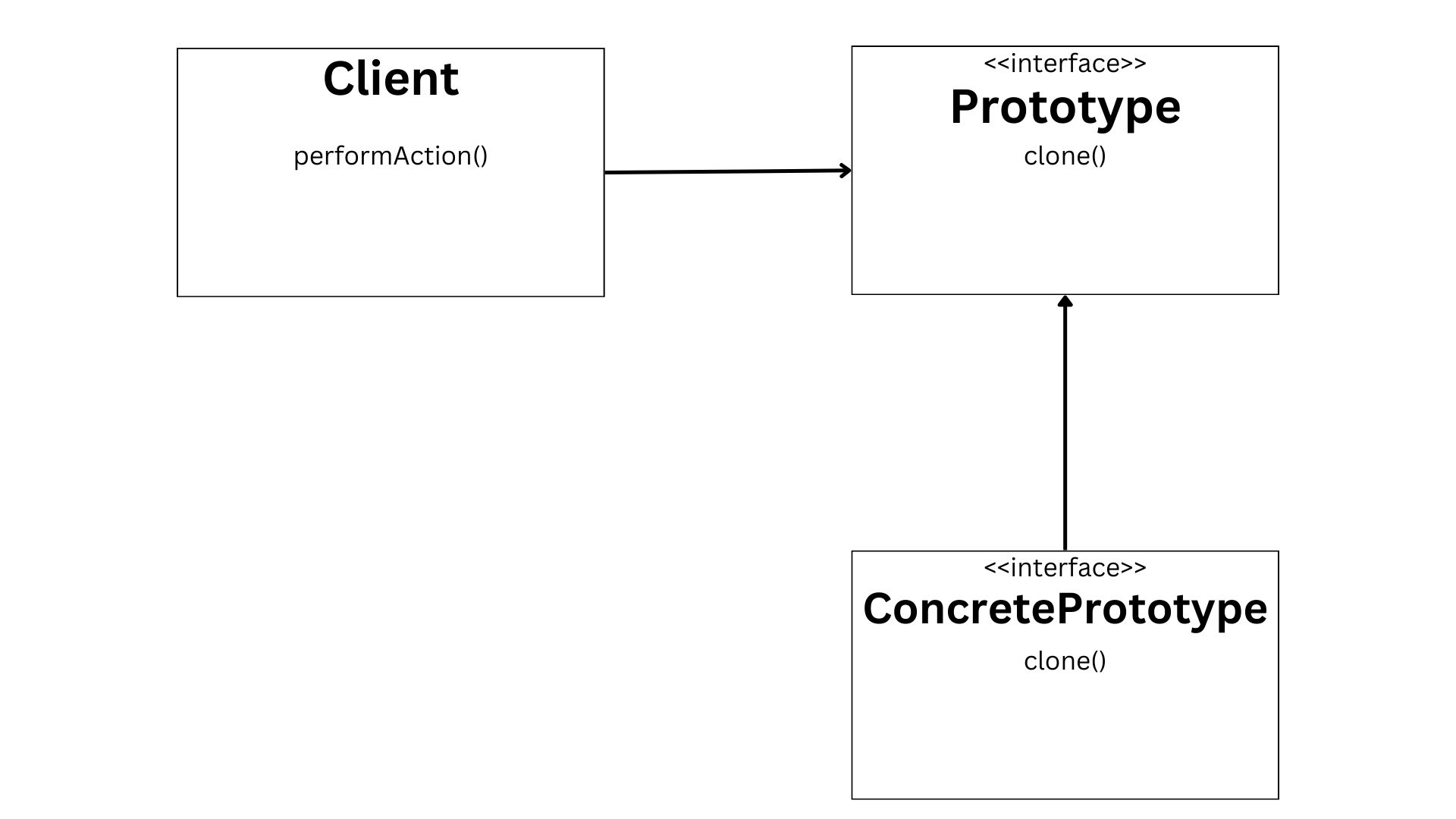
The Prototype pattern addresses the need for copying or cloning objects instead of creating new instances. It allows for the creation of new objects by copying an existing object, utilizing a prototype instance. This pattern consists of a prototype interface and concrete prototypes that implement the interface.
To understand the Prototype pattern, think of it as making photocopies of a document. The original document serves as the prototype, and the copies are created by simply duplicating the original. Similarly, the Prototype pattern allows for efficient cloning of objects by utilizing an existing instance as a blueprint for creating new instances.
In Java, you can implement the Prototype pattern by defining a prototype interface that declares a method for cloning the object. Each concrete prototype class then implements this interface and provides its own implementation of the cloning method. Here's an example:
In this example, the Prototype interface declares the clone() method for cloning the object. The ConcretePrototype class implements this interface and overrides the clone() method to perform a shallow copy of the object. The Main class demonstrates how to use the Prototype pattern by creating a concrete prototype and cloning it to obtain a new instance.
When using the Prototype pattern, keep in mind that the cloning process can become complex when involving deep cloning, where all the object's references are also cloned. It's important to handle any clone exceptions that may occur.
6. Adapter Pattern
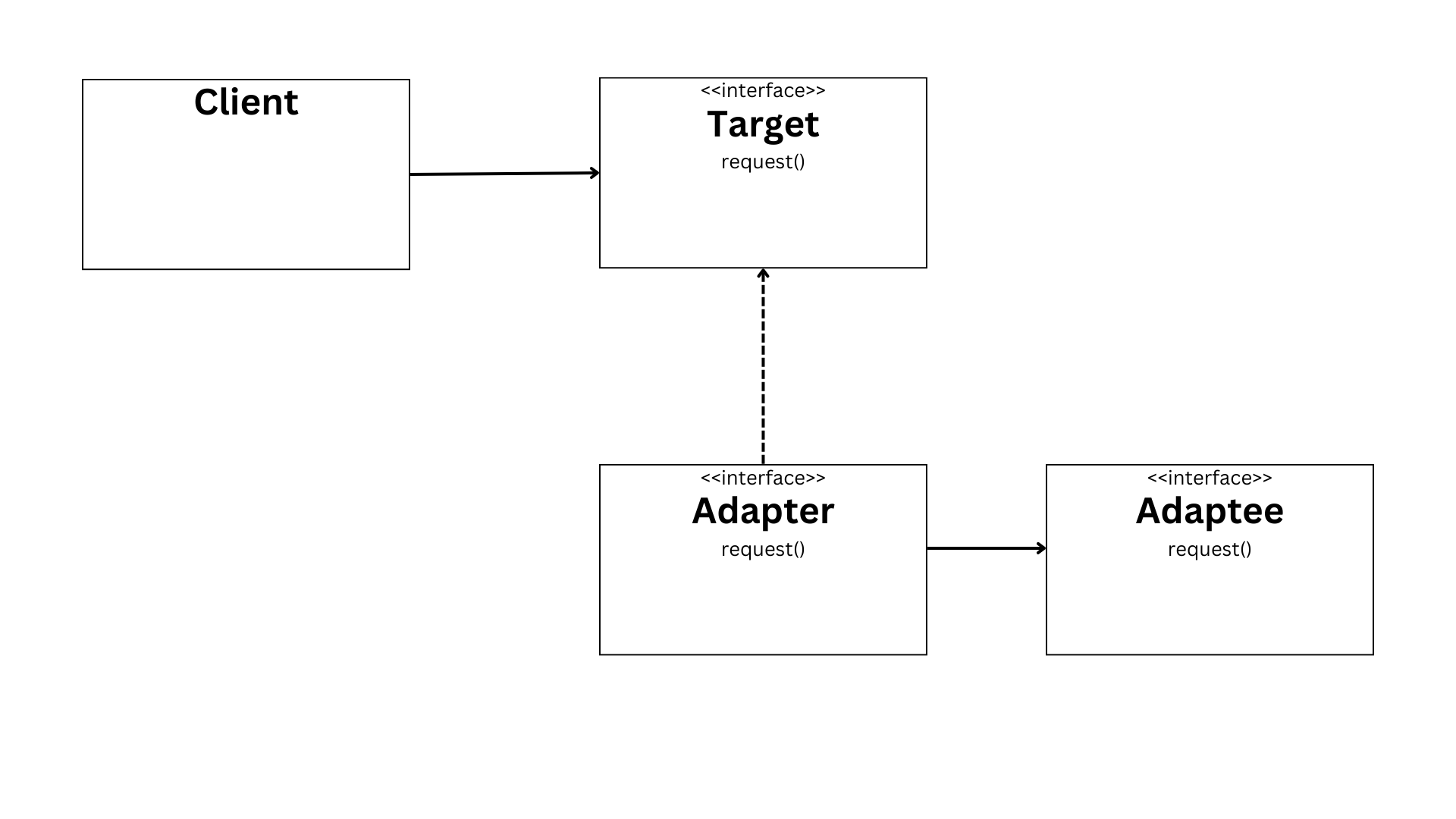
The Adapter pattern solves the problem of incompatible interfaces between classes, allowing them to collaborate effectively. It achieves this by adapting one interface to another using a middle layer called the adapter. The components involved in this pattern are the Adapter, Adaptee, and Target interface.
To understand the Adapter pattern, consider power socket adapters for different country plugs. The adapter serves as a bridge between the incompatible plug and the socket, allowing them to work together.
Similarly, the Adapter pattern enables collaboration between classes with incompatible interfaces by providing a common interface through the adapter.
Here's an example of how the Adapter pattern can be implemented in Java:
In this example, the LegacyCode interface represents the existing code with its own legacy method. The LegacyCodeImpl class implements this interface and provides the implementation of the legacy method.
The NewCode interface represents the desired new interface for the client code. The Adapter class implements this interface and contains a reference to the LegacyCode object. It adapts the new method to the existing legacy code by invoking the legacy method inside the new method.
By using the Adapter pattern, you can integrate legacy code or collaborate with classes that have incompatible interfaces. The adapter acts as a translator, enabling communication between the different components. Remember to choose meaningful names for the classes and interfaces to improve code readability.
When applying the Adapter pattern, consider the trade-offs it entails. While it allows collaboration between incompatible interfaces, it introduces an additional layer of complexity. Use this pattern judiciously and consider the specific needs of your project.
7. Composite Pattern
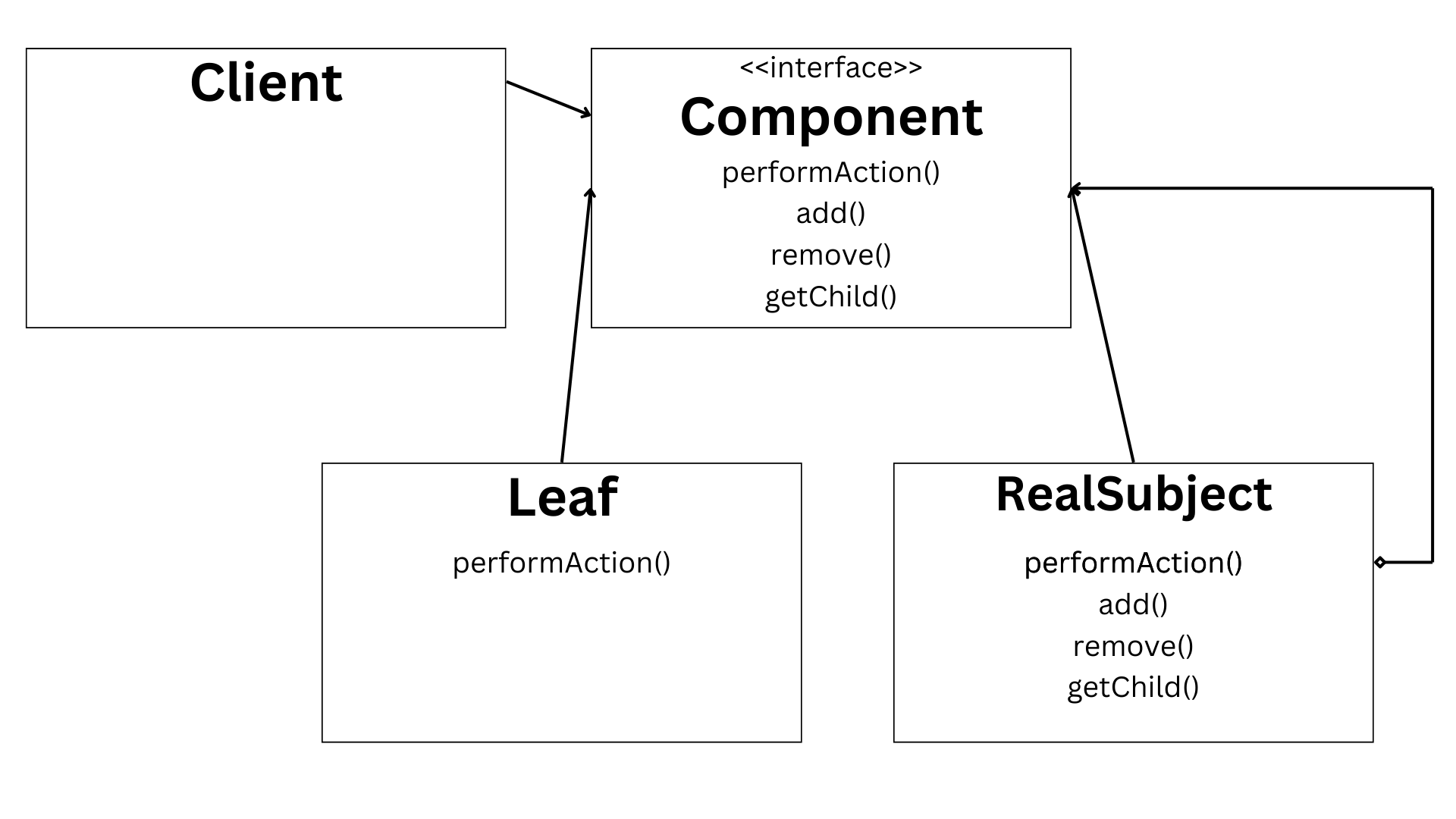
The Composite pattern addresses the problem of treating individual objects and compositions of objects uniformly. It allows us to create tree-like structures to represent part-whole hierarchies.
In this pattern, we have two types of objects: composite objects and leaf objects. Composite objects can contain other objects, including both composite objects and leaf objects. Leaf objects, on the other hand, are the building blocks of the hierarchy and cannot contain other objects.
To understand this pattern, imagine a file system where we have nested folders. The folders represent composite objects, while the files represent leaf objects. By treating folders and files uniformly, we can perform operations on them regardless of their specific type.
Here's an example implementation in Java:
In this example, the Component interface declares the operation() method that represents the operation to be performed on both composite objects and leaf objects. The Composite class implements this interface and contains a list of child components. It provides methods to add and remove child components and overrides the operation() method to perform the operation on itself and its children.
The Leaf class also implements the Component interface and provides its own implementation of the operation() method.
By using the Composite pattern, we can simplify client code by treating individual objects and compositions of objects uniformly. But we should be cautious not to make the design overly general, as it may introduce unnecessary complexity.
8. Proxy Pattern
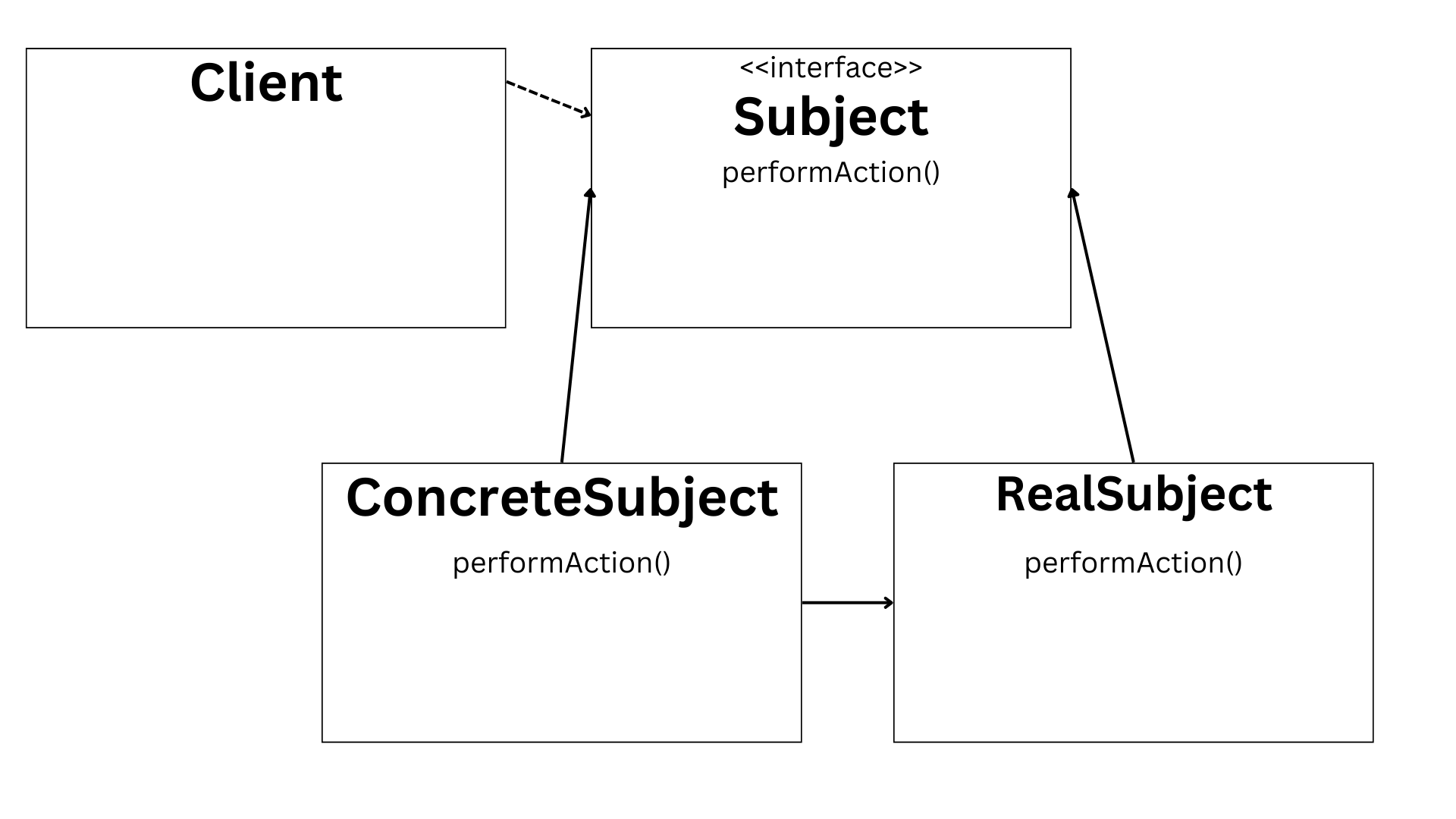
The Proxy pattern is a structural design pattern that provides a placeholder for another object. It is used to control access to an object or delay its instantiation. A common example is a bank teller acting as a proxy for bank account transactions.
To understand the Proxy pattern, let's consider a scenario where we want to access a resource-intensive object, such as a large image or a remote database. Instead of directly accessing the object, we can use a proxy to control the access and provide additional functionality if needed.
In the Proxy pattern, we have three main components: the Proxy, the Subject interface, and the RealSubject. The Proxy class acts as a middleman between the client and the RealSubject. It controls access to the RealSubject and provides any additional logic or checks before delegating the request.
In this example, the Subject interface declares the common method for the request. The RealSubject class implements this interface and provides the actual implementation of the request. The Proxy class also implements the Subject interface and acts as a proxy for the RealSubject.
When the client makes a request through the Proxy, the Proxy checks if the RealSubject has been instantiated. If not, it creates an instance of the RealSubject. The Proxy can also perform additional checks or logic before delegating the request to the RealSubject.
The Proxy pattern provides several advantages, such as controlling access to the real object, delaying the instantiation of the real object until it is actually needed, and providing additional functionality or checks. But it can introduce latency due to the extra layer of indirection.
It's important to note that the Proxy pattern is different from the Adapter pattern, which is used to bridge incompatible interfaces. The Proxy acts as a placeholder or wrapper for the real object, while the Adapter provides a different interface for an existing object.
The Proxy pattern is a powerful tool for controlling access to objects or delaying their instantiation. By using a proxy, you can add extra functionality, perform checks, or provide a simplified interface for the client. Just be cautious of the potential latency introduced by the proxy.
9. Observer Pattern
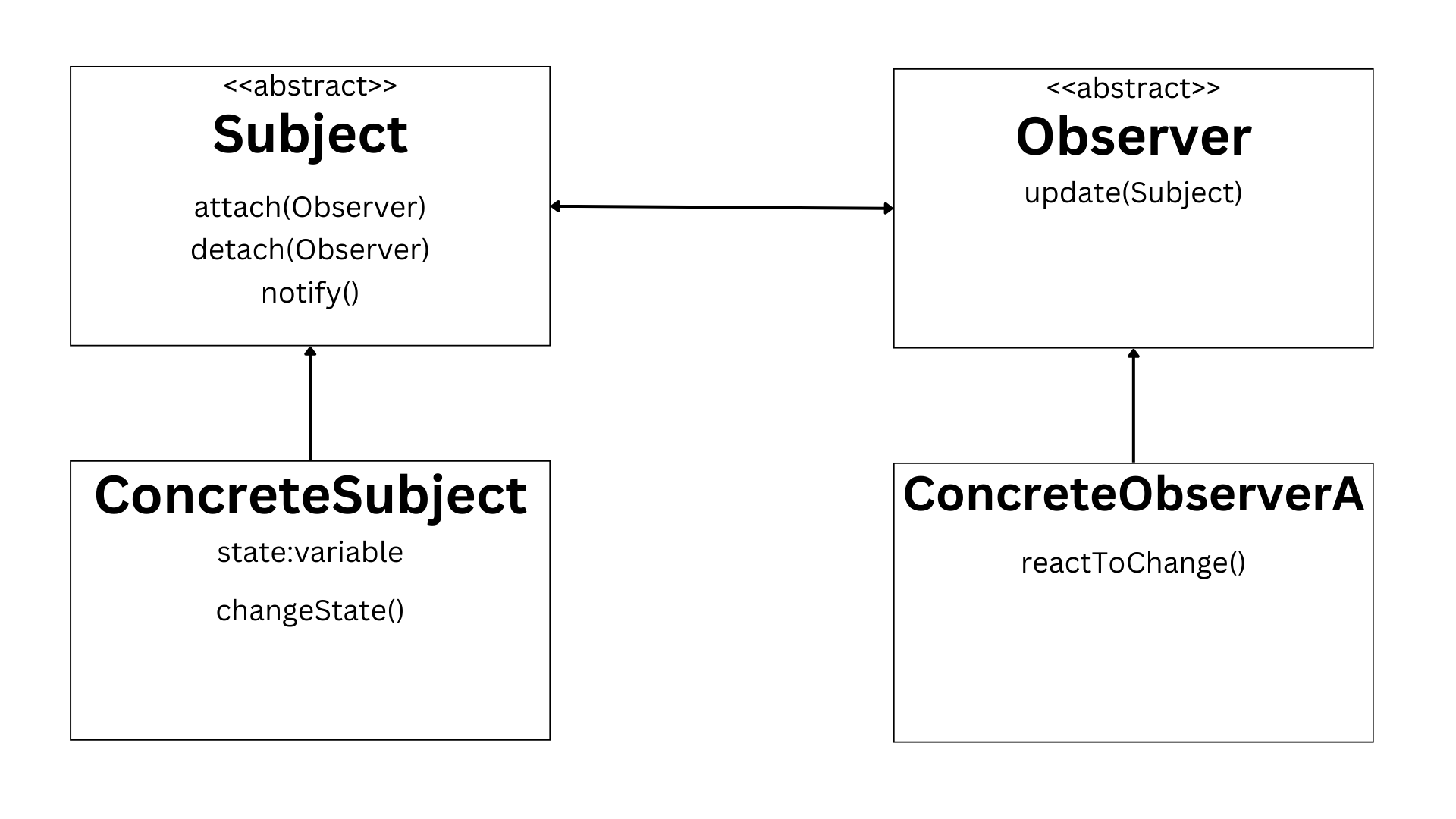
The Composite pattern addresses the need to treat individual objects and compositions of objects uniformly, creating a tree-like structure to represent part-whole hierarchies. This pattern is useful when we want to perform operations on objects regardless of their specific type, such as in a file system where we have folders (composite objects) and files (leaf objects).
To implement the Composite pattern in Java, we can define a Component interface that declares an operation() method. The Composite class represents the composite object and maintains a list of child components. It provides methods to add and remove components, as well as an implementation of the operation() method that calls the operation() method on each child component. The Leaf class represents the leaf object and provides its own implementation of the operation() method.
Here's an example code snippet:
By using the Composite pattern, we can treat individual objects and compositions of objects uniformly, simplifying the code and providing flexibility. But it's important to note that adding too many levels of nesting can make the code more complex and harder to maintain. Therefore, it's important to strike the right balance and use this pattern judiciously.
10. Strategy Pattern
The Strategy pattern is a behavioral design pattern that allows for selecting algorithms or behaviors at runtime. It addresses the need to choose different strategies based on the situation, providing flexibility and interchangeability.
To understand the Strategy pattern, let's consider a real-world example of choosing transportation methods. Depending on the situation, we may need to select a car, a bike, or a bus. Each transportation method represents a strategy, and the situation represents the context.
In Java, we can implement the Strategy pattern by creating a Context class, a Strategy interface, and multiple ConcreteStrategy classes. The Context class encapsulates the algorithms or behaviors and provides a method to change the strategy at runtime. The Strategy interface defines the contract for the different strategies, and the ConcreteStrategy classes implement specific strategies.
In this example, the Strategy interface declares the performAction() method, which represents the behavior of the different strategies. The ConcreteStrategyA and ConcreteStrategyB classes implement this interface and provide their own implementations of the strategies.
The Context class holds a reference to the current strategy and provides methods to set the strategy and execute it. By changing the strategy at runtime, we can easily switch between different behaviors.
When using the Strategy pattern, it's essential to identify the problem and choose the appropriate strategies. Consider the advantages and trade-offs, such as flexibility and potential complexity due to multiple strategy classes.

