
- My presentations

Auth with social network:
Download presentation
We think you have liked this presentation. If you wish to download it, please recommend it to your friends in any social system. Share buttons are a little bit lower. Thank you!
Presentation is loading. Please wait.
Components of a computer
Published by Ethelbert Preston Modified over 8 years ago
Similar presentations
Presentation on theme: "Components of a computer"— Presentation transcript:

HARDWARE Rashedul Hasan..

Introduction to Computer Hardware and Software. Definition of a Computer “A computer is an electronic device, operating under the control of instructions.

© Paradigm Publishing, Inc. 2-1 Chapter 2 Input and Processing Chapter 2 Input and Processing.

Introduction to Information Technology: Your Digital World © 2013 The McGraw-Hill Companies, Inc. All rights reserved.Using Information Technology, 10e©
Professor Michael J. Losacco CIS 1110 – Using Computers System Unit Chapter 4.

Objectives Overview Discovering Computers 2014: Chapter 6 See Page 248

Computer Parts There are many parts that work together to make a computer work.

Parts of a Computer.

Computers Are Your Future Eleventh Edition Chapter 2: Inside the System Unit Copyright © 2011 Pearson Education, Inc. Publishing as Prentice Hall1.

COMPONENTS OF A PERSONAL COMPUTER.
COMPUTER SYSTEM.

S3 Computer Literacy Computer Hardware. Overview of Computer Hardware Motherboard CPU RAM Harddisk CD-ROM Floppy Disk Display Card Sound Card LAN Card.

COMPONENTS OF THE SYSTEM UNIT

Computer Systems 1 Fundamentals of Computing

Chasis / System cabinet A plastic enclosure that contains most of the components of a computer (usually excluding the display, keyboard and mouse)

The Internal Components of a Personal Computer (PC)

Chapter 6 Inside Computers and Mobile Devices Discovering Computers Technology in a World of Computers, Mobile Devices, and the Internet.

Your Interactive Guide to the Digital World Discovering Computers 2012.

Memory Hierarchy.

Introduction to Computers Personal Computing 10. What is a computer? Electronic device Performs instructions in a program Performs four functions –Accepts.
About project
© 2024 SlidePlayer.com Inc. All rights reserved.
- Preferences

Computer parts - PowerPoint PPT Presentation

Computer parts
All about computer parts and types – powerpoint ppt presentation.
- this looks like a TV and lets you sees the software/programed and everything you do on your computer.
- this is the main part of the computer. It contains the brain of the computer which processes and communicates information with all other parts of the computer.
- the keyboard is an input device used to type in information into the computer.
- the mouse is an input device which is used to control what you see on your monitor. With a mouse you can click, select and move what you see on your screen.
- this is an output device used to print out hard copy of what is displayed on your monitor. You can use it to print text and pictures.
- is any part of your computer that has a physical structure, such as the computer monitor or keyboard.
- is any set of instructions that tells the hardware what to do. It is what guides the hardware and tells it how to accomplish each task. Some examples of software are web browsers, games, and word processors such as Microsoft Word.
PowerShow.com is a leading presentation sharing website. It has millions of presentations already uploaded and available with 1,000s more being uploaded by its users every day. Whatever your area of interest, here you’ll be able to find and view presentations you’ll love and possibly download. And, best of all, it is completely free and easy to use.
You might even have a presentation you’d like to share with others. If so, just upload it to PowerShow.com. We’ll convert it to an HTML5 slideshow that includes all the media types you’ve already added: audio, video, music, pictures, animations and transition effects. Then you can share it with your target audience as well as PowerShow.com’s millions of monthly visitors. And, again, it’s all free.
About the Developers
PowerShow.com is brought to you by CrystalGraphics , the award-winning developer and market-leading publisher of rich-media enhancement products for presentations. Our product offerings include millions of PowerPoint templates, diagrams, animated 3D characters and more.

Home Collections Geometry Computer Infographics Components Of A Computer System Ppt
Components of a Computer System PPT and Google Slides
Components of a Computer System
Features of the template:.
- The slide are 100% customizable.
- The slide is contained in 16:9 and 4:3 formats.
- Highly compatible with PowerPoint and Google Slides.
- Easy to change the slide's colors.
- This slide has a colorful design pattern.
- Computer Infographics
- Circle Diagrams
- Component of Computer System
- Computer Fundamedals
- Basics Of Computer
- Computer Design
- Computer Frame
- Computer Technology
- Computer Screen
- Computer System
- Four Options
- Google Slides
441+ Templates

Non Circular
148+ Templates

303+ Templates
75+ Templates
51+ Templates
67+ Templates
275+ Templates

186+ Templates
46+ Templates

20+ Templates
You May Also Like These PowerPoint Templates

Pete’s PowerPoint Station
- Science Index
- Math/Maths Index
- Language Arts/Literature Index
- Social Studies Index
- Holidays Index
- Art, Music, and Many More, A-Z
- Meteorology
- Four Seasons
- Pre-Algebra
- Trigonometry
- Pre-Calculus & Calculus
- Language Arts
- Punctuation
- Social Studies
- World Religions
- US Government
- Criminal Justice
- Famous People
- American History
- World History
- Ancient History
- The Middle Ages
- Architecture
- All Topics, A–Z
- Privacy & Cookie Policy
- Presentations
Parts of a Computer
Free Presentations in PowerPoint format
Mr. Computer - Basic Parts of a Computer
Parts of a Computer (HS)
See Also: Keyboarding
Computer Technology
For Teachers
Computer Lesson Plans
Free Games Downloads for Using Computers
Free Clipart
Free Templates

- Computer Hardware Components
- Popular Categories
Powerpoint Templates
Icon Bundle
Kpi Dashboard
Professional
Business Plans
Swot Analysis
Gantt Chart
Business Proposal
Marketing Plan
Project Management
Business Case
Business Model
Cyber Security
Business PPT
Digital Marketing
Digital Transformation
Human Resources
Product Management
Artificial Intelligence
Company Profile
Acknowledgement PPT
PPT Presentation
Reports Brochures
One Page Pitch
Interview PPT
All Categories
Powerpoint Templates and Google slides for Computer Hardware Components
Save your time and attract your audience with our fully editable ppt templates and slides..
Item 1 to 60 of 105 total items
- You're currently reading page 1

Enthrall your audience with this Confidential Computing Hardware Powerpoint Presentation Slides. Increase your presentation threshold by deploying this well-crafted template. It acts as a great communication tool due to its well-researched content. It also contains stylized icons, graphics, visuals etc, which make it an immediate attention-grabber. Comprising eighty three slides, this complete deck is all you need to get noticed. All the slides and their content can be altered to suit your unique business setting. Not only that, other components and graphics can also be modified to add personal touches to this prefabricated set.
This slide represents the performance tracking dashboard for confidential computing. The purpose of this slide is to represent the overall performance of the confidential computing cloud environment visually. The main components include overall health, operations, progress, time, cost and workloads. Deliver an outstanding presentation on the topic using this Confidential Computing Hardware Confidential Computing Performance Tracking Dashboard. Dispense information and present a thorough explanation of Performance Tracking Dashboard, Confidential Computing, Cloud Environment Visually, Cost And Workloads using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
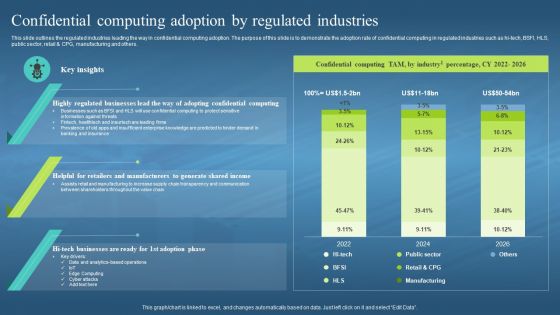
This slide outlines the regulated industries leading the way in confidential computing adoption. The purpose of this slide is to demonstrate the adoption rate of confidential computing in regulated industries such as hi-tech, BSFI, HLS, public sector, retail and CPG, manufacturing and others. Present the topic in a bit more detail with this Confidential Computing Adoption By Regulated Industries Confidential Computing Hardware. Use it as a tool for discussion and navigation on Confidential Computing Adoption, Demonstrate The Adoption Rate, Public Sector, Retail And CPG. This template is free to edit as deemed fit for your organization. Therefore download it now.
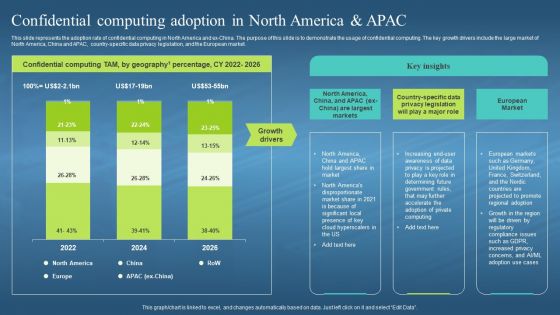
This slide represents the adoption rate of confidential computing in North America and ex-China. The purpose of this slide is to demonstrate the usage of confidential computing. The key growth drivers include the large market of North America, China and APAC, country-specific data privacy legislation, and the European market. Deliver an outstanding presentation on the topic using this Confidential Computing Adoption In North America Confidential Computing Hardware. Dispense information and present a thorough explanation of Adoption Rate, Confidential Computing, Demonstrate, Growth Drivers, Specific Data Privacy Legislation, European Market using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
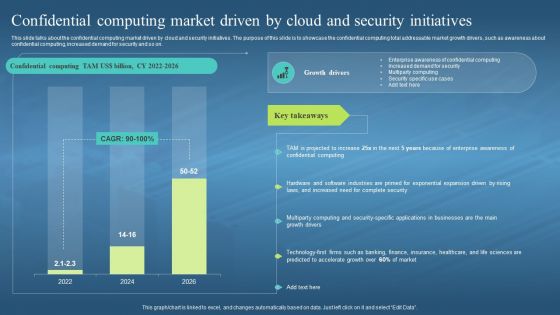
This slide talks about the confidential computing market driven by cloud and security initiatives. The purpose of this slide is to showcase the confidential computing total addressable market growth drivers, such as awareness about confidential computing, increased demand for security and so on. Deliver an outstanding presentation on the topic using this Confidential Computing Market Driven By Cloud And Security Confidential Computing Hardware. Dispense information and present a thorough explanation of Confidential Computing, Market Driven By Cloud, Security Initiatives, Awareness About Confidential Computing, Demand For Security using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
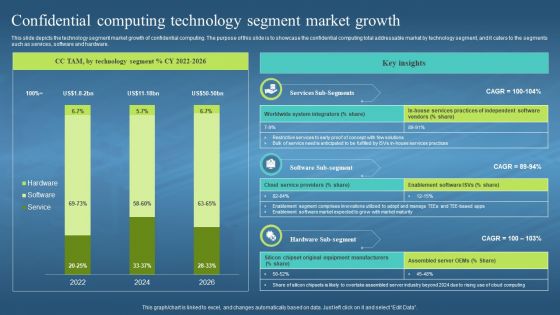
This slide depicts the technology segment market growth of confidential computing. The purpose of this slide is to showcase the confidential computing total addressable market by technology segment, and it caters to the segments such as services, software and hardware. Present the topic in a bit more detail with this Confidential Computing Technology Segment Market Confidential Computing Hardware. Use it as a tool for discussion and navigation on Technology Segment, Market Growth, Confidential Computing, Software And Hardware. This template is free to edit as deemed fit for your organization. Therefore download it now.

This slide outlines the overview of the confidential computing total addressable market. The purpose of this slide is to demonstrate the best, median and worst-case scenarios of the TAM market for the next five years. In the best case scenario, the market is expected to increase by ninety-five percent by 2026. Present the topic in a bit more detail with this Confidential Computing Total Addressable Market Confidential Computing Hardware. Use it as a tool for discussion and navigation on Confidential Computing, Addressable Market, Demonstrate The Best, Cloud Computing. This template is free to edit as deemed fit for your organization. Therefore download it now.
Increase audience engagement and knowledge by dispensing information using Table Of Contents Confidential Computing Hardware Ppt Icon File Formats. This template helps you present information on six stages. You can also present information on Importance Of Confidential Computing, Confidential Computing Overview, Architecture, Working And Approaches Of Confidential Computing using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.