Java optimization is a crucial aspect of developing high-performance applications. In this guide, we will explore the various techniques and tools that can help improve the speed and efficiency of your Java code.
When it comes to understanding Java performance, it is essential to grasp the basics. You should be familiar with key performance metrics and be able to identify common performance bottlenecks. By analyzing and addressing these bottlenecks, you can significantly enhance the overall performance of your application.
One effective way to optimize your Java code is through computational optimization. This involves using efficient data structures and algorithms to reduce CPU cycle consumption. By carefully selecting the right algorithms and optimizing their implementation, you can achieve significant performance improvements.
Another important aspect of Java optimization is resource conflict optimization. This involves managing multi-threaded environments and implementing synchronization and locking mechanisms appropriately. By ensuring proper coordination among threads, you can avoid conflicts and improve the efficiency of your code.
Additionally, JVM optimization plays a crucial role in enhancing Java performance. By tuning JVM parameters and configuring garbage collectors, you can optimize memory usage and reduce overhead. Understanding the behavior of garbage collection and leveraging profiling and benchmarking techniques can further aid in optimizing your Java code.
To assist you in the optimization process, there are various tools available. Code analysis tools can help identify potential issues and provide suggestions for improvement. Tools for garbage collection analysis, continuous profiling, JIT compilation analysis, benchmarking, and real-time monitoring can also be valuable in identifying performance bottlenecks and optimizing your code.
In order to achieve the best results, it is important to follow best practices in Java optimization. Writing clean and maintainable code, avoiding common pitfalls, and implementing efficient memory management strategies are essential.
Throughout this chapter, we will explore real-world case studies and provide practical advice based on experience. We will also touch upon advanced topics such as optimizing Java in cloud environments and Java performance in microservices architecture.
By applying these techniques and insights, you can optimize your Java code for speed and efficiency, leading to enhanced performance and better user experiences.
Java Optimization Techniques
When it comes to optimizing your Java code, there are several key areas to focus on: computational optimization, resource conflict optimization, algorithm code optimization, and JVM optimization.
Computational optimization
In computational optimization, one effective approach is to utilize efficient data structures and algorithms.
By carefully selecting the right data structures and algorithms for your specific use case, you can significantly reduce CPU cycle consumption and improve the overall performance of your code.
Let's take a look at an example:
Resource conflict optimization
In resource conflict optimization, it is crucial to effectively manage multi-threaded environments and implement synchronization and locking mechanisms.
By ensuring proper coordination among threads, you can avoid conflicts and enhance the efficiency of your code.
Here's an example to illustrate this concept:
Algorithm code optimization
Algorithm code optimization involves selecting the right algorithms and leveraging profiling and benchmarking techniques.
By analyzing the performance characteristics of different algorithms and fine-tuning their implementation, you can achieve significant performance improvements.
JVM Optimization
JVM optimization plays a crucial role in enhancing Java performance. By tuning JVM parameters and configuring garbage collectors, you can optimize memory usage and reduce overhead.
It is essential to understand the behavior of garbage collection and leverage profiling and benchmarking techniques to fine-tune your Java code. Remember, JVM optimization can have a significant impact on the overall performance of your application.
By focusing on these key areas of optimization and applying the techniques discussed, you can greatly improve the speed and efficiency of your Java code.
Java Optimization Tools
When it comes to optimizing your Java code, several key tools deserve your attention. Let's delve into each of them and explore practical advice to improve performance.
Code Analysis Tools like Checkstyle, PMD, and FindBugs (now SpotBugs).
Application: These tools statically analyze your Java code to catch style discrepancies, potential bugs, and anti-patterns.
For instance, Checkstyle can enforce a coding standard by checking for deviations from preset rules. PMD finds common programming flaws like unused variables, empty catch blocks, unnecessary object creation, and so on. SpotBugs scans for instances of bug patterns/potential errors that are likely to lead to runtime errors or incorrect behavior.
Garbage Collection Analysis Tools like VisualVM, GCViewer, and JClarity's Censum.
Application: These tools help in analyzing Java heap dumps and garbage collection logs.
VisualVM can attach to a running JVM and monitor object creation and garbage collection, which helps in tuning the heap size and selecting the appropriate garbage collector. GCViewer can read JVM garbage collection logs to visualize and analyze garbage collection processes. Censum can interpret verbose garbage collection logs to recommend optimizations.
Continuous Profiling Tools like YourKit, JProfiler, and Java Flight Recorder (JFR).
Application: Continuous profiling tools are used to identify performance issues in a running Java application.
YourKit provides powerful on-demand profiling of both CPU and memory usage, as well as extensive analysis capabilities. JProfiler offers a live profiling of a local or remote session, and can track down performance bottlenecks, memory leaks, and threading issues. Java Flight Recorder, part of the JDK, collects detailed runtime information about the JVM which can be analyzed later.
JIT Compilation Analysis Tools like JITWatch, Oracle Solaris Studio Performance Analyzer.
Application: These tools help developers understand the intricacies of the JIT compiler.
JITWatch is a tool that analyzes the Just-In-Time (JIT) compilation process of the HotSpot JVM. It visualizes the compiler optimizations and provides feedback on how the JIT compiler is translating bytecode into machine code. The Performance Analyzer can track the performance of applications and can show how code is being executed, allowing developers to see which methods are being JIT-compiled and how often.
Benchmarking Tools like JMH (Java Microbenchmark Harness), Google Caliper.
Application: Benchmarking tools like JMH are designed for benchmarking code sections (usually methods) to measure their performance.
JMH is specifically tailored for Java and other JVM languages and allows you to define a benchmarking job and measure its performance under different conditions. Google Caliper is another benchmarking framework that's designed to help you record, analyze, and compare the performance of your Java code.
Monitoring Tools like Nagios, Prometheus with JMX exporter, and New Relic.
Application: These tools are used for the real-time monitoring of Java applications.
Nagios can monitor JVM metrics and provide alerts based on thresholds. Prometheus can scrape metrics exposed by JVM using JMX exporter and allows for powerful querying. New Relic provides an APM (Application Performance Management) tool that offers real-time insights into your application's operation, with detailed transaction traces, error tracking, and application topology mapping.
Let's look at how you can use each type of tool to better optimize your Java code.

How to Use Code Analysis Tools
Static code analysis plays a crucial role in identifying potential issues and suggesting improvements in your Java code. By utilizing popular Java code analysis tools, you can gain valuable insights into code quality and ensure adherence to best practices.
Static Code Analysis Example:
How to Use Garbage Collection Analysis Tools
Understanding garbage collection in Java is essential for optimizing memory usage and reducing overhead. By employing tools specifically designed for analyzing garbage collection behavior, you can fine-tune your Java code and optimize memory allocation.
Garbage Collection Analysis Example:
How to Use Continuous Profiling Tools
Continuous profiling enables you to gather real-time performance data and identify performance bottlenecks in your Java application. By using recommended profiling tools, you can gain insights into CPU usage, memory allocation, and method-level performance, allowing you to make targeted optimizations.
Continuous Profiling Example:
How to Use JIT Compilation Analysis Tools
Just-in-time (JIT) compilation is a crucial component of Java performance. Exploring JIT compilation behavior through dedicated tools allows you to understand how your code is optimized at runtime. By analyzing JIT compilation, you can make informed decisions to improve performance.
JIT Compilation Analysis Example:
How to Use Benchmarking Tools
Benchmarking Java applications provides valuable performance data and helps you identify areas for improvement. Effective benchmarking tools allow you to compare different approaches, algorithms, or libraries, enabling you to make informed decisions to enhance performance.
Benchmarking Example:
How to Use Monitoring Tools
Real-time monitoring of Java applications provides crucial insights into system behavior and performance metrics. Top Java monitoring tools enable you to track key performance indicators, detect anomalies, and troubleshoot issues promptly, ensuring optimal performance.
Remember, while utilizing these tools is essential, it's equally important to focus on writing clean and maintainable code, avoiding common pitfalls, and implementing efficient memory management strategies.
Best Practices in Java Optimization
Writing clean and maintainable code is crucial for optimizing Java applications. Adhering to principles of modularity and encapsulation, breaking down code into reusable modules, and encapsulating data and functionality within classes are key practices.
You should also avoid excessive object creation, choose efficient data structures, and employ memory management strategies like lazy initialization and resource cleanup.
Example of clean and maintainable code:
Here's an example code snippet illustrating the importance of clean and maintainable code:
The provided Java code is a good example of clean code for several reasons:
- Single Responsibility Principle : The OrderProcessor class has a single responsibility – to process orders. This makes the class easier to maintain and test.
- Use of meaningful names : The class name OrderProcessor and method name processOrders clearly indicate their purpose. The variable names such as orderRepository and orders are also self-explanatory.
- Dependency Injection : The OrderRepository is passed into the OrderProcessor via its constructor, which is a form of Dependency Injection. This makes the code more flexible and easier to test.
- Code readability : The code is well-structured and easy to read. The use of whitespace and indentation improves readability.
- Error handling : The code checks if an order is valid before processing it, which is a good practice for error handling.
Overall, this code is clean because it is easy to understand, maintain, and extend.