This slide showcases major characteristics of edge computing hardware, enabling developers and industrialists to use this technology in careful manner. It provides details about vent, fan, shock, temperature, small form, storage, etc. Increase audience engagement and knowledge by dispensing information using Edge Computing Technology Key Characteristics Of Edge Computing Hardware AI SS. This template helps you present information on five stages. You can also present information on Impervious To Sudden Movements, Equipped With Ample Storage, Fan Less And Ventless using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
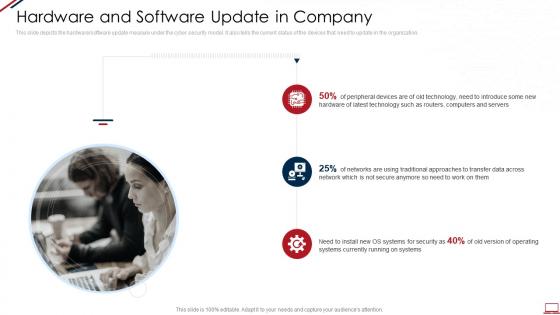
This slide depicts the hardware or software update measure under the cyber security model. It also tells the current status of the devices that need to update in the organization. Introducing Computer System Security Hardware And Software Update In Company to increase your presentation threshold. Encompassed with three stages, this template is a great option to educate and entice your audience. Dispence information on Technology, Security, Servers, using this template. Grab it now to reap its full benefits.
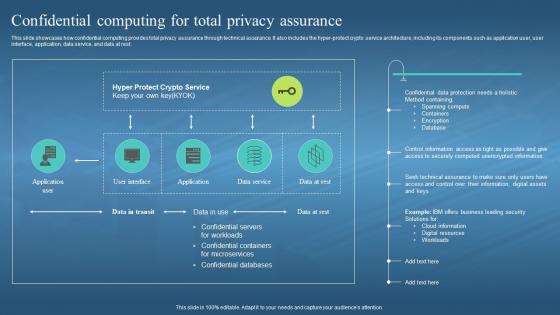
This slide showcases how confidential computing provides total privacy assurance through technical assurance. It also includes the hyper-protect crypto service architecture, including its components such as application user, user interface, application, data service, and data at rest. Present the topic in a bit more detail with this Confidential Computing Hardware Confidential Computing For Total Privacy Assurance. Use it as a tool for discussion and navigation on Spanning Compute, Containers, Encryption, Cloud Information, Digital Resources. This template is free to edit as deemed fit for your organization. Therefore download it now.
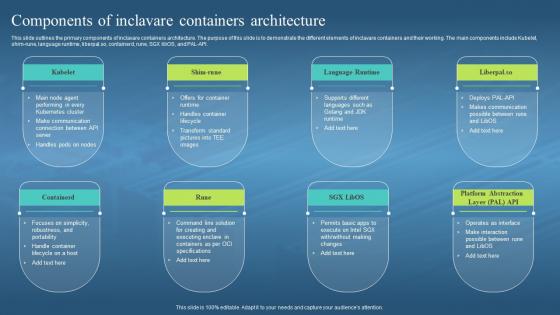
This slide outlines the primary components of inclavare containers architecture. The purpose of this slide is to demonstrate the different elements of inclavare containers and their working. The main components include Kubelet, shim-rune, language runtime, liberpal.so, containerd, rune, SGX libOS, and PAL-API. Increase audience engagement and knowledge by dispensing information using Confidential Computing Hardware Components Of Inclavare Containers Architecture. This template helps you present information on eight stages. You can also present information on Inclavare Containers Architecture, Demonstrate, Language Runtime, Handle Container Lifecycle using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
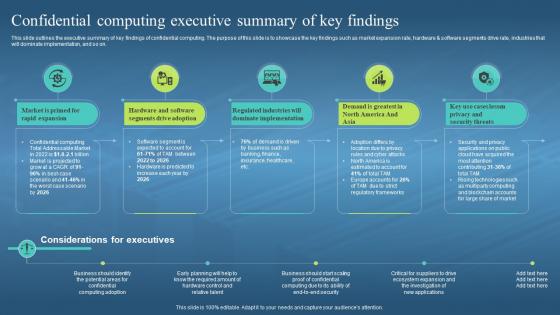
This slide outlines the executive summary of key findings of confidential computing. The purpose of this slide is to showcase the key findings such as market expansion rate, hardware and software segments drive rate, industries that will dominate implementation, and so on. Introducing Confidential Computing Hardware Confidential Computing Executive Summary Of Key Findings to increase your presentation threshold. Encompassed with five stages, this template is a great option to educate and entice your audience. Dispence information on Confidential Computing, Market Expansion Rate, Hardware And Software Segments, Dominate Implementation, using this template. Grab it now to reap its full benefits.
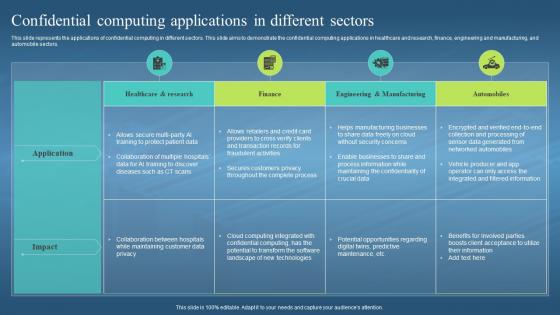
This slide represents the applications of confidential computing in different sectors. This slide aims to demonstrate the confidential computing applications in healthcare and research, finance, engineering and manufacturing, and automobile sectors. Present the topic in a bit more detail with this Confidential Computing Hardware Confidential Computing Applications In Different Sectors. Use it as a tool for discussion and navigation on Confidential Computing, Demonstrate, Healthcare And Research, Finance, Engineering And Manufacturing, Automobile Sectors. This template is free to edit as deemed fit for your organization. Therefore download it now.
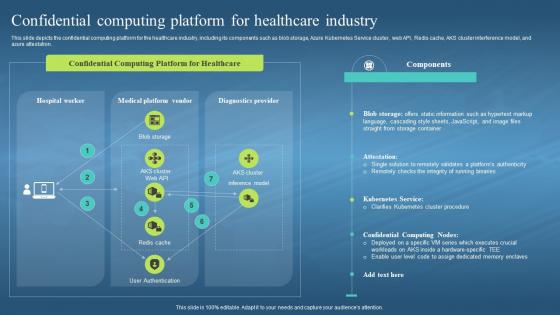
This slide depicts the confidential computing platform for the healthcare industry, including its components such as blob storage, Azure Kubernetes Service cluster, web API, Redis cache, AKS cluster interference model, and azure attestation. Present the topic in a bit more detail with this Confidential Computing Hardware Confidential Computing Platform For Healthcare Industry. Use it as a tool for discussion and navigation on Confidential Computing Platform, Healthcare Industry, Azure Kubernetes Service Cluster, Aks Cluster Interference Model. This template is free to edit as deemed fit for your organization. Therefore download it now.
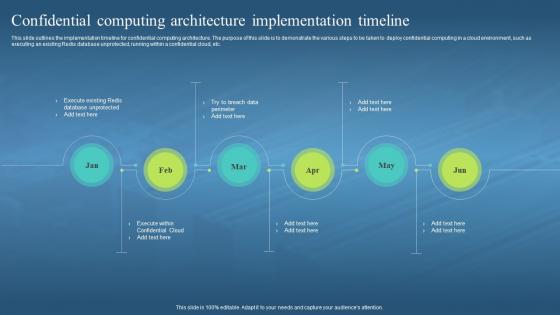
This slide outlines the implementation timeline for confidential computing architecture. The purpose of this slide is to demonstrate the various steps to be taken to deploy confidential computing in a cloud environment, such as executing an existing Redis database unprotected, running within a confidential cloud, etc. Increase audience engagement and knowledge by dispensing information using Confidential Computing Hardware Confidential Computing Architecture Implementation Timeline. This template helps you present information on six stages. You can also present information on Implementation Timeline, Confidential Computing Architecture, Deploy Confidential Computing, Cloud Environment, Existing Redis Database Unprotected using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
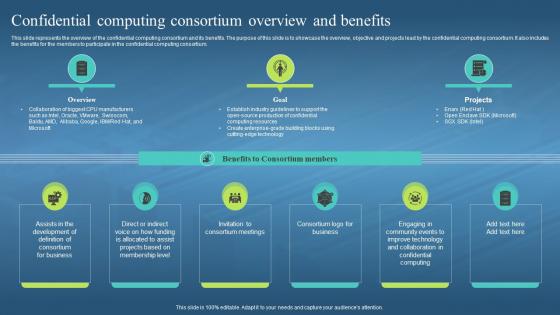
This slide represents the overview of the confidential computing consortium and its benefits. The purpose of this slide is to showcase the overview, objective and projects lead by the confidential computing consortium. It also includes the benefits for the members to participate in the confidential computing consortium. Increase audience engagement and knowledge by dispensing information using Confidential Computing Hardware Confidential Computing Consortium Overview And Benefits. This template helps you present information on three stages. You can also present information on Consortium Meetings, Engaging In Community Events, Technology And Collaboration, Confidential Computing using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.

Introducing Agenda Confidential Computing Hardware Ppt Ideas Infographic Template to increase your presentation threshold. Encompassed with five stages, this template is a great option to educate and entice your audience. Dispence information on Consortium, Architecture, Confidential Computing, Hardware And Technologies, Computing Environment, using this template. Grab it now to reap its full benefits.
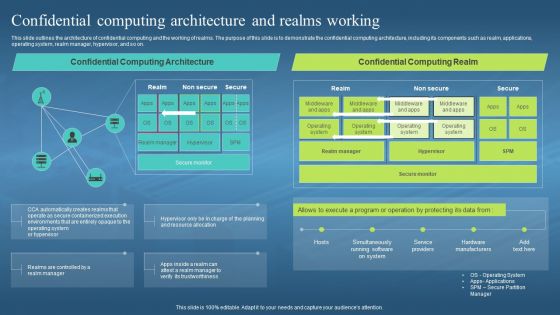
This slide outlines the architecture of confidential computing and the working of realms. The purpose of this slide is to demonstrate the confidential computing architecture, including its components such as realm, applications, operating system, realm manager, hypervisor, and so on. Present the topic in a bit more detail with this Confidential Computing Architecture And Realms Working Confidential Computing Hardware. Use it as a tool for discussion and navigation on Architecture Of Confidential Computing, Working Of Realms, Demonstrate, Operating System, Realm Manager, Hypervisor. This template is free to edit as deemed fit for your organization. Therefore download it now.
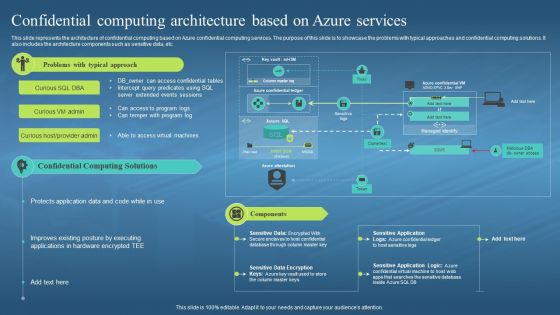
This slide represents the architecture of confidential computing based on Azure confidential computing services. The purpose of this slide is to showcase the problems with typical approaches and confidential computing solutions. It also includes the architecture components such as sensitive data, etc. Present the topic in a bit more detail with this Confidential Computing Architecture Based On Azure Services Confidential Computing Hardware. Use it as a tool for discussion and navigation on Architecture Of Confidential Computing, Azure Confidential Computing Services, Typical Approaches, Sensitive Data. This template is free to edit as deemed fit for your organization. Therefore download it now.
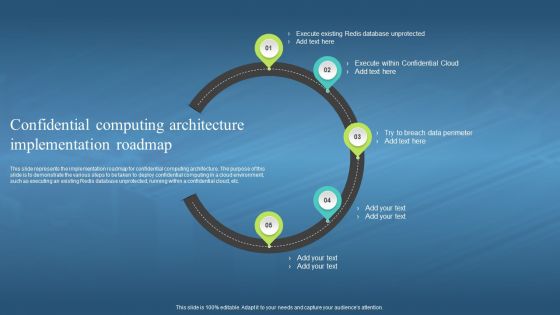
This slide represents the implementation roadmap for confidential computing architecture. The purpose of this slide is to demonstrate the various steps to be taken to deploy confidential computing in a cloud environment, such as executing an existing Redis database unprotected, running within a confidential cloud, etc. Introducing Confidential Computing Architecture Implementation Roadmap Confidential Computing Hardware to increase your presentation threshold. Encompassed with five stages, this template is a great option to educate and entice your audience. Dispence information on Implementation Roadmap, Confidential Computing Architecture, Demonstrate, Deploy Confidential Computing, Cloud Environment, Existing Redis Database Unprotected, using this template. Grab it now to reap its full benefits.
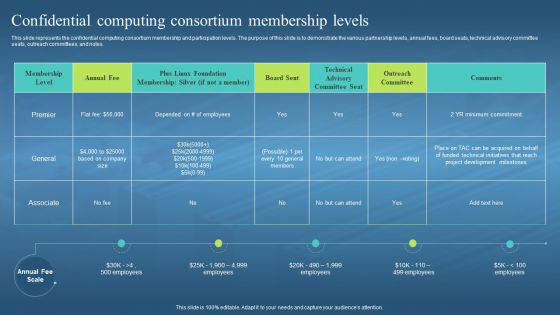
This slide represents the confidential computing consortium membership and participation levels. The purpose of this slide is to demonstrate the various partnership levels, annual fees, board seats, technical advisory committee seats, outreach committees, and notes. Deliver an outstanding presentation on the topic using this Confidential Computing Consortium Membership Levels Confidential Computing Hardware. Dispense information and present a thorough explanation of Confidential Computing, Consortium Membership, Participation Levels, Technical Advisory Committee Seats, Outreach Committees using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
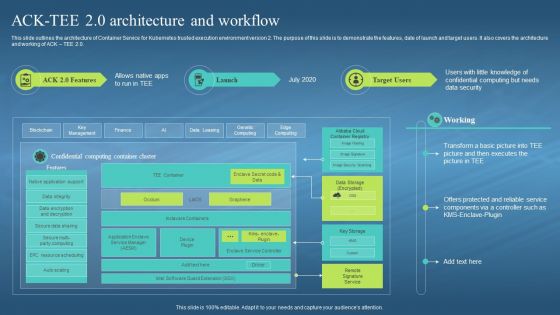
This slide outlines the architecture of Container Service for Kubernetes trusted execution environment version 2. The purpose of this slide is to demonstrate the features, date of launch and target users. It also covers the architecture and working of ACK TEE 2.0. Deliver an outstanding presentation on the topic using this Confidential Computing Hardware Ack Tee 2 0 Architecture And Workflow. Dispense information and present a thorough explanation of Architecture Of Container Service, Kubernetes Trusted, Execution Environment Version, Data Security using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
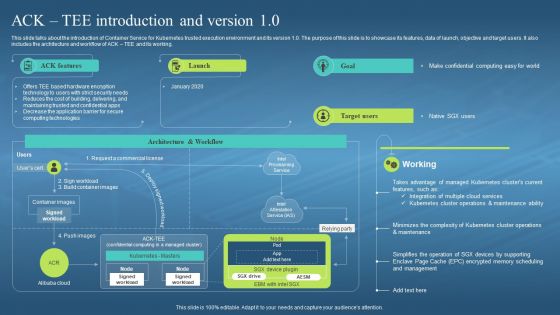
This slide talks about the introduction of Container Service for Kubernetes trusted execution environment and its version 1.0. The purpose of this slide is to showcase its features, data of launch, objective and target users. It also includes the architecture and workflow of ACK TEE and its working. Present the topic in a bit more detail with this Confidential Computing Hardware Ack Tee Introduction And Version 1 0. Use it as a tool for discussion and navigation on Hardware Encryption Technology, Strict Security Needs, Delivering And Maintaining Trusted, Confidential Apps, Computing Technologies. This template is free to edit as deemed fit for your organization. Therefore download it now.
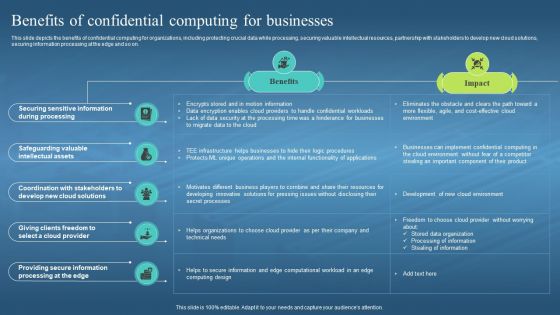
This slide depicts the benefits of confidential computing for organizations, including protecting crucial data while processing, securing valuable intellectual resources, partnership with stakeholders to develop new cloud solutions, securing information processing at the edge and so on. Deliver an outstanding presentation on the topic using this Confidential Computing Hardware Benefits Of Confidential Computing For Businesses. Dispense information and present a thorough explanation of Confidential Computing For Organizations, Protecting Crucial Data, Securing Valuable Intellectual Resources, New Cloud Solutions using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
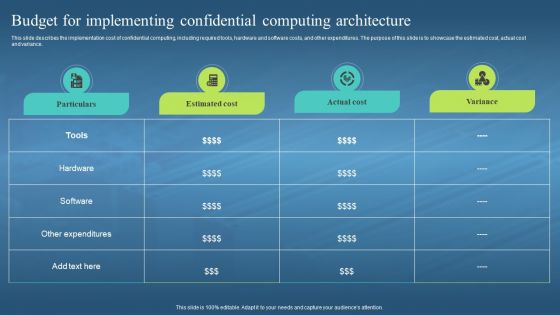
This slide describes the implementation cost of confidential computing, including required tools, hardware and software costs, and other expenditures. The purpose of this slide is to showcase the estimated cost, actual cost and variance. Present the topic in a bit more detail with this Confidential Computing Hardware Budget For Implementing Confidential Computing. Use it as a tool for discussion and navigation on Cost Of Confidential Computing, Hardware And Software Costs, Estimated Cost, Actual Cost And Variance. This template is free to edit as deemed fit for your organization. Therefore download it now.

This slide represents the business scenarios of confidential computing platform and it includes blockchain, key management, finance, artificial intelligence, multi-party computing, data leasing, and edge computing. Organizations can use confidential computing to secure their data while generating high economic value. Increase audience engagement and knowledge by dispensing information using Confidential Computing Hardware Business Scenarios Of Confidential Computing Platform. This template helps you present information on seven stages. You can also present information on Blockchain, Key Management, Finance, Edge Computing, Data Leasing using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
This slide talks about the case study carried out at Irene Energy organization. The purpose of this slide is to demonstrate how this corporation uses confidential computing technologies to provide electricity to remote American areas. The case study includes issues experienced, objectives, provided solutions and impact. Deliver an outstanding presentation on the topic using this Confidential Computing Hardware Case Study Irene Energy Ppt Icon Guidelines. Dispense information and present a thorough explanation of Irene Energy Organization, Demonstrate, Confidential Computing Technologies, Electricity To Remote American Areas, Electricity Roaming using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
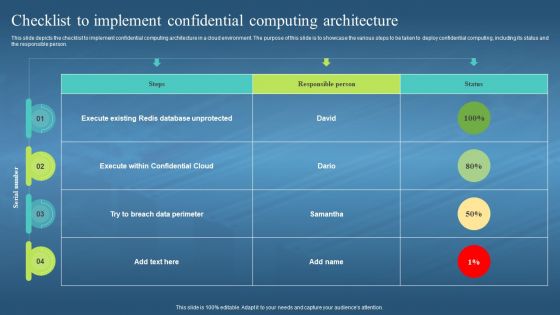
This slide depicts the checklist to implement confidential computing architecture in a cloud environment. The purpose of this slide is to showcase the various steps to be taken to deploy confidential computing, including its status and the responsible person. Present the topic in a bit more detail with this Confidential Computing Hardware Checklist To Implement Confidential Computing. Use it as a tool for discussion and navigation on Execute Within Confidential Cloud, Confidential Computing Architecture, Cloud Environment. Deploy Confidential Computing. This template is free to edit as deemed fit for your organization. Therefore download it now.
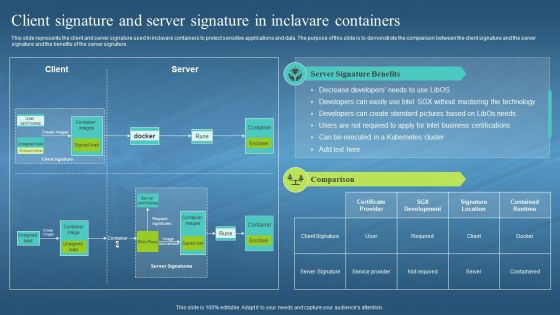
This slide represents the client and server signature used in inclavare containers to protect sensitive applications and data. The purpose of this slide is to demonstrate the comparison between the client signature and the server signature and the benefits of the server signature. Deliver an outstanding presentation on the topic using this Confidential Computing Hardware Client Signature And Server Signature In Inclavare. Dispense information and present a thorough explanation of Client And Server Signature, Inclavare Containers, Protect Sensitive Applications, Demonstrate, Intel Business Certifications using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.

This slide represents the top companies leading the way for confidential computing. The purpose of this slide is to showcase the leading companies adopting confidential computing to protect organizational and customer information in cloud environments. Top companies include IBM, Google, Microsoft, etc. Introducing Confidential Computing Hardware Companies Paving The Path For Confidential Computing to increase your presentation threshold. Encompassed with four stages, this template is a great option to educate and entice your audience. Dispence information on Confidential Computing, Cloud Environments, Cloud Platform, Hardware And Software Solutions, using this template. Grab it now to reap its full benefits.
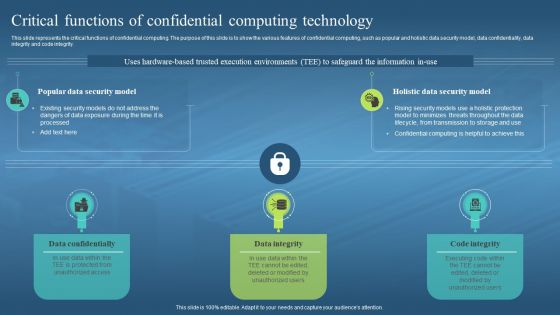
This slide represents the critical functions of confidential computing. The purpose of this slide is to show the various features of confidential computing, such as popular and holistic data security model, data confidentiality, data integrity and code integrity. Increase audience engagement and knowledge by dispensing information using Confidential Computing Hardware Critical Functions Of Confidential Computing Technology. This template helps you present information on three stages. You can also present information on Data Confidentially, Data Integrity, Code Integrity, Confidential Computing Technology using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
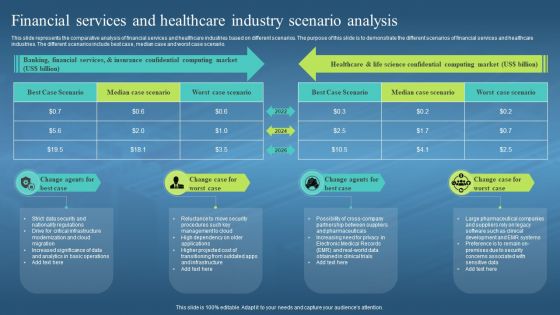
This slide represents the comparative analysis of financial services and healthcare industries based on different scenarios. The purpose of this slide is to demonstrate the different scenarios of financial services and healthcare industries. The different scenarios include best case, median case and worst case scenario. Introducing Confidential Computing Hardware Financial Services And Healthcare Industry Scenario to increase your presentation threshold. Encompassed with four stages, this template is a great option to educate and entice your audience. Dispence information on Banking, Financial Services, Insurance Confidential Computing Market, using this template. Grab it now to reap its full benefits.
Present the topic in a bit more detail with this Confidential Computing Hardware For Table Of Contents Ppt Icon Designs Download. Use it as a tool for discussion and navigation on Confidential Computing Market, Technology Segment Market Growth, Scenario Case Analysis. This template is free to edit as deemed fit for your organization. Therefore download it now.
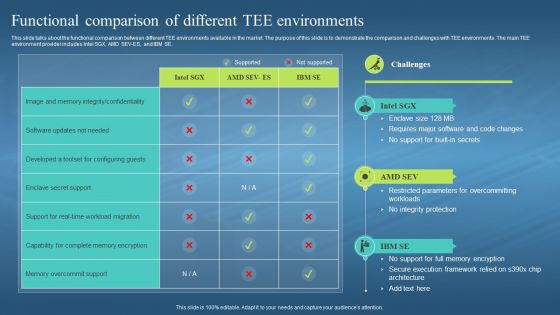
This slide talks about the functional comparison between different TEE environments available in the market. The purpose of this slide is to demonstrate the comparison and challenges with TEE environments. The main TEE environment provider includes Intel SGX, AMD SEV-ES, and IBM SE. Deliver an outstanding presentation on the topic using this Confidential Computing Hardware Functional Comparison Of Different Tee Environments. Dispense information and present a thorough explanation of Functional Comparison, Tee Environments, Restricted Parameters, Secure Execution Framework using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.