Chapter 6: Concurrent Data Structures and Algorithms for High-Performance Applications
In the fast-paced world of computing, where speed and efficiency are paramount, concurrent data structures and algorithms play a crucial role in achieving high performance.
Concurrency allows multiple tasks to execute simultaneously, maximizing resource utilization and enabling applications to handle complex workloads efficiently.
Understanding the fundamentals of concurrency in computing is essential for developers seeking to optimize their applications. By harnessing the power of parallelism, concurrent data structures and algorithms enable tasks to be executed concurrently, reducing overall execution time and improving responsiveness.
Key Concurrent Data Structures
Lock-based data structures provide a mechanism for ensuring mutual exclusion and data consistency in concurrent applications. They work by acquiring a lock or mutex before accessing shared data, ensuring that only one thread can access the data at a time. Common lock-based structures include locks, mutexes, and semaphores.
Lock-free data structures, on the other hand, offer a way to achieve concurrency without the use of locks. They utilize atomic operations and memory fences to ensure data consistency and avoid the need for explicit locking. Examples of lock-free structures include lock-free queues and lock-free stacks.
Wait-free data structures take concurrency a step further by guaranteeing that every thread makes progress even if other threads are stalled or delayed. They are designed to ensure that no thread is blocked indefinitely, making them suitable for real-time systems and high-performance applications.
We'll see some examples of these in a minute.
Remember, when utilizing lock-based data structures, it is crucial to handle potential issues such as deadlocks and contention. Always aim to strike a balance between concurrency and performance, ensuring efficient utilization of resources.
When working with lock-free and wait-free data structures, it is important to understand their limitations and use them judiciously. These structures can provide significant performance benefits in certain scenarios, but they may also introduce additional complexity and require careful synchronization.
By leveraging the appropriate concurrent data structures and algorithms in your Java applications, you can optimize performance, enhance responsiveness, and achieve efficient resource utilization.
Essential Concurrent Algorithms
In high-performance applications, concurrent data structures and algorithms are essential for achieving optimal speed and efficiency. They enable tasks to be executed simultaneously, maximizing resource utilization and improving responsiveness.
One important aspect of concurrency is task scheduling algorithms. These algorithms play a critical role in managing concurrent tasks. They determine the order in which tasks are executed and ensure efficient utilization of resources.
Here's an example of a round-robin scheduling algorithm implemented in Java:
Synchronization algorithms are crucial for ensuring data consistency in concurrent applications. They prevent data races and conflicts by providing mechanisms for thread synchronization.
Here's an example of using locks for synchronization in Java:
Deadlock detection and resolution are vital for handling potential deadlocks in concurrent applications, as we discussed above. If you remember, deadlocks occur when two or more threads are blocked indefinitely, waiting for each other to release resources.
Here's an example of deadlock prevention using resource ordering in Java:
By leveraging the appropriate concurrent data structures, algorithms, and synchronization techniques, you can optimize the performance of your Java applications. Remember to consider the limitations and complexities of concurrent programming and aim for simplicity and efficiency in your implementation.
Examples of Lock-based, Lock-free, and Wait-free Data Structures
Concurrent data structures and algorithms play a crucial role in achieving high performance in the fast-paced world of computing. By allowing multiple tasks to execute simultaneously, concurrency maximizes resource utilization and enables efficient handling of complex workloads.
Lock-based data structure
Lock-based data structures, such as locks, mutexes, and semaphores, ensure mutual exclusion and data consistency by acquiring locks before accessing shared data.
For example, in Java, you can use a lock-based data structure like the following code snippet:
The lock variable is an instance of the ReentrantLock class from the java.util.concurrent.locks package, which is a reentrant mutual exclusion Lock with the same basic behavior and semantics as the implicit monitor lock accessed using synchronized methods and statements, but with extended capabilities.
The ReentrantLock allows more flexible structuring, may have completely different properties, and may support multiple associated Condition objects.
The use of ReentrantLock helps to ensure that the increment() operation is thread-safe. This is crucial in a multi-threaded environment to prevent race conditions.
Lock-free data structure
On the other hand, lock-free data structures, such as lock-free queues and lock-free stacks, achieve concurrency without the use of locks. They employ atomic operations and memory fences to ensure data consistency.
In this code, AtomicReference is used to ensure that the operations on the top of the stack are atomic. The push and pop methods use a loop with compareAndSet to ensure that the operation is retried if the top was modified by another thread in the meantime.
This is a simple example of a lock-free data structure that achieves concurrency without the use of locks. But it’s important to note that while lock-free data structures can improve performance in multi-threaded environments, they can be more complex to implement correctly and may not always provide the best solution depending on the specific requirements of your application. It’s always important to understand their limitations and use them judiciously.
Wait-free data structure
Wait-free data structures guarantee that every thread makes progress, even if other threads are stalled or delayed. They are suitable for real-time systems and high-performance applications.
In this code, AtomicReference is used to ensure that the operations on the head and tail of the queue are atomic.
The enqueue and dequeue methods use a loop with compareAndSet to ensure that the operation is retried if the head or tail was modified by another thread in the meantime.
This is a simple example of a wait-free data structure that guarantees that every thread makes progress, even if other threads are stalled or delayed. But it’s important to note that while wait-free data structures can improve performance in multi-threaded environments, they can be more complex to implement correctly and may not always provide the best solution depending on the specific requirements of your application. It’s always important to understand their limitations and use them judiciously.
In real-world applications, concurrent structures find applications in scenarios where high-performance and efficient resource utilization are critical. Learning from successful implementations can provide valuable insights and practical advice for optimizing your own applications.