This slide represents the future of confidential computing technology. The purpose of this slide is to demonstrate the state of confidential computing in the coming years. It also includes how it will protect sensitive data from malicious attacks in the cloud environment. Increase audience engagement and knowledge by dispensing information using Confidential Computing Hardware Future Of Confidential Computing Technology. This template helps you present information on five stages. You can also present information on Confidential Computing Technology, Demonstrate, Cloud Environment, Prerequisite For Commercial Sectors using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
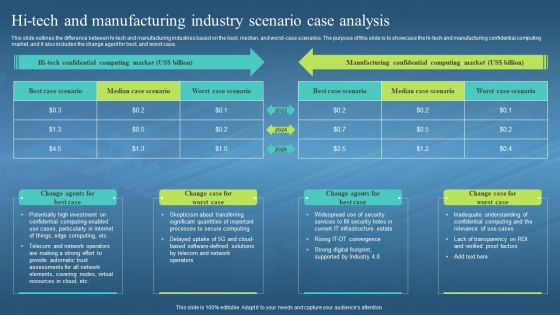
This slide outlines the difference between hi-tech and manufacturing industries based on the best, median, and worst-case scenarios. The purpose of this slide is to showcase the hi-tech and manufacturing confidential computing market, and it also includes the change agent for best, and worst case. Introducing Confidential Computing Hardware HI Tech And Manufacturing Industry Scenario Case Analysis to increase your presentation threshold. Encompassed with four stages, this template is a great option to educate and entice your audience. Dispence information on HI Tech And Manufacturing Industries, Worst Case Scenarios, It Infrastructure Estate, using this template. Grab it now to reap its full benefits.

This slide represents the in-scope and out-of-scope threat for confidential computing. The purpose of this slide is to showcase the threats that confidential computing handles, such as software, protocol, cryptographic and physical attacks. It also caters to the out of scope threats such as sophisticated physical and upstream hardware supply-chain attacks. Increase audience engagement and knowledge by dispensing information using Confidential Computing Hardware In And Out Scope Threat Vectors For Confidential Computing. This template helps you present information on four stages. You can also present information on Software Attacks, Protocol Attacks, Cryptographic Attacks, Physical Attacks using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
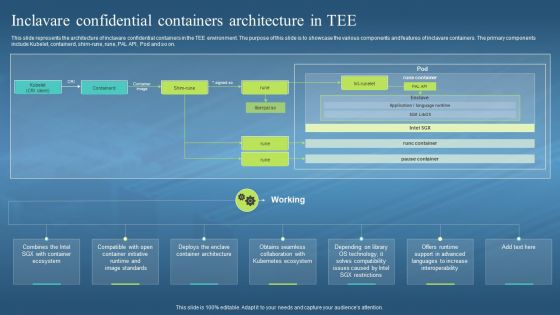
This slide represents the architecture of inclavare confidential containers in the TEE environment. The purpose of this slide is to showcase the various components and features of inclavare containers. The primary components include Kubelet, containerd, shim-rune, rune, PAL API, Pod and so on. Introducing Confidential Computing Hardware Inclavare Confidential Containers Architecture In Tee to increase your presentation threshold. Encompassed with seven stages, this template is a great option to educate and entice your audience. Dispence information on Architecture Of Inclavare, Confidential Containers, Tee Environment, Kubernetes Ecosystem, using this template. Grab it now to reap its full benefits.
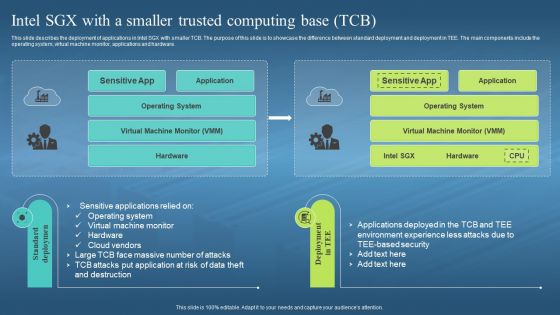
This slide describes the deployment of applications in Intel SGX with smaller TCB. The purpose of this slide is to showcase the difference between standard deployment and deployment in TEE. The main components include the operating system, virtual machine monitor, applications and hardware. Increase audience engagement and knowledge by dispensing information using Confidential Computing Hardware Intel SGX With A Smaller Trusted Computing Base TCB. This template helps you present information on two stages. You can also present information on Operating System, Virtual Machine Monitor, Hardware, Cloud Vendors using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
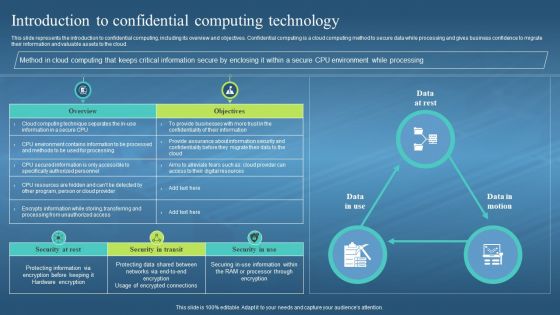
This slide represents the introduction to confidential computing, including its overview and objectives. Confidential computing is a cloud computing method to secure data while processing and gives business confidence to migrate their information and valuable assets to the cloud. Present the topic in a bit more detail with this Confidential Computing Hardware Introduction To Confidential Computing Technology. Use it as a tool for discussion and navigation on Confidential Computing, Cloud Computing Method, CPU Environment While Processing. This template is free to edit as deemed fit for your organization. Therefore download it now.

This slide depicts the key features of confidential computing platform, including confidential virtual machines, confidential space, confidential dataproc, and confidential Google Kubernetes Engine node. Increase audience engagement and knowledge by dispensing information using Confidential Computing Hardware Key Features Of Confidential Computing Platform. This template helps you present information on four stages. You can also present information on Confidential Computing Platform, Confidential Virtual Machines, Confidential Space, Confidential Google Kubernetes Engine Node using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
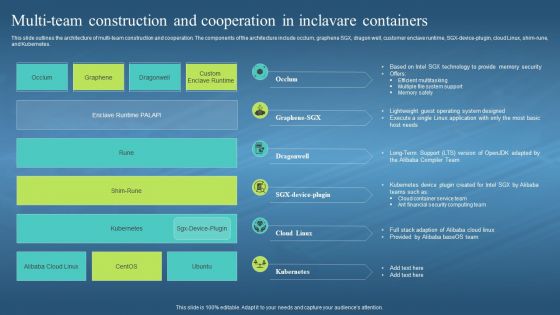
This slide outlines the architecture of multi-team construction and cooperation. The components of the architecture include occlum, graphene SGX, dragon well, customer enclave runtime, SGX-device-plugin, cloud Linux, shim-rune, and Kubernetes. Deliver an outstanding presentation on the topic using this Confidential Computing Hardware Multi Team Construction And Cooperation In Inclavare. Dispense information and present a thorough explanation of Efficient Multitasking, Multiple File System Support, Memory Safety, Cloud Container Service Team using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
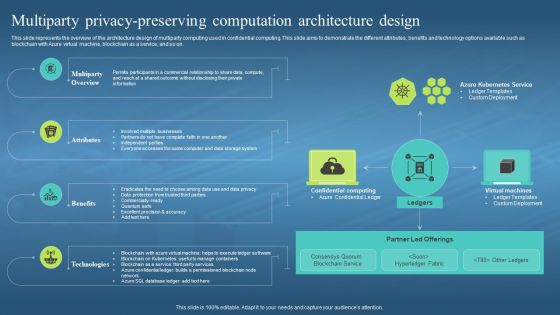
This slide represents the overview of the architecture design of multiparty computing used in confidential computing. This slide aims to demonstrate the different attributes, benefits and technology options available such as blockchain with Azure virtual machine, blockchain as a service, and so on. Introducing Confidential Computing Hardware Multiparty Privacy Preserving Computation Architecture to increase your presentation threshold. Encompassed with four stages, this template is a great option to educate and entice your audience. Dispence information on Architecture Design, Multiparty Computing, Confidential Computing, Blockchain With Azure Virtual Machine, Blockchain As A Service, using this template. Grab it now to reap its full benefits.
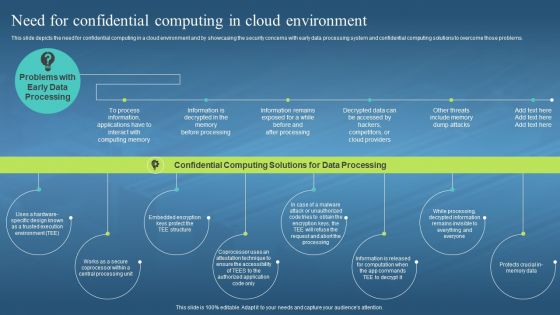
This slide depicts the need for confidential computing in a cloud environment and by showcasing the security concerns with early data processing system and confidential computing solutions to overcome those problems. Increase audience engagement and knowledge by dispensing information using Confidential Computing Hardware Need For Confidential Computing In Cloud Environment. This template helps you present information on six stages. You can also present information on Computing Memory, Competitors Or Cloud Providers, Memory Dump Attacks, Cloud Environment using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
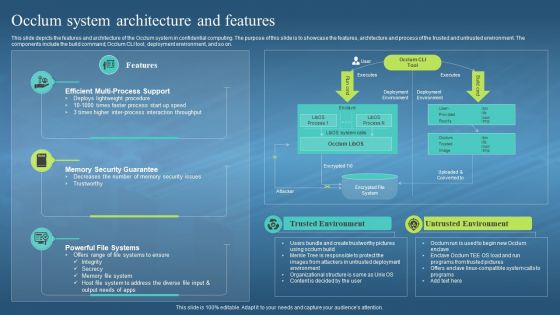
This slide depicts the features and architecture of the Occlum system in confidential computing. The purpose of this slide is to showcase the features, architecture and process of the trusted and untrusted environment. The components include the build command, Occlum CLI tool, deployment environment, and so on. Introducing Confidential Computing Hardware Occlum System Architecture And Features to increase your presentation threshold. Encompassed with two stages, this template is a great option to educate and entice your audience. Dispence information on Trusted Environment, Efficient Multi Process Support, Memory Security Guarantee, using this template. Grab it now to reap its full benefits.
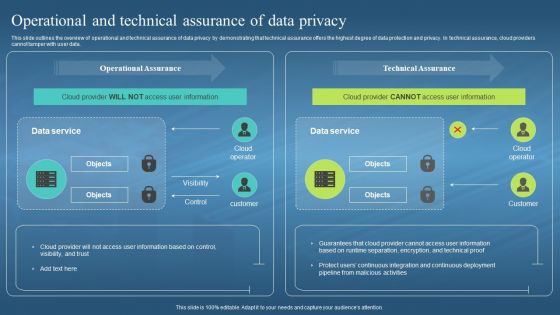
This slide outlines the overview of operational and technical assurance of data privacy by demonstrating that technical assurance offers the highest degree of data protection and privacy. In technical assurance, cloud providers cannot tamper with user data. Present the topic in a bit more detail with this Confidential Computing Hardware Operational And Technical Assurance Of Data Privacy. Use it as a tool for discussion and navigation on Operational Assurance, Technical Assurance, Data Privacy, Integration And Continuous Deployment. This template is free to edit as deemed fit for your organization. Therefore download it now.
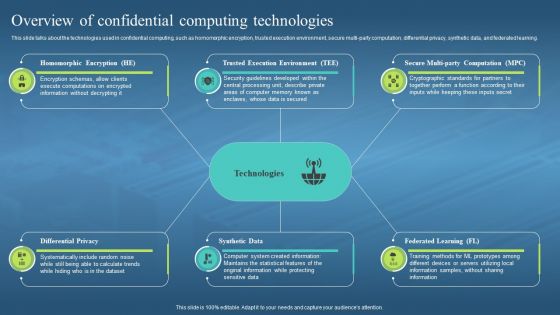
This slide talks about the technologies used in confidential computing, such as homomorphic encryption, trusted execution environment, secure multi-party computation, differential privacy, synthetic data, and federated learning. Increase audience engagement and knowledge by dispensing information using Confidential Computing Hardware Overview Of Confidential Computing Technologies. This template helps you present information on six stages. You can also present information on Homomorphic Encryption, Trusted Execution Environment, Federated Learning, Synthetic Data using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
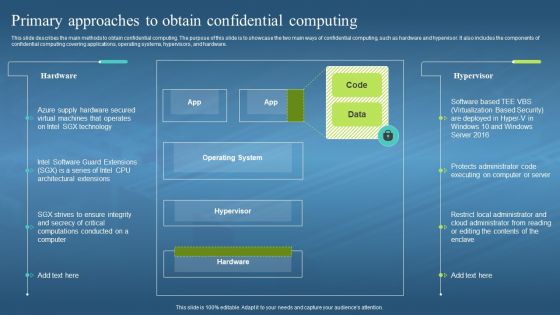
This slide describes the main methods to obtain confidential computing. The purpose of this slide is to showcase the two main ways of confidential computing, such as hardware and hypervisor. It also includes the components of confidential computing covering applications, operating systems, hypervisors, and hardware. Deliver an outstanding presentation on the topic using this Confidential Computing Hardware Primary Approaches To Obtain Confidential Computing. Dispense information and present a thorough explanation of Operating System, Hypervisor, Restrict Local Administrator, Cloud Administrator using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
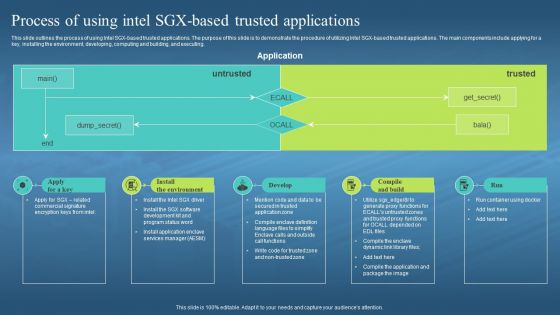
This slide outlines the process of using Intel SGX-based trusted applications. The purpose of this slide is to demonstrate the procedure of utilizing Intel SGX-based trusted applications. The main components include applying for a key, installing the environment, developing, computing and building, and executing. Introducing Confidential Computing Hardware Process Of Using Intel SGX Based Trusted Applications to increase your presentation threshold. Encompassed with five stages, this template is a great option to educate and entice your audience. Dispence information on SGX Based Trusted Applications, Installing The Environment, Developing, Computing And Building, using this template. Grab it now to reap its full benefits.
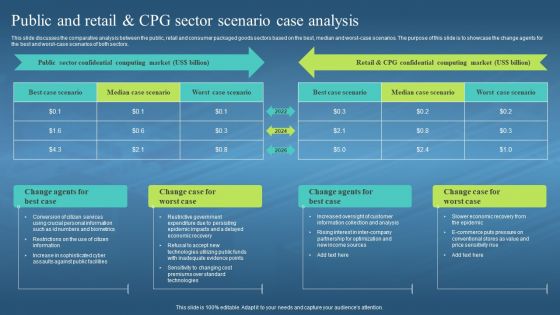
This slide discusses the comparative analysis between the public, retail and consumer packaged goods sectors based on the best, median and worst-case scenarios. The purpose of this slide is to showcase the change agents for the best and worst-case scenarios of both sectors. Increase audience engagement and knowledge by dispensing information using Confidential Computing Hardware Public And Retail And CPG Sector Scenario Case Analysis. This template helps you present information on four stages. You can also present information on Restrictive Government Expenditure, Persisting Epidemic Impacts, Delayed Economic Recovery, Technologies Utilizing Public Funds using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
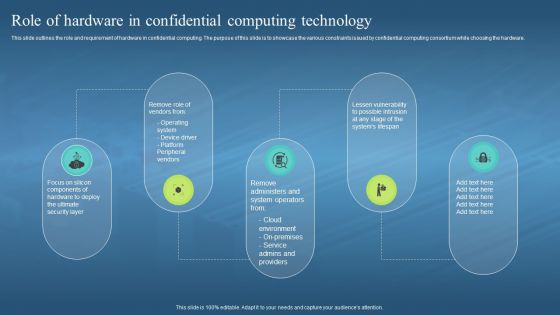
This slide outlines the role and requirement of hardware in confidential computing. The purpose of this slide is to showcase the various constraints issued by confidential computing consortium while choosing the hardware. Introducing Confidential Computing Hardware Role Of Hardware In Confidential Computing Technology to increase your presentation threshold. Encompassed with five stages, this template is a great option to educate and entice your audience. Dispence information on Cloud Environment, Service Admins And Providers, Operating System, Device Driver, Peripheral Vendors, using this template. Grab it now to reap its full benefits.
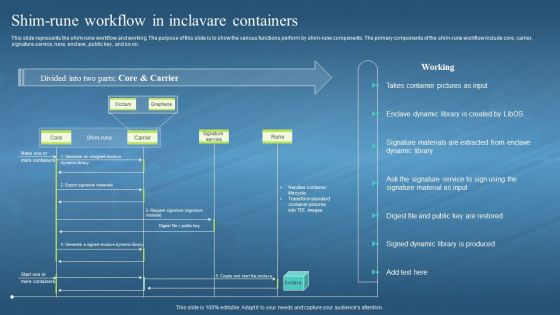
This slide represents the shim-rune workflow and working. The purpose of this slide is to show the various functions perform by shim-rune components. The primary components of the shim-rune workflow include core, carrier, signature service, rune, enclave, public key, and so on. Present the topic in a bit more detail with this Confidential Computing Hardware Shim Rune Workflow In Inclavare Containers. Use it as a tool for discussion and navigation on Shim Rune Workflow And Working, Shim Rune Components, Signature Service, Enclave Dynamic Library. This template is free to edit as deemed fit for your organization. Therefore download it now.
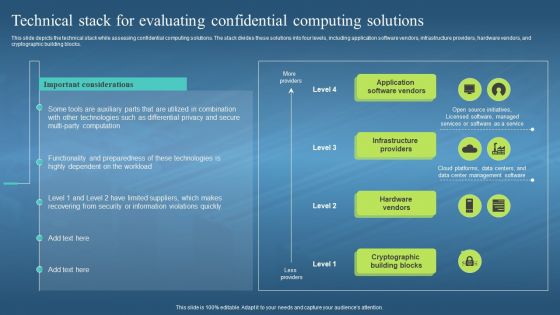
This slide depicts the technical stack while assessing confidential computing solutions. The stack divides these solutions into four levels, including application software vendors, infrastructure providers, hardware vendors, and cryptographic building blocks. Deliver an outstanding presentation on the topic using this Confidential Computing Hardware Technical Stack For Evaluating Confidential Computing. Dispense information and present a thorough explanation of Application Software Vendors, Infrastructure Providers, Hardware Vendors, Cryptographic Building Blocks using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
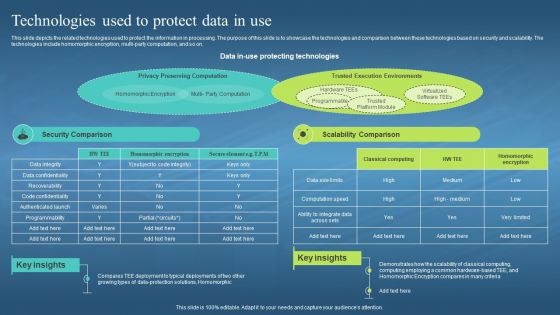
This slide depicts the related technologies used to protect the information in processing. The purpose of this slide is to showcase the technologies and comparison between these technologies based on security and scalability. The technologies include homomorphic encryption, multi-party computation, and so on. Present the topic in a bit more detail with this Confidential Computing Hardware Technologies Used To Protect Data In Use. Use it as a tool for discussion and navigation on Protect The Information In Processing, Security And Scalability, Homomorphic Encryption, Multi Party Computation. This template is free to edit as deemed fit for your organization. Therefore download it now.
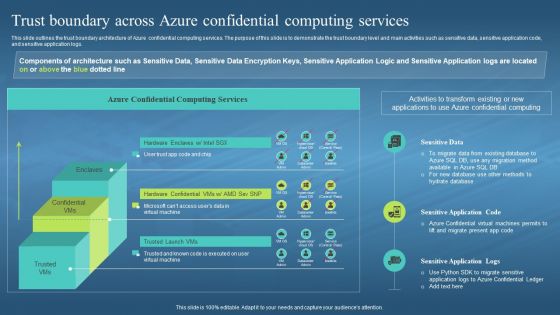
This slide outlines the trust boundary architecture of Azure confidential computing services. The purpose of this slide is to demonstrate the trust boundary level and main activities such as sensitive data, sensitive application code, and sensitive application logs. Deliver an outstanding presentation on the topic using this Confidential Computing Hardware Trust Boundary Across Azure Confidential Computing Services. Dispense information and present a thorough explanation of Trust Boundary Architecture, Azure Confidential Computing Services, Demonstrate The Trust Boundary, Sensitive Data, Sensitive Application Code using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
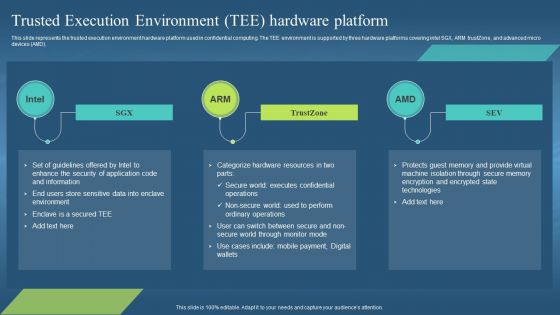
This slide represents the trusted execution environment hardware platform used in confidential computing. The TEE environment is supported by three hardware platforms covering intel SGX, ARM trustZone, and advanced micro devices AMD. Increase audience engagement and knowledge by dispensing information using Confidential Computing Hardware Trusted Execution Environment Tee Hardware Platform. This template helps you present information on three stages. You can also present information on Protects Guest Memory, Provide Virtual Machine Isolation, Secure Memory Encryption, Encrypted State Technologies using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
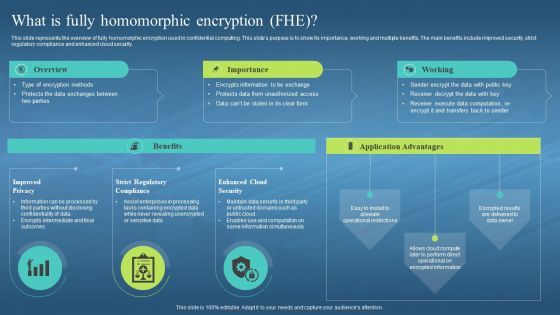
This slide represents the overview of fully homomorphic encryption used in confidential computing. This slides purpose is to show its importance, working and multiple benefits. The main benefits include improved security, strict regulatory compliance and enhanced cloud security. Introducing Confidential Computing Hardware What Is Fully Homomorphic Encryption FHE to increase your presentation threshold. Encompassed with three stages, this template is a great option to educate and entice your audience. Dispence information on Fully Homomorphic Encryption, Strict Regulatory Compliance, Enhanced Cloud Security, using this template. Grab it now to reap its full benefits.
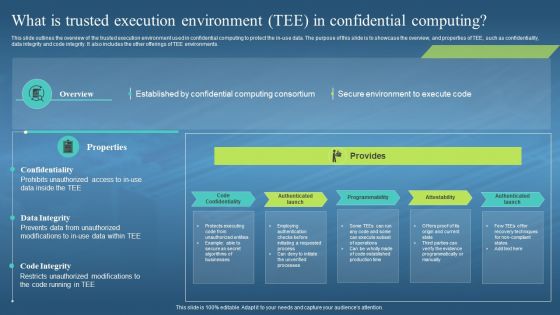
This slide outlines the overview of the trusted execution environment used in confidential computing to protect the in-use data. The purpose of this slide is to showcase the overview, and properties of TEE, such as confidentiality, data integrity and code integrity. It also includes the other offerings of TEE environments. Increase audience engagement and knowledge by dispensing information using Confidential Computing Hardware What Is Trusted Execution Environment Tee In Confidential. This template helps you present information on five stages. You can also present information on Code Confidentiality, Authenticated Launch, Programmability, Confidential Computing Consortium using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
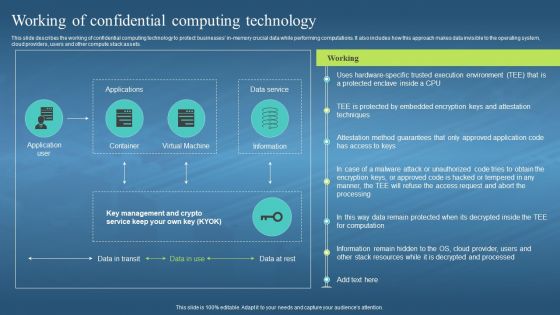
This slide describes the working of confidential computing technology to protect businesses in-memory crucial data while performing computations. It also includes how this approach makes data invisible to the operating system, cloud providers, users and other compute stack assets. Present the topic in a bit more detail with this Confidential Computing Hardware Working Of Confidential Computing Technology. Use it as a tool for discussion and navigation on Confidential Computing Technology, Protect Businesses, Performing Computations, Operating System, Cloud Providers. This template is free to edit as deemed fit for your organization. Therefore download it now.