Understanding the importance of Java security is crucial in today's digital landscape. Over the years, Java security has evolved to address emerging threats and provide robust protection for applications and data. Let's delve into these key concepts and explore their practical implications.
When it comes to Java security, you'll want to prioritize the safety of your applications and the sensitive information they handle. By implementing strong security measures, you can safeguard against unauthorized access, data breaches, and malicious attacks.
To illustrate the significance of Java security, consider the following example code snippet:
This Java code sample illustrates the significance of Java security in several ways:
- Hashing Passwords : The hashPassword method uses the MessageDigest class from the java.security package to hash passwords using the SHA-256 algorithm. Hashing passwords is a critical security practice because it means that even if an attacker gains access to the password hash, they cannot easily determine the original password.
- User Authentication : The authenticate method checks if the entered username exists in the userDatabase and if the hashed version of the entered password matches the stored hashed password. This is a basic form of user authentication, which is crucial for protecting user accounts and data.
- User Authorization : The isAuthorized method checks if the authenticated user has the necessary permissions to perform secure operations. This is an example of user authorization, which is important for ensuring that users can only perform actions they are allowed to.
- Exception Handling : The code includes exception handling to deal with potential errors, such as the NoSuchAlgorithmException that might be thrown when getting an instance of MessageDigest . Proper exception handling is important for both security and reliability.
- Secure Operations : The performSecureOperations method is a placeholder for operations that should only be performed by authorized users. Ensuring that only authorized users can perform sensitive operations is a key aspect of application security.
- Logging : The code uses a Logger to record information about authentication and authorization processes. Logging is important for monitoring and troubleshooting security-related events.
These security features are all critical for building secure Java applications. But it’s important to note that this is a simplified example and real-world applications would require additional security measures.
Through regular updates and patches, Java vulnerabilities are addressed, and new features are introduced to mitigate emerging risks. Staying up to date with the latest security practices and incorporating them into your development process is essential for maintaining a secure Java environment.
Let's dive into security principles and best practices in more detail.
What Is Java Security?
Java security refers to the measures and mechanisms in place to safeguard applications and data from unauthorized access, breaches, and malicious attacks. It encompasses a range of practices, including authentication, authorization, encryption, secure coding, and more.
By implementing robust security measures, you can create a secure environment that inspires user confidence and protects valuable information.
Core Principles of Java Security
Java security is built upon several core principles that guide the development and implementation of secure applications:
Authentication
Authentication is a fundamental aspect of cybersecurity. It serves as the first line of defense in securing sensitive resources and functionalities by ensuring that only verified users gain access. In the context of Java, there are several ways to implement authentication, each with its own significance.
Validating usernames and passwords is the most basic form of authentication. It involves checking the entered credentials against a database of registered users.
While simple, this method is susceptible to various attacks such as brute force or dictionary attacks. So it’s crucial to store passwords securely, often as hashed values rather than plain text. Java provides several libraries for secure password hashing, such as Bcrypt.
Example Code:
Multi-factor authentication (MFA) adds an extra layer of security. It requires users to provide two or more verification factors to gain access. These factors could be something the user knows (like a password), something the user has (like a hardware token or phone), or something the user is (like a fingerprint or other biometric trait).
MFA significantly improves security because even if an attacker obtains one factor (like the user’s password), they still need the other factor(s) to gain access.
External authentication systems, such as OAuth2 or OpenID Connect, allow users to authenticate using an external trusted provider (like Google or Facebook). These systems can provide a secure and user-friendly way to handle authentication, as they offload the responsibility of secure credential storage to the external provider. Java has several libraries, like Spring Security, that provide out-of-the-box support for these systems.
Authorization
Access control is a critical aspect of cybersecurity, particularly in Java applications. It involves defining and enforcing policies that determine which users have permissions to access specific resources or perform certain operations within the application.
In a typical Java application, access control can be implemented at various levels. For instance, at the method level, developers can use Java’s built-in access modifiers (public, private, protected, and package-private) to control which other classes can call a particular method. However, for more granular and dynamic access control, developers often turn to frameworks like Spring Security.
Spring Security provides a comprehensive security solution for Java applications. It includes support for both authentication (verifying who a user is) and authorization (controlling what a user can do).
For example, consider a web application where only authenticated users should be able to access certain pages. With Spring Security, developers can annotate controller methods with @PreAuthorize to specify access control rules. Here’s an example:
In this code, the @PreAuthorize annotation ensures that only users with the ‘ADMIN’ role can access the ‘admin’ page. If a user without the ‘ADMIN’ role tries to access this page, Spring Security will block the request.
This is just one example of how access control can be implemented in Java. The key is to carefully define access control policies that align with the application’s requirements and to enforce these policies consistently throughout the application. This helps to ensure that sensitive resources and operations are protected from unauthorized access, thereby enhancing the overall security of the application.
Secure Coding
Secure coding practices are essential in Java cybersecurity. They help eliminate vulnerabilities and prevent common exploits, thereby enhancing the overall security of Java applications.
Input validation is one such practice. It involves checking the data provided by users to ensure it meets specific criteria before processing it.
This is crucial because unvalidated or improperly validated inputs can lead to various types of attacks, such as SQL injection, cross-site scripting (XSS), and command injection.
In Java, you can perform input validation using various methods, such as regular expressions, built-in functions, or third-party libraries.
Here’s an example of basic input validation in Java:
In this code, the isValidUsername method checks if the provided username only contains alphanumeric characters and underscores, which is often a requirement for usernames.
Output encoding is another important secure coding practice. It involves encoding the data before sending it to the client to prevent attacks like XSS, where an attacker injects malicious scripts into content that’s displayed to other users.
Java provides several ways to perform output encoding, such as using the escapeHtml4 method from the Apache Commons Text library to encode HTML content.
Parameterized queries, also known as prepared statements, are used to prevent SQL injection attacks.
SQL injection is a technique where an attacker inserts malicious SQL code into a query, which can then be executed by the database. By using parameterized queries, you ensure that user input is always treated as literal data, not part of the SQL command.
Here’s an example of a parameterized query in Java using JDBC:
In this code, the ? is a placeholder that gets replaced with the username variable. Because the username is automatically escaped by the PreparedStatement , it’s not possible for an attacker to inject malicious SQL code via the username .
Following secure coding practices like input validation, output encoding, and using parameterized queries is crucial for preventing common exploits and enhancing the security of Java applications.
Protecting sensitive data, both at rest and in transit, is a cornerstone of cybersecurity. Encryption plays a vital role in this protection. It involves converting plaintext data into ciphertext using an encryption algorithm, rendering it unreadable to anyone without the decryption key.
In Java, the Java Cryptography Extension (JCE) provides functionalities for encryption and decryption. It supports various encryption algorithms, including AES (Advanced Encryption Standard), which is widely recognized for its strength and efficiency.
Here’s an example of how you might use AES encryption to protect data at rest in Java:
In this code, we first generate a new AES key. We then create a Cipher instance and initialize it for encryption using the generated key. Finally, we encrypt the plaintext data and print the resulting ciphertext.
When it comes to protecting data in transit, secure communication protocols like HTTPS (HTTP over SSL/TLS) are commonly used. These protocols use encryption to protect data as it travels over the network. In Java, you can use the HttpsURLConnection class or libraries like Apache HttpClient to send and receive data over HTTPS.
Managing encryption keys is another critical aspect of data protection. Keys need to be securely generated, stored, and managed. They should be rotated regularly and revoked if compromised. In Java, you can use the Java KeyStore (JKS) to securely store cryptographic keys.
Encryption is a powerful tool for protecting sensitive data in Java applications. By using strong encryption algorithms and properly managing encryption keys, you can significantly enhance the security of your data, both at rest and in transit.
Logging and Monitoring
Implementing comprehensive logging and monitoring systems is a crucial aspect of cybersecurity in Java applications. These systems serve as the eyes and ears of your application, providing visibility into its operations and helping to detect and respond to security incidents effectively.
Logging involves recording events that occur in your application. These events can include user actions, system events, or errors. Logs can provide valuable information for troubleshooting issues, understanding user behavior, and detecting security incidents.
In Java, there are several libraries available for logging, such as Log4j, SLF4J, and java.util.logging.
Here’s an example of how you might use Log4j in a Java application:
In this code, we first create a Logger instance. We then use the info , warn , and error methods to log messages at different levels. These messages will be recorded in the application’s log file, where they can be reviewed later.
Monitoring, on the other hand, involves continuously observing your application to track its performance, identify issues, and detect potential security breaches.
Monitoring can help you identify suspicious activities, such as repeated failed login attempts, unexpected system behavior, or significant changes in traffic patterns, which could indicate a security incident.
Java provides several tools and libraries for monitoring, such as JMX (Java Management Extensions) for monitoring and managing Java applications, and third-party solutions like New Relic or Dynatrace for application performance monitoring.
By adhering to these core principles and incorporating them into the development process, developers can build robust and secure Java applications.
Remember, while these principles provide a solid foundation for Java security, it's essential to stay updated with the latest security practices, frameworks, and libraries. Regularly reviewing and enhancing security measures is crucial to adapt to emerging threats and ensure the ongoing protection of your Java applications.
By focusing on these fundamental aspects of Java security, you can create a secure and reliable environment for your applications and instill confidence in your users.
Here is a final code incorporating all the discussed aspects of Java security:
This code integrates the discussed principles of Java security, such as authentication, authorization, secure coding, encryption, and logging. It provides a foundation for building secure Java applications and protecting sensitive information.
Remember to adapt and enhance the code based on specific application requirements and the latest security practices. Regularly review and update the code to address emerging threats and vulnerabilities, ensuring the ongoing security of your Java applications.
Java Language Features for Security
When it comes to Java security, several key language features play a crucial role in ensuring the safety and protection of applications and data. Let's explore these features and understand their significance in securing Java code.
Static Data Typing: Enforcing Type Safety
One fundamental aspect of Java security is static data typing. By enforcing type safety, Java helps prevent common programming errors and vulnerabilities.
Static typing ensures that variables are declared with specific data types and that only compatible operations can be performed on them. This reduces the risk of type-related security issues, such as type confusion or type casting vulnerabilities.
For example, consider the following code snippet:
In this example, the compiler will detect any attempts to assign an integer value to the userName variable, preventing potential security risks.
Access Modifiers: Controlling Visibility and Accessibility
Access modifiers in Java, such as public , private , and protected , allow developers to control the visibility and accessibility of classes, methods, and variables. This plays a crucial role in ensuring the security of Java code by restricting access to sensitive information or functionalities.
In this example, the sensitiveData variable and the processSensitiveData method are declared as private , ensuring that they can be accessed only within the SecureApplication class.
Automatic Memory Management: Mitigating Memory-Related Vulnerabilities
Java's automatic memory management, enabled by the garbage collector, plays a significant role in enhancing security by mitigating memory-related vulnerabilities.
By automatically deallocating memory that is no longer in use, Java helps prevent issues such as memory leaks and buffer overflows that can lead to security vulnerabilities.
In this example, Java's garbage collector ensures that the memory occupied by the userInput variable is automatically reclaimed after it is no longer needed, reducing the risk of memory-related vulnerabilities.
Bytecode Verification: Ensuring Safe Code Execution
Java's bytecode verification process plays a critical role in ensuring the safe execution of code.
When Java code is compiled, it is transformed into bytecode, which is then executed by the Java Virtual Machine (JVM). Before executing the bytecode, the JVM performs bytecode verification to ensure that it adheres to specific safety requirements.
This process helps prevent common security risks, such as stack overflow or buffer overflow vulnerabilities.
In this example, the JVM verifies the bytecode of the processInput method to ensure that it operates safely, preventing potential security vulnerabilities.
By leveraging these language features, you can enhance the security of your Java code. But it's important to remember that these features alone are not sufficient to guarantee complete security. It is crucial to follow secure coding practices, apply encryption where necessary, and implement other security measures as required by your specific application and environment.
Security Architecture in Java
Overview of java security architecture.
Java security architecture is designed to provide a secure environment for Java applications. It includes various components such as the Java Development Kit (JDK), Java Runtime Environment (JRE), and Java Virtual Machine (JVM).
The architecture ensures the enforcement of security policies, handling of permissions, and management of cryptographic services.
Role of Provider Implementations in Java Security
In Java, a provider refers to a package or a set of packages that supply a concrete implementation of a subset of the cryptography aspects of the Java Cryptography Architecture (JCA) and the Java Cryptography Extension (JCE). They supply the actual program code that implements standard algorithms such as RSA, DSA, and AES.
Provider implementations are indeed crucial in Java security. They provide the necessary cryptographic algorithms and services that are used for various purposes such as generating key pairs, creating secure random numbers, and creating message digests.
Java includes several built-in providers. For instance, SunJCE (Java Cryptography Extension) is a provider that offers a wide range of cryptographic functionalities including support for encryption, key generation and key agreement, and Message Authentication Code (MAC) algorithms.
SunPKCS11 is another provider that offers a wide range of cryptographic functionalities. It provides a bridge from the JCA to native PKCS11 cryptographic tokens. PKCS11 is a standard that defines a platform-independent API to cryptographic tokens, such as hardware security modules (HSM) and smart cards, and names the API itself “Cryptoki”.
While the built-in providers offer a wide range of cryptographic functionalities, Java also allows for custom providers. This means you can implement your own provider to extend the security capabilities of your Java applications.
This is particularly useful when you need to use cryptographic services that are not offered by the built-in providers or when you want to use a device-specific implementation.
Implementing a custom provider involves extending the java.security.Provider class and implementing the required cryptographic services. Once implemented, the provider can be dynamically registered at runtime by calling the Security.addProvider() method.
Understanding Cryptographic Algorithms in Java
Java supports a comprehensive set of cryptographic algorithms for various purposes, including encryption, digital signatures, and hash functions. These algorithms ensure the confidentiality, integrity, and authenticity of data. Some commonly used algorithms include AES, RSA, and SHA-256.
To illustrate the usage of cryptographic algorithms in Java, consider the following example code:
In this example, we generate a key pair using the RSA algorithm, encrypt the data using the public key, and then decrypt it using the private key.
By understanding Java security architecture, provider implementations, and cryptographic algorithms, you can effectively implement secure solutions in your Java applications.
Cryptography in Java
In Java Cryptographic Architecture (JCA), you have access to a wide range of cryptographic functionalities to enhance the security of your Java applications. Let's explore some key concepts and techniques that can be implemented in Java code.
Introduction to Java Cryptographic Architecture (JCA)
To ensure the confidentiality, integrity, and authenticity of data, JCA provides a framework for implementing cryptographic algorithms and services. It includes classes and interfaces that allow you to perform various cryptographic operations, such as encryption, decryption, digital signatures, and message digests.
How to Implement Digital Signatures and Message Digests
Digital signatures provide a way to verify the authenticity and integrity of data. By generating a digital signature, you can ensure that the data has not been tampered with during transmission or storage.
Message digests, on the other hand, create a fixed-size hash value representing the input data. This hash value can be used to verify the integrity of the data.
Here is an example of generating a digital signature and verifying it using Java code:
Symmetric vs. Asymmetric Ciphers
Symmetric ciphers use the same key for both encryption and decryption, while asymmetric ciphers use different keys for these operations.
Symmetric ciphers are generally faster but require a secure method of key exchange. Asymmetric ciphers provide a secure way to exchange keys but are slower than symmetric ciphers.
Here is an example of using symmetric and asymmetric ciphers in Java:
Key Generators and Factories
In Java, you can use key generators and factories to generate and manage cryptographic keys. Key generators provide a way to generate secret keys for symmetric ciphers, while key factories are used to generate public and private keys for asymmetric ciphers.
Here is an example of using key generators and factories in Java:
By understanding and implementing these cryptographic concepts in Java, you can enhance the security of your Java applications and protect sensitive information effectively.
Public Key Infrastructure (PKI) in Java
When it comes to securing your Java applications, understanding the fundamentals of Public Key Infrastructure (PKI) is essential.
PKI provides a framework for managing keys and certificates. These play a crucial role in establishing secure communication and verifying the authenticity of entities in a networked environment.
In Java, you can leverage the KeyStore and CertStore classes to manage keys and certificates effectively.
The KeyStore class allows you to store and retrieve cryptographic keys, while the CertStore class provides a means to access certificates.
By properly managing keys and certificates, you can ensure the integrity and confidentiality of sensitive information.
Here's an example of using the KeyStore class to load a keystore file and retrieve a private key:
In this example, we load a keystore file in JKS format, provide the keystore password, and retrieve a private key using its alias and the associated key password. Once you have the private key, you can use it for various cryptographic operations.
Another important aspect of PKI in Java is the usage of tools such as Keytool and Jarsigner. Keytool is a command-line utility that allows you to manage keys and certificates within a keystore. Jarsigner, on the other hand, is used for digitally signing JAR files, ensuring their integrity and authenticity.
Here's an example of using Keytool to generate a key pair and store it in a keystore:
In this command, we generate a key pair using the RSA algorithm and store it in a keystore named "keystore.jks" with an alias "mykey". Keytool will prompt you for additional details such as the keystore password, key password, and the owner's information.
These tools provide essential functionalities for managing keys and certificates, enabling you to establish a secure environment for your Java applications. By incorporating these practices into your development process, you can enhance the security of your applications and protect sensitive data.
Authentication in Java
When it comes to Java security, understanding authentication mechanisms is crucial. Java provides various authentication mechanisms that can be implemented to ensure the safety and protection of applications and data. Let's explore some of these mechanisms and how they can be implemented in Java code.
Understanding Authentication Mechanisms in Java
In Java, authentication is the process of verifying the identity of a user or entity before granting access to protected resources. Java offers several authentication mechanisms, such as username and password authentication, token-based authentication, and certificate-based authentication.
One common authentication mechanism is username and password authentication. This mechanism involves validating a user's credentials, typically a username and password, to grant access.
To implement username and password authentication in Java, you can use the java.security package and the MessageDigest class to securely hash and compare passwords.
Here's an example code snippet that demonstrates username and password authentication in Java:
In this example, the UserAuthentication class demonstrates username and password authentication. It uses a HashMap to store the user database, where usernames are mapped to their corresponding hashed passwords. The authenticate method checks if the provided username exists in the database and compares the hashed password with the provided password.
Remember, this is a basic example, and in real-world scenarios, you would need to consider additional security measures such as using a salt for password hashing and storing passwords securely.
By implementing these authentication mechanisms in your Java applications, you can ensure the secure verification of user identities and protect sensitive resources.
Pluggable Login Modules: Flexibility and Security
In addition to the username and password authentication mechanism, Java provides a flexible and secure approach to authentication through pluggable login modules. Pluggable login modules allow you to define and implement custom authentication mechanisms based on specific requirements.
To implement pluggable login modules in Java, you can utilize the Java Authentication and Authorization Service (JAAS). JAAS provides a framework for authentication and authorization, allowing you to define and configure login modules to authenticate users.
Here's a simplified example code snippet that demonstrates the use of pluggable login modules in Java:
In this example, the PluggableAuthentication class demonstrates the usage of pluggable login modules. The LoginContext class is responsible for authenticating users using the specified login module, in this case, "SampleLoginModule". Once authenticated, the Subject object can be obtained from the LoginContext to access the authenticated user's information and perform further operations.
By leveraging pluggable login modules, you can customize and extend authentication mechanisms to meet specific security requirements, providing flexibility and enhanced security in your Java applications.
Case Study: How to Implement Username and Password Authentication
To illustrate the implementation of username and password authentication in Java, let's consider a case study. Suppose you are developing a web application that requires user authentication to access certain resources.
To implement username and password authentication in this case, you can utilize Java's Servlet API and the Java Persistence API (JPA). The Servlet API provides functionality for handling HTTP requests and responses, while JPA allows you to interact with a database and store user information securely.
Here's a high-level example code snippet that demonstrates the implementation of username and password authentication in a web application:
In this example, the LoginServlet class handles the HTTP POST request for the login page. It retrieves the username and password entered by the user and delegates the authentication process to the UserService .
If the authentication is successful, a session is created, and the user is redirected to the dashboard page. Otherwise, an error parameter is appended to the URL, indicating an invalid login attempt.
The UserService class encapsulates the authentication logic and interacts with the UserRepository to retrieve user information from the database. It compares the hashed password stored in the User entity with the provided password using the implemented password hashing algorithm.
Remember, this is a simplified example, and in a real-world scenario, you would need to consider additional security measures such as implementing secure session management, protecting against brute force attacks, and using stronger password hashing algorithms.