Got any suggestions?
We want to hear from you! Send us a message and help improve Slidesgo
Top searches
Trending searches

26 templates
first day of school
69 templates
18 templates

48 templates

6 templates

great barrier reef
17 templates
Computer Presentation templates
Use these google slides themes or download our ppt files for powerpoint or keynote to give a presentation about a computer-related topic, including information technology..
It seems that you like this template!
Premium template.
Unlock this template and gain unlimited access
Linear Grid Newsletter
Give an original touch to your employee newsletters with this grid design. It perfectly combines colors like green, yellow or orange with geometric icons to give dynamism to your news. You can use a different tone for each section, so they can be easily differentiated. Report on the latest company...

How to Code Workshop
Are you an expert of Java? Yes, it's a beautiful island in Indonesia and more than half of the population of this country lives there... No! Well, yes, those facts are true, but we were talking about the programming language! We think workshops on how to code are a necessity,...

Computer Science Degree for College
Computer science degrees prepare students for the jobs of the future (and the present!). If you are interested in getting an education about coding, math, computers, and robots, this is the degree for you! Speak about it with this futuristic template that will take the viewers to another digital dimension....

Internet Academia Aesthetics School Center Infographics
Download the Internet Academia Aesthetics School Center Infographics template for PowerPoint or Google Slides and discover the power of infographics. An infographic resource gives you the ability to showcase your content in a more visual way, which will make it easier for your audience to understand your topic. Slidesgo infographics...

Computer Science College Major
If you are a guru of computers, most likely you've studied computer science in college. Would you like to show others what a major in this field has to offer and what it could contribute to their professional development? Customize this template and let them feel the future, at least...

Thesis Statement on How Nations Use Digital Espionage Infographics
Download the Thesis Statement on How Nations Use Digital Espionage Infographics template for PowerPoint or Google Slides and discover the power of infographics. An infographic resource gives you the ability to showcase your content in a more visual way, which will make it easier for your audience to understand your...

Cloud Computing Computer Science Bachelor's Degree
Download the Cloud Computing Computer Science Bachelor's Degree presentation for PowerPoint or Google Slides. The education sector constantly demands dynamic and effective ways to present information. This template is created with that very purpose in mind. Offering the best resources, it allows educators or students to efficiently manage their presentations...


Virtual Slides for Education Day
Digital learning is making its way into the world of education. For this reason, we've designed this new template so that the slides look like the screen of a laptop (complete with reflections!). Apart from graphs and infographics, the font is quite "computer-esque" and a perfect fit for this theme....
Silicon Valley Programmer Minitheme
No matter your actual profession, you can’t say you’ve never ever imagined being one of those fabled Silicon Valley programmers that make alternate realities come to life and can make us question the structures that govern our world. The good news: With this minitheme, you can join them for a...
Soft Colors UI Design for Agencies
Agencies have the most creative employees, so having boring meetings with traditional Google Slides & PowerPoint presentations would be a waste. Make the most out of this potential with this creative design full of editable resources and beautiful decorations in calming, pastel tones. Let the creativity of your agency be...

Staff Induction Onboarding
Download the Staff Induction Onboarding presentation for PowerPoint or Google Slides. The world of business encompasses a lot of things! From reports to customer profiles, from brainstorming sessions to sales—there's always something to do or something to analyze. This customizable design, available for Google Slides and PowerPoint, is what you...

Multimedia Software Pitch Deck
Download the "Multimedia Software Pitch Deck" presentation for PowerPoint or Google Slides. Whether you're an entrepreneur looking for funding or a sales professional trying to close a deal, a great pitch deck can be the difference-maker that sets you apart from the competition. Let your talent shine out thanks to...

Social Media Report
Download the Social Media Report presentation for PowerPoint or Google Slides. How do you use social media platforms to achieve your business goals? If you need a thorough and professional tool to plan and keep track of your social media strategy, this fully customizable template is your ultimate solution. It...

Port, Cables and Conectors
Download the Port, Cables and Conectors presentation for PowerPoint or Google Slides and start impressing your audience with a creative and original design. Slidesgo templates like this one here offer the possibility to convey a concept, idea or topic in a clear, concise and visual way, by using different graphic...

Retro Video Games Newsletter Infographics
Download the Retro Video Games Newsletter Infographics template for PowerPoint or Google Slides and discover the power of infographics. An infographic resource gives you the ability to showcase your content in a more visual way, which will make it easier for your audience to understand your topic. Slidesgo infographics like...

Software Development Company Profile
Download the Software Development Company Profile presentation for PowerPoint or Google Slides. Presenting a comprehensive company profile can be a game-changer for your business. A well-crafted profile connects with potential clients and vendors on another level, giving them a deep understanding of your organization. This company profile template can help...

Web Project Proposal
We live in the internet era, which means that web design is currently one of the most demanded skills. This free template is perfect for those designers who want to present their web project proposal to their clients and see a preview of the final work.

Global Technology Investments Project Proposal Infographics
Download the "Global Technology Investments Project Proposal Infographics" template for PowerPoint or Google Slides to get the most out of infographics. Whether you want to organize your business budget in a table or schematically analyze your sales over the past year, this set of infographic resources will be of great...
- Page 1 of 31

Register for free and start editing online
WPS PDF - Convert and Edit Your PDF Files Freely
WPS PDF tools allow you to convert PDF files to and from Word, Excel PowerPoint, and image files online for free. You can also view, edit, read, and collaborate on PDF files on multiple platforms. You can also download WPS PDF for free to easily experience PDF file editing features such as adding comments, filling in forms, signing contracts, and printing files.

Great Alternative To Adobe PDF
Key features for wps office pdf, pdf convert, pdf organize, pdf compress, cloud collaboration, pdf protect, more free features, features under development.
Edit PDF Like Word
Edit PDF content and make beautiful annotations Insert links, page numbers, comments, and shapes
Powerful PDF Tools Across All Platforms
Desktop application all-in-one office suite for windows pc or mac, mobile app the complete office suite for android & iphone, online web free pdf productivity solution on the cloud..
Free to try WPS PDF toolkits with powerful editing and converting features.
1. For the Windows system on PC: Get the installation package in EXE format. WPS Office is available for Windows 7/8/9/10/11. 2. For the MacOS or Linux system: Click "Free Download" to get the installation package for the corresponding system.
1. For phones with the Android system: Go to Google Play and get the WPS Office installation package in apk format. 2. For iPhones with the iOS system: Go to Apple Store and search for WPS Office. 3. PDF Editor Pro: Download it from Google Play or Apple App Store.
Online PDF tools: Use free online PDF tools to merge, compress, create, edit and convert PDFs. Quick and easy. No installation or registration required. Turn images, ebooks, and documents to PDFs in a secure manner and vice versa.
Create PDF from the file
Create blank pdf, edit&manage pdf, compress pdf, organize pdf, convert pdf, pdf to word, word to pdf, pdf to excel, excel to pdf, pdf to picture, picture to pdf, other useful features, picture to text (ocr), extract text in pictures, pdf cloud collaboration, batch pdf printing, batch pdf printing for mutiple pdf files, pdf template, desktop application, all-in-one office suite for windows pc or mac, faq online for pdf, what is the best free pdf tool.
WPS PDF Blog offers quality articles with recommended top PDF tools (available online or offline) for users to choose:
7 Best Free PDF Tools for Beginners
4 Best Free PDF Converter Apps for Mobile and Laptop
3 Best Free PDF Tools for Editing
3 Best Free PDF Editors for Android Smartphones
Get the Best Free PDF Converters 2022 Online
How can I edit a PDF without Adobe?
There are 2 easy alternative methods for editing PDF files if you haven't downloaded Adobe:
Convert your PDF file into an editable format
1. Go to pdf.wps.com and choose an editable format (Word or Excel or PPT) that you like.
2. Select the PDF file that you want to edit.
3. Convert your PDF file to Word or Excel or PowerPoint online.
4. Click "OK" and go to edit the (Word or Excel or PowerPoint) file.
Download the all-in-one WPS Office app
1. WPS PDF is one of the service tools of WPS Office (including Writer, Spreadsheet, Presentation, and PDF), and the PDF edition is available across desktop, web and mobile platforms.
2. All file formats of WPS Office are compatible with Microsoft and Adobe.
Is the PDF to Word conversion free of charge?
Yes. It is a 100% free online tool, and each user can convert files 5 times free of charge.
1. Go to WPS PDF website pdf.wps.com , then users can find the PDF to Word tool page.
2. Go to the WPS PDF website pdf.wps.com , find Free PDF Converter, and choose PDF to Word.
Trust by users around the world
This is by far one of the best esign apps I have ever used. Simple, easy, and free. You can easily fill in check mark boxes and sign a signature and line it up. I finished filling out my document in 3 mins and was able to save and print it as a PDF which could be downloaded to my PC Windows system and phone with no ads. I would suggest this app to everyone.
I like WPS. It is a competitive free office suite, at no cost! WPS Office also has a PDF editor and viewer option, with a number of features including PDF to Word, PDF to Excel, and Merge PDF. I mostly use the viewer.
On PDF, WPS is capable of converting and editing a PDF file. You can convert to other formats (Word, Excel, PowerPoint, JPG), edit text, change font, change image, put a signature and do much more. You can also print files from other file formats like .doc or .xls to PDFs. You can do these even while offline.
Find the Free Fesources and Solutions
Meet our professional services, support 7*24, stay in advanced and quick to improve, get expert tutorials, tips, and tricks online to help you operate writer in, download wps pdf for free to discover more features..
Select multiple PDF files and merge them into one PDF file online.
Convert PDF files to editable Word documents in seconds (doc, docx formats)
Convert PDF files to editable Excel spreadsheets online without downloading any software
Convert PDF files to editable PowerPoint presentations online without size limit
Separate all pages from a single PDF file online and extract pages to multiple PDF files.
Convert Word (doc, docx) files to easy-to-share PDF files while preserving the layout for free
Convert Excel spreadsheets (xls, xlsx) to easy-to-read PDF files for free
Convert PowerPoint presentations (ppt, pptx) to easy-to-view and easy-to-share PDF files for free
Convert images (JPG, JPEG, PNG, BMP) to PDF files for free and easily adjust PDF orientation and margins
Manage multiple pages of a PDF file (add, delete, or rearrange pages)
Reduce the size of PDF files online using 3 compression methods
Create and fill e-signatures in PDF files online and secure your e-signature

COMPUTER HARDWARE
Mar 13, 2019
14.32k likes | 28.01k Views
2. Chapter. COMPUTER HARDWARE. Objectives of this chapter:. You can…. Define input and output. List the characteristics of input and output devices. Describe the components of a processor and how they complete a machine cycle. Differentiate among the various types of memory.
Share Presentation
- pointing device
- input device
- output device
- 1 input device
- monitor houses display device

Presentation Transcript
2 Chapter COMPUTER HARDWARE Chapter 2 SAK3002 – Information Technology and Its Application
Objectives of this chapter: You can… Define input and output List the characteristics of input and output devices Describe the components of a processor and how they complete a machine cycle Differentiate among the varioustypes of memory Differentiate between storage devicesand storage media Chapter 2 SAK3002 – Information Technology and Its Application
Overview • This chapter covers • Input Device • Output Device • Central Unit Processing (CPU) • Memory Unit • Storage • Communications Chapter 2 SAK3002 – Information Technology and Its Application
Introduction • What is computer hardware? • Computer devices in physical form • Comprised of 4 components: • Input devices • Central Processing Unit (CPU) • Output devices • Memory Chapter 2 SAK3002 – Information Technology and Its Application
Processor Control Unit Arithmetic Logic Unit (ALU) InstructionsDataInformation InstructionsDataInformation Introduction (cont’d) Control Unit Arithmetic Logic Unit (ALU) Memory InputDevices OutputDevices Data Information StorageDevices Chapter 2 SAK3002 – Information Technology and Its Application
Introduction (cont’d) • Bit and bytes • Bit (Binary Digit) is the basic unit of information in computers • 1 bit = 0 or 1 Computer binary system • Refers to transfer rate per second • Kilobyte, megabyte, gigabyte, and terabyte are terms that describe large units of data used in measuring data storage • Example: 100 GB hard drive 8 bits = 1 Byte 1024 Bytes = 1 Kilobyte (KB) 1,048,576 Bytes = 1 Megabyte (MB) 1,043,741,824 Bytes = 1 Gigabyte (GB) 1,099,511,627,776 Bytes = 1 Terabyte (TB) Chapter 2 SAK3002 – Information Technology and Its Application
2.1 Input Device Chapter 2 SAK3002 – Information Technology and Its Application
Input Device • What is input? • Data or instructions entered into memory of computer • Input device is any hardware component that allows users to enter data and instructions Chapter 2 SAK3002 – Information Technology and Its Application
Input Device (cont’d) • Two types of input: • Data • Unprocessed text, numbers, images, audio, and video • Instructions • Programs • Commands • User responses Chapter 2 SAK3002 – Information Technology and Its Application
Input Device (cont’d) • Keyboard allows the computer user to enter • Words • Numbers • Punctuation • symbols and • special function commands into the computer’s memory Chapter 2 SAK3002 – Information Technology and Its Application
Input Device (cont’d) Chapter 2 SAK3002 – Information Technology and Its Application
mouse buttons wheel button ball mouse pad Input Device (cont’d) Pointing device controls movement of pointer, also called mouse pointer • Pointing Device Mouse • Pointing device that fits under palm of hand • Mechanical mouse has rubber or metal ball on underside Chapter 2 SAK3002 – Information Technology and Its Application
Input Device (cont’d) • Pointing Device (cont’d) Optical mouse • No moving mechanical parts inside • Senses light to detect mouse’s movement • More precise than mechanical mouse • Connects using a cable, or wireless Chapter 2 SAK3002 – Information Technology and Its Application
Input Device (cont’d) • Pointing Device (cont’d) Trackball • Stationary pointing device with a ball on its top or side • To move pointer, rotate ball with thumb, fingers, or palm of hand Chapter 2 SAK3002 – Information Technology and Its Application
Input Device (cont’d) • Pointing Device (cont’d) Touchpad and a pointing stick • Touchpadis small, flat, rectangular pointing device sensitive to pressure and motion • Pointing stickis pointing device shaped like pencil eraser positioned between keys on keyboard Chapter 2 SAK3002 – Information Technology and Its Application
Input Device (cont’d) • Pointing Device (cont’d) Joystick and a wheel • Joystickis vertical lever mounted on a base • Wheelis steering-wheel-type input device • Pedal simulates car brakes and accelerator Chapter 2 SAK3002 – Information Technology and Its Application
Input Device (cont’d) • Pointing Device (cont’d) Touch screen • Touch areas of screen with finger • Often used with kiosks Chapter 2 SAK3002 – Information Technology and Its Application
Input Device (cont’d) • Sound and voice input MIDI (musical instrument digital interface) • External device, such as electronic piano keyboard, to input music and sound effects Microphone • Allow user to input their voice Chapter 2 SAK3002 – Information Technology and Its Application
Input Device (cont’d) • Video input • Process of entering full-motion images into computer • Video capture cardis adapter card that converts analog video signal into digital signal that computer can use • Digital video (DV) camerarecords video as digital signals Chapter 2 SAK3002 – Information Technology and Its Application
Flatbed Pen or Handheld Sheet-fed Drum Input Device (cont’d) • Scanner • Light-sensing device that reads printed text and graphics • Used for image processing, converting paper documents into electronic images • Flatbed scanner – design to scan flat objects • Handheld scanner – capture small amounts of text • Sheet-fed scanner – scan one flat document at a time Chapter 2 SAK3002 – Information Technology and Its Application
Step 1: Place the document to be scanned face down on the glass window. Using buttons on the scanner or the scanner program, start the scanning process. Step 2: The scanner converts the document content to digital information, which is transmitted through the cable to the memory of the computer. Step 3: Once in the memory of the computer, users can display the image, print it, e-mail it, include it in a document, or place it on a Web page. Input Device (cont’d) How does a flatbed scanner work? Chapter 2 SAK3002 – Information Technology and Its Application
Input Device (cont’d) • Readers • Barcode Readers • Optical Mark Readers (OMR) • Radio frequency Identification (RFID) Readers • Optical Character Recognition (OCR) Devices • Magnetic Ink Character Recognition (MICR) Readers • Biometric Readers Chapter 2 SAK3002 – Information Technology and Its Application
2.2 Output Device Chapter 2 SAK3002 – Information Technology and Its Application
Output Device • What is output? • Data that has been processed into a useful form, • Output device is any hardware component that can convey information to user Chapter 2 SAK3002 – Information Technology and Its Application
Output Devices (cont’d) • Display device • Output device that visually conveys information • Information on display device sometimes called soft copy • Monitorhouses display device as separate peripheral Chapter 2 SAK3002 – Information Technology and Its Application
Output Devices (cont’d) • Display device LCD monitor • Uses liquid crystal display • Have a small footprint • Mobile devices that contain LCD displays include • Notebook computer, Tablet PC, PDA, and Smart Phone Chapter 2 SAK3002 – Information Technology and Its Application
Transparent electrodes Alignment layer Color filter Polarizing glass filter Fluorescent tube panel Output Device (cont’d) • Uses liquid compound to present information on a display How does LCD work? Step 2.As light passes through liquid crystal, electrical charge causes some of the cells to twist, making light waves bend as they pass through color filter. Step 1.Panel of fluorescent tubes emits light waves through polarizing glass filter, which guides light toward layer of liquid crystal cells. Liquid crystal cells Step 3.When light reaches second polarizing glass filter, light is allowed to pass through any cells that line up at the first polarizing glass filter. Absence and presence of colored light cause image to display on the screen. Chapter 2 SAK3002 – Information Technology and Its Application
Output Device (cont’d) • Display device Plasma monitor • Displays image by applying voltage to layer of gas • Larger screen size and higher display quality than LCD, but are more expensive Chapter 2 SAK3002 – Information Technology and Its Application p. 306 Fig. 6-7
Output Device (cont’d) • Display device CRT monitor • Contains cathode-ray tube (CRT) • Screen coated with tiny dots of phosphor material • Each dot consists of a red, blue, and green phosphor • Common sizes are 15, 17, 19, 21, and 22 inches • Viewable size is diagonal measurement of actual viewing area Chapter 2 SAK3002 – Information Technology and Its Application
portrait landscape Output Device (cont’d) • Printer • Output device that produces text and graphics on a physical medium • Result ishard copy, orprintout • Two orientations:portraitandlandscape Chapter 2 SAK3002 – Information Technology and Its Application
Output Device (cont’d) • Depends on printing needs • How do you know which printer to buy? Budget Speed Color orblack and white Cost per page Multiple copies Graphics and photo printing Paper typesand sizes Systemcompatibility Future needs Wirelesscapability Chapter 2 SAK3002 – Information Technology and Its Application
300 dpi 600 dpi 1200 dpi Output Device (cont’d) • Printer • Two basic types: • Impact • Non-impact • What is the resolution of a printer? • Sharpness and clarity • Measured by number of dots per inch (dpi) printer can output Chapter 2 SAK3002 – Information Technology and Its Application
Output Device (cont’d) • Impact printer • Characters/graphics are formed on the paper by physical striking contact between ink ribbon and paper • Examples are • dot-matrix printer (continuous paper), • line printer (mainframe/minicomputer) Chapter 2 SAK3002 – Information Technology and Its Application
Output Device (cont’d) • Nonimpact printer • Forms characters and graphics without striking paper Ink-jet printer • sprays tiny drops of liquid ink onto paper • Prints in black-and-white or color on a variety of paper types Chapter 2 SAK3002 – Information Technology and Its Application
Output Device (cont’d) Photo printer • Color printer that produces photo-lab-quality pictures • Many photo printers have a built-in card slot Chapter 2 SAK3002 – Information Technology and Its Application
Output Device (cont’d) Laser printer • High-speed, high-quality nonimpact printer • Prints text and graphics in very high-quality resolution, ranging from 1,200 to 2,400 dpi • Typically costs more than ink-jet printer, but is much faster Chapter 2 SAK3002 – Information Technology and Its Application
Output Device (cont’d) Thermal printer • Generates images by pushing electrically heated pins against heat-sensitive paper • Dye-sublimation printer (also called a digital photo printer) uses heat to transfer dye to specially coated paper Chapter 2 SAK3002 – Information Technology and Its Application
Output Device (cont’d) Mobile printer • Small, lightweight, battery-powered printer that allows mobile user to print from notebook computer, Tablet PC, or PDA while traveling Chapter 2 SAK3002 – Information Technology and Its Application
Output Device (cont’d) • Small printer that prints on adhesive-type material Label printers and Postage printers • Most also print bar codes • Postage printer has built-in digital scale and printspostage stamps Chapter 2 SAK3002 – Information Technology and Its Application
Output Device (cont’d) Plotter • Sophisticated printer used to produce high-quality drawings • Large-format printercreates photo-realistic-qualitycolor prints Chapter 2 SAK3002 – Information Technology and Its Application
Output Device (cont’d) • Audio output device • Computer component that produces music, speech, or other sounds • Speakers and headsets are common devices Chapter 2 SAK3002 – Information Technology and Its Application
Output device (cont’d) • Data projector • Device that takes image from computer screen and projects it onto larger screen Chapter 2 SAK3002 – Information Technology and Its Application
Output Device (cont’d) • Sends resistance to joystick or wheel in response to actions of user • Force feedback Chapter 2 SAK3002 – Information Technology and Its Application
2.3 Central Processing Unit (CPU) Chapter 2 SAK3002 – Information Technology and Its Application
Processor Control Unit Arithmetic Logic Unit (ALU) CPU • What is the central processing unit (CPU)? • Also called theprocessor • Interprets and carries out basic instructions that operate a computer Control Unit Arithmetic Logic Unit (ALU) • Control unit directs and coordinates operations in computer • Arithmetic logic unit (ALU) performs arithmetic, comparison, and logical operations Chapter 2 SAK3002 – Information Technology and Its Application
Memory Processor ALU Control Unit CPU (cont’d) • Four operations of the CPU comprise a machine cycle • Machine cycle Step 1. FetchObtain program instruction or data item from memory Step 2. DecodeTranslate instruction into commands Step 4. StoreWrite result to memory Step 3. ExecuteCarry out command Chapter 2 SAK3002 – Information Technology and Its Application
CPU (cont’d) • Register • Temporary high-speed storage area that holds data and instructions Stores location from where instruction was fetched Stores instruction while it is being decoded Stores data while ALU computes it Stores results of calculation Chapter 2 SAK3002 – Information Technology and Its Application
CPU (cont’d) • System clock • Controls timing of all computer operations • Generates regular electronic pulses, or ticks, that set operating pace of components of system unit Each tick is a clock cycle Pace of system clock is clock speed Most clock speeds are in the gigahertz (GHz) range (1 GHz = one billion ticks of system clock per second) Processor speed can also be measured in millions of instructions per second (MIPS) Chapter 2 SAK3002 – Information Technology and Its Application
Processor 1 Processor 2 Processor 3 Processor 4 Memory Memory Memory Memory CPU (cont’d) Control Processor • Parallel processing • Using multiple processors simultaneously to execute a program faster • Requires special software to divide problem and bring results together Results combined Chapter 2 SAK3002 – Information Technology and Its Application
2.4 Memory Unit Chapter 2 SAK3002 – Information Technology and Its Application
- More by User