When it comes to securing client-server communication in Java, there are several protocols and techniques available. Let's explore some of these options:
SSL/TLS Protocols and Java Implementation
To establish a secure connection between a client and a server, the SSL/TLS protocols are commonly used.
In Java, you can utilize the Java Secure Socket Extension (JSSE) to implement SSL/TLS functionality. Here's an example of how to set up a secure connection using JSSE:
In this example, we create an SSLSocketFactory and an SSLSocket to establish a secure connection with the server at example.com on port 443 .
SASL: Securing Client-Server Communication
The Simple Authentication and Security Layer (SASL) is a framework that provides a flexible way to secure client-server communication. It allows clients and servers to negotiate and select authentication mechanisms that suit their requirements.
Here's an example of how to use SASL in Java:
In this example, we create a SaslClient using the PLAIN authentication mechanism for secure communication with the server at example.com .
GSS-API/Kerberos: Advanced Security Protocols
The Generic Security Service Application Program Interface (GSS-API) provides a framework for implementing advanced security protocols, such as Kerberos, in Java. Kerberos is a widely used authentication protocol that enables secure client-server communication.
Here's an example of how to use GSS-API/Kerberos in Java:
In this example, we use the GSS-API to perform a Kerberos login and obtain a Subject that represents the authenticated client.
Access Control in Java
Java provides several key features and tools to enhance security in your applications. Let's explore the role of SecurityManager , implementing permissions for resource access, and policy files.
Role of SecurityManager in Java
The SecurityManager class plays a vital role in Java security by enforcing fine-grained access control policies. It acts as a gatekeeper, preventing untrusted code from accessing sensitive resources or performing unauthorized operations.
By configuring and utilizing the SecurityManager , you can define and enforce security rules specific to your application's requirements.
Example code:
By setting a SecurityManager instance, you enable the enforcement of security policies within your Java application.
Implement Permissions for Resource Access
Java's permission model allows you to grant or deny specific permissions to code based on its origin or identity.
By defining and enforcing permissions, you can control which resources or operations a piece of code can access. This helps mitigate the risk of unauthorized access or misuse of sensitive resources.
In this example, we define a FilePermission to grant read access to a specific file. The SecurityManager 's checkPermission method ensures that the code has the required permission before accessing the file.
Policy Files: Defining and Enforcing Security Policies
Policy files provide a flexible and configurable way to define and enforce security policies in Java applications. They allow you to specify permissions, code sources, and associated permissions, granting or denying access based on defined rules.
By customizing and managing policy files, you can tailor the security policies to the specific needs of your application.
Example policy file (example.policy):
In this example, we grant read permission to the file "/path/to/file.txt". To enforce this policy file, you can specify it when launching your Java application using the -Djava.security.policy system property:
By leveraging policy files, you can define and enforce security policies without modifying your application's code.
Advanced Java Security Topics
Java provides various security features and tools to ensure the safety and protection of your applications. Let's explore some important concepts and techniques you can implement in your Java code.
XML Signature in Java
XML Signature is a crucial aspect of Java security that allows you to digitally sign XML documents to ensure their integrity and authenticity. By using the Java XML Digital Signature API, you can generate and verify XML signatures.
Here's an example code snippet to demonstrate the usage:
Deprecated Security APIs to Avoid
Java has deprecated certain security APIs due to their vulnerabilities or outdated functionality. It is important to avoid using these deprecated APIs and migrate to the recommended alternatives.
Here are a few examples of deprecated security APIs and their recommended replacements:
- java.security.KeyStore : Deprecated in favor of java.security.KeyStore.Builder .
- java.security.SecureRandom : Deprecated in favor of java.security.SecureRandom.getInstanceStrong() or java.security.SecureRandom.getInstance() .
- java.security.KeyPairGenerator : Deprecated in favor of java.security.KeyPairGenerator.getInstance() .
Always refer to the Java documentation for the complete list of deprecated security APIs and their recommended alternatives.
Security Tools and Commands in Java
Java provides various security tools and commands that can assist you in analyzing and enhancing the security of your applications.
Here are a few commonly used tools and commands:
- jarsigner : The jarsigner tool allows you to digitally sign JAR files to ensure their integrity and authenticity.
- keytool : The keytool command-line utility enables you to manage cryptographic keys and certificates in a Java KeyStore.
- javadoc : The javadoc tool generates API documentation, including security-related APIs, from Java source code.
- jps : The jps command-line utility displays information about Java processes running on a system, including their security settings.
- jinfo : The jinfo command-line utility provides configuration information for a running Java process, including security-related properties.
These tools and commands can be valuable in securing your Java applications and ensuring proper configuration and management of security-related components.
Remember to always refer to the official Java documentation and stay updated with the latest security practices and recommendations. Implementing robust security measures and regularly reviewing your code for potential vulnerabilities are essential for maintaining a secure Java environment.
Java Security in Practice
Java security plays a crucial role in today's digital landscape, ensuring the safety and protection of applications and sensitive data. Let's explore some real-world applications where Java security is prominently used and discuss case studies in the banking and e-commerce sectors.
Real-World Applications of Java Security
Java security is extensively utilized in various real-world applications, including banking systems, e-commerce platforms, and government services.
For example, in the banking sector, Java security is crucial for ensuring secure online transactions, protecting customer data, and preventing unauthorized access. Robust authentication mechanisms, encryption algorithms, and secure coding practices are employed to maintain the integrity and confidentiality of financial data.
In e-commerce platforms, Java security plays a vital role in safeguarding sensitive customer information, such as credit card details and personal data. Strict access control, secure communication protocols, and secure coding practices are implemented to prevent data breaches and protect customer privacy.
Let's explore two case studies that illustrate the practical implementation of Java security in the banking and e-commerce sectors.
Case Study: Banking Application
In a banking application, Java security is crucial for protecting customer accounts, preventing fraudulent activities, and ensuring the confidentiality of financial transactions.
To achieve this, the application incorporates several security measures:
- Secure Authentication : The banking application employs strong authentication mechanisms to verify the identity of users. Multi-factor authentication, such as combining passwords with biometric data, adds an extra layer of security.
- Secure Communication : The application uses secure communication protocols, such as HTTPS, to encrypt data transmission between the client and the server. This prevents eavesdropping and ensures the integrity of sensitive information.
- Secure Data Storage : Customer data, including account details and transaction history, is securely stored using encryption techniques. Strong encryption algorithms and proper key management ensure the confidentiality of sensitive data.
Case Study: E-commerce Platform
In an e-commerce platform, Java security is vital for protecting customer data, securing payment transactions, and preventing unauthorized access to user accounts. The platform incorporates various security measures to ensure a safe and trustworthy shopping experience.
- Secure Payment Processing : The e-commerce platform integrates with secure payment gateways, employing encryption and tokenization techniques to protect sensitive payment information. This ensures that customer payment details are securely transmitted and stored.
- Secure User Account Management : The platform enforces strong password policies, implements secure password storage techniques such as hashing and salting, and provides multi-factor authentication options to protect user accounts from unauthorized access.
- Secure Session Management : The e-commerce platform ensures secure session management by generating unique session IDs, implementing session timeouts, and securely storing session data to prevent session hijacking attacks.
By implementing these Java security measures, banking and e-commerce applications can provide a secure and trustworthy environment for their users. Remember to adapt these examples to your specific application requirements and consider additional security measures based on industry standards and best practices.
Java Security for Developers
When it comes to writing secure code in Java, it is important to follow best practices to ensure the safety and protection of your applications. By avoiding common security pitfalls and enhancing your skills through developer security training, you can create robust and secure Java applications. Let's explore these concepts in more detail.
How to Write Secure Code: Best Practices
Writing secure code involves adopting best practices that help mitigate security risks. Here are some key practices to consider:
Input Validation : Always validate and sanitize user input to prevent common vulnerabilities such as SQL injection or cross-site scripting (XSS) attacks. Use built-in Java libraries or frameworks to handle input validation effectively.
Secure Communication : Utilize secure communication protocols, such as HTTPS, to encrypt data transmitted between the client and the server. This ensures the confidentiality and integrity of sensitive information.
Authentication and Authorization : Implement strong authentication mechanisms to verify the identity of users and grant appropriate access privileges. Use secure algorithms for password hashing and consider multi-factor authentication for enhanced security.
Error Handling : Handle errors securely by providing informative error messages to users while avoiding exposing sensitive information that could be exploited by attackers. Log errors appropriately for monitoring and debugging purposes.
Secure Session Management : Implement secure session management techniques, such as using secure tokens or session IDs, to prevent session hijacking or fixation attacks. Set appropriate session timeouts and invalidate sessions after logout.
Common Security Pitfalls and How to Avoid Them
To write secure Java code, it is crucial to be aware of common security pitfalls and take steps to avoid them. Here are some pitfalls to watch out for:
Insecure Direct Object References : Avoid exposing internal object references directly in URLs or hidden fields, as it can lead to unauthorized access to sensitive data. Use indirect references or access control mechanisms to protect confidential information.
Cross-Site Scripting (XSS) Attacks : Prevent XSS attacks by properly encoding user-generated content and validating input. Utilize frameworks or libraries that automatically handle HTML encoding to mitigate this risk.
Insecure Cryptography : Avoid using weak or outdated cryptographic algorithms, as they can be vulnerable to attacks. Utilize the cryptographic functionalities provided by Java, such as AES or RSA, with secure key management practices.
Code Injection : Prevent code injection attacks, such as SQL injection or OS command injection, by utilizing prepared statements or parameterized queries. Avoid constructing queries or commands by concatenating user input.
Here is an example of an insecure code and the solution to it:
Here’s an example of a Java Servlet that has several security issues related to Insecure Cryptography, Cross-Site Scripting (XSS) Attacks, and Insecure Direct Object References:
In this code:
- Insecure Direct Object References : The code constructs an SQL query using the user-supplied username directly, which can lead to SQL Injection attacks if the username is not properly sanitized.
- Insecure Cryptography : The code uses MD5 to hash the password, which is considered insecure due to its vulnerability to collision attacks. A stronger algorithm like bcrypt or scrypt should be used instead.
- Cross-Site Scripting (XSS) Attacks : The code directly outputs the user-supplied username to the response without any sanitization or encoding, which can lead to XSS attacks if the username contains malicious scripts.
Here is the solution to it:
In this revised code, we use a PreparedStatement to prevent SQL Injection attacks. We replace MD5 with bcrypt for password hashing. And we escape the username using StringEscapeUtils.escapeHtml4() from Apache Commons Lang to prevent XSS attacks.
Note that this is a simplified example and real-world applications may have additional complexities and security considerations. Always follow best practices for secure coding to protect your application from these and other security vulnerabilities.
Also, remember to never expose sensitive information like secret keys in your code as done in this example. It’s always recommended to store such information in secure and encrypted environment variables or configuration files.
Developer Security Training: Enhancing Skills
Continuously improving your security skills through developer security training is crucial for writing secure Java code.
Here are some steps you can take to enhance your skills:
- Stay Updated : Keep yourself informed about the latest security threats, vulnerabilities, and best practices by following reputable security resources, attending security conferences, and participating in security-focused communities.
- Training Programs : Explore security training programs and certifications specifically designed for developers. These programs provide in-depth knowledge and practical guidance on secure coding practices, vulnerability assessment, and secure software development.
- Code Reviews : Engage in peer code reviews that include security-focused analysis. Collaborating with experienced developers can help identify potential security weaknesses and learn from their expertise.
- Security Tools : Utilize security analysis tools, such as static code analysis or vulnerability scanners, to identify potential security vulnerabilities in your code. These tools provide automated checks and recommendations for improvement.
By following these practices, avoiding common pitfalls, and continuously enhancing your security skills, you can write secure Java code that protects your applications and user data.
In conclusion, this book has equipped you with advanced Java programming skills crucial for any software engineer.
You've covered key topics ranging from unit testing and debugging to Java security, preparing you to handle real-world software development challenges.
Your journey through these chapters has enhanced your technical expertise, making you adept at creating efficient, secure, and robust software solutions.
Your newfound knowledge opens up a world of opportunities, from advancing in your current role to aspiring for senior developer positions or embarking on your own tech venture. With Java's role in AI, big data, and cloud computing, your skills are more relevant than ever.
As you step forward, remember that mastering Java is about applying these concepts to develop innovative solutions. Continue to grow, adapt to new technologies, and let your passion for programming drive you.
Now, with both the knowledge and confidence, you're ready to make your mark in the world of Java programming. Whether contributing to open-source projects, seeking Java certification, or innovating in your professional endeavors, you are well-prepared for the challenges and opportunities ahead. The path from learning to leading in the Java community awaits.
If you're keen on furthering your Java knowledge, here's a guide to help you conquer Java and launch your coding career . It's perfect for those interested in AI and machine learning, focusing on effective use of data structures in coding. This comprehensive program covers essential data structures, algorithms, and includes mentorship and career support.
Additionally, for more practice in data structures, you can explore these resources:
- Java Data Structures Mastery - Ace the Coding Interview : A free eBook to advance your Java skills, focusing on data structures for enhancing interview and professional skills.
- Foundations of Java Data Structures - Your Coding Catalyst : Another free eBook, diving into Java essentials, object-oriented programming, and AI applications.
Visit LunarTech's website for these resources and more information on the bootcamp .
Connect with Me:
- Follow me on LinkedIn for a ton of Free Resources in CS, ML and AI
- Visit my Personal Website
- Subscribe to my The Data Science and AI Newsletter
About the Author
I'm Vahe Aslanyan, specializing in the world of computer science, data science, and artificial intelligence. Explore my work at vaheaslanyan.com . My expertise encompasses robust full-stack development and the strategic enhancement of AI products, with a focus on inventive problem-solving.
.png)
My experience includes spearheading the launch of a prestigious data science bootcamp, an endeavor that put me at the forefront of industry innovation. I've consistently aimed to revolutionize technical education, striving to set a new, universal standard.
As we close this book, I extend my sincere thanks for your focused engagement. Imparting my professional insights through this book has been a journey of professional reflection. Your participation has been invaluable. I anticipate these shared experiences will significantly contribute to your growth in the dynamic field of technology.
I'm Vahe Aslanyan, dedicated to making AI and data science education inclusive and accessible. I guide developers towards clear tech understanding in software engineering.
If you read this far, thank the author to show them you care. Say Thanks
Learn to code for free. freeCodeCamp's open source curriculum has helped more than 40,000 people get jobs as developers. Get started
Open Educational Resources Repository
Jordan university of science and technology.
- JUST OER Repository Home
- Faculty of Computer & Information Technology
- Computer Science
- Digital Learning Materials - CS
Java, Java, Java: Object-Oriented Problem Solving
Description, collections.
The following license files are associated with this item:
- Creative Commons

In order to continue enjoying our site, we ask that you confirm your identity as a human. Thank you very much for your cooperation.
Enter the characters you see below
Sorry, we just need to make sure you're not a robot. For best results, please make sure your browser is accepting cookies.
Type the characters you see in this image:


1st Edition
Java Programming Fundamentals Problem Solving Through Object Oriented Analysis and Design
- Taylor & Francis eBooks (Institutional Purchase) Opens in new tab or window
Description
While Java texts are plentiful, it’s difficult to find one that takes a real-world approach, and encourages novice programmers to build on their Java skills through practical exercise. Written by an expert with 19 experience teaching computer programming, Java Programming Fundamentals presents object-oriented programming by employing examples taken from everyday life. Provides a foundation in object-oriented design principles and UML notation Describes common pitfalls and good programming practices Furnishes supplemental links, documents, and programs on its companion website, www.premnair.net Uses day-to-day life examples to introduce every object-oriented and programming concept Includes an extensive stand-alone chapter on GUI and event programming Contains numerous examples, self-check questions, quick review material and an extensive list of both programming and non-programming exercises The text presents object-oriented design and programming principles in a completely integrated and incremental fashion. It correlates each concept to a real-world application example and then introduces the corresponding Java language construct. The approach continues throughout the book, in that every concept is first introduced through practical examples, followed by short programming tutorials. To round out its coverage, the book provides several case studies, which illustrate various design issues and demonstrate the usefulness of techniques presented throughout the book. Using its one-of-a-kind approach, Java Programming Fundamentals demonstrates the object-oriented design techniques required to simulate actual real-life situations without compromising study of traditional programming constructs and structures.
Table of Contents
Premchand S. Nair
Critics' Reviews
…carefully thought out and well crafted … teaches object-oriented design and programming in a completely integrated and incremental fashion. … a pedagogically excellent first course in object-oriented design and programming … Nair’s outstanding book is my first choice for learning object orientation and Java in considerable depth … —George Hacken, in Computing Reviews, Reviews.com, July 2009 … covers a good deal of Java, while also providing the rudiments of UML, some fundamental algorithms like sorting, and data structures like arrays. … The abundance of examples and exercises is very valuable … Summing Up: Recommended. —L. Benedicenti, University of Regina, in CHOICE , Vol. 47, No. 04
About VitalSource eBooks
VitalSource is a leading provider of eBooks.
- Access your materials anywhere, at anytime.
- Customer preferences like text size, font type, page color and more.
- Take annotations in line as you read.
Multiple eBook Copies
This eBook is already in your shopping cart. If you would like to replace it with a different purchasing option please remove the current eBook option from your cart.
Book Preview

The country you have selected will result in the following:
- Product pricing will be adjusted to match the corresponding currency.
- The title Perception will be removed from your cart because it is not available in this region.
Section 1.5
Objects and object-oriented programming.
P rograms must be designed . No one can just sit down at the computer and compose a program of any complexity. The discipline called software engineering is concerned with the construction of correct, working, well-written programs. The software engineer tries to use accepted and proven methods for analyzing the problem to be solved and for designing a program to solve that problem.
During the 1970s and into the 80s, the primary software engineering methodology was structured programming . The structured programming approach to program design was based on the following advice: To solve a large problem, break the problem into several pieces and work on each piece separately; to solve each piece, treat it as a new problem which can itself be broken down into smaller problems; eventually, you will work your way down to problems that can be solved directly, without further decomposition. This approach is called top-down programming .
There is nothing wrong with top-down programming. It is a valuable and often-used approach to problem-solving. However, it is incomplete. For one thing, it deals almost entirely with producing the instructions necessary to solve a problem. But as time went on, people realized that the design of the data structures for a program was at least as important as the design of subroutines and control structures. Top-down programming doesn't give adequate consideration to the data that the program manipulates.
Another problem with strict top-down programming is that it makes it difficult to reuse work done for other projects. By starting with a particular problem and subdividing it into convenient pieces, top-down programming tends to produce a design that is unique to that problem. It is unlikely that you will be able to take a large chunk of programming from another program and fit it into your project, at least not without extensive modification. Producing high-quality programs is difficult and expensive, so programmers and the people who employ them are always eager to reuse past work.
So, in practice, top-down design is often combined with bottom-up design . In bottom-up design, the approach is to start "at the bottom," with problems that you already know how to solve (and for which you might already have a reusable software component at hand). From there, you can work upwards towards a solution to the overall problem.
The reusable components should be as "modular" as possible. A module is a component of a larger system that interacts with the rest of the system in a simple, well-defined, straightforward manner. The idea is that a module can be "plugged into" a system. The details of what goes on inside the module are not important to the system as a whole, as long as the module fulfills its assigned role correctly. This is called information hiding , and it is one of the most important principles of software engineering.
One common format for software modules is to contain some data, along with some subroutines for manipulating that data. For example, a mailing-list module might contain a list of names and addresses along with a subroutine for adding a new name, a subroutine for printing mailing labels, and so forth. In such modules, the data itself is often hidden inside the module; a program that uses the module can then manipulate the data only indirectly, by calling the subroutines provided by the module. This protects the data, since it can only be manipulated in known, well-defined ways. And it makes it easier for programs to use the module, since they don't have to worry about the details of how the data is represented. Information about the representation of the data is hidden.
Modules that could support this kind of information-hiding became common in programming languages in the early 1980s. Since then, a more advanced form of the same idea has more or less taken over software engineering. This latest approach is called object-oriented programming , often abbreviated as OOP.
The central concept of object-oriented programming is the object , which is a kind of module containing data and subroutines. The point-of-view in OOP is that an object is a kind of self-sufficient entity that has an internal state (the data it contains) and that can respond to messages (calls to its subroutines). A mailing list object, for example, has a state consisting of a list of names and addresses. If you send it a message telling it to add a name, it will respond by modifying its state to reflect the change. If you send it a message telling it to print itself, it will respond by printing out its list of names and addresses.
The OOP approach to software engineering is to start by identifying the objects involved in a problem and the messages that those objects should respond to. The program that results is a collection of objects, each with its own data and its own set of responsibilities. The objects interact by sending messages to each other. There is not much "top-down" in the large-scale design of such a program, and people used to more traditional programs can have a hard time getting used to OOP. However, people who use OOP would claim that object-oriented programs tend to be better models of the way the world itself works, and that they are therefore easier to write, easier to understand, and more likely to be correct.
You should think of objects as "knowing" how to respond to certain messages. Different objects might respond to the same message in different ways. For example, a "print" message would produce very different results, depending on the object it is sent to. This property of objects—that different objects can respond to the same message in different ways—is called polymorphism .
It is common for objects to bear a kind of "family resemblance" to one another. Objects that contain the same type of data and that respond to the same messages in the same way belong to the same class . (In actual programming, the class is primary; that is, a class is created and then one or more objects are created using that class as a template.) But objects can be similar without being in exactly the same class.
For example, consider a drawing program that lets the user draw lines, rectangles, ovals, polygons, and curves on the screen. In the program, each visible object on the screen could be represented by a software object in the program. There would be five classes of objects in the program, one for each type of visible object that can be drawn. All the lines would belong to one class, all the rectangles to another class, and so on. These classes are obviously related; all of them represent "drawable objects." They would, for example, all presumably be able to respond to a "draw yourself" message. Another level of grouping, based on the data needed to represent each type of object, is less obvious, but would be very useful in a program: We can group polygons and curves together as "multipoint objects," while lines, rectangles, and ovals are "two-point objects." (A line is determined by its two endpoints, a rectangle by two of its corners, and an oval by two corners of the rectangle that contains it. The rectangles that I am talking about here have sides that are vertical and horizontal, so that they can be specified by just two points; this is the common meaning of "rectangle" in drawing programs.) We could diagram these relationships as follows:

DrawableObject, MultipointObject, and TwoPointObject would be classes in the program. MultipointObject and TwoPointObject would be subclasses of DrawableObject. The class Line would be a subclass of TwoPointObject and (indirectly) of DrawableObject. A subclass of a class is said to inherit the properties of that class. The subclass can add to its inheritance and it can even "override" part of that inheritance (by defining a different response to some message). Nevertheless, lines, rectangles, and so on are drawable objects, and the class DrawableObject expresses this relationship.
Inheritance is a powerful means for organizing a program. It is also related to the problem of reusing software components. A class is the ultimate reusable component. Not only can it be reused directly if it fits exactly into a program you are trying to write, but if it just almost fits, you can still reuse it by defining a subclass and making only the small changes necessary to adapt it exactly to your needs.
So, OOP is meant to be both a superior program-development tool and a partial solution to the software reuse problem. Objects, classes, and object-oriented programming will be important themes throughout the rest of this text. You will start using objects that are built into the Java language in the next chapter , and in Chapter 5 you will begin creating your own classes and objects.