COMPUTER HARDWARE MOUSE A computer mouse can drag icons. A computer mouse can move the cursor. A computer mouse is an input device. KEYBOARD A keyboard is what you use to type. A keyboard has letters, numbers, & symbols. A keyboard is an input device. MONITOR
1.08k views • 9 slides

Computer Hardware
If the computer does not have enough RAM to run an application than pieces of ... a type of display used in digital watches and many portable computers. Video Cards ...
1.19k views • 20 slides

Computer Hardware. 1. The parts of a computer you can see and touch. Hardware. 2. Where you see visual output from your computer. Monitor. 3. Largest circuit board. Motherboard. 4. 1 trillion bytes. Terabyte. 5. Temporary Memory. RAM.
976 views • 23 slides

Chapter 2: Computer Hardware. 2. Chapter Contents. Section A: Personal Computer BasicsSection B: Microprocessors and MemorySection C: Storage DevicesSection D: Input and Output DevicesSection E: Hardware Security. Chapter 2: Computer Hardware. 3. Personal Computer Basics. Personal Computer Syste
1.19k views • 54 slides

Computer Hardware. Hery hamdi azwir. ICT & Computer. What is ICT (TIK)? Teknologi Informasi meliputi segala hal yang berkaitan dengan proses , penggunaan sebagai alat bantu, manipulasi , dan pengelolaan informasi . (Wikipedia)
572 views • 40 slides

Computer Hardware. Input Devices. In computing, an input device is any peripheral (piece of computer hardware equipment) used to provide data and control signals to an information processing system such as a computer or other information appliance. Keyboard. Wired or wireless
720 views • 29 slides
COMPUTER HARDWARE. All the physical Components that make up a Computer System. (Catherine). TERMONOLOGY BASICS. By Angus Macaulay. THE NEW USER BASZIC TERMONOLOGY COMPETENCY QUIZ. HOW DO YOU STACK UP??.
665 views • 10 slides

computer hardware
computer hardware . f1031 – computer hardware. hard drive. The hard disk drive (HDD) is a magnetic storage device installed inside the computer. The storage capacity is measured in gigabytes (GB).
402 views • 10 slides
Computer Hardware. Introduction. Computer System Components. Input Keyboard, Mouse, Camera, Touch Pad Processing CPU Output Monitor, Printer Storage Floppy, Hard Drive, CD, DVD, Flash Drive. Generations . The Binary System. Bits – Binary digits, or 0,1.
682 views • 9 slides

Computer Hardware. 1. The parts of a computer you can see and touch. Hardware. 2. Where you see visual output from your computer. Monitor. 3. Largest circuit board. Motherboard . 4. 1 trillion bytes. Terabyte . 5. Temporary Memory. RAM.
1.45k views • 23 slides

Computer Hardware. Topic 3. Computer Hardware. Shows location of the following devices on a standard ATX motherboard Advanced Technology Extended (ATX) – computers are standardize for parts and fit Many parts are interchangeable Not true for laptops; designs vary. Computer Hardware.
685 views • 10 slides

COMPUTER HARDWARE. Types of Computers. Super Computers $5-20M 2.1B ops/sec Massively Parallel = 8.6B ops/sec Cray Main Frames $50K-5M - several million ops/sec IBM. Types of Computers. Mini Computers few thou to $100K client/server VAX by DEC
645 views • 12 slides

Computer Hardware. Course: CIS 3003 Fundamental of Information Technology. Logic and Binary. Logic FALSE is represented with binary 0. Logic TRUE is represented with binary 1. AND/NAND Gates. OR/NOR Gates. XOR/NXOR Gates. Binary Addition Gate. Transistors, Logic Gates, and IC.
698 views • 35 slides

Computer Hardware. The Processing Unit. The Computer System. Communication Devices. Processing Unit. Input Devices. Output Devices. Storage Devices. The Processing Unit. The main part of a microcomputer is called the System Unit Most of the processing hardware is on the motherboard.
1.37k views • 22 slides

Computer Hardware. Unit 1 Computer Applications A. Hardware defined. Physical parts of a computer Four main components of hardware Input devices Processing unit Output devices Storage devices. Input Devices. Transport data into the computer Keyboard Mouse Scanner Digital camera
533 views • 7 slides

Computer Hardware. In this lecture, we will study: The hardware components of an information system: CPU (central processing unit) Memory (primary and secondary storage) Input devices Output devices. The classification of computers by power. Strategic issues regarding hardware.
1.13k views • 25 slides
Computer Hardware. Learning Objectives. Understand the history and evolution of computer hardware. Identify the major types and uses of microcomputer, midrange, and mainframe computer systems. Outline the major technologies and uses of computer peripherals for input, output, and storage.
1.09k views • 44 slides

Computer Hardware. Standard 1 - Objective 1: Demonstrate understanding of computer hardware, peripherals and troubleshooting. All the physical or tangible parts of a computer
732 views • 35 slides
Chapter 2. Computer Hardware. Chapter PREVIEW. When you complete this chapter, you should be able to: Explain why most computers are digital Describe the role of the ALU List factors that affect performance Explain RAM Compare storage technologies Describe computer’s expansion bus
846 views • 67 slides

COMPUTER HARDWARE. Hardware is any physical part of the computer that you can touch, see and pickup. Peripheral Devices Any external device attached to the system unit is called a computer peripheral. CLASSIFICATION OF COMPUTER HARDWARE. Input devices Output devices Processing devices
2.16k views • 51 slides

Computer Hardware. Objectives. Explain why most computers are digital Describe the role of the ALU List factors that affect performance Explain RAM Compare storage technologies Describe computer’s expansion bus Explain hardware compatibility considerations
376 views • 15 slides

Data Representation and Digital Electronics. Section A. CHAPTER 2. Computer Hardware. PARSONS/OJA. Page 58. Chapter 2. Computer Hardware. Chapter PREVIEW. When you complete this chapter, you should be able to: Explain why most computers are digital Describe the role of the ALU
1.15k views • 40 slides

IMAGES
COMMENTS
BASIC COMPUTER COMPONENTS Case • Often called the "CPU"/ "computer", the case houses and provides power to the major computer components, including the MotherBoard, CPU, Hard Drive, RAM, Video Card, Sound Card, etc. • Those components that do not housed in the computer case are usually referred to as "peripherals". • Houses the power ...
Download ppt "Chapter 1: Introduction to Computer". Computer A computer is an electronic device, operating under the control of instructions stored in its own memory that can accept data (input), process the data according to specified rules, produce information (output), and store the information for future use.
Computer Components - Download as a PDF or view online for free. Computer Components - Download as a PDF or view online for free ... Parts of a Computer ppt OECLIB Odisha Electronics ... Mac - OS PC - DOS (basis) Windows Linux (used in computer servers, and open source-free to all, application) Memory - Write/Read What is Writable? RAM What is ...
Download ppt "Components of a computer". Components of a personal computer Computer systems ranging from a controller in a microwave oven to a large supercomputer contain components providing five functions. A typical personal computer has hard, floppy and CD-ROM disks for storage, memory and CPU chips inside the system unit, a keyboard and ...
contains the brain of the computer which. processes and communicates information with all. other parts of the computer. 6. Keyboard. the keyboard is an input device used to type in. information into the computer. 7. Mouse.
Basic Parts of Computer. Nov 26, 2015 • Download as PPTX, PDF •. 66 likes • 98,633 views. Dex Wasin. Basic parts of computer. Technology. 1 of 17. Download now. Basic Parts of Computer - Download as a PDF or view online for free.
1.97k likes | 5.08k Views. Computer Basics 1. Computer Basic 1 includes two lessons: Lesson 1: Introduction to Computers Lesson 2: Common Computer Terminology. Lesson 1 - Introduction to Computer Objectives. After completing lesson 1, you will be able to: Describe the importance of computers in today's world. Download Presentation.
Basics of Computer.ppt - Download as a PDF or view online for free. Basics of Computer.ppt - Download as a PDF or view online for free ... Introduction to Computer 2. Main Parts of Computer 3. Types of Computer 4. Storage Unit vs. Memory Unit 5. Classification on Working System 6. Types of Network 7. Classification of Computer- Based on Size 8 ...
Presentation Transcript. Computer Components By Kelsey Wright. Motherboard • Amotherboard is the central printed circuit board (PCB) in many modern computers and holds many of the crucial components of the system, providing connectors for other peripherals. Power Supply • A power supply unit (PSU) converts mains AC to low-voltage regulated ...
Components of a Computer A Computer system consists of the following 4 components. Input Unit Output Unit Central Processing Unit Memory Unit. Input Unit An Input Unit is any device (i.e., a piece of a computer hardware equipment) used to provide data and control signals to an computer. Different Input Devices are, Keyboard Pointing Devices ...
Components of a Computer System. A computer system is made up of several key components, including the central processing unit (CPU), memory, storage, input devices, output devices, and connectivity hardware. The CPU is the brain of the computer, while memory stores data temporarily for processing. Storage devices provide long-term data storage.
A power supply mounts inside the computer case. This converts the AC mains supply from the wall socket and supplies the correct DC voltages to all the components inside the computer. A computer power supply supplies the following voltages: • +3.3v: This voltage is supplied to the motherboard.
Computer Hardware Parts.ppt - Free download as Powerpoint Presentation (.ppt), PDF File (.pdf), Text File (.txt) or view presentation slides online. The document provides information about the basic components and structure of a computer system. It discusses the three main parts: the CPU, input/output devices, and memory. It then describes various hardware components such as the motherboard ...
Free Google Slides theme, PowerPoint template, and Canva presentation template. Hardware is the set of physical or material elements that make up a computer or computer system. Your workshop attendees will learn about this concept and much more, especially if you use this creative template that we have designed to help you prepare your material.
Computer Hardware Components. 2. Computer Hardware components Motherboard CPU Keyboard Mouse RAM Monitor Floppy drive CD-ROM drive Hard disk drive DVD Drives. 3. 4. 5. Central Processing Unit The microprocessor consists of three sections: 1.Arithmetic Logic Unit 2.Registers 3.Control Unit.
Below you'll see thumbnail sized previews of the title slides of a few of our 52 best computer components templates for PowerPoint and Google Slides. The text you'll see in in those slides is just example text. The computer components-related image or video you'll see in the background of each title slide is designed to help you set the ...
The Motherboard • Motherboard: The place where most of the electronics including the CPU are mounted. The Central Processing Unit • The Central Processing Unit ( CPU) • Often referred to as the "brain" of the computer. • Responsible for controlling all activities of the computer system. • The two major components of the CPU are: 1.
Google Slides: Click the link to make a copy that saves to your Google Drive. PowerPoint: Click the link to open the presentation in view mode, then download and save the file. Once you have downloaded the PPT, you will be able to enable editing. Please note, PowerPoint and Google Slides have different functionalities, so the resources may have ...
For Teachers. Computer Lesson Plans. Free Games Downloads for Using Computers. Free Clipart. Free Templates. Pete's PowerPoint Station is your destination for free PowerPoint presentations for kids and teachers about Parts of a Computer, and so much more.
This slide outlines the primary components of inclavare containers architecture. The purpose of this slide is to demonstrate the different elements of inclavare containers and their working. The main components include Kubelet, shim-rune, language runtime, liberpal.so, containerd, rune, SGX libOS, and PAL-API.
Operating system • Tells computer how to use its own components • Windows XP, Macintosh, Linux • Essential for any computer as it acts as an interpreter between hardware, application programs and the user • Network operating system (OS) • Allows computers to communicate and share data across a network • Windows Server 2003 ...
Download our Computer-related Google Slides themes and PowerPoint templates and create outstanding presentations Free Easy to edit Professional ... Use these Google Slides themes or download our PPT files for PowerPoint or Keynote to give a presentation about a Computer-related topic, including Information Technology. ... This free template is ...
Free Download. 1. For phones with the Android system: Go to Google Play and get the WPS Office installation package in apk format. 2. For iPhones with the iOS system: Go to Apple Store and search for WPS Office. 3. PDF Editor Pro: Download it from Google Play or Apple App Store. Try PDF Tools online.
2. Chapter. COMPUTER HARDWARE. Objectives of this chapter:. You can…. Define input and output. List the characteristics of input and output devices. Describe the components of a processor and how they complete a machine cycle. Differentiate among the various types of memory.