- All Courses
Object Oriented programming (OOP)
Problem solving in object oriented paradigm, introduction:, problem solving methodology in oop:.
The world around us is made up of objects, such as people, automobiles, buildings, streets, and so forth. Each of these objects has the ability to perform certain actions, and each of these actions has some effect on some of the other objects in the world.
OOP is a programming methodology that views a program as similarly consisting of objects that interact with each other by means of actions.
Object-oriented programming has its own specialized terminology. The objects are called, appropriately enough, objects. The actions that an object can take are called methods. Objects of the same kind are said to have the same type or, more often, are said to be in the same class.
For example, in an airport simulation program, all the simulated airplanes might belong to the same class, probably called the Airplane class. All objects within a class have the same methods. Thus, in a simulation program, all airplanes have the same methods (or possible actions), such as taking off, flying to a specific location, landing, and so forth. However, all simulated airplanes are not identical. They can have different characteristics, which are indicated in the program by associating different data (that is, some different information) with each particular airplane object. For example, the data associated with an airplane object might be two numbers for its speed and altitude.
Things that are called procedures, methods, functions, or subprograms in other languages are all called methods in Java. In Java, all methods (and for that matter, any programming constructs whatsoever) are part of a class.
Lab Activities:
Activity 1:.
Consider the concept of a CourseResult. The CourseResult should have data members like the student name, course name and grade obtained in that course.
This concept can be represented in a class as follows:
Public class CourseResult
Public String studentname; Public String coursename; Public String grade;
public void display()
System.out.println(“Student Name is: ― + studentname + “Course Name is: ― + coursename + “Grade is: ― + grade);
Public class CourseResultRun
public static void main(String[]args)
CourseResult c1=new CourseResult (); c1.studentName= ―Ali‖; c1.courseName= ―OOP‖;
c1.grade= ―A‖; c1.display();
CourseResult c2=new CourseResult (); c2.studentName= ―Saba‖; c2.courseName= ―ICP‖;
c2.grade= ―A+‖; c2.display();
Note that both objects; c1 and c2 have three data members, but each object has different values for their data members.
Activity 2:
The example below represents a Date class. As date is composed of three attributes, namely month, year and day; so the class contains three Data Members. Now every date object will have these three attributes, but each object can have different values for these three
public class Date
public String month; public int day;
public int year; //a four digit number.
public void displayDate()
System.out.println(month + ” ” + day + “, ” + year);
public class DateDemo
public static void main(String[] args)
Date date1, date2; date1 = new Date();
date1.month = “December”; date1.day = 31;
date1.year = 2012; System.out.println(“date1:”); date1.display();
Activity 3:
date2 = new Date(); date2.month = “July”; date2.day = 4;
date2.year = 1776; System.out.println(“date2:”); date2.display();
Consider the concept of a Car Part. After analyzing this concept we may consider that it can be described by three data members: modelNumber , partNumber and cost.
The methods should facilitate the user to assign values to these data members and show the values for each object.
importjavax.swing.JOptionPane;
Public class CarPart
private String modelNumber; private String partNumber; private String cost;
public void setparameter(String x, String y,String z)
modelNumber=x; partNumber=y; cost=z;
public static void display()
System.out.println(“Model Number: ―+modelNumber + ―Part Number: ―+partNumber +
―Cost: ― + cost);
Public class CarPartRunner
CarPart car1=new CarPart ();
String x=JOptionPane.showInputDialog(“What is Model Number?” ); String y=JOptionPane.showInputDialog(“What is Part Number?” ); String z=JOptionPane.showInputDialog(“What is Cost?” ); car1.setparameter(x,y,z);
car1.display();
Home Activities:
A Student is an object in a university management System. Analyze the concept and identify the data members that a Student class should have. Also analyze the behavior of student in a university management System and identify the methods that should be included in Student class.
Time is an intangible concept. Analyze the concept and identify the data members and methods that should be included in Time class.
Assignment 1:
Car is an object that helps us in transportation. Analyze the concept and identify the data members and methods that should be included in Car class.
Assignment 2:
Rectangle is an object that represents a specific shape. Analyze the concept and identify the data members and methods that should be included in Rectangle class.
Leave a Reply Cancel reply
You must be logged in to post a comment.

Important Pages
© Copyright Cuitutorial All Rights Reserved
Modal title

4 Advantages of Object-Oriented Programming

- Modularity for easier troubleshooting
- Reuse of code through inheritance
- Flexibility through polymorphism
- Effective problem solving
Object-oriented programming is such a fundamental part of software development that it’s hard to remember a time when people used any other approach. However, when objected-oriented programming, or OOP, first appeared in the 1980s, it was a radical leap forward from the traditional top-down method.
These days, most major software development is performed using OOP. Thanks to the widespread use of languages like Java and C++, you can’t develop software for mobile unless you understand the object-oriented approach. The same goes for web development, given the popularity of OOP languages like Python, PHP and Ruby. That said, many developers start off with top-down languages like Visual Basic or JavaScript.
You may be used to breaking down large problems into sub-problems and solving them in separate units of code. Or you may have experience with functional programming, which treats elements of code as precise mathematical functions, and prevents them from affecting other elements — that is, no side effects. Come to grips with OOP, however, and you’ll see that it offers a whole new way of solving problems.
With OOP, instead of writing a program, you create classes. A class contains both data and functions. When you want to create something in memory, you create an object, which is an instance of that class. So, for example, you can declare a Customer class, which holds data and functions related to customers. If you then want your program to create a customer in memory, you create a new object of the Customer class.
The advantages of object-oriented programming lie in this kind of encapsulation. Here’s a look at some of OOP’s top benefits:
1. Modularity for easier troubleshooting
When working with object-oriented programming languages, you know exactly where to look when something goes wrong. “Oh, the car object broke down? The problem must be in the Car class!” You don’t have to go line-by-line through all your code.
That’s the beauty of encapsulation. Objects are self-contained, and each bit of functionality does its own thing while leaving the other bits alone. Also, this modularity allows an IT team to work on multiple objects simultaneously while minimizing the chance that one person might duplicate someone else’s functionality.
2. Reuse of code through inheritance
Suppose that in addition to your Car object, one colleague needs a RaceCar object, and another needs a Limousine object. Everyone builds their objects separately but discover commonalities between them. In fact, each object is just a different kind of Car. This is where the inheritance technique saves time: Create one generic class (Car), and then define the subclasses (RaceCar and Limousine) that are to inherit the generic class’s traits.
Of course, Limousine and RaceCar still have their unique attributes and functions. If the RaceCar object needs a method to “fireAfterBurners” and the Limousine object requires a Chauffeur, each class could implement separate functions just for itself. However, because both classes inherit key aspects from the Car class, for example the “drive” or “fillUpGas” methods, your inheriting classes can simply reuse existing code instead of writing these functions all over again.
What if you want to make a change to all Car objects, regardless of type? This is another advantage of the OOP approach. Make a change to your Car class, and all car objects will simply inherit the new code.
3. Flexibility through polymorphism
Riffing on this example, you now need just a few drivers, or functions, like “driveCar,” driveRaceCar” and “DriveLimousine.” RaceCarDrivers share some traits with LimousineDrivers, but other things, like RaceHelmets and BeverageSponsorships, are unique.
This is where object-oriented programming’s polymorphism comes into play. Because a single function can shape-shift to adapt to whichever class it’s in, you could create one function in the parent Car class called “drive” — not “driveCar” or “driveRaceCar,” but just “drive.” This one function would work with the RaceCarDriver, LimousineDriver and so on. In fact, you could even have “raceCar.drive(myRaceCarDriver)” or “limo.drive(myChauffeur).”
4. Effective problem solving
Many people avoid learning OOP because the learning curve seems steeper than that for top-down programming. But take the time to master OOP and you’ll find it’s the easier, more intuitive approach for developing big projects.
Object-oriented programming is ultimately about taking a huge problem and breaking it down to solvable chunks. For each mini-problem, you write a class that does what you require. And then — best of all — you can reuse those classes, which makes it even quicker to solve the next problem.
This isn’t to say that OOP is the only way to write software. But there’s a reason that languages like C++, C# and Java are the go-to options for serious software development.
What to know about OOP developer jobs
There’s an insatiable demand right now for talented software developers with experience using C# and Java, and when it comes to job-hunting, employer demand is one of the biggest benefits of OOP. Employers are also keen for OOP programmers with other qualifications, such as Certified Information Security Manager (CISM) or AWS-Certified Cloud Practitioner.
Industries with the highest demand for OOP developers include:
- Financial services
- Professional services
- Real estate
- Retail and e-commerce
To find the projected starting salary for software developers, get the latest Robert Half Salary Guide . You can also find the market rates for your area in the Salary Guide.
If you’ve worked exclusively with top-down languages so far, it might be hard to land a position as an OOP developer. Here are some steps you can take to build up your object-oriented programming skills:
- Teach yourself an OOP language: The Java SDK is free to download and use. You will also find a wide range of free programming tutorials available online.
- Attend a boot camp: Boot camps are intended to help coders learn new skills, fast. They are usually intensive courses with a project at the end that shows what you’ve learned.
- Work on a solo project: The best way to learn is by doing, of course. Use your new skills to build software demos and test out new concepts. Android apps run on Java, so you can build a mobile application and release it to the world.
- Join coding forums: There are many online communities where you can network with more experienced developers. The pros you connect with in these forums can offer advice on ways to hone your skills and strengthen your resume.
Once you understand how to use classes and objects, you’ll wonder why you ever used anything else. And when you are able to start your career as an OOP developer, you’ll never look back.
- Trending Now
- Foundational Courses
- Data Science
- Practice Problem
- Machine Learning
- System Design
- DevOps Tutorial
- BCA 3rd Semester Syllabus (2023)
Introduction of Object Oriented Programming
- Abstraction in C++
- Encapsulation in C++
- C++ Classes and Objects
- Life cycle of Objects in C++ with Example
- What is Dynamic Memory Allocation?
- Difference between Inheritance and Polymorphism
- Class Hierarchy in Objective-C
- Generics in C++
- C++ Polymorphism
- Multiple Inheritance in C++
- Exception Handling in C++
- File Handling through C++ Classes
DS Using C and C++
- Introduction to Data Structures
- What is Array?
- Multidimensional Arrays in C
- Stack Data Structure
- Queue Data Structure
- Difference Between Stack and Queue Data Structures
- Linked List Data Structure
- Introduction to Tree Data Structure
- Introduction to Binary Tree
- Sorting Algorithms
Computer Architecture and Assembly Language
- Computer Organization and Architecture Tutorial
- Central Processing Unit (CPU)
- Introduction of General Register based CPU Organization
- RISC and CISC in Computer Organization
- Computer Organization | Booth's Algorithm
- Computer Arithmetic | Set - 1
- Introduction to Input-Output Interface
- Direct Memory Access (DMA) Controller in Computer Architecture
- Difference between Serial and Parallel Transmission
- Evolution of Microprocessors
- Difference between assembly language and high level language
Business Economics
- The Scope and Nature of Economics
- Revenue Formula
- Market : Characteristics & Classification
- Introduction to Macroeconomics
- Basic Concepts Related To Economics
Elements of Statistics
- Population vs Sample in Statistic
- Measures of Central Tendency in Statistics
- Measures of Dispersion | Types, Formula and Examples
- Permutations and Combinations
- Mathematics | Probability
- BCA 1st Semester Syllabus (2023)
- BCA 2nd Semester Syllabus (2023)
- BCA 4th Semester Syllabus (2023)
- BCA 5th Semester Syllabus (2023)
- BCA 6th Semester Subjects and Syllabus (2023)
- BCA Full Form
- Bachelor of Computer Applications: Curriculum and Career Opportunity
As the name suggests, Object-Oriented Programming or OOPs refers to languages that use objects in programming. Object-oriented programming aims to implement real-world entities like inheritance, hiding, polymorphism, etc in programming. The main aim of OOP is to bind together the data and the functions that operate on them so that no other part of the code can access this data except that function.
OOPs Concepts:
- Data Abstraction
- Encapsulation
- Inheritance
- Polymorphism
- Dynamic Binding
- Message Passing
A class is a user-defined data type. It consists of data members and member functions, which can be accessed and used by creating an instance of that class. It represents the set of properties or methods that are common to all objects of one type. A class is like a blueprint for an object.
For Example: Consider the Class of Cars. There may be many cars with different names and brands but all of them will share some common properties like all of them will have 4 wheels, Speed Limit, Mileage range, etc. So here, Car is the class, and wheels, speed limits, mileage are their properties.
2. Object:
It is a basic unit of Object-Oriented Programming and represents the real-life entities. An Object is an instance of a Class. When a class is defined, no memory is allocated but when it is instantiated (i.e. an object is created) memory is allocated. An object has an identity, state, and behavior. Each object contains data and code to manipulate the data. Objects can interact without having to know details of each other’s data or code, it is sufficient to know the type of message accepted and type of response returned by the objects.
For example “Dog” is a real-life Object, which has some characteristics like color, Breed, Bark, Sleep, and Eats.
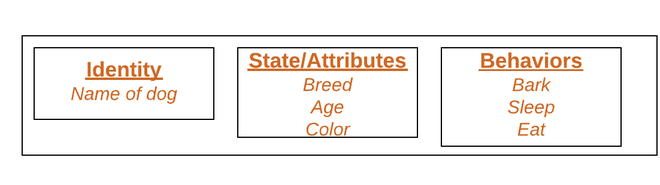
3. Data Abstraction:
Data abstraction is one of the most essential and important features of object-oriented programming. Data abstraction refers to providing only essential information about the data to the outside world, hiding the background details or implementation. Consider a real-life example of a man driving a car. The man only knows that pressing the accelerators will increase the speed of the car or applying brakes will stop the car, but he does not know about how on pressing the accelerator the speed is increasing, he does not know about the inner mechanism of the car or the implementation of the accelerator, brakes, etc in the car. This is what abstraction is.
4. Encapsulation:
Encapsulation is defined as the wrapping up of data under a single unit. It is the mechanism that binds together code and the data it manipulates. In Encapsulation, the variables or data of a class are hidden from any other class and can be accessed only through any member function of their class in which they are declared. As in encapsulation, the data in a class is hidden from other classes, so it is also known as data-hiding .
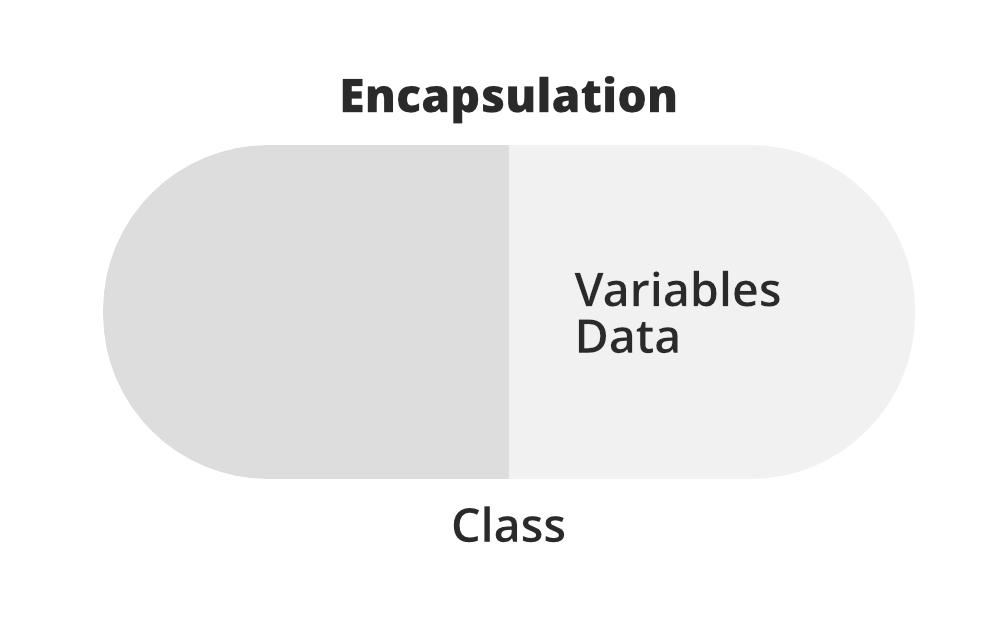
Consider a real-life example of encapsulation, in a company, there are different sections like the accounts section, finance section, sales section, etc. The finance section handles all the financial transactions and keeps records of all the data related to finance. Similarly, the sales section handles all the sales-related activities and keeps records of all the sales. Now there may arise a situation when for some reason an official from the finance section needs all the data about sales in a particular month. In this case, he is not allowed to directly access the data of the sales section. He will first have to contact some other officer in the sales section and then request him to give the particular data. This is what encapsulation is. Here the data of the sales section and the employees that can manipulate them are wrapped under a single name “sales section”.
5. Inheritance:
Inheritance is an important pillar of OOP(Object-Oriented Programming). The capability of a class to derive properties and characteristics from another class is called Inheritance. When we write a class, we inherit properties from other classes. So when we create a class, we do not need to write all the properties and functions again and again, as these can be inherited from another class that possesses it. Inheritance allows the user to reuse the code whenever possible and reduce its redundancy.
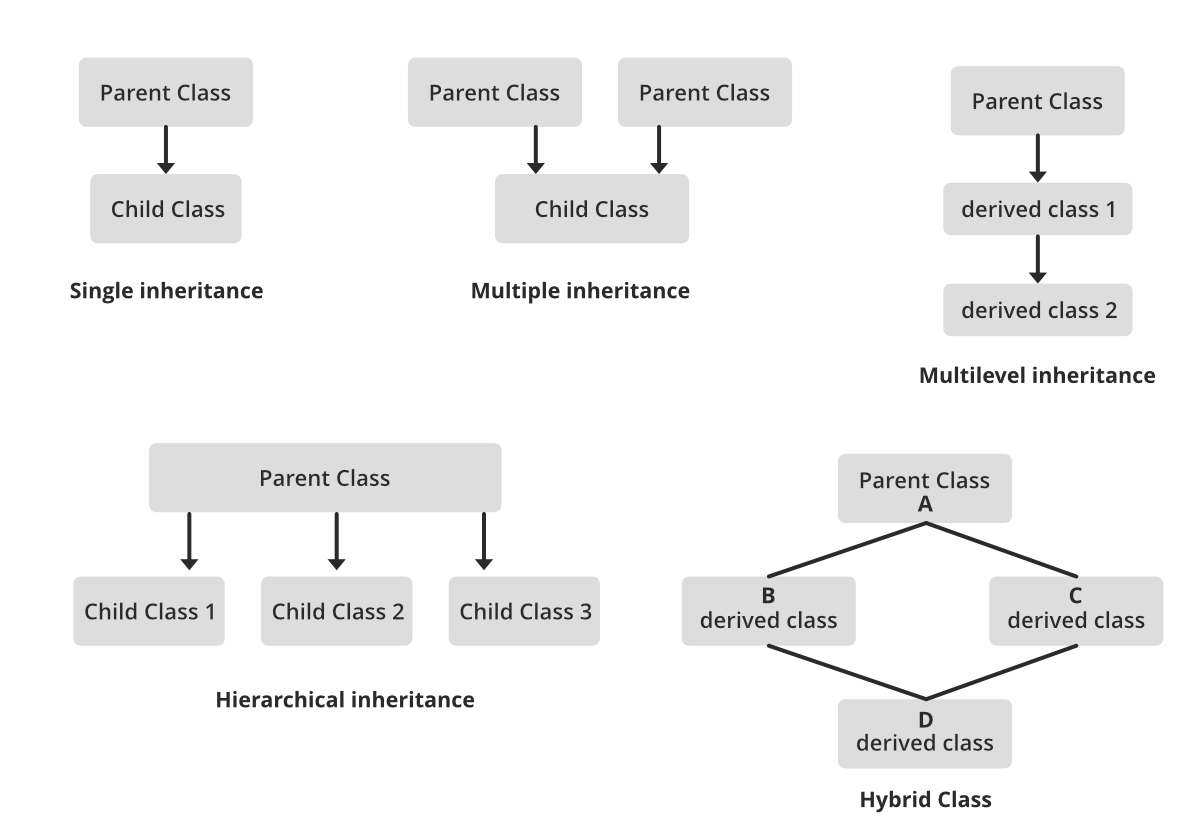
6. Polymorphism:
The word polymorphism means having many forms. In simple words, we can define polymorphism as the ability of a message to be displayed in more than one form. For example, A person at the same time can have different characteristics. Like a man at the same time is a father, a husband, an employee. So the same person posses different behavior in different situations. This is called polymorphism.
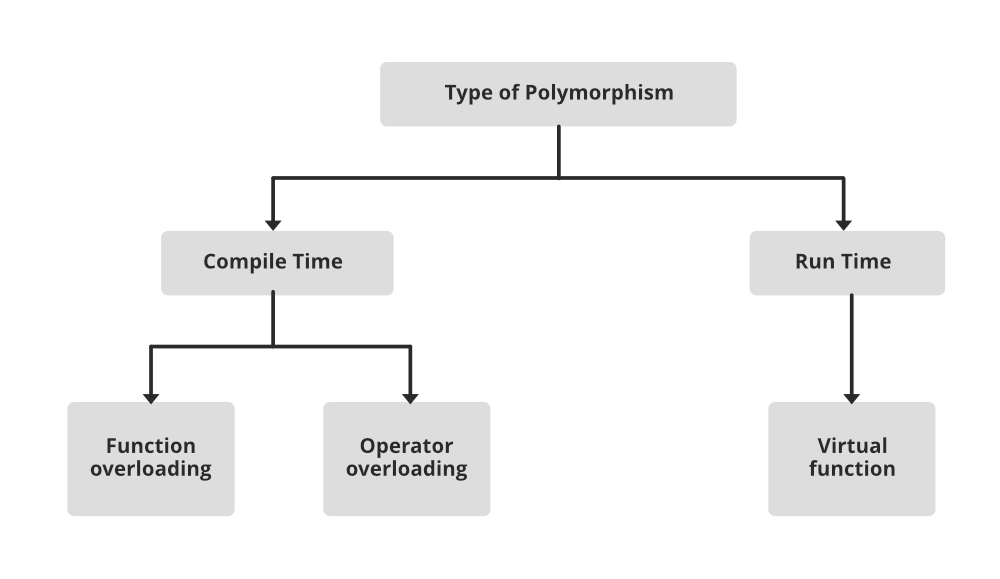
7. Dynamic Binding:
In dynamic binding, the code to be executed in response to the function call is decided at runtime. Dynamic binding means that the code associated with a given procedure call is not known until the time of the call at run time. Dynamic Method Binding One of the main advantages of inheritance is that some derived class D has all the members of its base class B. Once D is not hiding any of the public members of B, then an object of D can represent B in any context where a B could be used. This feature is known as subtype polymorphism.
8. Message Passing:
It is a form of communication used in object-oriented programming as well as parallel programming. Objects communicate with one another by sending and receiving information to each other. A message for an object is a request for execution of a procedure and therefore will invoke a function in the receiving object that generates the desired results. Message passing involves specifying the name of the object, the name of the function, and the information to be sent.
Why do we need object-oriented programming
- To make the development and maintenance of projects more effortless.
- To provide the feature of data hiding that is good for security concerns.
- We can solve real-world problems if we are using object-oriented programming.
- It ensures code reusability.
- It lets us write generic code: which will work with a range of data, so we don’t have to write basic stuff over and over again.

Please Login to comment...
Similar reads.
- Programming Language
- School Programming
Improve your Coding Skills with Practice
What kind of Experience do you want to share?

- System Analysis and Design Tutorial
- System Analysis and Design - Home
- System Analysis & Design - Overview
- System Development Life Cycle
- System Planning
- Structured Analysis
- System Design
- Design Strategies
- Input / Output & Forms Design
- Testing and Quality Assurance
- Implementation & Maintenance
- System Security and Audit
- Object-Oriented Approach
- System Analysis & Design Resources
- Quick Guide
- Useful Resources
- Selected Reading
- UPSC IAS Exams Notes
- Developer's Best Practices
- Questions and Answers
- Effective Resume Writing
- HR Interview Questions
- Computer Glossary
Object Oriented Approach
In the object-oriented approach, the focus is on capturing the structure and behavior of information systems into small modules that combines both data and process. The main aim of Object Oriented Design (OOD) is to improve the quality and productivity of system analysis and design by making it more usable.
In analysis phase, OO models are used to fill the gap between problem and solution. It performs well in situation where systems are undergoing continuous design, adaption, and maintenance. It identifies the objects in problem domain, classifying them in terms of data and behavior.
The OO model is beneficial in the following ways −
It facilitates changes in the system at low cost.
It promotes the reuse of components.
It simplifies the problem of integrating components to configure large system.
It simplifies the design of distributed systems.
Elements of Object-Oriented System
Let us go through the characteristics of OO System −
Objects − An object is something that is exists within problem domain and can be identified by data (attribute) or behavior. All tangible entities (student, patient) and some intangible entities (bank account) are modeled as object.
Attributes − They describe information about the object.
Behavior − It specifies what the object can do. It defines the operation performed on objects.
Class − A class encapsulates the data and its behavior. Objects with similar meaning and purpose grouped together as class.
Methods − Methods determine the behavior of a class. They are nothing more than an action that an object can perform.
Message − A message is a function or procedure call from one object to another. They are information sent to objects to trigger methods. Essentially, a message is a function or procedure call from one object to another.
Features of Object-Oriented System
An object-oriented system comes with several great features which are discussed below.
Encapsulation
Encapsulation is a process of information hiding. It is simply the combination of process and data into a single entity. Data of an object is hidden from the rest of the system and available only through the services of the class. It allows improvement or modification of methods used by objects without affecting other parts of a system.
Abstraction
It is a process of taking or selecting necessary method and attributes to specify the object. It focuses on essential characteristics of an object relative to perspective of user.
Relationships
All the classes in the system are related with each other. The objects do not exist in isolation, they exist in relationship with other objects.
There are three types of object relationships −
Aggregation − It indicates relationship between a whole and its parts.
Association − In this, two classes are related or connected in some way such as one class works with another to perform a task or one class acts upon other class.
Generalization − The child class is based on parent class. It indicates that two classes are similar but have some differences.
Inheritance
Inheritance is a great feature that allows to create sub-classes from an existing class by inheriting the attributes and/or operations of existing classes.
Polymorphism and Dynamic Binding
Polymorphism is the ability to take on many different forms. It applies to both objects and operations. A polymorphic object is one who true type hides within a super or parent class.
In polymorphic operation, the operation may be carried out differently by different classes of objects. It allows us to manipulate objects of different classes by knowing only their common properties.
Structured Approach Vs. Object-Oriented Approach
The following table explains how the object-oriented approach differs from the traditional structured approach −
| Structured Approach | Object Oriented Approach |
|---|---|
| It works with Top-down approach. | It works with Bottom-up approach. |
| Program is divided into number of submodules or functions. | Program is organized by having number of classes and objects. |
| Function call is used. | Message passing is used. |
| Software reuse is not possible. | Reusability is possible. |
| Structured design programming usually left until end phases. | Object oriented design programming done concurrently with other phases. |
| Structured Design is more suitable for offshoring. | It is suitable for in-house development. |
| It shows clear transition from design to implementation. | Not so clear transition from design to implementation. |
| It is suitable for real time system, embedded system and projects where objects are not the most useful level of abstraction. | It is suitable for most business applications, game development projects, which are expected to customize or extended. |
| DFD & E-R diagram model the data. | Class diagram, sequence diagram, state chart diagram, and use cases all contribute. |
| In this, projects can be managed easily due to clearly identifiable phases. | In this approach, projects can be difficult to manage due to uncertain transitions between phase. |
Unified Modeling Language (UML)
UML is a visual language that lets you to model processes, software, and systems to express the design of system architecture. It is a standard language for designing and documenting a system in an object oriented manner that allow technical architects to communicate with developer.
It is defined as set of specifications created and distributed by Object Management Group. UML is extensible and scalable.
The objective of UML is to provide a common vocabulary of object-oriented terms and diagramming techniques that is rich enough to model any systems development project from analysis through implementation.
UML is made up of −
Diagrams − It is a pictorial representations of process, system, or some part of it.
Notations − It consists of elements that work together in a diagram such as connectors, symbols, notes, etc.
Example of UML Notation for class
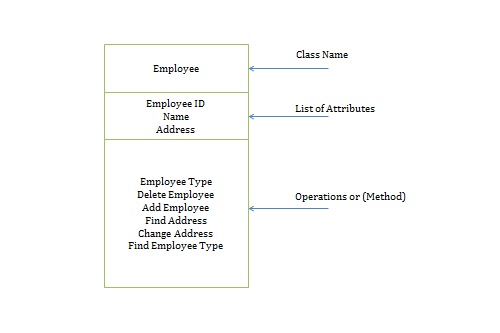
Instance diagram-UML notation
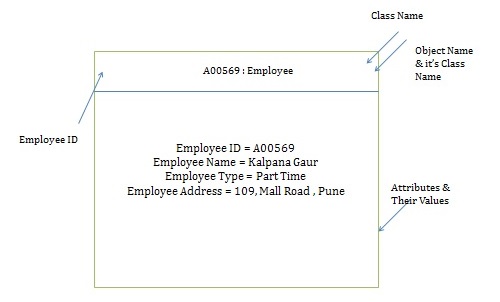
Operations Performed on Objects
The following operations are performed on the objects −
Constructor/Destructor − Creating new instances of a class and deleting existing instances of a class. For example, adding a new employee.
Query − Accessing state without changing value, has no side effects. For example, finding address of a particular employee.
Update − Changes value of one or more attributes & affect state of object For example, changing the address of an employee.
Uses of UML
UML is quite useful for the following purposes −
- Modeling the business process
- Describing the system architecture
- Showing the application structure
- Capturing the system behavior
- Modeling the data structure
- Building the detailed specifications of the system
- Sketching the ideas
- Generating the program code
Static Models
Static models show the structural characteristics of a system, describe its system structure, and emphasize on the parts that make up the system.
They are used to define class names, attributes, methods, signature, and packages.
UML diagrams that represent static model include class diagram, object diagram, and use case diagram.
Dynamic Models
Dynamic models show the behavioral characteristics of a system, i.e., how the system behaves in response to external events.
Dynamic models identify the object needed and how they work together through methods and messages.
They are used to design the logic and behavior of system.
UML diagrams represent dynamic model include sequence diagram, communication diagram, state diagram, activity diagram.
Object Oriented System Development Life Cycle
It consists of three macro processes −
- Object Oriented Analysis (OOA)
- Object oriented design (OOD)
- Object oriented Implementation (OOI)
Object Oriented Systems Development Activities
Object-oriented systems development includes the following stages −
- Object-oriented analysis
- Object-oriented design
Prototyping
Implementation.
- Incremental testing
Object-Oriented Analysis
This phase concerns with determining the system requirements and to understand the system requirements build a use-case model . A use-case is a scenario to describe the interaction between user and computer system. This model represents the user needs or user view of system.
It also includes identifying the classes and their relationships to the other classes in the problem domain, that make up an application.
Object-Oriented Design
The objective of this phase is to design and refine the classes, attributes, methods, and structures that are identified during the analysis phase, user interface, and data access. This phase also identifies and defines the additional classes or objects that support implementation of the requirement.
Prototyping enables to fully understand how easy or difficult it will be to implement some of the features of the system.
It can also give users a chance to comment on the usability and usefulness of the design. It can further define a use-case and make use-case modeling much easier.
It uses either Component-Based Development (CBD) or Rapid Application Development (RAD).
Component-based development (CBD)
CODD is an industrialized approach to the software development process using various range of technologies like CASE tools. Application development moves from custom development to assembly of pre-built, pre-tested, reusable software components that operate with each other. A CBD developer can assemble components to construct a complete software system.
Rapid Application Development (RAD)
RAD is a set of tools and techniques that can be used to build an application faster than typically possible with traditional methods. It does not replace SDLC but complements it, since it focuses more on process description and can be combined perfectly with the object oriented approach.
Its task is to build the application quickly and incrementally implement the user requirements design through tools such as visual basic, power builder, etc.
Incremental Testing
Software development and all of its activities including testing are an iterative process. Therefore, it can be a costly affair if we wait to test a product only after its complete development. Here incremental testing comes into picture wherein the product is tested during various stages of its development.
Basics of object-oriented problem solving
Summary: We consider, at a high level, the basic issues involved in object-oriented problem solving and object-oriented programming languages.
Prerequisites: None.
Background: Problem-Solving Paradigms
As you may have heard, Computer Science is the study of algorithms (formalized instructions for solving problems) and data. One key aspect of this study involves the ways in which we represent algorithms. Early algorithms (by early, I mean long before computers) were often written as examples. For example, in describing how to compute the volume of a rectangular hole, one might say “Suppose the hole is 3 feet deep, 4 feet wide, and 6 feet long. We multiply 4 and 6 to get the area of a cross section, and then by 3 to get the volume of the hole.”
With the advent of automated computing devices, it became important to describe algorithms more carefully, and in such a way that the steps of the algorithm could be automated. In thinking about these descriptions, computer scientists developed four main paradigms for structuring solutions.
In imperative (also procedural ) languages, we express algorithms as a sequence of individual steps. Steps traditionally involve basic computation, input, and output. To some, imperative algorithms look very much like the recipes in a cookbook (do this, do that, do this other thing this many times).
In functional languages, we express algorithms by defining and combining functions. Functional algorithms tend to deemphasize precise sequencing of operations; for example, it usually does not matter which argument to a function you compute first.
In object-oriented languages, we express algorithms by defining “objects” and having the objects interact with each other.
In declarative languages, we express algorithms by specifying a set of facts or goals, and let the computer determine how to apply those facts or goals to solve the problem at hand.
Why object-oriented?
Object-oriented languages currently dominate, although most of these languages also have a strong imperative aspect. (The past few years have also seen strong growth in the use of functional approaches in languages; most new languages are now multi-paradigm languages.) Why do programmers like object-oriented languages? There are a variety of reasons to like these languages.
First, object-oriented languages are appropriate for programs that model the real world. In writing such models, we can have one object in the program for each object in the world. If your task is to, say, figure out optimal cashier placement at Wal-Mart, such modeling is completely appropriate.
Second, object-oriented languages can simplify parallelization. Since each object can, in effect, work independently, it is possible to put different objects on different processors, and therefore make the program faster.
Third, object-oriented languages are helpful in building for modern graphical user interfaces (GUIs). Programmers have found it much easier to design and implement GUIs when they think of each part of the interface as an object that communicates with other objects in the interface and with objects that provide the underlying computation. For example, we can think of each menu, each button, and each window as a separate object and write the code by which they react to user actions separately.
Finally, it turns out that many core ideas of object-oriented programming make it much easier to write large programs and to reuse code written for previous programs (or for other parts of the same program). We will visit and revisit these approaches and their associated efficiencies.
Object basics
So, what is an object? In object-oriented problem solving, we think of an object as something that collects data and capabilities. Typically, the data within the object are categorized. For example, if we have an object that represents a book, we would identify part of the data as the title, part as the author, part as the publisher, and so on and so forth. Similarly, for an object that represents a menu, we would identify part of the data as the name of the menu and other parts as the items in the menu.
Traditionally, we call the categorized parts of an object the fields or attributes of the object.
But objects do more than collect data. Most objects also provide a variety of capabilities. That is, they can do things, typically things with their internal data (and with values passed in). For example, a book object might provide the text of a page, if you give it a page number, and a menu object might tell you what item was last selected. Some call these capabilities methods (the term we will use). Others refer to them as messages or message handlers . You may also think of them as procedures or functions .
Encapsulation: Separating what from how
In a well-designed object-oriented program, the clients of an object (that is, the other objects that use an object or the programmers who write those objects) interact with an object and the fields of the object exclusively through the methods of that object. Why limit that access? That is, why not give the client direct access to the fields? Experience suggests that giving the client such access can create problems in the long term. For example, suppose the client assumes your object has a field called lastName . If you later change the name of that field, to, say, surname , the client code will no longer work. In almost every case, the program will be just as efficient if the client does not directly access the fields, so there is little reason to give the client that access.
In fact, there are also other reasons to limit access to the internals of an object (not just the fields, but also the details of how each method works). By limiting such access, you absolve the client from having to know how each method works. Clients need only know what your methods do. Consider a rational number (fraction) object. It is likely that you will represent rational numbers as a pair of integers, one for the numerator and one for the denominator. A client that uses your numerator and denominator will need to know not only what names you have chosen for the numerator and denominator, but also particular other details of your representation, such as how you deal with negative numbers and whether you always store rational numbers in simplified form. Rather than forcing the client to know such details, we use methods to separate what one might do with an object (e.g., negate a number) from how we implement those methods.
Traditionally, we call such the separation of the interface (what an object does) from the implementation (how it achieves) its goals information hiding .
Because objects combine methods and data and protect the data from the outside world, we often say that objects encapsulate their contents.
Classes: Templates for objects
One of the first problems any object-oriented language designer encounters is how programmers are to describe the objects that appear in their programs. Many object-oriented languages rely on classes . A class is, in effect, a template for objects. Each class gives the names (and, often, types) of the fields for related objects and the names (and, often, instructions) for the related methods.
For example, a class to represent rational numbers might have two fields, a numerator (integer) and a denominator (integer). It might provide methods to add another rational number to the current rational, subtract another rational number, multiply by another rational number, and so on and so forth.
Similarly, a class to represent books might have a field for the title (a string), a field for the authors (a list of names, where “name” is a previously defined class), a field for the pages, and so on and so forth. That class might provide methods to access the title and authors (but probably not to change them) and to get pages by number.
Inheritance: Building new classes from old
Object-oriented programmers quickly realize that the new classes they build often closely relate to previous classes they’ve built. For example, if we are called upon to write a class to represent library books, that class will be very similar to the class for regular books, except that the library book class will include additional fields (such as the call number) and additional methods (such as checking the book in or out). The technique called inheritance permits you to define a new class in terms of an old class, and “automatically” inherit all of the fields and methods of the original class.
At times, when we inherit from another class, we also want to override (change the behavior of) some of the methods of the original class. Most object-oriented languages permit such behavior. For example, suppose we design a square class that inherits from the rectangle class. If the rectangle class includes a method that sets the width, we would want the square class to change that method to set both width and height.
Although some aspects of inheritance could be implemented by the legendary technique of copying and pasting code, real inheritance permits one to make changes to the original class and have those changes automatically propagate to the inheriting class. The automatic reuse and update capabilities associate with inheritance are one of the reasons programmers so prefer object-oriented programming.
Polymorphism: Writing general code
The final key aspect of most object-oriented languages is called polymorphism . While inheritance lets you reuse field and method definitions by building new classes from old, polymorphism lets you write a common piece of code that can be used in multiple contexts.
In subtype polymorphism , you can reuse methods by applying them to new objects. In particular, subtype polymorphism is the notion that you once you write methods that make particular assumptions about the objects they take as parameters (most typically, the methods those objects provide), those methods can then work with any objects that meet those assumptions.
For example, we know that we can square anything that we can multiply by itself. The square operation can therefore work with integers, real numbers, and complex numbers. It can even work with new numeric types we develop, such as rational rational numbers, as long as we define the multiply operation for those types.
In parametric polymorphism , you can design generic types and then make them work concretely by specifying a “parameter type”. For example, we can write a generic list type and then make concrete list-of-string and list-of-integer types.
Summary: Some things to look for when learning a new OOP language
In this short reading, we’ve considered some key aspects of object-oriented programming languages. When you start to learn a new object-oriented language, you will need to find out how each of these features is implemented. In particular, you may need to figure out
- how to define a class (and the methods and fields in that class);
- how, given a class, to build objects that belong to that class;
- how to indicate that one class inherits from another,;
- how to write a polymorphic method (one that works with multiple kinds of related objects); and
- how to write a polymorphic class or type (one that can be specialized to hold particular types).
We will cover each of these ideas in our explorations of Java. You’ll also find that other languages take somewhat different approaches. For example, in some languages, we achieve subtype polymorphism through “duck typing”.
Wrapping up
Important terms.
- Encapsulation
- Inherit/Inheritance
- Polymorphism
Review Questions
- Why do programmers like object-oriented programming?
- What are two benefits to encapsulation?
- Why does inheritance improve code reuse?
- Why does polymorphism improve code reuse?
Exploratory Questions
- In the reading, we noted that most, but not all, object-oriented languages use classes. Find an object-oriented language that does not use classes and determine how programmers create new objects in such languages.
- Find a few examples of polymorphic functions.
- Find a few examples of polymorphic data structures (or ADTs).
Copyright © Samuel A. Rebelsky
Unless specified otherwise elsewhere on this page, this work is licensed under a Creative Commons Attribution 3.0 Unported License. To view a copy of this license, visit http://creativecommons.org/licenses/by-nc/3.0/ or send a letter to Creative Commons, 543 Howard Street, 5th Floor, San Francisco, California, 94105, USA.
This website was built using Jekyll , Twitter Bootstrap , and the Bootswatch Cosmo Theme .
Last updated 27/06/24: Online ordering is currently unavailable due to technical issues. We apologise for any delays responding to customers while we resolve this. For further updates please visit our website: https://www.cambridge.org/news-and-insights/technical-incident
We use cookies to distinguish you from other users and to provide you with a better experience on our websites. Close this message to accept cookies or find out how to manage your cookie settings .
Login Alert

- > Research and Development in Expert Systems IX
- > An object oriented approach to distributed problem solving
Book contents
- Frontmatter
Introduction
- CONSULTANT: providing advice for the machine learning toolbox
- A methods model for the integration of KBS and conventional information technology
- KBS methodology as a framework for co-operative working
- Project management for the evolutionary development of expert systems
- The specification and development of rule-based expert systems
- Towards a method for multi-agent system design
- Jigsaw: configuring knowledge acquisition tools
- On the relationship between repertory grid and term subsumption knowledge structures: theory practice tools
- Strategy maze: an on-line tool for support management of the knowledge acquisition process
- Concurrent engineering using collaborating truth maintenance systems
- Ockham's razor as a gardening tool
- A designer's consultant
- Fairness of attribute selection in probabilistic induction
- An application of case-based expert system technology to dynamic job-shop scheduling
- Neural network design via LP
- KEshell2: an intelligent learning data base system
- Approaches to self-explanation and system visibility in the context of application tasks
- An object oriented approach to distributed problem solving
- Intelligent user interface for multiple application systems
- Combining qualitative and quantitative information for temporal reasoning
- Documents as expert systems
Published online by Cambridge University Press: 04 August 2010
One of the principal difficulties in developing a distributed problem solver is how to distribute the reasoning task between the agents cooperating to find a solution.
We will propose the distributed logic programming language DLP as a vehicle for the design and implementation of distributed knowledge based systems. The language DLP combines logic programming with active objects .
We will show how object oriented modeling may be applied for the specification and implementation of a distributed diagnostic (medical) expert system. The example illustrates how the diagnostic process is distributed over the agents participating in the diagnosis according to the structure of the knowledge of that particular domain.
Keywords: object oriented modeling, distributed problem-solving, knowledge-based systems, expert systems, distributed logic programming
Logic programming offers a declarative way to solve problems in Artificial Intelligence. However, when implementing large (possibly distributed) systems, traditional software engineering problems such as modularization and the distribution of data and control reoccur. Cf. [Subrahmanyam, 1985].
Due to its declarative nature, logic programming has become popular for implementing knowledge-based systems. However, lacking adequate modularization facilities, logic programming languages such as Prolog fall short in providing the mechanisms necessary to specify the distribution of data and control.
Object oriented modeling To tackle these problems, we suggest in this paper to embed the logic programming paradigm into an object oriented approach.
Access options
Save book to kindle.
To save this book to your Kindle, first ensure [email protected] is added to your Approved Personal Document E-mail List under your Personal Document Settings on the Manage Your Content and Devices page of your Amazon account. Then enter the ‘name’ part of your Kindle email address below. Find out more about saving to your Kindle .
Note you can select to save to either the @free.kindle.com or @kindle.com variations. ‘@free.kindle.com’ emails are free but can only be saved to your device when it is connected to wi-fi. ‘@kindle.com’ emails can be delivered even when you are not connected to wi-fi, but note that service fees apply.
Find out more about the Kindle Personal Document Service .
- By A. Eliëns , Vrije Universiteit, Department of Mathematics and Computer Science De Boelelaau 1081, 1081 HV Amsterdam The Netherlands
- M. A. Bramer , University of Portsmouth , R. W. Milne
- Book: Research and Development in Expert Systems IX
- Online publication: 04 August 2010
- Chapter DOI: https://doi.org/10.1017/CBO9780511569944.019
Save book to Dropbox
To save content items to your account, please confirm that you agree to abide by our usage policies. If this is the first time you use this feature, you will be asked to authorise Cambridge Core to connect with your account. Find out more about saving content to Dropbox .
Save book to Google Drive
To save content items to your account, please confirm that you agree to abide by our usage policies. If this is the first time you use this feature, you will be asked to authorise Cambridge Core to connect with your account. Find out more about saving content to Google Drive .

COMMENTS
About the Book. We have designed this third edition of Java, Java, Java to be suitable for a typical Introduction to Computer Science (CS1) course or for a slightly more advanced Java as a Second Language course. This edition retains the "objects first" approach to programming and problem solving that was characteristic of the first two ...
Object-oriented programming (OOP) is a fundamental programming paradigm used by nearly every developer at some point in their career. OOP is the most popular programming paradigm used for software development and is taught as the standard way to code for most of a programmer's educational career. Another popular programming paradigm is ...
The most common programming paradigms are procedural, functional, and object-oriented programming. Object-oriented is the most popular, and the one most often taught in programming courses. Object-oriented programming is a software development approach that focuses on defining and sculpting named classes as entities with attributes and behaviors.
OO, or Object Oriented, programming refers to a set of activities that lead to a computer program, written in an object-oriented language, that when executed on a computer will solve a problem. Java is an OO language used in CS 180. Other OO languages include C++, C#, Delphi, Modula, Oberon, Objective C, Simula, Smalltalk, and many more!
In object-oriented problem solving, we think of an object as something that collects data and capabilities. Typically, the data within the object are categorized. For example, if we have an object that represents a book, we would identify part of the data as the title, part as the author, part as the publisher, and so on and so forth.
Object-oriented programming (OOP) is a fundamental programming paradigm based on the concept of " objects ". These objects can contain data in the form of fields (often known as attributes or properties) and code in the form of procedures (often known as methods). The core concept of the object-oriented approach is to break complex problems ...
1. The real world is made up of objects and each object has its own behaviour and characteristics. Using object-oriented programming we can represent real world problems and solve them in a much more efficient manner. This paper has represented several real-world problems and how it is solved using objects and classes.
• Introduce the object-oriented paradigm • Contrast it with functional decomposition • Discuss important concepts of object-oriented programming • Discuss the difference between abstraction and encapsulation • This is VERY important • Address the problem of requirements and the need to deal with change 2
Get started. Java is a go-to language for many programmers, and it's a critical skill for any software engineer. After learning Java, picking up other programming languages and advanced concepts becomes much easier. In this book, I'll cover the practical knowledge you need to move from writing basic Java code to.
Description. We have designed this third edition of Java, Java, Java to be suitable for a typical Introduction to Computer Science (CS1) course or for a slightly more advanced Java as a Second Language course. This edition retains the "objects first" approach to programming and problem solving that was characteristic of the first two editions.
Object-oriented programming, or OOP, is an approach to problem solving where all computations are carried out using objects. An object is a component of a program that knows how to perform certain ...
Problem-Solving Approach. A pedagogical, problem-solving approach is taken throughout the text. There are a total of 13 fully developed case studies, as well as numerous other examples that illustrate the problem-solving process. Marginal notes in the text repeatedly emphasize the basic elements of object-oriented problem solving: What objects ...
While Java texts are plentiful, it's difficult to find one that takes a real-world approach, and encourages novice programmers to build on their Java skills through practical exercise. Written by an expert with 19 experience teaching computer programming, Java Programming Fundamentals presents object-oriented programming by employing examples taken from everyday life. Provides a foundation ...
The OOP approach to software engineering is to start by identifying the objects involved in a problem and the messages that those objects should respond to. The program that results is a collection of objects, each with its own data and its own set of responsibilities. The objects interact by sending messages to each other.
Object-oriented programming has its own specialized terminology. The objects are called, appropriately enough, objects. The actions that an object can take are called methods. Objects of the same kind are said to have the same type or, more often, are said to be in the same class. For example, in an airport simulation program, all the simulated ...
I had a problem to be solved and I was solving it step by step. To better understand the difference between the procedural and Object-Oriented Programming approach to solving problems lets look at ...
Object-oriented programming is such a fundamental part of software development that it's hard to remember a time when people used any other approach. However, when objected-oriented programming, or OOP, first appeared in the 1980s, it was a radical leap forward from the traditional top-down method.
Encapsulation is one of the fundamental concepts in object-oriented programming (OOP). It describes the idea of wrapping data and the methods that work on data within one unit, e.g., a class in Java. This concept is often used to hide the internal state representation of an object from the outside. Inheritance -.
As the name suggests, Object-Oriented Programming or OOPs refers to languages that use objects in programming. Object-oriented programming aims to implement real-world entities like inheritance, hiding, polymorphism, etc in programming. The main aim of OOP is to bind together the data and the functions that operate on them so that no other part ...
In the object-oriented approach, the focus is on capturing the structure and behavior of information systems into small modules that combines both data and process. The main aim of Object Oriented Design (OOD) is to improve the quality and productivity of system analysis and design by making it more usable. In analysis phase, OO models are used ...
A typical extract of analysis of the collaborative solution is presented here. The problem solving team studied in this section is A-B-F comprising a group of two students (A, B) solving a problem and the tutor called F (Facilitator). For group A-B-F the produced OCAF model contained the following items: M = {.
Basics of object-oriented problem solving. Summary: We consider, at a high level, the basic issues involved in object-oriented problem solving and object-oriented programming languages. Prerequisites: None. Background: Problem-Solving Paradigms. As you may have heard, Computer Science is the study of algorithms (formalized instructions for solving problems) and data.
An object oriented approach to distributed problem solving; By A. Eliëns, Vrije Universiteit, Department of Mathematics and Computer Science De Boelelaau 1081, 1081 HV Amsterdam The Netherlands M. A. Bramer, University of Portsmouth, R. W. Milne; Book: Research and Development in Expert Systems IX; Online publication: 04 August 2010